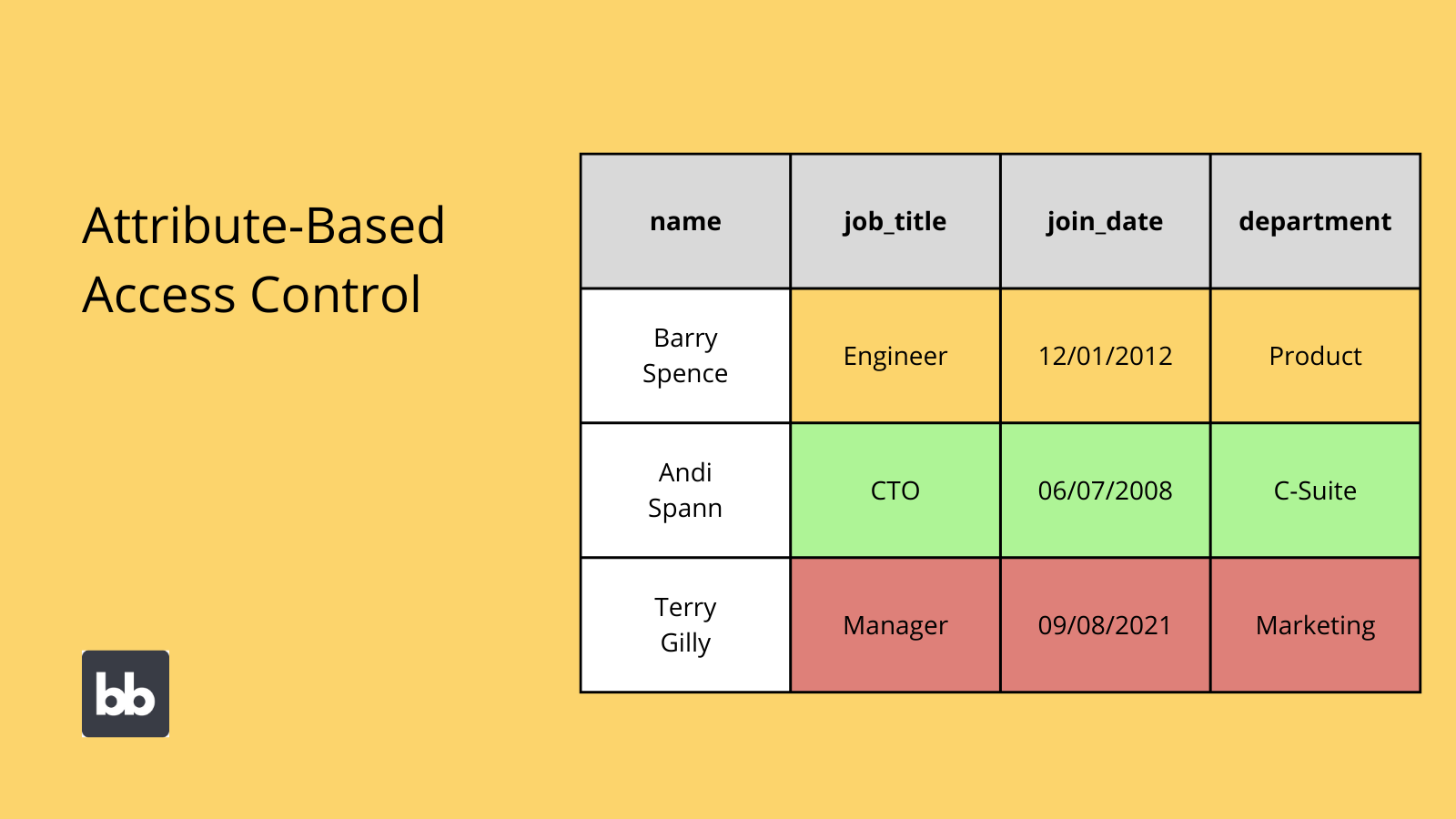
Access Control With Example . It involves assigning users or. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Examples include virtual private networks (vpns) and zero trust security solutions. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is a security policy that restricts access to places and/or data.
from budibase.com
Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust security solutions. It involves assigning users or. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture.
RoleBased Access Control Ultimate Guide
Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. It involves assigning users or. Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is a security policy that restricts access to places and/or data. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture.
From www.magnum.org.in
Description of Access Control System with Example Access Control With Example An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. It involves assigning users or. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is key in it and cybersecurity to minimize risks. Access Control With Example.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control With Example With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is a security policy that restricts access to places and/or data. Examples include. Access Control With Example.
From ashwinitpro.blogspot.com
Role Based Access Control (RBAC) (part 1 of 3) Access Control With Example Access control is a security policy that restricts access to places and/or data. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control. Access Control With Example.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Access Control With Example Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a security policy that restricts access to places and/or data. An. Access Control With Example.
From gotchasecurity.net
Access Control Systems for Apartment Buildings Gotcha Security Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. It involves assigning users or. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. An example of physical access control. Access Control With Example.
From cie-group.com
How to design an Access Control system Access Control With Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. It involves assigning users or. Access control defines the schemas that prescribe how subjects. Access Control With Example.
