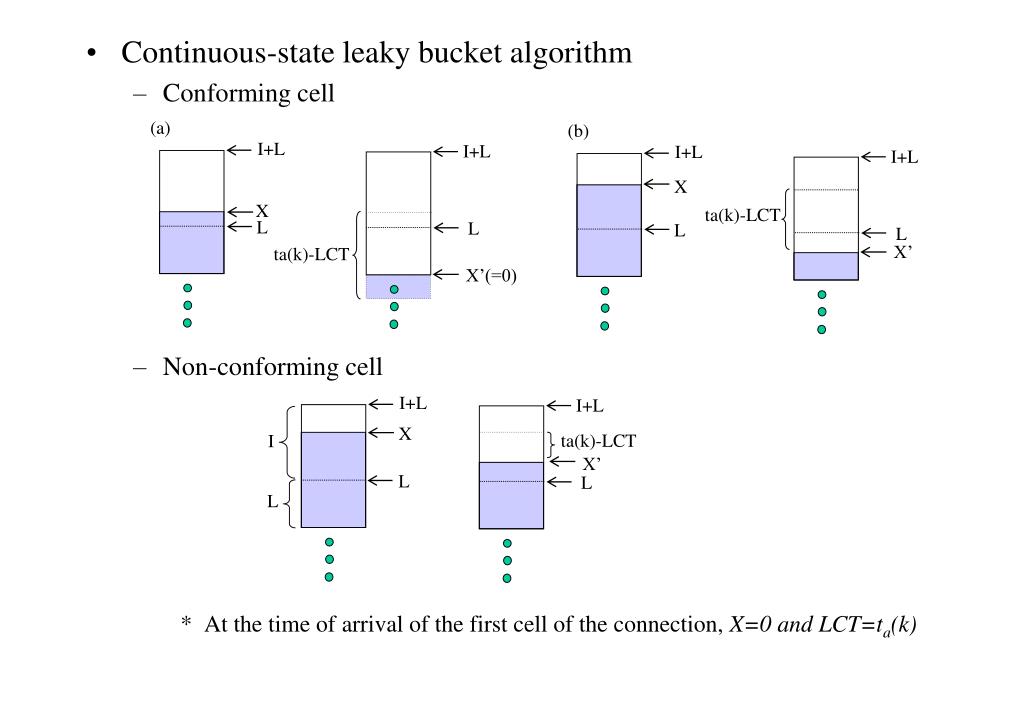
Leaky Bucket Algorithm And Its Properties . a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. A fifo queue holds the packets. It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. a simple leaky bucket algorithm can be implemented using fifo queue.
from www.slideserve.com
the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. A fifo queue holds the packets. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. It ensures that the flow of. a simple leaky bucket algorithm can be implemented using fifo queue. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network.
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download
Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. a simple leaky bucket algorithm can be implemented using fifo queue. A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring. Leaky Bucket Algorithm And Its Properties.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Leaky Bucket Algorithm And Its Properties A fifo queue holds the packets. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Step 1 − let us. A fifo queue holds the packets. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. It ensures that the flow of.. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Leaky Bucket Algorithm And Its Properties It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. a simple leaky bucket algorithm can be implemented using fifo queue.. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. A fifo queue holds the packets. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It ensures that the flow of. leaky bucket algorithm mainly controls the total. Leaky Bucket Algorithm And Its Properties.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm And Its Properties Step 1 − let us. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. a simple leaky bucket algorithm can be implemented using. Leaky Bucket Algorithm And Its Properties.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm And Its Properties It ensures that the flow of. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A fifo queue holds the packets. . Leaky Bucket Algorithm And Its Properties.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm And Its Properties the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket algorithm is a traffic shaping. Leaky Bucket Algorithm And Its Properties.
From www.studocu.com
Leaky Bucket Algorithm Leaky Bucket A leaking bucket is a simple Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. A fifo queue holds the packets. It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. a leaky bucket algorithm is a method. Leaky Bucket Algorithm And Its Properties.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. It ensures that the flow of. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. A fifo queue holds the. Leaky Bucket Algorithm And Its Properties.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm And Its Properties Step 1 − let us. A fifo queue holds the packets. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. a simple leaky bucket algorithm can be implemented using fifo queue. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID1753059 Leaky Bucket Algorithm And Its Properties the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. a simple leaky bucket algorithm can be implemented using fifo queue. Step 1 − let us. A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping and policing technique used. Leaky Bucket Algorithm And Its Properties.
From vtucselabs.blogspot.com
VTU CSE LABS CN 12 LEAKY BUCKET ALGORITHM Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It. Leaky Bucket Algorithm And Its Properties.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket. Leaky Bucket Algorithm And Its Properties.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Leaky Bucket Algorithm And Its Properties It ensures that the flow of. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. A fifo queue holds the packets. a simple. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT Lecture 14 Distributed Multimedia Systems PowerPoint Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. the leaky bucket is a traffic shaping algorithm used to control the flow of data. Leaky Bucket Algorithm And Its Properties.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network.. Leaky Bucket Algorithm And Its Properties.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A fifo queue holds the packets.. Leaky Bucket Algorithm And Its Properties.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm And Its Properties Step 1 − let us. It ensures that the flow of. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. a simple leaky bucket algorithm can be implemented using fifo queue. a leaky bucket algorithm is a method used in computer networks to. Leaky Bucket Algorithm And Its Properties.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm And Its Properties A fifo queue holds the packets. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic.. Leaky Bucket Algorithm And Its Properties.
From www.pinterest.com
This sample shows the Leaky Bucket Algorithm that is widely used in Leaky Bucket Algorithm And Its Properties the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. A fifo queue holds the packets. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a traffic shaping and policing. Leaky Bucket Algorithm And Its Properties.
From www.youtube.com
Leaky bucket algorithm YouTube Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A fifo queue holds the packets. a simple leaky bucket algorithm can be implemented using fifo queue. It ensures that the flow of. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. It ensures that the flow of. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. Step 1 − let us. a leaky bucket. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
Selectivity of the conventional leaky bucket algorithm, the fuzzy leaky Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring. Leaky Bucket Algorithm And Its Properties.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm And Its Properties a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us. It ensures that the flow of. the leaky bucket algorithm is a traffic shaping and policing. Leaky Bucket Algorithm And Its Properties.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm And Its Properties Step 1 − let us. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission. Leaky Bucket Algorithm And Its Properties.
From www.tech-maze.info
System Design Leaky Bucket Algorithm And Its UsesSystem Design Rohit Modi Leaky Bucket Algorithm And Its Properties leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the. Leaky Bucket Algorithm And Its Properties.
From www.prepbytes.com
Leaky Bucket Algorithm Leaky Bucket Algorithm And Its Properties It ensures that the flow of. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping and policing technique. Leaky Bucket Algorithm And Its Properties.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm And Its Properties the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. a leaky bucket algorithm is a method. Leaky Bucket Algorithm And Its Properties.
From gamma.app
Leaky bucket algorithm Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm. Leaky Bucket Algorithm And Its Properties.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm And Its Properties a simple leaky bucket algorithm can be implemented using fifo queue. It ensures that the flow of. the leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of. Leaky Bucket Algorithm And Its Properties.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic Leaky Bucket Algorithm And Its Properties Step 1 − let us. a leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. the leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in. A fifo queue holds the packets. a simple leaky bucket algorithm can be implemented. Leaky Bucket Algorithm And Its Properties.