Threat Modeling As Code . however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. Omer levi hevroni has a very interesting post exploring ways to represent threat. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. threat modeling as code. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. Describe your system using oo syntax (object.property = value). this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically.
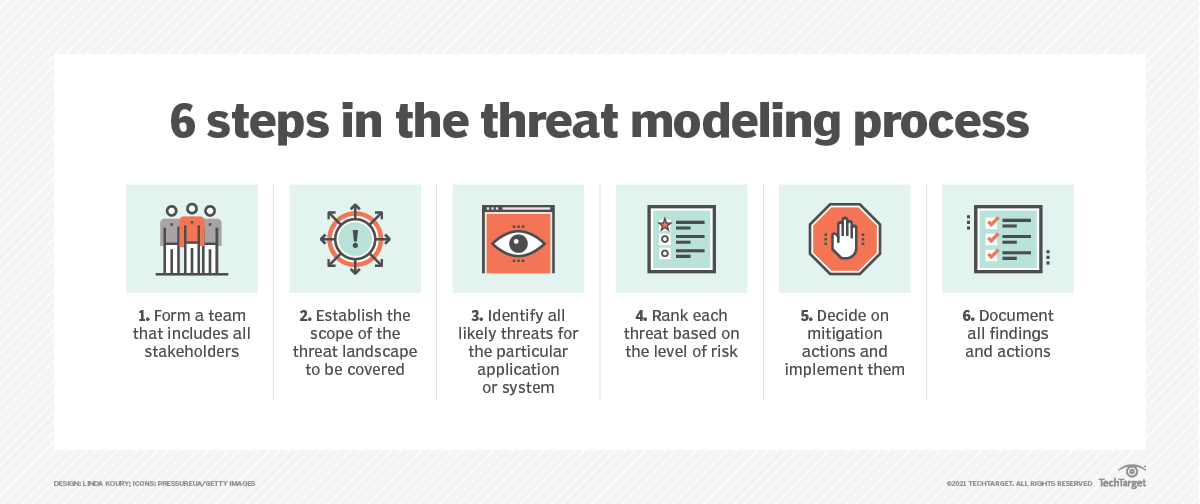
from www.techtarget.com
there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. Omer levi hevroni has a very interesting post exploring ways to represent threat. threat modeling as code. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. Describe your system using oo syntax (object.property = value). this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically.
What is threat modeling?
Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. Omer levi hevroni has a very interesting post exploring ways to represent threat. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. threat modeling as code. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. Describe your system using oo syntax (object.property = value). however, we should iterate into a threat modeling with code to interpret and process information to identify threats and.
From speakerdeck.com
Agile Threat ModelingasCode Speaker Deck Threat Modeling As Code there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. Omer levi hevroni has a very interesting post exploring ways to represent threat. threat modeling as code. you then overlay your threat model on top by adding few more lines of code of your. Threat Modeling As Code.
From www.guardrails.io
A Guide to Effective Threat Modeling GuardRails Threat Modeling As Code you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. threat modeling as code. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. this is achieved by having developers. Threat Modeling As Code.
From threat-modeling.com
Threat Modeling with STRIDE using a Threat Modeling Tool Threat Modeling As Code Omer levi hevroni has a very interesting post exploring ways to represent threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. threat. Threat Modeling As Code.
From subscription.packtpub.com
Threat modeling tools Network Vulnerability Assessment Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. there are only a few. Threat Modeling As Code.
From devops.com
Threat Modeling The Why, How, When and Which Tools Threat Modeling As Code threat modeling as code. Omer levi hevroni has a very interesting post exploring ways to represent threat. Describe your system using oo syntax (object.property = value). there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. you then overlay your threat model on top by adding few more. Threat Modeling As Code.
From medium.com
Threat Modeling The Practical Way codelogicx Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. threat modeling as code. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. Describe your system using oo syntax (object.property = value). Omer. Threat Modeling As Code.
From speakerdeck.com
Agile Threat ModelingasCode Speaker Deck Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. threat modeling as code. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. there are only a few ways to seamlessly turn devops into. Threat Modeling As Code.
From www.slcyber.io
Threat Models 5 Steps To Building A Threat Model SL Cyber Threat Modeling As Code you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. there are multiple solutions out there to. Threat Modeling As Code.
From threat-modeling.com
STRIDE Threat Modeling in DevOps A Perfect Fit Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. Omer levi hevroni has a very interesting post exploring ways to represent threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. there. Threat Modeling As Code.
From threat-modeling.com
Threat Modeling Tool Threat Modeling As Code there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. you then. Threat Modeling As Code.
From henrikparkkinen.com
THREAT MODELING MADE SIMPLE Henrik Parkkinen Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. however, we should iterate into a threat modeling with code to interpret and process. Threat Modeling As Code.
From www.nuspire.com
Threat Modeling Cybersecurity Consulting Nuspire Threat Modeling As Code Omer levi hevroni has a very interesting post exploring ways to represent threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. however, we should iterate into a threat modeling with code to interpret and process information to identify threats. Threat Modeling As Code.
