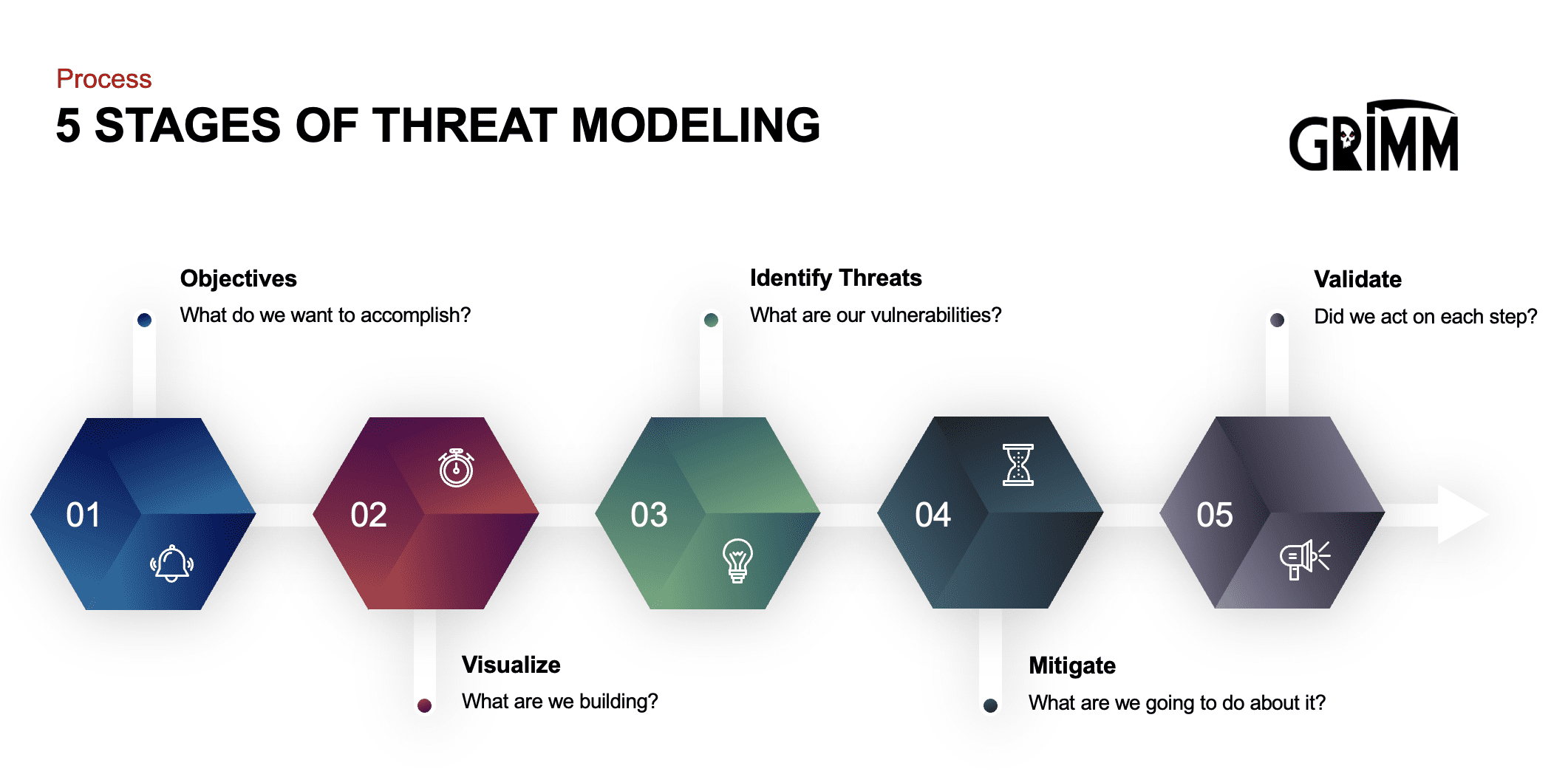
What Are Popular Threat Modelling Techniques . 1.1 importance of threat modelling. This contrasts with the other threat. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. Therefore, system owners must prioritise r. Threat intelligence, asset identification, mitigation capabilities, risk. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints.
from grimmcyber.com
Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. This contrasts with the other threat. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Therefore, system owners must prioritise r. A typical threat modeling process includes five steps:
Threat Modeling GRIMM Cyber R&D
What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. This contrasts with the other threat. 1.1 importance of threat modelling. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: Threat intelligence, asset identification, mitigation capabilities, risk. Therefore, system owners must prioritise r.
