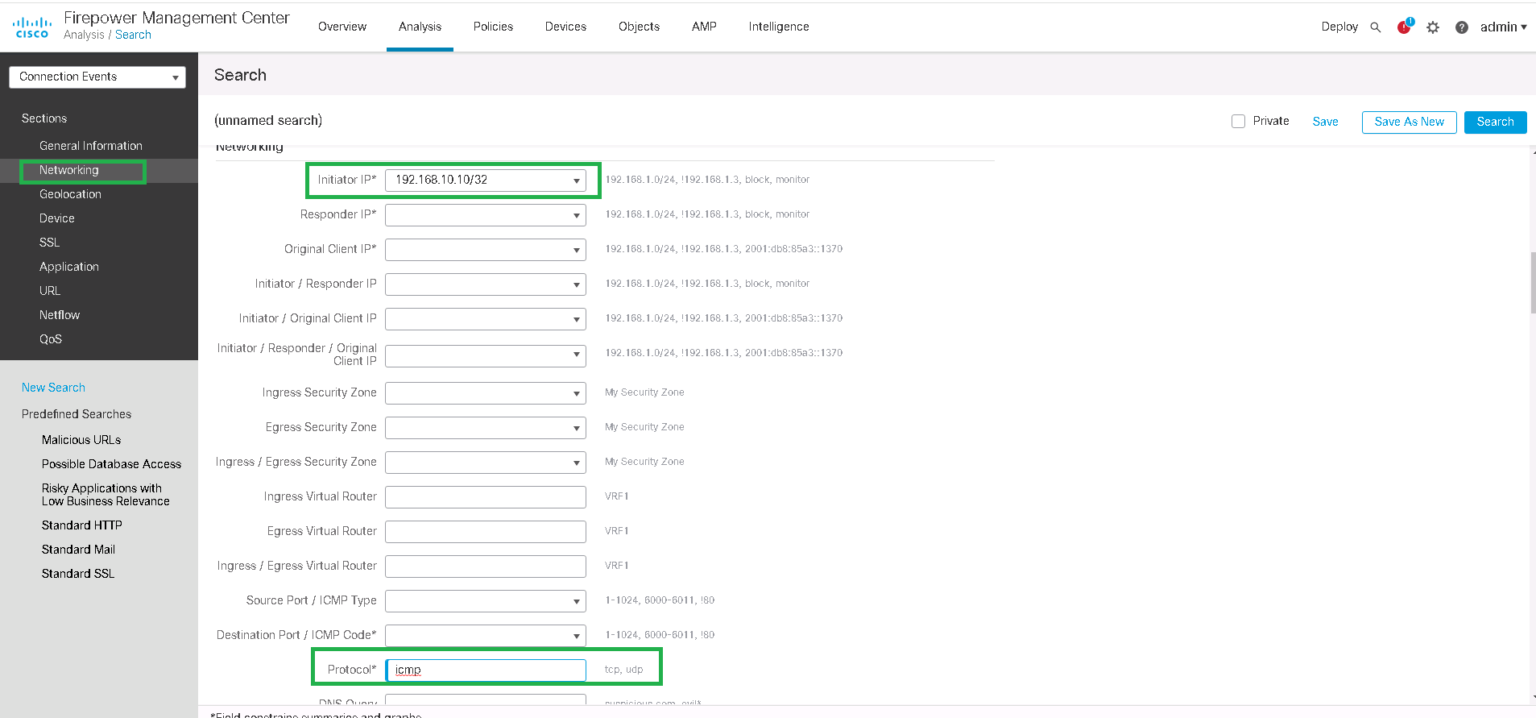
Cisco Ftd Access Control Policy Best Practices . Review the following requirements and general. Best practices for access control. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Best practices for access control rules. Access control rules provide a granular method of handling network traffic. Cisco secure firewall access control policy guidance. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. The access control policy is your primary tool for protecting your internal networks and. Consider these common practices and. This document discusses the secure firewall's access control feature's key components and configuration. Access control —use the access control policy to determine which connections are allowed on the network. General best practices for access control.
from rayka-co.com
Best practices for access control. General best practices for access control. Best practices for access control rules. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. This document discusses the secure firewall's access control feature's key components and configuration. The access control policy is your primary tool for protecting your internal networks and. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. Access control —use the access control policy to determine which connections are allowed on the network. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Access control rules provide a granular method of handling network traffic.
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?)
Cisco Ftd Access Control Policy Best Practices General best practices for access control. Best practices for access control rules. This document discusses the secure firewall's access control feature's key components and configuration. Access control —use the access control policy to determine which connections are allowed on the network. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. The access control policy is your primary tool for protecting your internal networks and. Access control rules provide a granular method of handling network traffic. Cisco secure firewall access control policy guidance. Best practices for access control. Review the following requirements and general. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. General best practices for access control. Consider these common practices and.
From www.petenetlive.com
Configure Cisco FTD Port Forwarding (via FDM) Cisco Ftd Access Control Policy Best Practices Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. This document discusses the secure firewall's access control feature's key components and configuration. The following topics explain some common tasks. Cisco Ftd Access Control Policy Best Practices.
