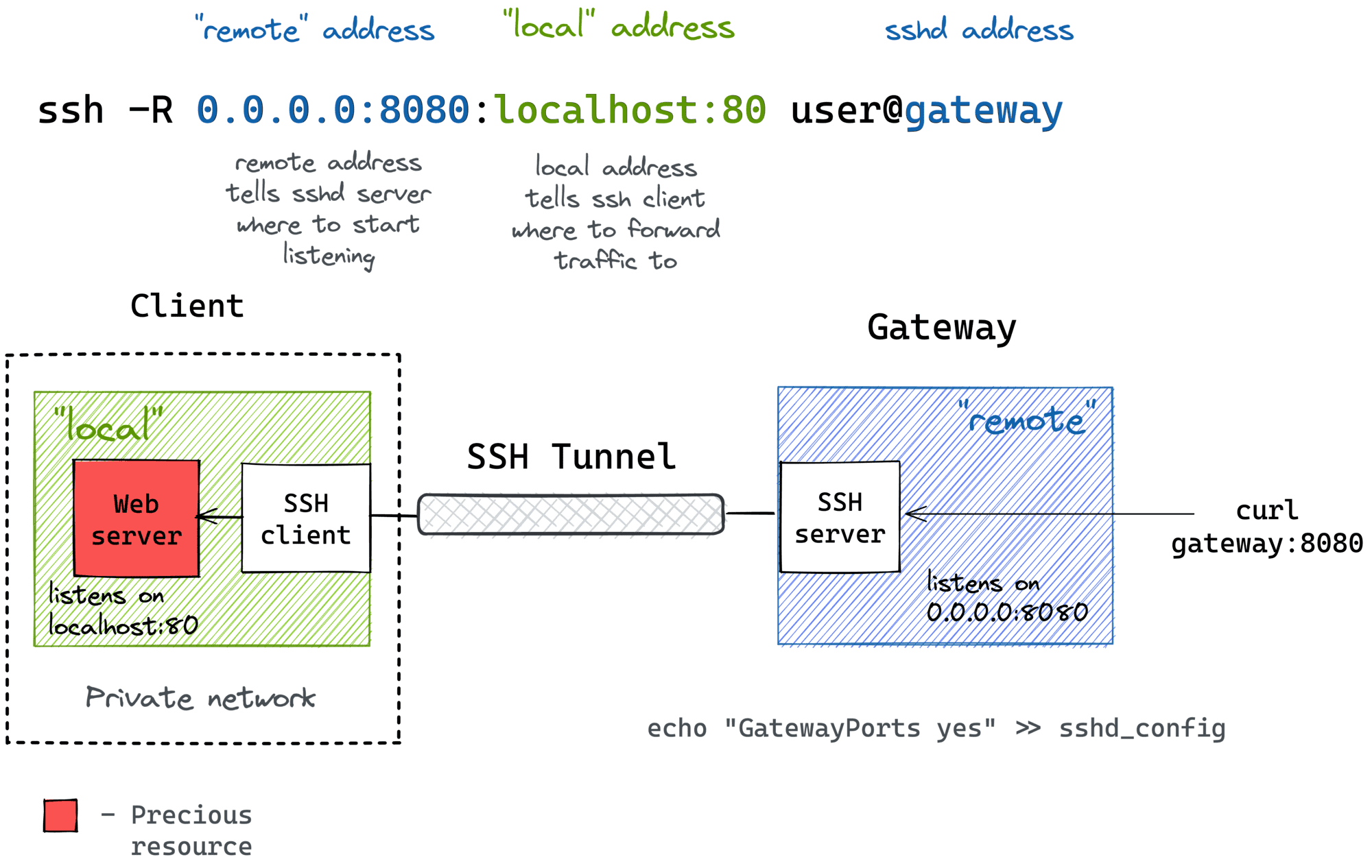
Socks Proxy Vs Ssh Tunnel . A special case of the forward tcp tunnels is the socks proxy capability. Operators can combine ssh tunnels with. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Using these options, the ssh client listens on a specified. What you describe is a socks proxy. Dynamic port forwarding turns your ssh client into a socks proxy server. It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. What openssh does it to tunnel this.
from www.mybluelinux.com
A special case of the forward tcp tunnels is the socks proxy capability. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. What openssh does it to tunnel this. It is standalone protocol used by various tools. Using these options, the ssh client listens on a specified. What you describe is a socks proxy. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Dynamic port forwarding turns your ssh client into a socks proxy server. Operators can combine ssh tunnels with.