From www.dnsstuff.com
RBAC vs. ABAC Access Control What’s the Difference? DNSstuff Access Control With Example It involves assigning users or. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is a security. Access Control With Example.
From kentonbrothers.com
CPTED Part 2 Natural Surveillance and Natural Access Control Kenton Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. It involves assigning users or. An example of physical access. Access Control With Example.
From budibase.com
RoleBased Access Control Ultimate Guide Access Control With Example Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a security policy that restricts access to places and/or data. It involves assigning users or. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to. Access Control With Example.
From kintronics.com
Security Provided by Access Control Systems Kintronics Access Control With Example Access control is a security policy that restricts access to places and/or data. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Examples include virtual private networks (vpns) and zero trust security solutions. Access control defines the schemas that prescribe how subjects can interact. Access Control With Example.
From www.fingerprint-access-control.com
Office Building Access Control using Biometrics Fingerprint Access Access Control With Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. It involves assigning users or. Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security policy that restricts access to places and/or data. An example of physical access control can be allowing access. Access Control With Example.
From butterflymx.com
The 4 Types of Access Control Models Explained [+Examples] Access Control With Example Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Examples include virtual private networks (vpns) and zero trust security solutions. Access control is. Access Control With Example.
From www.youtube.com
Role Based Access Control YouTube Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security policy that restricts access to places and/or data. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. An example of physical access control can be allowing access for all users to a. Access Control With Example.
From trivestgroup.com
What is Physical Access Control and Which Types Do You Need? Access Control With Example It involves assigning users or. Examples include virtual private networks (vpns) and zero trust security solutions. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is key in it and cybersecurity to. Access Control With Example.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Access Control With Example An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a security policy that restricts. Access Control With Example.
From www.strongdm.com
What is Rolebased access control (RBAC)? Access Control With Example It involves assigning users or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control defines the schemas that prescribe how subjects. Access Control With Example.
From study.com
Access Control Types & Implementation Lesson Access Control With Example Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. With the development of strong access control barriers, it is possible. Access Control With Example.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK Access Control With Example It involves assigning users or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security policy that restricts access to places and/or data. An example of physical access control. Access Control With Example.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Examples include virtual private networks (vpns) and zero trust security solutions. An example of physical access control can be allowing access for. Access Control With Example.
From study.com
Access Control Matrix Definition, Function & Examples Lesson Access Control With Example Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a security policy that restricts access to places and/or data. With. Access Control With Example.
From www.atatus.com
RoleBased Access Control Definition, Implementation & More Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security policy that restricts access to places and/or data. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. It involves assigning users or. Access control is a security process that determines who can. Access Control With Example.
From hideez.com
Why Access Control Is Important? Examples and Solutions Hideez Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized. Access Control With Example.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. It involves assigning users or. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is a security policy that restricts access. Access Control With Example.
From www.cloudflare.com
What is rolebased access control (RBAC)? Cloudflare Access Control With Example An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. It involves assigning users or. With the development of strong access control. Access Control With Example.
From searchsecurity.techtarget.com
What is rolebased access control (RBAC)? Definition from Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. It involves assigning users or. Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is a security policy that restricts access. Access Control With Example.
From getsafeandsound.com
Access Control System An Overview Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. It involves assigning users or. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and. Access Control With Example.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. It involves assigning users or. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or.. Access Control With Example.
From securityboulevard.com
6 Examples of Discretionary Access Control (DAC) Security Boulevard Access Control With Example It involves assigning users or. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. With the development of strong access control barriers, it is possible to safeguard. Access Control With Example.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is a security policy that restricts access to places and/or data. Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and. Access Control With Example.
From technicalproduct1314.blogspot.com
Access Control System (ACS) B SQUARE NETWORKING SOLUTION Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a security policy that restricts access to places and/or data. Access control is key in it and cybersecurity to minimize risks. Access Control With Example.
From www.slideshare.net
8 Access Control Access Control With Example Examples include virtual private networks (vpns) and zero trust security solutions. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is a security process that determines who can access certain resources (files,. Access Control With Example.
From www.slideserve.com
PPT Resource access control example PowerPoint Presentation, free Access Control With Example Access control defines the schemas that prescribe how subjects can interact with objects in your it architecture. Access control is a security policy that restricts access to places and/or data. With the development of strong access control barriers, it is possible to safeguard organizational information and networks against. It involves assigning users or. Examples include virtual private networks (vpns) and. Access Control With Example.
From www.dnsstuff.com
RBAC vs. ABAC Access Control What’s the Difference? DNSstuff Access Control With Example An example of physical access control can be allowing access for all users to a main door using their entry card, key fob door entry systems or. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Examples include virtual private networks (vpns) and zero trust security solutions. Access. Access Control With Example.
From quizlet.com
Access Control Models Diagram Quizlet Access Control With Example Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Examples include virtual private networks (vpns) and zero trust security solutions. It involves assigning. Access Control With Example.
From www.youtube.com
The flexibility of AEOS Access Control Systems YouTube Access Control With Example Access control is key in it and cybersecurity to minimize risks by allowing resource access only to authorized users and systems. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. With the development of strong access control barriers, it is possible to safeguard organizational. Access Control With Example.