Ldap Bind Request Wireshark . In the connect dialog box, enter the ldap. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. Ldap was developed as simple access protocol for x.500 databases. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. Typically, ldap uses tcp or udp. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. The problem is that my capture is full of bindrequest(1) root simple. This is most useful for testing the username/password in bind request. I try to find if there are any ldap auth request from a client. In the command prompt, type ldp.exe. This example uses the active directory users and computers application as a source for generating ldap traffic.
from unit42.paloaltonetworks.com
In the connect dialog box, enter the ldap. I try to find if there are any ldap auth request from a client. This example uses the active directory users and computers application as a source for generating ldap traffic. This is most useful for testing the username/password in bind request. Typically, ldap uses tcp or udp. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. The problem is that my capture is full of bindrequest(1) root simple. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. Ldap was developed as simple access protocol for x.500 databases.
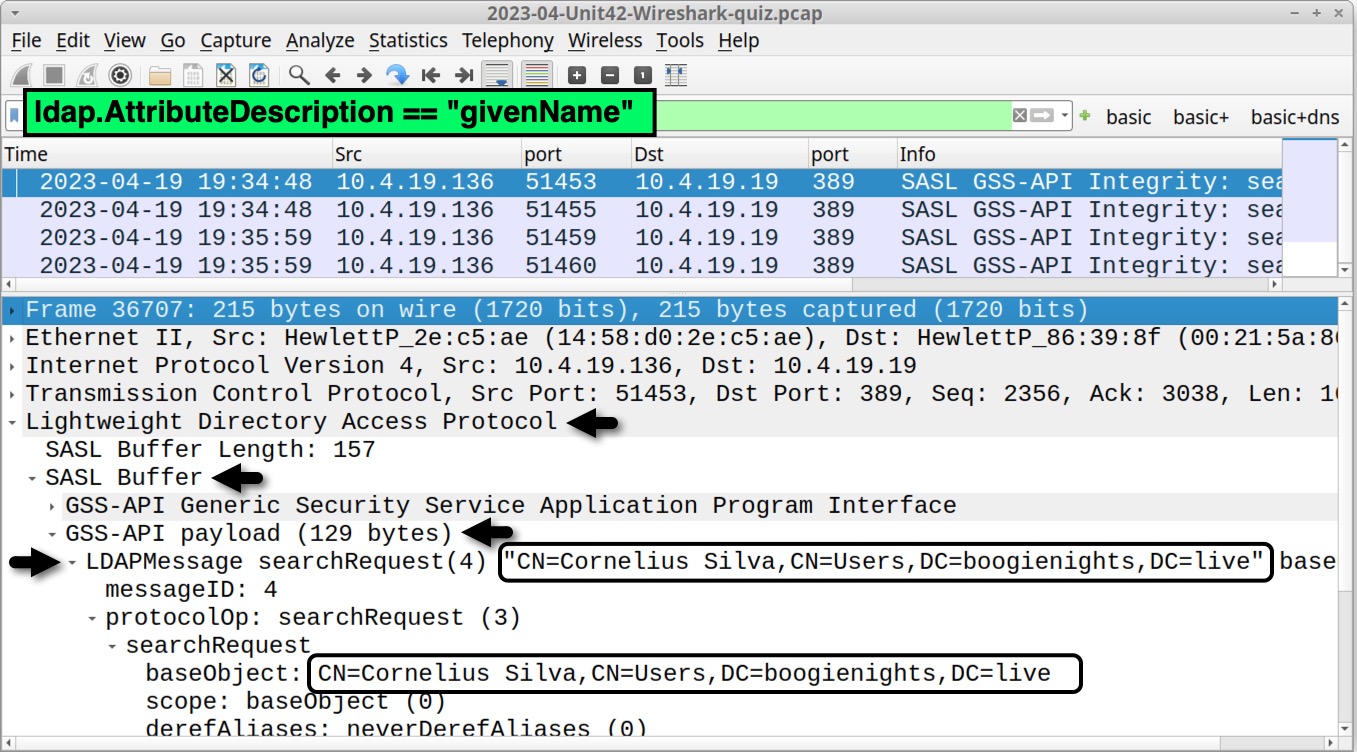
Cold as Ice Answers to Unit 42 Wireshark Quiz for IcedID
Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. This is most useful for testing the username/password in bind request. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. This example uses the active directory users and computers application as a source for generating ldap traffic. In the command prompt, type ldp.exe. In the connect dialog box, enter the ldap. Typically, ldap uses tcp or udp. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. I try to find if there are any ldap auth request from a client. The problem is that my capture is full of bindrequest(1) root simple. Ldap was developed as simple access protocol for x.500 databases. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account.
From unit42.paloaltonetworks.com
Wireshark Tutorial Identifying Hosts and Users Ldap Bind Request Wireshark In the command prompt, type ldp.exe. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. The problem is that my capture is full of bindrequest(1) root simple. Ldap was developed as simple access protocol for x.500 databases. I'm looking to limit the intake into the pcap file. Ldap Bind Request Wireshark.
