Security Evaluation . security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. the cc permits comparability between the results of independent security evaluations, by providing a common set of. an information security assessment is the process of determining how effectively an entity being. — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. this document establishes the general concepts and principles of it security evaluation and specifies the general. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with.
from www.titanhq.com
this document establishes the general concepts and principles of it security evaluation and specifies the general. — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. an information security assessment is the process of determining how effectively an entity being. the cc permits comparability between the results of independent security evaluations, by providing a common set of. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security.
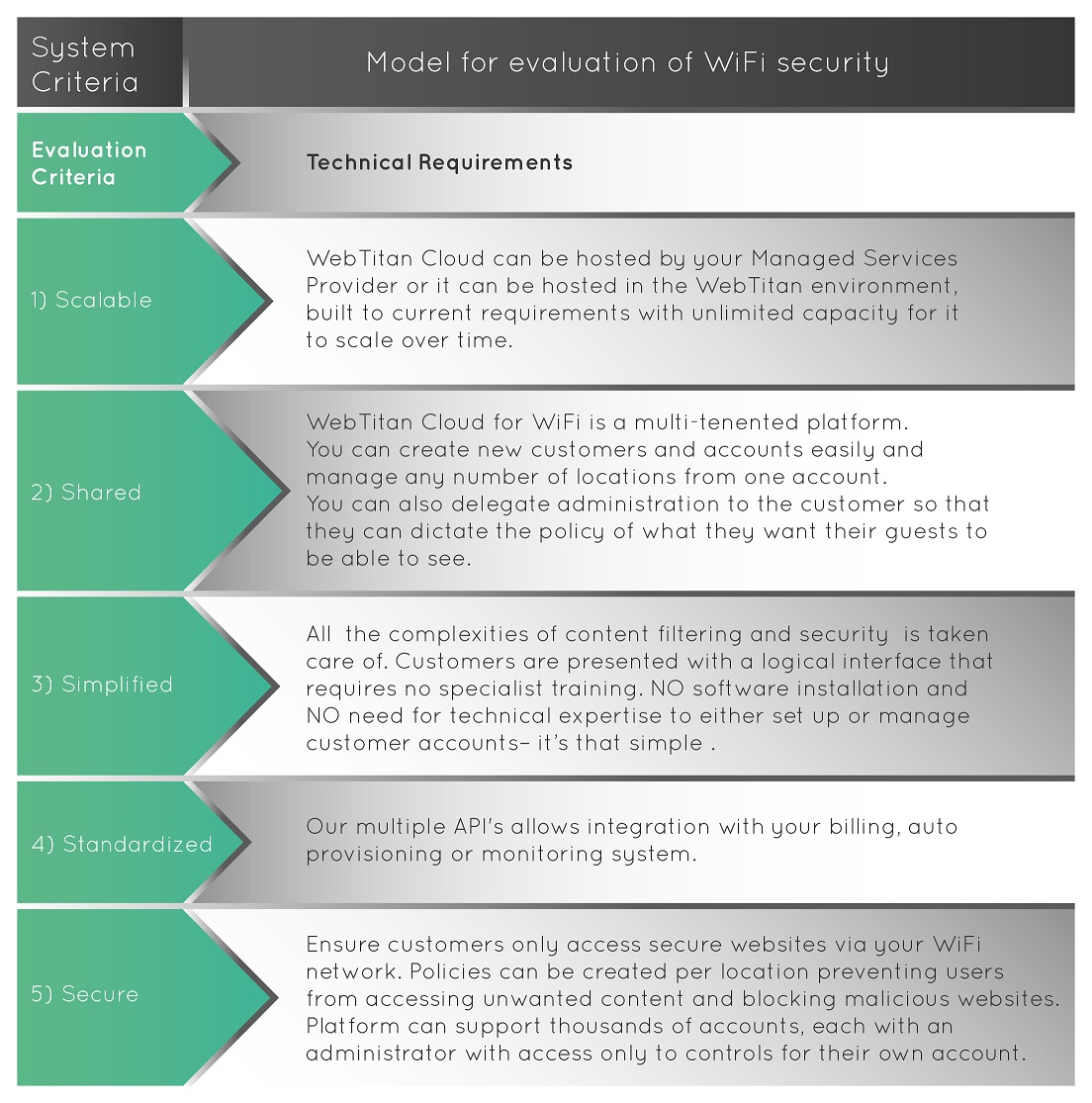
How to evaluate a WiFi security solution A Guide for MSPs
Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. this document establishes the general concepts and principles of it security evaluation and specifies the general. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. the cc permits comparability between the results of independent security evaluations, by providing a common set of. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. an information security assessment is the process of determining how effectively an entity being.
