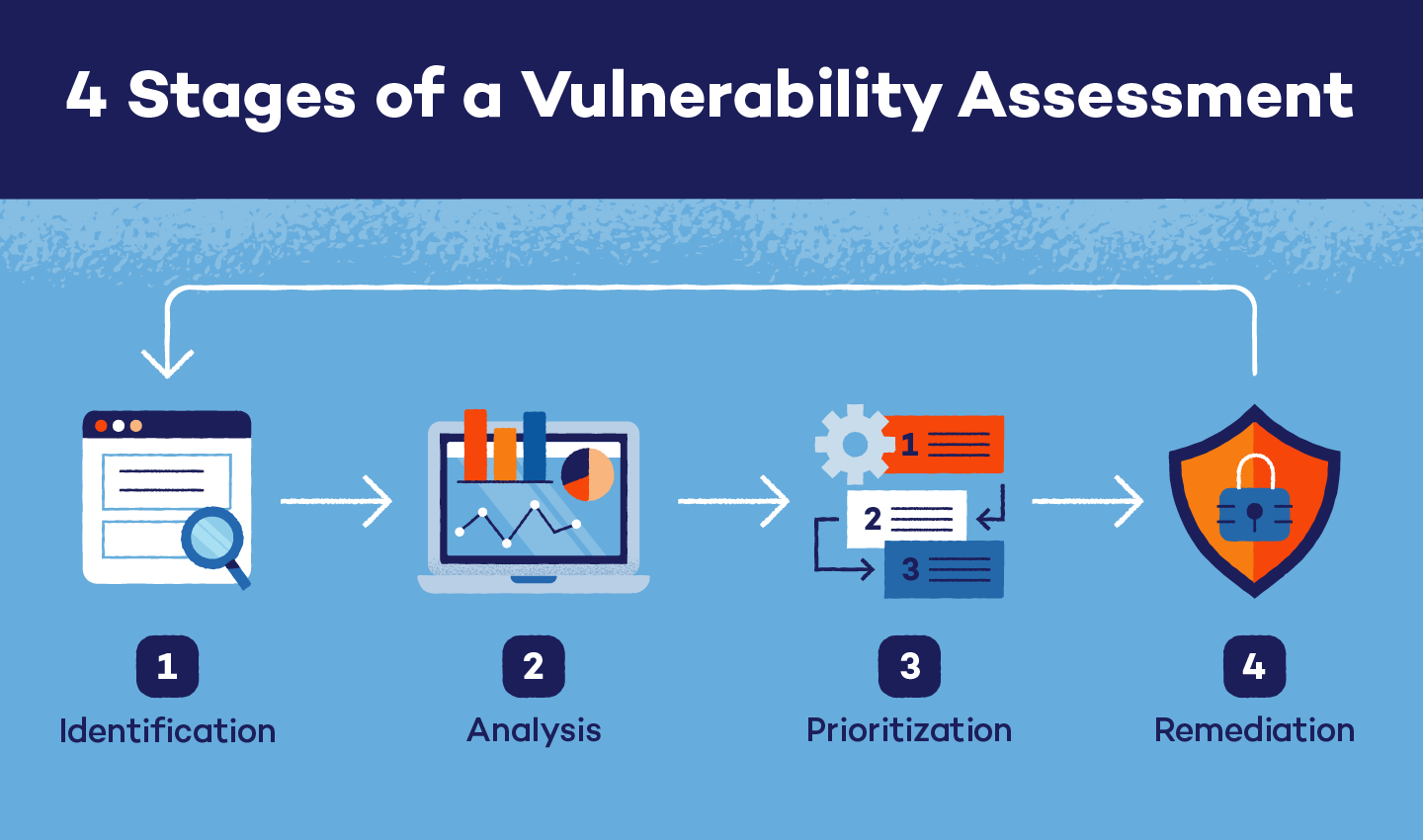
Vulnerability Management Program Risks . Yet, as indicated by the wave of massive data breaches and. Prioritize vulnerabilities based on risk. vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. It empowers security teams to prioritize. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a robust vulnerability management program can help organizations:
from www.pandasecurity.com
Prioritize vulnerabilities based on risk. It empowers security teams to prioritize. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. vulnerability management is one of the most effective means of controlling cybersecurity risk.
What is a Vulnerability Assessment? Panda Security
Vulnerability Management Program Risks a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust vulnerability management program can help organizations: a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. It empowers security teams to prioritize. vulnerability management is one of the most effective means of controlling cybersecurity risk. Prioritize vulnerabilities based on risk.
From securityboulevard.com
Building a Vulnerability Management Program Key Components and Tips to Get Started Security Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust. Vulnerability Management Program Risks.