From www.youtube.com
5 Cisco NGFW Firepower Threat Defense FTD 7 0 Access Control Policies Cisco Ftd Access Control Policy Best Practices Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. General best practices for access control. Cisco secure firewall access control policy guidance. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. This document discusses the secure firewall's access. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices This document discusses the secure firewall's access control feature's key components and configuration. Best practices for access control rules. Consider these common practices and. The access control policy is your primary tool for protecting your internal networks and. Access control rules provide a granular method of handling network traffic. Cisco secure firewall access control policy guidance. Rules in an access. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
7. Cisco FTD Prefilter Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. This document discusses the secure firewall's access control feature's key components and configuration. Access control —use the access control policy to determine which. Cisco Ftd Access Control Policy Best Practices.
From www.resmo.com
9 Access Control Best Practices Resmo Cisco Ftd Access Control Policy Best Practices General best practices for access control. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. The access control policy is your primary tool for protecting your internal networks and. Best practices for. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
5. Cisco FTD Application Control Policy RAYKA (are you a network Cisco Ftd Access Control Policy Best Practices Best practices for access control rules. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Access control —use the access control policy to determine which connections are allowed on the network. Best practices for access control.. Cisco Ftd Access Control Policy Best Practices.
From community.cisco.com
Cisco FTD Access control, Identity and NAT policy sequence Cisco Cisco Ftd Access Control Policy Best Practices Access control rules provide a granular method of handling network traffic. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Best practices for access control rules. Access control —use the access control policy to determine which connections are allowed on the network. Cisco firepower threat defense (ftd) policies help. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices General best practices for access control. Consider these common practices and. Cisco secure firewall access control policy guidance. Best practices for access control. Best practices for access control rules. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. The following topics explain some common tasks you might want to. Cisco Ftd Access Control Policy Best Practices.
From community.cisco.com
Disable Security Intelligence on FTD Access Control Policy Cisco Cisco Ftd Access Control Policy Best Practices Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. The access control policy is your primary tool for protecting your internal networks and. Best practices for access control rules. Review the following requirements and general. Access control rules provide a granular method of handling network traffic. Best practices for access control. General best. Cisco Ftd Access Control Policy Best Practices.
From securityzone.vn
Cisco FTD [LAB2] Cấu hình Access Control Policy và NAT trên Cisco Cisco Ftd Access Control Policy Best Practices Consider these common practices and. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Access control rules provide a granular method of handling network traffic. Best practices for access control rules. The access control policy is your primary tool for protecting your internal networks and. Review the following requirements. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. The access control policy is your primary tool for protecting your internal networks and. Best practices for access control. Cisco firepower threat defense. Cisco Ftd Access Control Policy Best Practices.
From community.cisco.com
Disable Security Intelligence on FTD Access Control Policy Cisco Cisco Ftd Access Control Policy Best Practices Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Cisco secure firewall access control policy guidance. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better. Cisco Ftd Access Control Policy Best Practices.
From www.youtube.com
How to create an Access Control Policy with URL Filtering YouTube Cisco Ftd Access Control Policy Best Practices The access control policy is your primary tool for protecting your internal networks and. Access control —use the access control policy to determine which connections are allowed on the network. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. The following topics explain some common tasks you might want. Cisco Ftd Access Control Policy Best Practices.
From community.cisco.com
Cisco FTD 1140 Dynamic Access Policy endpoint check Cisco Community Cisco Ftd Access Control Policy Best Practices Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Review the following requirements and general. This document discusses the secure firewall's access control feature's key components and configuration. Access control —use the access. Cisco Ftd Access Control Policy Best Practices.
From www.youtube.com
4. Cisco FTD Access Control Policy YouTube Cisco Ftd Access Control Policy Best Practices Review the following requirements and general. Access control —use the access control policy to determine which connections are allowed on the network. Access control rules provide a granular method of handling network traffic. This document discusses the secure firewall's access control feature's key components and configuration. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
5. Cisco FTD Application Control Policy RAYKA (are you a network Cisco Ftd Access Control Policy Best Practices The access control policy is your primary tool for protecting your internal networks and. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. This document discusses the secure firewall's access control feature's key components and configuration. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns,. Cisco Ftd Access Control Policy Best Practices.
From www.youtube.com
Introduction to Access Control Policy on FTD Connection flow Part 2 Cisco Ftd Access Control Policy Best Practices Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Consider these common practices and. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Best practices for access control. Cisco secure firewall access control policy guidance. This document discusses the secure firewall's. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices This document discusses the secure firewall's access control feature's key components and configuration. Access control —use the access control policy to determine which connections are allowed on the network. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Consider these common practices and. Cisco firepower threat defense (ftd) policies help you flag. Cisco Ftd Access Control Policy Best Practices.
From community.cisco.com
FTD AnyConnect VPN and Prefilter and/or Bypass Access Control Policy Cisco Ftd Access Control Policy Best Practices Review the following requirements and general. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. Cisco secure firewall access control policy guidance. General best practices for access control. Access control rules provide a granular method of handling network traffic. This document discusses the secure firewall's access control feature's key. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices General best practices for access control. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Consider these common practices and. Best practices for access control. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. Use an access control policy's advanced settings. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices The access control policy is your primary tool for protecting your internal networks and. Consider these common practices and. Best practices for access control rules. General best practices for access control. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Cisco secure firewall access control policy guidance. Review the. Cisco Ftd Access Control Policy Best Practices.