From www.alpinesecurity.com
How to Perform a Cybersecurity Risk Assessment A StepbyStep Guide Security Evaluation security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. an information security assessment is the process of determining how effectively an entity being. this version of. Security Evaluation.
From www.researchgate.net
(PDF) New approach in information system security evaluation Security Evaluation an information security assessment is the process of determining how effectively an entity being. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this document establishes the general concepts and principles of it security evaluation and specifies the general. security evaluation should be an integral part of a. Security Evaluation.
From www.riscure.com
Security highlight What did we learn in 20 years of security Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this document establishes the general. Security Evaluation.
From www.onwardsecurity.com
Product Security Assessment Onward Security, a DEKRA company Security Evaluation an information security assessment is the process of determining how effectively an entity being. this document establishes the general concepts and principles of it security evaluation and specifies the general. — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology security evaluation (cc v3.1) is. Security Evaluation.
From www.all-electronics.de
Safety und SecurityManagement im Automobilbereich die Grundlagen Security Evaluation this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits. Security Evaluation.
From www.researchgate.net
(PDF) Security Evaluation of Digital Libraries Security Evaluation an information security assessment is the process of determining how effectively an entity being. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. security evaluation should be an integral part of a system security. Security Evaluation.
From subscription.packtpub.com
Cloud security assessment Practical Industrial of Things Security Evaluation the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this. Security Evaluation.
From bleuwire.com
Why You Should Conduct an IT Security Assessment Bleuwire Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. security evaluation should be an integral part. Security Evaluation.
From slidesdocs.com
Form To Evaluate The Performance Of Security Guards Excel Template And Security Evaluation this document establishes the general concepts and principles of it security evaluation and specifies the general. an information security assessment is the process of determining how effectively an entity being. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. security evaluation refers to the process of. Security Evaluation.
From zeltser.com
Tips for Creating a Strong Cybersecurity Assessment Report Security Evaluation this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. an information security assessment is the process of determining how effectively an entity being. — the guide provides practical recommendations for designing, implementing, and maintaining technical. the cc permits comparability between the results of independent security evaluations,. Security Evaluation.
From www.getapp.com
IT Security Assessment Template To Conduct Thorough Security Audits for Security Evaluation this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits comparability between the results of independent security evaluations, by providing a common set of. — the guide provides practical recommendations for designing, implementing, and maintaining technical. an information security assessment is the process of determining how effectively. Security Evaluation.
From www.pinterest.com
Security Assessment Checklist Template in 2020 Checklist template Security Evaluation security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. an information security assessment is the process of determining how effectively an entity being. the cc permits comparability between the results of independent security evaluations, by providing a common set of. — the guide provides practical recommendations. Security Evaluation.
From www.researchgate.net
(PDF) Advanced Information Security Management Evaluation System Security Evaluation an information security assessment is the process of determining how effectively an entity being. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. — the guide. Security Evaluation.
From www.slideteam.net
Tips To Create Cyber Security Evaluation Report Presentation Graphics Security Evaluation this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. an information security assessment is the process of determining how effectively an entity being. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. — the guide provides. Security Evaluation.
From triciascaglione.blogspot.com
customer service evaluation tool cset triciascaglione Security Evaluation an information security assessment is the process of determining how effectively an entity being. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits comparability between the results. Security Evaluation.
From www.verkada.com
What to Ask Before You Buy Security Vendor Evaluation Checklist Verkada Security Evaluation the cc permits comparability between the results of independent security evaluations, by providing a common set of. an information security assessment is the process of determining how effectively an entity being. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation should be an integral part. Security Evaluation.
From www.researchgate.net
Overview of the Security Evaluation Framework SEF (Figure 4) receives Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology security evaluation. Security Evaluation.
