Types Of Mobile Device Vulnerabilities . To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information.
from securityboulevard.com
Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security.
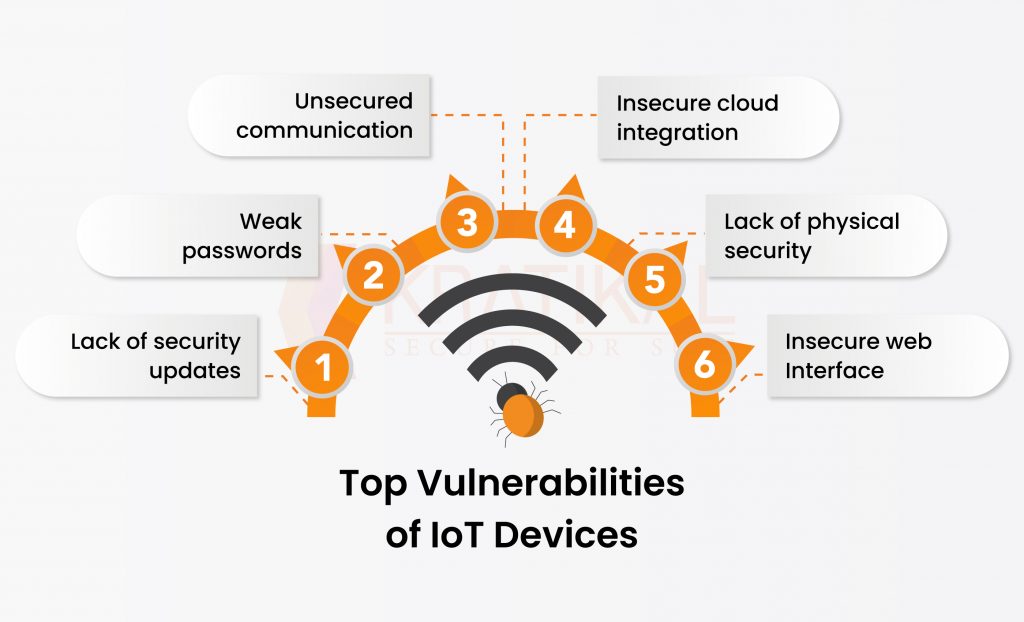
“Don’t let your ignorance make you vulnerable to IoT attacks
Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required
From technic4u.com
The Ultimate Guide To Smartphone Security (Protecting Your Phone In 2024) Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From www.networksolutions.com
How to Secure Mobile Devices from Common Vulnerabilities Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From www.le-vpn.com
Mobile Apps Security What apps put privacy at risk. Le VPN Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From blog.airdroid.com
10 Most Common Mobile Security Myths Debunked AirDroid Blog Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From educatererindia.blogspot.com
Mobile Security Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From gotowebsecurity.com
Mobile Security Vulnerabilities You Should Know Security Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From research.aimultiple.com
Ultimate Guide to Vulnerability Scanning Automation in 2024 Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From securityboulevard.com
“Don’t let your ignorance make you vulnerable to IoT attacks Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From www.youtube.com
Mobile Device Vulnerabilities YouTube Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.thompsoncoburn.com
The serious security vulnerabilities of mobile devices Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From www.trendmicro.com
Smart Yet Flawed IoT Device Vulnerabilities Explained Trend Micro (US) Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.stealthlabs.com
Top 8 Mobile Device Cyber Threats You Should Know to Protect Your Data! Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.todaytechmedia.com
4 Mobile App Security Vulnerabilities You Should Know About Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From securityboulevard.com
“Mobile application vulnerabilities The hidden threat to sensitive Types Of Mobile Device Vulnerabilities Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From www.shadowdetect.com
Mobile Device Vulnerabilities Shadow Detect Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your. Types Of Mobile Device Vulnerabilities.
From www.youtube.com
Mobile Device Vulnerabilities CompTIA Security+ SY0701 2.3 YouTube Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.externetworks.com
Reduce Business Security Risks with Mobile Security Management Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful. Types Of Mobile Device Vulnerabilities.
From www.researchgate.net
(PDF) Mobile Device Security A Survey on Mobile Device Threats Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From sectigostore.com
OWASP Mobile Top 10 Vulnerabilities & Mitigation Strategies InfoSec Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From coggle.it
MOBILE DEVICE VULNERABILITIES Coggle Diagram Types Of Mobile Device Vulnerabilities Results in 30 secondsno credit card required These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From secure-networksco.com
advanced threat and vulnerability management Secure Networks Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. Results in 30 secondsno credit card required These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From auth0.com
The 9 Most Common Security Threats to Mobile Devices in 2021 Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. Results in 30 secondsno credit card required These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From mobilepersuasion.org
Mobile application vulnerabilities and threats Mobile Persuasion Types Of Mobile Device Vulnerabilities Results in 30 secondsno credit card required These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From securityzap.com
25 Android Smartphone Devices Found to Contain Severe Vulnerabilities Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From thecyphere.com
Top 10 Network Security Vulnerabilities Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.tutorsindia.com
The Most Significant Security Threats With IOT Devices Latest Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.le-vpn.com
How to security challenges on mobile devices. Le VPN Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From www.slideserve.com
PPT Cellphone and Mobile Device Forensics An update on concepts Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your. Types Of Mobile Device Vulnerabilities.
From www.ptsecurity.com
Mobile Application Security Threats and Vulnerabilities 2019 Mobile Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.newsoftwares.net
Using Device Encryption To Secure Cellphones And Their Vulnerabilities Types Of Mobile Device Vulnerabilities To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Results in 30 secondsno credit card required Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.seasiainfotech.com
Top 7 Mobile Application Security Vulnerabilities You Must Know Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Results in 30 secondsno credit card required These handheld devices, carried in. Types Of Mobile Device Vulnerabilities.
From www.itensure.com
Mobile Vulnerability ITensure Types Of Mobile Device Vulnerabilities Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we. Types Of Mobile Device Vulnerabilities.
From www.researchgate.net
Security Vulnerabilities of Mobile Devices. Threats related to wearable Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your. Types Of Mobile Device Vulnerabilities.
From www.theknowledgeacademy.com
What is Vulnerability in Cyber Security With Example? Types Of Mobile Device Vulnerabilities These handheld devices, carried in our pockets, are used to store and protect sensitive information. Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. Results in 30 secondsno credit card required To update the owasp top 10, we start by collecting. Types Of Mobile Device Vulnerabilities.
From www.lookout.com
Mobile Vulnerabilities What They Are & How They Impact Enterprise Lookout Types Of Mobile Device Vulnerabilities Okta’s complete guide on the four types of mobile security threats, the six most common mobile attacks we face today, and how to protect your devices against them. To update the owasp top 10, we start by collecting data on the most common and impactful mobile application security. These handheld devices, carried in our pockets, are used to store and. Types Of Mobile Device Vulnerabilities.