From info.threatmodeler.com
Toward Threat Modeling as Code Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. Describe your system using oo syntax (object.property = value). Omer levi hevroni has a very interesting post exploring ways to represent threat. Get. Threat Modeling As Code.
From speakerdeck.com
Agile Threat ModelingasCode Speaker Deck Threat Modeling As Code however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. threat modeling as code. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. there are only a few ways to seamlessly. Threat Modeling As Code.
From www.harness.io
The Threat Modeling Process Harness Threat Modeling As Code Omer levi hevroni has a very interesting post exploring ways to represent threat. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. you then overlay your threat model on top by adding few more lines of code of your own that capture. Threat Modeling As Code.
From www.dts-solution.com
Threat Modelling Network and Cyber Security Solutions and Services, Testing in Threat Modeling As Code there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. there are. Threat Modeling As Code.
From www.omerlh.info
Threat Modeling as Code Omer Levi Hevroni Threat Modeling As Code however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. Omer levi hevroni has a very interesting post exploring ways to represent threat. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. . Threat Modeling As Code.
From www.techtarget.com
What is threat modeling? Threat Modeling As Code Omer levi hevroni has a very interesting post exploring ways to represent threat. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and. Threat Modeling As Code.
From www.practical-devsecops.com
Top 5 Threat Modeling Methodologies Practical DevSecOps Threat Modeling As Code threat modeling as code. Omer levi hevroni has a very interesting post exploring ways to represent threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. however, we should iterate into a threat modeling with code to interpret and. Threat Modeling As Code.
From www.youtube.com
Live Code Session ThreatPlaybook v3 ThreatModelingasCode YouTube Threat Modeling As Code threat modeling as code. Omer levi hevroni has a very interesting post exploring ways to represent threat. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by. Threat Modeling As Code.
From www.youtube.com
Threat ModelingasCode & Automation for DevSecOps wins by Abhay Bhargav YouTube Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. this is achieved by having developers and security engineers write threat specifications alongside. Threat Modeling As Code.
From www.slideserve.com
PPT Threat Modeling PowerPoint Presentation, free download ID468625 Threat Modeling As Code you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. threat modeling as code. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. Describe your system using oo syntax (object.property. Threat Modeling As Code.
From www.youtube.com
we45 inarThreat Modeling as Code with Threat Playbook YouTube Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. Describe your system using oo syntax (object.property = value). threat modeling as code.. Threat Modeling As Code.
From www.youtube.com
📣Threat Models in organization & how should they be delivered? Threat Modeling as Code Threat Modeling As Code Describe your system using oo syntax (object.property = value). there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. however, we should iterate into a. Threat Modeling As Code.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. Omer levi hevroni has a very interesting post exploring ways to represent threat. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. Get your dev/architect to use your. Threat Modeling As Code.
From www.memcyco.com
Examples of Threat Modeling That Create Secure Design Patterns Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. Describe your system using oo syntax (object.property = value). threat modeling as code. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. . Threat Modeling As Code.
From medium.com
Threat Modeling — A Practical Guide Part I by PRASAD Nov, 2023 Medium Threat Modeling As Code this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. Describe your system using oo syntax (object.property = value). Get your dev/architect to use your threat model embededed template. Threat Modeling As Code.
From threat-modeling.com
Threat Modeling Terminology Threat Modeling As Code there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. this is achieved by having developers and security engineers write threat. Threat Modeling As Code.
From www.geeksforgeeks.org
Threat Modelling Threat Modeling As Code however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. this is achieved by having developers and security engineers write threat specifications alongside code, then dynamically. there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. there are. Threat Modeling As Code.
From offensive360.com
How to create a threat model Offensive 360 O360 Threat Modeling As Code you then overlay your threat model on top by adding few more lines of code of your own that capture your threat model q&as, risk and recommendations. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. threat modeling as code. . Threat Modeling As Code.
From henrikparkkinen.com
THREAT MODELING MADE SIMPLE Henrik Parkkinen Threat Modeling As Code there are only a few ways to seamlessly turn devops into devsecops today and one of the very best is by incorporating threat. Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. Describe your system using oo syntax (object.property = value). . Threat Modeling As Code.
From threat-modeling.com
STRIDE Threat Modeling Example for Better Understanding and Learning Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. however, we should iterate into a threat modeling with code to interpret and process information to identify threats and. you then overlay your threat model on top by adding few more lines. Threat Modeling As Code.
From www.slcyber.io
Threat Models 5 Steps To Building A Threat Model SL Cyber Threat Modeling As Code Get your dev/architect to use your threat model embededed template plantuml to draw their architecture diagrams, answer your questions and generate the initial threat model themselves. Describe your system using oo syntax (object.property = value). there are multiple solutions out there to build threat model such as, microsoft threat modeling tool (mtmt), owasp threat. however, we should iterate. Threat Modeling As Code.