From www.researchgate.net
DEMIS Threat modelling technique for attack against encrypted videos What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat intelligence, asset identification, mitigation capabilities, risk. Therefore, system owners must prioritise r. This contrasts. What Are Popular Threat Modelling Techniques.
From www.slideserve.com
PPT Introduction to Intelligence Preparation of the Battlespace (IPB What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. Therefore, system owners must prioritise r. A typical threat modeling process includes five steps: This contrasts with the other threat. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an. What Are Popular Threat Modelling Techniques.
From lab.wallarm.com
👉Using Threat Modeling in Cybersecurity to Hunt and Remediate What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. This contrasts with the other threat. Threat. What Are Popular Threat Modelling Techniques.
From www.slcyber.io
Threat Models 5 Steps To Building A Threat Model SL Cyber What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: Threat intelligence, asset identification, mitigation capabilities, risk.. What Are Popular Threat Modelling Techniques.
From infosecwriteups.com
Learn how to perform threat modeling to proactively identify potential What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. Therefore, system owners must prioritise r. This contrasts with the other threat. A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From github.com
GitHub 0x736E/threatmodelling Threat Modelling Assets (STRIDE What Are Popular Threat Modelling Techniques Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. This contrasts with the other threat. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From www.aquia.us
Threat Modeling What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. A typical threat modeling process includes five steps: This contrasts with the other threat. Therefore, system owners must prioritise r. Threat intelligence, asset identification, mitigation capabilities, risk. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial. What Are Popular Threat Modelling Techniques.
From www.joetheitguy.com
ITSM Basics Know Your Information Security Threats! Joe The IT Guy What Are Popular Threat Modelling Techniques A typical threat modeling process includes five steps: This contrasts with the other threat. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints.. What Are Popular Threat Modelling Techniques.
From awesomeopensource.com
Threat Model Playbook What Are Popular Threat Modelling Techniques A typical threat modeling process includes five steps: Threat intelligence, asset identification, mitigation capabilities, risk. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Therefore, system owners must prioritise r. 1.1 importance of threat modelling. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which. What Are Popular Threat Modelling Techniques.
From threat-modeling.com
Threat Modeling Terminology What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. A typical threat modeling process includes five steps: Threat intelligence, asset identification, mitigation capabilities, risk. This contrasts with the other threat. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial. What Are Popular Threat Modelling Techniques.
From usa.kaspersky.com
How to choose threat intelligence Kaspersky official blog What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. This contrasts with the other threat. Therefore, system owners must prioritise r. A typical threat. What Are Popular Threat Modelling Techniques.
From www.jimmwayans.com
THREAT MODELING TODAY What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: Therefore, system owners must prioritise r. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. Threat. What Are Popular Threat Modelling Techniques.
From www.practical-devsecops.com
Top 5 Threat Modeling Methodologies Practical DevSecOps What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. This contrasts with the other threat. 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker. What Are Popular Threat Modelling Techniques.
From www.practical-devsecops.com
Threat Modeling In Practice Practical DevSecOps What Are Popular Threat Modelling Techniques Therefore, system owners must prioritise r. This contrasts with the other threat. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system.. What Are Popular Threat Modelling Techniques.
From community.arm.com
Five Steps to Successful Threat Modelling of Things What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. Threat intelligence, asset identification, mitigation capabilities, risk.. What Are Popular Threat Modelling Techniques.
From templates.rjuuc.edu.np
Stride Threat Model Template What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system.. What Are Popular Threat Modelling Techniques.
From www.collidu.com
Stride Threat Model PowerPoint Presentation Slides PPT Template What Are Popular Threat Modelling Techniques Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: This contrasts with the other threat. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. 1.1 importance of threat modelling. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial. What Are Popular Threat Modelling Techniques.