From www.infotech.com
Implement RiskBased Vulnerability Management InfoTech Research Group Vulnerability Management Program Risks a robust vulnerability management program can help organizations: vulnerability management is one of the most effective means of controlling cybersecurity risk. Yet, as indicated by the wave of massive data breaches and. Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address.. Vulnerability Management Program Risks.
From learn.microsoft.com
Microsoft Defender Vulnerability Management Microsoft Learn Vulnerability Management Program Risks It empowers security teams to prioritize. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities based on risk. Yet, as indicated by the wave of massive data breaches and. a robust vulnerability management program can help organizations: a strong vulnerability management program uses. Vulnerability Management Program Risks.
From e-janco.com
Threat Vulnerability Assessment Tool Vulnerability Management Program Risks vulnerability management is one of the most effective means of controlling cybersecurity risk. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. a robust vulnerability management program can help organizations: It empowers security teams. Vulnerability Management Program Risks.
From bleuwire.com
How to Have an Effective Vulnerability Management Program Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a robust vulnerability management program can help organizations: vulnerability management is one of the most effective means of controlling cybersecurity risk. Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and. Vulnerability Management Program Risks.
From www.g2.com
What Is Vulnerability Management? Why Does It Matter? Vulnerability Management Program Risks a robust vulnerability management program can help organizations: vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. Yet, as indicated by the wave of massive data breaches and. the objective of this. Vulnerability Management Program Risks.
From www.rapid7.com
Top Rated Vulnerability Management Software Rapid7 Vulnerability Management Program Risks vulnerability management is one of the most effective means of controlling cybersecurity risk. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities based on risk. Yet, as indicated by the wave of massive data breaches. Vulnerability Management Program Risks.
From brightsec.com
Vulnerability Management Lifecycle, Tools, and Best Practices Vulnerability Management Program Risks It empowers security teams to prioritize. Yet, as indicated by the wave of massive data breaches and. a robust vulnerability management program can help organizations: a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information. Vulnerability Management Program Risks.
From avatao.com
Understanding the importance of vulnerability management Avatao Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. It. Vulnerability Management Program Risks.
From wp-blog.getastra.dev
Risk Assessment VS Vulnerability Assessment A Detailed Discussion Vulnerability Management Program Risks It empowers security teams to prioritize. Prioritize vulnerabilities based on risk. vulnerability management is one of the most effective means of controlling cybersecurity risk. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a strong vulnerability management program uses threat intelligence and knowledge of it. Vulnerability Management Program Risks.
From cediahwk.blob.core.windows.net
Vulnerability Management Tracking Tools at Charles Loggins blog Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. Yet, as indicated by the wave of massive data breaches and. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. . Vulnerability Management Program Risks.
From www.crowdstrike.com
What is Vulnerability Management? CrowdStrike Vulnerability Management Program Risks a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust vulnerability management program can help organizations: vulnerability management is one of the most effective means of controlling cybersecurity risk. Yet, as indicated by the wave of massive data breaches and. the objective of this. Vulnerability Management Program Risks.
From www.sample-templatess123.com
Threat Vulnerability Risk Assessment Template Sample Templates Sample Templates Vulnerability Management Program Risks Yet, as indicated by the wave of massive data breaches and. vulnerability management is one of the most effective means of controlling cybersecurity risk. It empowers security teams to prioritize. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust vulnerability management program can help. Vulnerability Management Program Risks.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying Vulnerabilities in your Business Vulnerability Management Program Risks a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. vulnerability management is one of the most effective means of controlling cybersecurity risk. Prioritize vulnerabilities based. Vulnerability Management Program Risks.
From toolkit.climate.gov
FHWA Vulnerability Assessment Framework U.S. Climate Resilience Toolkit Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a robust vulnerability management program can help organizations: vulnerability management. Vulnerability Management Program Risks.
From blog.teamascend.com
The Five Stages of Vulnerability Management Vulnerability Management Program Risks It empowers security teams to prioritize. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities. Vulnerability Management Program Risks.
From s4applications.uk
Vulnerability Management Programme And Dashboards S4 Applications Vulnerability Management Program Risks a robust vulnerability management program can help organizations: Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. vulnerability management. Vulnerability Management Program Risks.
From avleonov.com
Remediation capabilities of Vulnerability Management products Alexander V. Leonov Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. vulnerability management is one of the most effective means of controlling cybersecurity risk. It empowers security teams to prioritize. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. Yet, as indicated by the wave of massive data breaches and. the objective. Vulnerability Management Program Risks.
From www.alertmedia.com
Threat and Vulnerability Assessment [+ Free Template] Vulnerability Management Program Risks a robust vulnerability management program can help organizations: It empowers security teams to prioritize. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities based on risk. Yet, as indicated by the wave of massive data breaches and. a strong vulnerability management program uses. Vulnerability Management Program Risks.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine Vulnerability Manager Plus Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. vulnerability management is one of the most effective means of controlling cybersecurity risk. Prioritize vulnerabilities based on risk. a robust vulnerability management program can help. Vulnerability Management Program Risks.