A Visual Guide to SSH Tunnels Local and Remote Port Forwarding
Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Dynamic port forwarding turns your ssh client into a socks proxy server. What you describe is a socks proxy. What openssh does it to tunnel this. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A special case of the forward tcp tunnels is the socks proxy capability. Operators can combine ssh tunnels with. Using these options, the ssh client listens on a specified.
From pswalia2u.medium.com
SSH Tunneling / Port Forwarding / Pivoting /Socks proxy/adb port fwd Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Using these options, the ssh client listens on a specified. Dynamic port forwarding turns your ssh client into a socks proxy server. With an ssh socks5 proxy, your traffic is encrypted, and your true. Socks Proxy Vs Ssh Tunnel.
From www.youtube.com
How to Make an SSH Proxy Tunnel YouTube Socks Proxy Vs Ssh Tunnel What openssh does it to tunnel this. Dynamic port forwarding turns your ssh client into a socks proxy server. Using these options, the ssh client listens on a specified. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an ssh socks5 proxy, your traffic is encrypted, and your true location. Socks Proxy Vs Ssh Tunnel.
From sockstunneling.blogspot.com
SSH SOCKS Proxy Tunnel with Putty & Firefox Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. Dynamic port forwarding turns your ssh client into a socks proxy server. It is standalone protocol used by various tools. Using these options, the ssh client listens on a specified. Operators can combine ssh tunnels with. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security. Socks Proxy Vs Ssh Tunnel.
From proxyscrape.com
How To Setup SSH SOCKS Proxy 5 Simple Steps Socks Proxy Vs Ssh Tunnel Operators can combine ssh tunnels with. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. What you describe is a socks proxy. Using these options, the ssh client listens on a specified. A special case of the forward tcp tunnels is the socks proxy capability. Leveraging the. Socks Proxy Vs Ssh Tunnel.
From www.youtube.com
SSH tunneling for bypassing firewall (http and socks) (2 Solutions Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. A special case of the forward tcp tunnels is the socks proxy capability. What openssh does it to tunnel this. What you describe is a socks proxy. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Operators can combine. Socks Proxy Vs Ssh Tunnel.
From github.com
GitHub SinaXhpm/SocksProxyoverSsh Socks Proxy Ssh tunnel/Forwarding Socks Proxy Vs Ssh Tunnel Using these options, the ssh client listens on a specified. It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Dynamic port forwarding turns your ssh client into a socks proxy server. A special case of the forward tcp tunnels is the socks proxy. Socks Proxy Vs Ssh Tunnel.
From proxyandsshfree.blogspot.com
proxy ssh How To Route Traffic Securely Without a VPN Using a Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A special case of the forward tcp tunnels is the socks proxy. Socks Proxy Vs Ssh Tunnel.
From 9to5answer.com
[Solved] How do I set up an SSH SOCKS proxy with Gnome 9to5Answer Socks Proxy Vs Ssh Tunnel With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A special case of the forward tcp tunnels is the socks proxy capability. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. What openssh does it to tunnel this.. Socks Proxy Vs Ssh Tunnel.
From research.aimultiple.com
HTTP vs SOCKS Proxies Benefits and Technical Overview in '24 Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. Dynamic port forwarding turns your ssh client into a socks proxy server. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Using these options, the ssh client listens on a specified. A special case of the forward tcp tunnels is. Socks Proxy Vs Ssh Tunnel.
From proxyandsshfree.blogspot.com
proxy ssh How To Route Traffic Securely Without a VPN Using a Socks Proxy Vs Ssh Tunnel A special case of the forward tcp tunnels is the socks proxy capability. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. What openssh does it to tunnel this.. Socks Proxy Vs Ssh Tunnel.
From crawlbase.com
What is a SOCKS5 Proxy, and What is it Best for? Crawlbase Socks Proxy Vs Ssh Tunnel What openssh does it to tunnel this. Dynamic port forwarding turns your ssh client into a socks proxy server. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A. Socks Proxy Vs Ssh Tunnel.