From www.thenetworkdna.com
Security Cisco ASA Vs Cisco FTD The Network DNA Cisco Ftd Access Control Policy Best Practices Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Review the following requirements and general. Access control rules provide a granular method of handling network traffic. Consider these common practices and. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control. Cisco Ftd Access Control Policy Best Practices.
From www.informit.com
Cisco Firepower Threat Defense (FTD) Configuration and Troubleshooting Cisco Ftd Access Control Policy Best Practices Review the following requirements and general. Consider these common practices and. General best practices for access control. Cisco secure firewall access control policy guidance. The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices The following topics explain some common tasks you might want to accomplish with ftd using the fdm. Best practices for access control rules. General best practices for access control. The access control policy is your primary tool for protecting your internal networks and. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Use. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
1. Cisco FTD Overview and Features RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices Access control rules provide a granular method of handling network traffic. Access control —use the access control policy to determine which connections are allowed on the network. General best practices for access control. This document discusses the secure firewall's access control feature's key components and configuration. Rules in an access control policy are numbered, starting at 1, including rules inherited. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
5. Cisco FTD Application Control Policy RAYKA (are you a network Cisco Ftd Access Control Policy Best Practices Access control —use the access control policy to determine which connections are allowed on the network. Best practices for access control. Review the following requirements and general. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Consider these common practices and. The following topics explain some common tasks you might want to accomplish. Cisco Ftd Access Control Policy Best Practices.
From www.cisco.com
Configure Management Access to FTD (HTTPS and SSH) via FMC Cisco Cisco Ftd Access Control Policy Best Practices Best practices for access control rules. General best practices for access control. Access control —use the access control policy to determine which connections are allowed on the network. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Consider these common practices and. Use an access control policy's advanced settings to associate one of. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
5. Cisco FTD Application Control Policy RAYKA (are you a network Cisco Ftd Access Control Policy Best Practices Cisco secure firewall access control policy guidance. Review the following requirements and general. Best practices for access control. Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. General best practices for access control. Access control rules provide a granular method of handling network traffic. Consider these common practices and.. Cisco Ftd Access Control Policy Best Practices.
From www.youtube.com
How to configure Cisco FTD 4100 Management IP, Ssh, Https from FXOS CLI Cisco Ftd Access Control Policy Best Practices Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. Access control rules provide a granular method of handling network traffic. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. Access control —use the access control policy to determine which connections are allowed. Cisco Ftd Access Control Policy Best Practices.
From dokumen.tips
(PDF) Getting Started with Access Control Policies · 43 Cisco Ftd Access Control Policy Best Practices Review the following requirements and general. Cisco firepower threat defense (ftd) policies help you flag specific network trafic patterns, create alerts and better control your network. The access control policy is your primary tool for protecting your internal networks and. Access control rules provide a granular method of handling network traffic. Rules in an access control policy are numbered, starting. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices Best practices for access control rules. Access control rules provide a granular method of handling network traffic. Consider these common practices and. Review the following requirements and general. Access control —use the access control policy to determine which connections are allowed on the network. The access control policy is your primary tool for protecting your internal networks and. This document. Cisco Ftd Access Control Policy Best Practices.
From ciscocustomer.lookbookhq.com
NGFW FTD Policy Management Common Practices Cisco Ftd Access Control Policy Best Practices Best practices for access control rules. Rules in an access control policy are numbered, starting at 1, including rules inherited from ancestor. General best practices for access control. Cisco secure firewall access control policy guidance. Review the following requirements and general. Access control —use the access control policy to determine which connections are allowed on the network. Use an access. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA Cisco Ftd Access Control Policy Best Practices Best practices for access control. Access control rules provide a granular method of handling network traffic. Consider these common practices and. General best practices for access control. Access control —use the access control policy to determine which connections are allowed on the network. Review the following requirements and general. Best practices for access control rules. Cisco secure firewall access control. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
4. Cisco FTD Access Control Policy RAYKA (are you a network engineer?) Cisco Ftd Access Control Policy Best Practices Use an access control policy's advanced settings to associate one of each of the following subpolicies with the access control. Review the following requirements and general. Best practices for access control rules. Access control —use the access control policy to determine which connections are allowed on the network. Cisco firepower threat defense (ftd) policies help you flag specific network trafic. Cisco Ftd Access Control Policy Best Practices.
From rayka-co.com
5. Cisco FTD Application Control Policy RAYKA (are you a network Cisco Ftd Access Control Policy Best Practices General best practices for access control. The access control policy is your primary tool for protecting your internal networks and. Review the following requirements and general. This document discusses the secure firewall's access control feature's key components and configuration. Access control rules provide a granular method of handling network traffic. Cisco secure firewall access control policy guidance. Access control —use. Cisco Ftd Access Control Policy Best Practices.