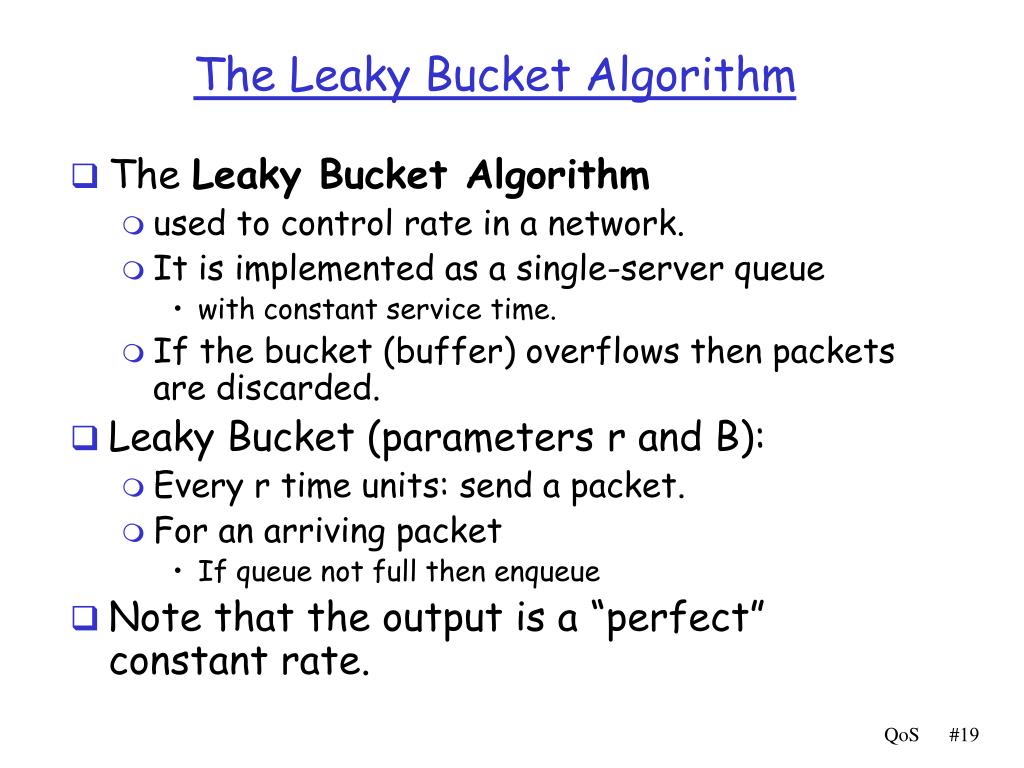
Leaky Bucket Rate Limit Algorithm . Fixed window rate limiting works by. How to choose the right algorithm? By controlling the rate at which data enters a system, it prevents sudden spikes in. If the bucket (buffer) overflows, new requests are discarded. One of the primary applications of the leaky bucket algorithm is rate limiting. Different algorithms can be used to implement rate limiting. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Let's review the most common types in this section. Without the leaky bucket, the. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s.
from www.slideserve.com
Let's review the most common types in this section. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Different algorithms can be used to implement rate limiting. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. One of the primary applications of the leaky bucket algorithm is rate limiting. Fixed window rate limiting works by. Without the leaky bucket, the. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. By controlling the rate at which data enters a system, it prevents sudden spikes in. How to choose the right algorithm?
PPT Quality of Service Support PowerPoint Presentation, free download
Leaky Bucket Rate Limit Algorithm The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Let's review the most common types in this section. By controlling the rate at which data enters a system, it prevents sudden spikes in. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. If the bucket (buffer) overflows, new requests are discarded. How to choose the right algorithm? Without the leaky bucket, the. One of the primary applications of the leaky bucket algorithm is rate limiting. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Rate Limit Algorithm Without the leaky bucket, the. How to choose the right algorithm? Let's review the most common types in this section. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. If the bucket (buffer) overflows, new requests are discarded. By controlling the rate at which data enters a. Leaky Bucket Rate Limit Algorithm.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Rate Limit Algorithm Without the leaky bucket, the. One of the primary applications of the leaky bucket algorithm is rate limiting. If the bucket (buffer) overflows, new requests are discarded. How to choose the right algorithm? Let's review the most common types in this section. Fixed window rate limiting works by. Different algorithms can be used to implement rate limiting. Using the leaky. Leaky Bucket Rate Limit Algorithm.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Rate Limit Algorithm One of the primary applications of the leaky bucket algorithm is rate limiting. If the bucket (buffer) overflows, new requests are discarded. Different algorithms can be used to implement rate limiting. By controlling the rate at which data enters a system, it prevents sudden spikes in. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at. Leaky Bucket Rate Limit Algorithm.