From www.slideteam.net
Threat Vulnerability Dashboard Information Security Risk Management Program Presentation Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a robust vulnerability management program can help organizations: vulnerability management is one of the most effective means of controlling cybersecurity risk. It empowers security teams to prioritize. Yet, as indicated by the wave of massive data. Vulnerability Management Program Risks.
From www.qualys.com
What is VMDR (Vulnerability Management, Detection and Response)? Qualys Vulnerability Management Program Risks a robust vulnerability management program can help organizations: Prioritize vulnerabilities based on risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. It empowers security. Vulnerability Management Program Risks.
From www.crowdstrike.com
What is Vulnerability Management? CrowdStrike Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a robust vulnerability management program can help organizations: Yet, as indicated by the wave of massive data breaches and. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize. Vulnerability Management Program Risks.
From www.lanworks.com
Vulnerability Assessment Lanworks Vulnerability Management Program Risks Yet, as indicated by the wave of massive data breaches and. a robust vulnerability management program can help organizations: a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. vulnerability management is one of the most effective means of controlling cybersecurity risk. the objective of this. Vulnerability Management Program Risks.
From www.compasscyber.com
A Risk Manager's Approach to Cyber Security Compass Cyber Security Vulnerability Management Program Risks It empowers security teams to prioritize. Prioritize vulnerabilities based on risk. vulnerability management is one of the most effective means of controlling cybersecurity risk. a robust vulnerability management program can help organizations: Yet, as indicated by the wave of massive data breaches and. a strong vulnerability management program uses threat intelligence and knowledge of it and business. Vulnerability Management Program Risks.
From threatpost.com
Vulnerabilities are Beyond What You Think Threatpost Vulnerability Management Program Risks the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. Yet, as indicated. Vulnerability Management Program Risks.
From www.balbix.com
Vulnerability Management Program How to Built It? Balbix Vulnerability Management Program Risks It empowers security teams to prioritize. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities based on risk. vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability. Vulnerability Management Program Risks.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security Vulnerability Management Program Risks Yet, as indicated by the wave of massive data breaches and. It empowers security teams to prioritize. Prioritize vulnerabilities based on risk. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations. Vulnerability Management Program Risks.
From www.teimouri.net
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) Part 1 Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. Yet, as indicated by the wave of massive data breaches and. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. It empowers security teams to prioritize. a robust vulnerability management program can help organizations: vulnerability management is one of the most. Vulnerability Management Program Risks.
From www.rootshellsecurity.net
Vulnerability Management Process Flow Chart Rootshell Vulnerability Management Program Risks vulnerability management is one of the most effective means of controlling cybersecurity risk. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. Prioritize vulnerabilities based on risk. It empowers security teams to prioritize. a robust vulnerability management program can help organizations: Yet, as indicated by the. Vulnerability Management Program Risks.
From blog.invgate.com
Vulnerability Management Processes and tools Vulnerability Management Program Risks a robust vulnerability management program can help organizations: Prioritize vulnerabilities based on risk. It empowers security teams to prioritize. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by the wave of massive data breaches and. vulnerability management is one of the. Vulnerability Management Program Risks.
From cybeready.com
8 Tips to Master Your Vulnerability Management Program Vulnerability Management Program Risks Yet, as indicated by the wave of massive data breaches and. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Prioritize vulnerabilities based on risk. It empowers security teams to prioritize. vulnerability management is one of the. Vulnerability Management Program Risks.
From www.slideteam.net
Vulnerability Management Lifecycle Risk Security Reporting Monitoring Presentation PowerPoint Vulnerability Management Program Risks Prioritize vulnerabilities based on risk. It empowers security teams to prioritize. vulnerability management is one of the most effective means of controlling cybersecurity risk. a robust vulnerability management program can help organizations: the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. Yet, as indicated by. Vulnerability Management Program Risks.
From www.rapid7.com
Building a Comprehensive Vulnerability Management Program Rapid7 Blog Vulnerability Management Program Risks a robust vulnerability management program can help organizations: It empowers security teams to prioritize. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address. vulnerability management is one of the most effective means of controlling cybersecurity risk. Prioritize vulnerabilities based on risk. the objective of this. Vulnerability Management Program Risks.
From www.esecforte.com
Vulnerability Assessment Scanning Tools List 2018 eSecForte Vulnerability Management Program Risks Yet, as indicated by the wave of massive data breaches and. vulnerability management is one of the most effective means of controlling cybersecurity risk. It empowers security teams to prioritize. Prioritize vulnerabilities based on risk. the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable. a. Vulnerability Management Program Risks.