From www.alphr.com
How to Use Wireshark Ldap Bind Request Wireshark I try to find if there are any ldap auth request from a client. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. Typically, ldap uses tcp or udp. Ldap was developed as simple access protocol for x.500 databases. I'm looking to limit the intake into the. Ldap Bind Request Wireshark.
From www.slideserve.com
PPT Lightweight Directory Access Protocol (LDAP) PowerPoint Ldap Bind Request Wireshark In the connect dialog box, enter the ldap. Typically, ldap uses tcp or udp. I try to find if there are any ldap auth request from a client. This is most useful for testing the username/password in bind request. The problem is that my capture is full of bindrequest(1) root simple. I'm looking to limit the intake into the pcap. Ldap Bind Request Wireshark.
From www.slideserve.com
PPT LDAP Protocol Overview PowerPoint Presentation, free download Ldap Bind Request Wireshark In the connect dialog box, enter the ldap. This example uses the active directory users and computers application as a source for generating ldap traffic. Ldap was developed as simple access protocol for x.500 databases. This is most useful for testing the username/password in bind request. I try to find if there are any ldap auth request from a client.. Ldap Bind Request Wireshark.
From cammyd.com
Wireshark 101 Sending And Analyzing An ICMP Ping, Part 1 Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. The problem is that my capture is full of bindrequest(1) root simple. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. Ldap was developed as simple access protocol for x.500. Ldap Bind Request Wireshark.
From www.lifewire.com
How to Use Wireshark A Complete Tutorial Ldap Bind Request Wireshark Typically, ldap uses tcp or udp. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. The problem is that my capture is full of bindrequest(1) root simple. In the command prompt, type ldp.exe. I would like to filter the ldap.bindrequest containing the username and the. Ldap Bind Request Wireshark.
From stereohor.weebly.com
How use wireshark stereohor Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. The problem is that my capture is full of bindrequest(1) root simple. In the command prompt, type ldp.exe. This example uses the active directory users and computers application. Ldap Bind Request Wireshark.
From dadlending.weebly.com
How to use wireshark linux to view network traffic dadlending Ldap Bind Request Wireshark The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. This is most useful for testing the username/password in bind request. In the connect dialog box, enter the ldap. Ldap was developed as simple access protocol for x.500 databases. I try to find if there are any ldap. Ldap Bind Request Wireshark.
From unit42.paloaltonetworks.com
Wireshark Tutorial Identifying Hosts and Users Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. I try to find if there are any ldap auth request from a client. Typically, ldap uses tcp or udp. I would like to filter the ldap.bindrequest containing. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. In the command prompt, type ldp.exe. This is most useful for testing the username/password in bind request. Ldap was developed as simple access protocol for x.500 databases. Typically, ldap uses tcp or udp. The sslkeylogfile provides the session. Ldap Bind Request Wireshark.
From www.nationalcybersecurityuniversity.com
Wireshark Analyzing Network Protocols Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. Typically, ldap uses tcp or udp. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. In the command prompt, type ldp.exe. I try to find if there are any ldap. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. In the connect dialog box, enter the ldap. This example uses the active directory users and computers application as a source for generating ldap traffic. In the command prompt, type ldp.exe. Ldap was developed as simple access protocol. Ldap Bind Request Wireshark.
From www.fileeagle.com
Wireshark 2.4.0 Network Tools Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. I try to find if there are any ldap auth request from a client. The problem is that my. Ldap Bind Request Wireshark.
From www.techsolveprac.com
Wireshark Beginner's step by step guide TechSolvePrac Ldap Bind Request Wireshark In the connect dialog box, enter the ldap. Ldap was developed as simple access protocol for x.500 databases. The problem is that my capture is full of bindrequest(1) root simple. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. I'm looking to limit the intake into the. Ldap Bind Request Wireshark.
From unit42.paloaltonetworks.com
Cold as Ice Answers to Unit 42 Wireshark Quiz for IcedID Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. This is most useful for testing the username/password in bind request. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. I try to find if there are any ldap auth. Ldap Bind Request Wireshark.
From www.wireshark.org
Wireshark User’s Guide Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. This is most useful for testing the username/password in bind request. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. Ldap was developed as simple access protocol for x.500 databases. I would like to filter. Ldap Bind Request Wireshark.
From blog.webernetz.net
Wireshark 02 IXFR by BIND reload Blog Ldap Bind Request Wireshark Typically, ldap uses tcp or udp. Ldap was developed as simple access protocol for x.500 databases. The problem is that my capture is full of bindrequest(1) root simple. I try to find if there are any ldap auth request from a client. This example uses the active directory users and computers application as a source for generating ldap traffic. In. Ldap Bind Request Wireshark.