From whalefallnotes.blog
Rate Limit Algorithms 鯨落筆記 Whale Fall Notes Leaky Bucket Rate Limit Algorithm Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. How to choose the right algorithm? The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Let's review the most common types in this section. Without the leaky bucket, the. If. Leaky Bucket Rate Limit Algorithm.
From blog.cloudflare.com
How we built rate limiting capable of scaling to millions of domains Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. One of the primary applications of the leaky bucket algorithm is rate limiting. Fixed window rate limiting works by. Using the leaky bucket, requests can come in at different rates while the server processes. Leaky Bucket Rate Limit Algorithm.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Rate Limit Algorithm The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by. How to choose the right algorithm? The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate.. Leaky Bucket Rate Limit Algorithm.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Rate Limit Algorithm How to choose the right algorithm? If the bucket (buffer) overflows, new requests are discarded. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. One of the primary applications of the leaky bucket algorithm is rate limiting. Let's review the most common types in this section. The. Leaky Bucket Rate Limit Algorithm.
From hechao.li
Rate Limiting Part 1 Leaky Bucket Rate Limit Algorithm By controlling the rate at which data enters a system, it prevents sudden spikes in. Let's review the most common types in this section. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Different algorithms can be used to implement rate limiting. How to choose the right algorithm? Fixed window rate limiting. Leaky Bucket Rate Limit Algorithm.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by. Without the leaky bucket, the. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Let's. Leaky Bucket Rate Limit Algorithm.
From github.com
GitHub Shareed2k/http_limiter http_limiter using redis as store for Leaky Bucket Rate Limit Algorithm The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Different algorithms can be used to implement rate limiting. By controlling the rate at which data enters a system, it prevents sudden spikes in. Let's review the most common types in this section. One of the primary applications. Leaky Bucket Rate Limit Algorithm.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Rate Limit Algorithm Fixed window rate limiting works by. Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. How to choose the right algorithm? By controlling the rate at which data enters a system, it prevents sudden spikes in. Without the leaky bucket, the. The leaky bucket algorithm metaphorically allows requests to drip out. Leaky Bucket Rate Limit Algorithm.
From lowleveldesign.io
Design a Distributed Scalable API Rate Limiter Leaky Bucket Rate Limit Algorithm The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Without the leaky bucket, the. One of the primary applications of the leaky bucket algorithm is rate limiting. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. If the bucket. Leaky Bucket Rate Limit Algorithm.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. By controlling the rate at which data enters a system, it prevents sudden spikes in. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Let's review the most common types in this section. Fixed window rate limiting works. Leaky Bucket Rate Limit Algorithm.
From dev.to
Rate Limiter in System Design. Part 2 Commonly Used Algorithms DEV Leaky Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. One of the primary applications of the leaky bucket algorithm is rate limiting. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. If the bucket (buffer) overflows, new requests are discarded. By controlling the rate at which data. Leaky Bucket Rate Limit Algorithm.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Rate Limit Algorithm One of the primary applications of the leaky bucket algorithm is rate limiting. Without the leaky bucket, the. How to choose the right algorithm? The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works. Leaky Bucket Rate Limit Algorithm.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Rate Limit Algorithm Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Fixed window rate limiting works by. One of the primary applications of the leaky bucket algorithm is rate limiting. If. Leaky Bucket Rate Limit Algorithm.
From blog.bytebytego.com
Rate Limiting Fundamentals by Alex Xu Leaky Bucket Rate Limit Algorithm Fixed window rate limiting works by. How to choose the right algorithm? The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Let's review the most common types in this section. If the bucket (buffer) overflows, new requests are discarded. Different algorithms can be used to implement rate. Leaky Bucket Rate Limit Algorithm.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Without the leaky bucket, the. Different algorithms. Leaky Bucket Rate Limit Algorithm.