From www.iiconsortium.org
Security Claims Evaluation Testbed Industrial Consortium Security Evaluation the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation should be an integral part of. Security Evaluation.
From dremelmicro.com
Security Assessment Checklist Template Security Evaluation this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. an information security assessment is the process of determining how effectively an entity being. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this document establishes the general concepts and. Security Evaluation.
From kleinhirn.eu
Common Criteria for Information Technology Security Evaluation Das Security Evaluation this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. an information security assessment is the process of determining how effectively an entity being. security evaluation refers to. Security Evaluation.
From www.smartsheet.com
Free Cybersecurity Risk Assessment Templates Smartsheet Security Evaluation security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this document establishes the general concepts and principles of it security evaluation and specifies the general. this version of. Security Evaluation.
From www.pdffiller.com
Security Guard Evaluation Form Fill Online, Printable, Fillable Security Evaluation an information security assessment is the process of determining how effectively an entity being. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. the cc permits comparability. Security Evaluation.
From docslib.org
Common Criteria for Information Technology Security Evaluation Part 2 Security Evaluation this document establishes the general concepts and principles of it security evaluation and specifies the general. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. the cc permits comparability between the results of independent security evaluations, by providing a common set of. — the guide provides. Security Evaluation.
From www.titanhq.com
How to evaluate a WiFi security solution A Guide for MSPs Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. this document establishes the general concepts and principles of it security evaluation and specifies the general. this version of the common criteria for information. Security Evaluation.
From www.researchgate.net
Security Specification & Evaluation Framework. Download Scientific Security Evaluation an information security assessment is the process of determining how effectively an entity being. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. this version of the common criteria for. Security Evaluation.
From www.ferrarisinvestigations.com
Security Assessments Ferraris Investigations & Consulting, LLC Security Evaluation this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation should be an integral part. Security Evaluation.
From www.secure-ic.com
Cybersecurity evaluation tool and risk assessment SecureIC Security Evaluation this document establishes the general concepts and principles of it security evaluation and specifies the general. this version of the common criteria for information technology security evaluation (cc v3.1) is the first major revision since. — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology. Security Evaluation.
From www.youtube.com
System Security Evaluation Models on Common Criteria (CISSP Free by Security Evaluation an information security assessment is the process of determining how effectively an entity being. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this version of. Security Evaluation.
From www.smartsheet.com
Free Cybersecurity Risk Assessment Templates Smartsheet Security Evaluation the cc permits comparability between the results of independent security evaluations, by providing a common set of. an information security assessment is the process of determining how effectively an entity being. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation refers to the process of conducting regular reviews and checks of. Security Evaluation.
From www.oreilly.com
Security Evaluation Strategy EnterpriseWide Security Architecture Security Evaluation an information security assessment is the process of determining how effectively an entity being. this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology. Security Evaluation.
From www.blackberry.com
Cybersecurity Maturity Evaluation Guide Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. the cc permits comparability between the results. Security Evaluation.
From docslib.org
An Approach for Security Evaluation and Certification of a Complete Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. an information security assessment is the process of determining how effectively an entity being. this document establishes the general concepts and principles of it security evaluation and specifies the general. the cc permits comparability between the results of independent security evaluations, by providing a. Security Evaluation.
From studylib.net
Security Evaluation Security Evaluation the cc permits comparability between the results of independent security evaluations, by providing a common set of. — the guide provides practical recommendations for designing, implementing, and maintaining technical. security evaluation refers to the process of conducting regular reviews and checks of it systems to ensure compliance with. this document establishes the general concepts and principles. Security Evaluation.
From www.crowdstrike.com
Cloud Security Assessments Data Sheet CrowdStrike Security Evaluation — the guide provides practical recommendations for designing, implementing, and maintaining technical. an information security assessment is the process of determining how effectively an entity being. security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. this version of the common criteria for information technology security. Security Evaluation.
From www.researchgate.net
Regional water security evaluation system Download Scientific Diagram Security Evaluation security evaluation should be an integral part of a system security with the purpose of assessing and analyzing the security. the cc permits comparability between the results of independent security evaluations, by providing a common set of. this version of the common criteria for information technology security evaluation (cc:2022) is the first major revision since. this. Security Evaluation.