From www.upguard.com
What is Threat Modelling? 10 Threat Identity Methods Explained UpGuard What Are Popular Threat Modelling Techniques A typical threat modeling process includes five steps: Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. This contrasts with the other threat. Threat intelligence, asset identification, mitigation capabilities, risk. A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From offensive360.com
How to create a threat model Offensive 360 O360 What Are Popular Threat Modelling Techniques Therefore, system owners must prioritise r. 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: This. What Are Popular Threat Modelling Techniques.
From www.knowledgehut.com
Threat Modeling Tools, Importance, Process and Methodologies What Are Popular Threat Modelling Techniques Threat intelligence, asset identification, mitigation capabilities, risk. This contrasts with the other threat. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. A typical. What Are Popular Threat Modelling Techniques.
From threat-modeling.com
Automated Threat Modeling What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. This contrasts with the other threat. Therefore, system owners must prioritise r. 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. A typical threat. What Are Popular Threat Modelling Techniques.
From threatmodeler.com
Threat Modeling as a Service ThreatModeler What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. Therefore, system owners must prioritise r. This contrasts. What Are Popular Threat Modelling Techniques.
From www.practical-devsecops.com
What Is Threat Modeling And How Does It Help? Practical DevSecOps What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints.. What Are Popular Threat Modelling Techniques.
From www.linkedin.com
Threat Modeling Methodologies A Comparative Study of PASTA and STRIDE What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling.. What Are Popular Threat Modelling Techniques.
From jonnytyers.co.uk
What are the Benefits of a Threat Model? What Are Popular Threat Modelling Techniques A typical threat modeling process includes five steps: Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. This contrasts with the other threat. Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From www.researchgate.net
Threat model diagram elements Download Scientific Diagram What Are Popular Threat Modelling Techniques This contrasts with the other threat. 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From www.linkedin.com
A Threat Modeling Process to Improve Resiliency of Cybersecurity Program What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. This contrasts with the other threat. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. Therefore, system owners must prioritise r. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From www.pinterest.com
15 best images about Information Assurance Threat Models on Pinterest What Are Popular Threat Modelling Techniques A typical threat modeling process includes five steps: This contrasts with the other threat. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat intelligence, asset identification, mitigation capabilities, risk. Therefore, system owners must prioritise r. 1.1 importance of threat modelling. Threat modeling analyzes a system from an adversarial. What Are Popular Threat Modelling Techniques.
From www.slcyber.io
Threat Models 5 Steps To Building A Threat Model SL Cyber What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. This contrasts with the other threat. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing. What Are Popular Threat Modelling Techniques.
From www.labellerr.com
What are adversarial attacks in machine learning and how to prevent them? What Are Popular Threat Modelling Techniques A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling.. What Are Popular Threat Modelling Techniques.
From threat-modeling.com
Automated Threat Modeling What Are Popular Threat Modelling Techniques Therefore, system owners must prioritise r. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. A typical threat modeling process includes five steps: This contrasts with the other threat. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system.. What Are Popular Threat Modelling Techniques.
From www.csoonline.com
Threat modeling explained A process for anticipating cyber attacks What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Therefore, system owners must prioritise r. This contrasts with the other threat. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial. What Are Popular Threat Modelling Techniques.
From teachsafeagile.com
Threat Modelling What Are Popular Threat Modelling Techniques Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. Therefore, system owners must prioritise r. Threat intelligence, asset identification, mitigation capabilities, risk. 1.1 importance of threat modelling. A typical threat modeling process includes five steps: This contrasts with the other threat. A threat modeling methodology focuses on examining the. What Are Popular Threat Modelling Techniques.
From grimmcyber.com
Threat Modeling GRIMM Cyber R&D What Are Popular Threat Modelling Techniques Therefore, system owners must prioritise r. Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. 1.1 importance of threat modelling. Threat intelligence, asset identification, mitigation capabilities, risk. A typical threat modeling process includes five steps: A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing. What Are Popular Threat Modelling Techniques.
From insights.sei.cmu.edu
Threat Modeling 12 Available Methods What Are Popular Threat Modelling Techniques 1.1 importance of threat modelling. This contrasts with the other threat. A typical threat modeling process includes five steps: Threat modeling analyzes a system from an adversarial perspective, focusing on ways in which an attacker can exploit a system. A threat modeling methodology focuses on examining the system from an attacker’s perspective, allowing security professionals to thoroughly research endpoints. Threat. What Are Popular Threat Modelling Techniques.