From tonyteaches.tech
How to Make an SSH Proxy Tunnel Tony Teaches Tech Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. Operators can combine ssh tunnels with. What you describe is a socks proxy. A special case of the forward tcp tunnels is the socks proxy capability. Dynamic port forwarding turns your ssh client into a socks proxy server. Using these options, the ssh client listens on a specified. With an ssh socks5. Socks Proxy Vs Ssh Tunnel.
From www.pinterest.com
Set up a SOCKS5 proxy via SSH to bypass filters. All you need Socks Proxy Vs Ssh Tunnel With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. It is standalone protocol used by various tools. What you describe is a socks proxy. Operators can combine ssh tunnels with. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security. Socks Proxy Vs Ssh Tunnel.
From linuxize.com
How to Set up SSH SOCKS Tunnel for Private Browsing Linuxize Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. What openssh does it to tunnel this. A special case of the forward tcp tunnels is the socks proxy capability. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Using these options, the ssh client listens on a specified. Dynamic port forwarding turns. Socks Proxy Vs Ssh Tunnel.
From blog.regolit.com
SOCKSпрокси через SSH — Expertus metuit Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. A special case of the forward tcp tunnels is the socks proxy capability. What you describe is a socks proxy. With an ssh socks5 proxy, your traffic is encrypted, and your true location is. Socks Proxy Vs Ssh Tunnel.
From www.mybluelinux.com
A Visual Guide to SSH Tunnels Local and Remote Port Forwarding Socks Proxy Vs Ssh Tunnel With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. What you describe is a socks proxy. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Dynamic port forwarding turns your ssh client into a socks proxy server. What. Socks Proxy Vs Ssh Tunnel.
From www.techtarget.com
How to use SSH tunnels to cross network boundaries TechTarget Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. Using these options, the ssh client listens on a specified. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Operators can combine ssh tunnels with. What you describe is a socks proxy. A special case of the forward tcp tunnels is the socks. Socks Proxy Vs Ssh Tunnel.
From howtowiki91.blogspot.com
How To Ssh Tunneling Howto Techno Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Operators can combine ssh tunnels with. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. It is standalone protocol used by various. Socks Proxy Vs Ssh Tunnel.
From crawlbase.com
What is a SOCKS5 Proxy, and What is it Best for? Crawlbase Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. What you describe is a socks proxy. What openssh does it to tunnel this. Using these options, the ssh client listens on a specified. A special case of the forward tcp tunnels is the socks proxy capability. Operators can combine ssh tunnels with. Dynamic port forwarding turns your ssh client into a. Socks Proxy Vs Ssh Tunnel.
From incogniton.com
SOCKS vs HTTP Proxy Detailed Comparison Incogniton Socks Proxy Vs Ssh Tunnel Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A special case of the forward tcp tunnels is the socks proxy capability. What openssh does it to tunnel this.. Socks Proxy Vs Ssh Tunnel.
From technology.amis.nl
Secure browsing using a local SOCKS proxy server (on desktop or mobile Socks Proxy Vs Ssh Tunnel Dynamic port forwarding turns your ssh client into a socks proxy server. What openssh does it to tunnel this. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. A special case of the forward tcp tunnels is the socks proxy capability. It is standalone protocol used by. Socks Proxy Vs Ssh Tunnel.
From www.youtube.com
ProxyNVPN Guide Use Putty & SSH Tunnel as Secure SOCKS Proxy YouTube Socks Proxy Vs Ssh Tunnel Dynamic port forwarding turns your ssh client into a socks proxy server. A special case of the forward tcp tunnels is the socks proxy capability. What openssh does it to tunnel this. Using these options, the ssh client listens on a specified. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions.. Socks Proxy Vs Ssh Tunnel.
From www.youtube.com
Linux Proxychains Using SSH & SOCKS Proxy For Easy Remote Management Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. What openssh does it to tunnel this. Dynamic port forwarding turns your ssh client into a socks proxy server. It is standalone protocol used by various tools. Operators can combine ssh tunnels with. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an. Socks Proxy Vs Ssh Tunnel.
From exobjxpdj.blob.core.windows.net
Socks Proxy Over Ssh Tunnel at John Beals blog Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. A special case of the forward tcp tunnels is the socks proxy capability. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Using these options, the ssh client listens on a specified. What you describe is a socks proxy. Operators can combine ssh. Socks Proxy Vs Ssh Tunnel.