From stackoverflow.com
ruby Implementing a "leaky bucket"like algorithm for message queues Leaky Bucket Rate Limit Algorithm The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Without the leaky bucket, the. By controlling the rate at which data enters a system, it prevents sudden spikes in. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by. If the bucket. Leaky Bucket Rate Limit Algorithm.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Rate Limit Algorithm Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. Without the leaky bucket, the. How to choose the right algorithm? The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. The leaky bucket algorithm metaphorically allows requests to drip. Leaky Bucket Rate Limit Algorithm.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Rate Limit Algorithm By controlling the rate at which data enters a system, it prevents sudden spikes in. One of the primary applications of the leaky bucket algorithm is rate limiting. If the bucket (buffer) overflows, new requests are discarded. How to choose the right algorithm? Fixed window rate limiting works by. The leaky bucket smooths out the traffic by sending out data. Leaky Bucket Rate Limit Algorithm.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. By controlling the rate at which data enters a system, it prevents sudden spikes in. Fixed window rate limiting works by. Let's review the most common types in this section. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10. Leaky Bucket Rate Limit Algorithm.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. How to choose the right algorithm? By controlling the rate at which data enters a system, it prevents sudden spikes in. Without the leaky bucket, the. Using the leaky bucket, requests can come in. Leaky Bucket Rate Limit Algorithm.
From slideplayer.com
ECE544 Communication NetworksII, Spring ppt download Leaky Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. Let's review the most common types in this section. One of the primary applications of the leaky bucket algorithm is rate limiting. How to choose the right algorithm? The. Leaky Bucket Rate Limit Algorithm.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Rate Limit Algorithm By controlling the rate at which data enters a system, it prevents sudden spikes in. If the bucket (buffer) overflows, new requests are discarded. One of the primary applications of the leaky bucket algorithm is rate limiting. Fixed window rate limiting works by. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate.. Leaky Bucket Rate Limit Algorithm.
From github.com
GitHub wambugucoder/SPRINGBOOTRATELIMITING A Springboot Leaky Bucket Rate Limit Algorithm How to choose the right algorithm? Fixed window rate limiting works by. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Different algorithms can be. Leaky Bucket Rate Limit Algorithm.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download Leaky Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. Without the leaky bucket, the. One of the primary applications of the leaky bucket algorithm is rate limiting. By controlling the rate at which data enters a system, it prevents sudden spikes in. How to choose the right algorithm? Using the leaky bucket, requests can come in at different rates while. Leaky Bucket Rate Limit Algorithm.
From infosecwriteups.com
Advanced Encryption Standard (AES) A Secure and Efficient Symmetric Leaky Bucket Rate Limit Algorithm Fixed window rate limiting works by. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. By controlling the rate at which data enters a system, it prevents sudden spikes in. Let's review the most common types in this section. If the bucket (buffer) overflows, new requests are. Leaky Bucket Rate Limit Algorithm.
From mozillazg.com
rate limiting 之 leaky bucket mozillazg's Blog Leaky Bucket Rate Limit Algorithm Without the leaky bucket, the. If the bucket (buffer) overflows, new requests are discarded. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. By controlling the rate at which data enters a system, it prevents sudden spikes in. How to choose the right algorithm? One of the. Leaky Bucket Rate Limit Algorithm.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Rate Limit Algorithm One of the primary applications of the leaky bucket algorithm is rate limiting. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. Without the leaky bucket, the. Fixed window rate limiting works by. How. Leaky Bucket Rate Limit Algorithm.
From systemsdesign.cloud
Design a Distributed Scalable API Rate Limiter Leaky Bucket Rate Limit Algorithm Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Without the leaky bucket, the. How to choose the right algorithm? The leaky bucket algorithm metaphorically. Leaky Bucket Rate Limit Algorithm.
From www.geeksforgeeks.org
How to Design a Rate Limiter API Learn System Design Leaky Bucket Rate Limit Algorithm The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. By controlling the rate at which data enters a system, it prevents sudden spikes in. Fixed window rate limiting works by. Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. How to choose the. Leaky Bucket Rate Limit Algorithm.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. How to choose the right algorithm? By controlling the rate at which data enters a system, it prevents sudden spikes in. The leaky bucket algorithm metaphorically allows requests to. Leaky Bucket Rate Limit Algorithm.
From www.researchgate.net
Selectivity of the conventional leaky bucket algorithm, the fuzzy leaky Leaky Bucket Rate Limit Algorithm Without the leaky bucket, the. The leaky bucket smooths out the traffic by sending out data at a rate of 3 mbps during the same 10 s. Let's review the most common types in this section. Different algorithms can be used to implement rate limiting. By controlling the rate at which data enters a system, it prevents sudden spikes in.. Leaky Bucket Rate Limit Algorithm.
From www.code4it.dev
Davide's Code and Architecture Notes 4 algorithms to implement Rate Leaky Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. Using the leaky bucket, requests can come in at different rates while the server processes them at a constant and predictable rate. How to choose the right algorithm? Without the leaky bucket, the. Let's review the most common types in this section. The leaky bucket smooths out the traffic by sending. Leaky Bucket Rate Limit Algorithm.