From unit42.paloaltonetworks.com
Wireshark Tutorial Identifying Hosts and Users Ldap Bind Request Wireshark In the command prompt, type ldp.exe. This is most useful for testing the username/password in bind request. In the connect dialog box, enter the ldap. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. I would like to filter the ldap.bindrequest containing the username and. Ldap Bind Request Wireshark.
From linuxhint.com
HTTP analysis using Wireshark Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to. Ldap Bind Request Wireshark.
From corporatedesignmunchengha.blogspot.com
How To Load Host File Into Wireshark Corporate design munchen Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. Ldap was developed as simple access protocol for x.500 databases. This is most useful for testing the username/password in bind request. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. In the connect dialog box,. Ldap Bind Request Wireshark.
From sys-admin.in.ua
Что такое LDAP Simple Bind и почему это плохо Нотатки системного Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. In the command prompt, type ldp.exe. In the connect dialog box, enter the ldap. Ldap was developed as simple access protocol for x.500 databases.. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. This is most useful for testing the username/password in bind request. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. In the command prompt, type. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. I try to find if there are any ldap auth request from a client. In the connect dialog box, enter the ldap. This example uses the. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. In the command prompt, type ldp.exe. Typically, ldap uses tcp or udp. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. In the connect dialog. Ldap Bind Request Wireshark.
From seclists.org
Wireshark SSL LDAP dialog bad request interpretation? Ldap Bind Request Wireshark This example uses the active directory users and computers application as a source for generating ldap traffic. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. In the connect dialog box, enter the ldap. In the command prompt, type ldp.exe. I try to find if. Ldap Bind Request Wireshark.
From blog.csdn.net
wireshark数据流分析学习日记day2 识别主机用户专题_ldap协议使用wireshark解析CSDN博客 Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. This is most useful for testing the username/password in bind request. I'm looking to limit the intake into the pcap file by using a capture filter to target. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark Typically, ldap uses tcp or udp. In the command prompt, type ldp.exe. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. I try to find if there are any ldap auth request from a client. This example uses the active directory users and computers application as a. Ldap Bind Request Wireshark.
From sys-admin.in.ua
Что такое LDAP Simple Bind и почему это плохо Нотатки системного Ldap Bind Request Wireshark This is most useful for testing the username/password in bind request. I try to find if there are any ldap auth request from a client. In the command prompt, type ldp.exe. Typically, ldap uses tcp or udp. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular. Ldap Bind Request Wireshark.
From ask.wireshark.org
Wireshark Filter ldap bindresponse with invalidCredentials Ask Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. In the connect dialog box, enter the ldap. Ldap was developed as simple access protocol for x.500 databases. In the command prompt, type ldp.exe. I would like to filter the ldap.bindrequest containing the username and the ldap.bindresponse containing the message invalidcredentials related to the bindrequest that. The sslkeylogfile. Ldap Bind Request Wireshark.
From unit42.paloaltonetworks.com
Wireshark Tutorial Identifying Hosts and Users Ldap Bind Request Wireshark Ldap was developed as simple access protocol for x.500 databases. This is most useful for testing the username/password in bind request. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. The problem is that my capture is full of bindrequest(1) root simple. I would like to filter. Ldap Bind Request Wireshark.
From developer.aliyun.com
LDAP协议入门阿里云开发者社区 Ldap Bind Request Wireshark I try to find if there are any ldap auth request from a client. The problem is that my capture is full of bindrequest(1) root simple. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. In the connect dialog box, enter the ldap. This is most useful. Ldap Bind Request Wireshark.
From infocenter.nokia.com
LDAP authentication process Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. This is most useful for testing the username/password in bind request. Ldap was developed as simple access protocol for x.500 databases. Typically, ldap uses tcp or udp. In the connect dialog box, enter the ldap. I try to find if there are any ldap auth request from a. Ldap Bind Request Wireshark.
From unit42.paloaltonetworks.com
Wireshark Tutorial Decrypting HTTPS Traffic (Includes SSL and TLS) Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. In the command prompt, type ldp.exe. I try to find if there are any ldap auth request from a client. In the connect dialog box, enter the ldap. Ldap was developed as simple access protocol for x.500 databases. The sslkeylogfile provides the session keys needed to decrypt this. Ldap Bind Request Wireshark.
From nimishprabhu.com
Analyze POST and GET packets using WireShark Ldap Bind Request Wireshark The problem is that my capture is full of bindrequest(1) root simple. Ldap was developed as simple access protocol for x.500 databases. In the connect dialog box, enter the ldap. The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. This example uses the active directory users and. Ldap Bind Request Wireshark.
From www.golinuxcloud.com
How to analyze LDAP traffic with Wireshark Tutorial GoLinuxCloud Ldap Bind Request Wireshark The sslkeylogfile provides the session keys needed to decrypt this data, making it possible to view the actual contents of the communication. I'm looking to limit the intake into the pcap file by using a capture filter to target the ldap bind for a particular account. In the connect dialog box, enter the ldap. This is most useful for testing. Ldap Bind Request Wireshark.