From proxidize.com
The Basic Guide to SOCKS Proxies What You Need to Know Proxidize Socks Proxy Vs Ssh Tunnel Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. A special case of the forward tcp tunnels is the socks proxy capability. It is standalone protocol used by various tools. What you describe is a socks proxy. Dynamic port forwarding turns your ssh client into a socks proxy server. Using these. Socks Proxy Vs Ssh Tunnel.
From www.malekal.com
Comment configurer le tunnel SSH (redirection de port) Socks Proxy Vs Ssh Tunnel Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. It is standalone protocol used by various tools. Using these options, the ssh client listens on a specified. A special case of the forward tcp tunnels is the socks proxy capability. What openssh does it to tunnel this. Operators can combine ssh. Socks Proxy Vs Ssh Tunnel.
From goteleport.com
What is SSH Tunnel, SSH Reverse Tunnel and SSH Port Forwarding? Socks Proxy Vs Ssh Tunnel It is standalone protocol used by various tools. What openssh does it to tunnel this. Dynamic port forwarding turns your ssh client into a socks proxy server. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Leveraging the ssh client remote and local port forward tunnels allows. Socks Proxy Vs Ssh Tunnel.
From proxidize.com
The Basic Guide to SOCKS Proxy Proxidize Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. A special case of the forward tcp tunnels is the socks proxy capability. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions.. Socks Proxy Vs Ssh Tunnel.
From hide-ip-proxy.com
What is a SOCKS proxy and where to find good SOCKS proxies Socks Proxy Vs Ssh Tunnel Using these options, the ssh client listens on a specified. What openssh does it to tunnel this. What you describe is a socks proxy. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from expert hackers;. Leveraging the ssh client remote and local port forward tunnels allows an operator to. Socks Proxy Vs Ssh Tunnel.
From rocksmokasin.weebly.com
Ssh tunnel manager socks 5 rocksmokasin Socks Proxy Vs Ssh Tunnel Dynamic port forwarding turns your ssh client into a socks proxy server. It is standalone protocol used by various tools. Using these options, the ssh client listens on a specified. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. What you describe is a socks proxy. With an ssh socks5 proxy,. Socks Proxy Vs Ssh Tunnel.
From posts.specterops.io
Offensive Security Guide to SSH Tunnels and Proxies by Russel Van Socks Proxy Vs Ssh Tunnel A special case of the forward tcp tunnels is the socks proxy capability. Using these options, the ssh client listens on a specified. What openssh does it to tunnel this. Dynamic port forwarding turns your ssh client into a socks proxy server. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions.. Socks Proxy Vs Ssh Tunnel.
From 123host.vn
Hướng dẫn tạo SOCKS Proxy từ SSH Tunneling Tài liệu 123Host Socks Proxy Vs Ssh Tunnel A special case of the forward tcp tunnels is the socks proxy capability. Dynamic port forwarding turns your ssh client into a socks proxy server. It is standalone protocol used by various tools. What openssh does it to tunnel this. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re not safe from. Socks Proxy Vs Ssh Tunnel.
From netnut.io
What are socks Proxy? Complete Guide to Socks Proxy NetNut Socks Proxy Vs Ssh Tunnel What you describe is a socks proxy. Dynamic port forwarding turns your ssh client into a socks proxy server. Operators can combine ssh tunnels with. What openssh does it to tunnel this. It is standalone protocol used by various tools. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. Using these. Socks Proxy Vs Ssh Tunnel.
From 123host.vn
Hướng dẫn tạo SOCKS Proxy từ SSH Tunneling Tài liệu 123Host Socks Proxy Vs Ssh Tunnel What openssh does it to tunnel this. Operators can combine ssh tunnels with. Dynamic port forwarding turns your ssh client into a socks proxy server. Leveraging the ssh client remote and local port forward tunnels allows an operator to bypass network security restrictions. With an ssh socks5 proxy, your traffic is encrypted, and your true location is hidden, but you’re. Socks Proxy Vs Ssh Tunnel.
From howtowiki91.blogspot.com
How To Ssh Tunneling Howto Techno Socks Proxy Vs Ssh Tunnel Dynamic port forwarding turns your ssh client into a socks proxy server. Operators can combine ssh tunnels with. It is standalone protocol used by various tools. What openssh does it to tunnel this. A special case of the forward tcp tunnels is the socks proxy capability. With an ssh socks5 proxy, your traffic is encrypted, and your true location is. Socks Proxy Vs Ssh Tunnel.