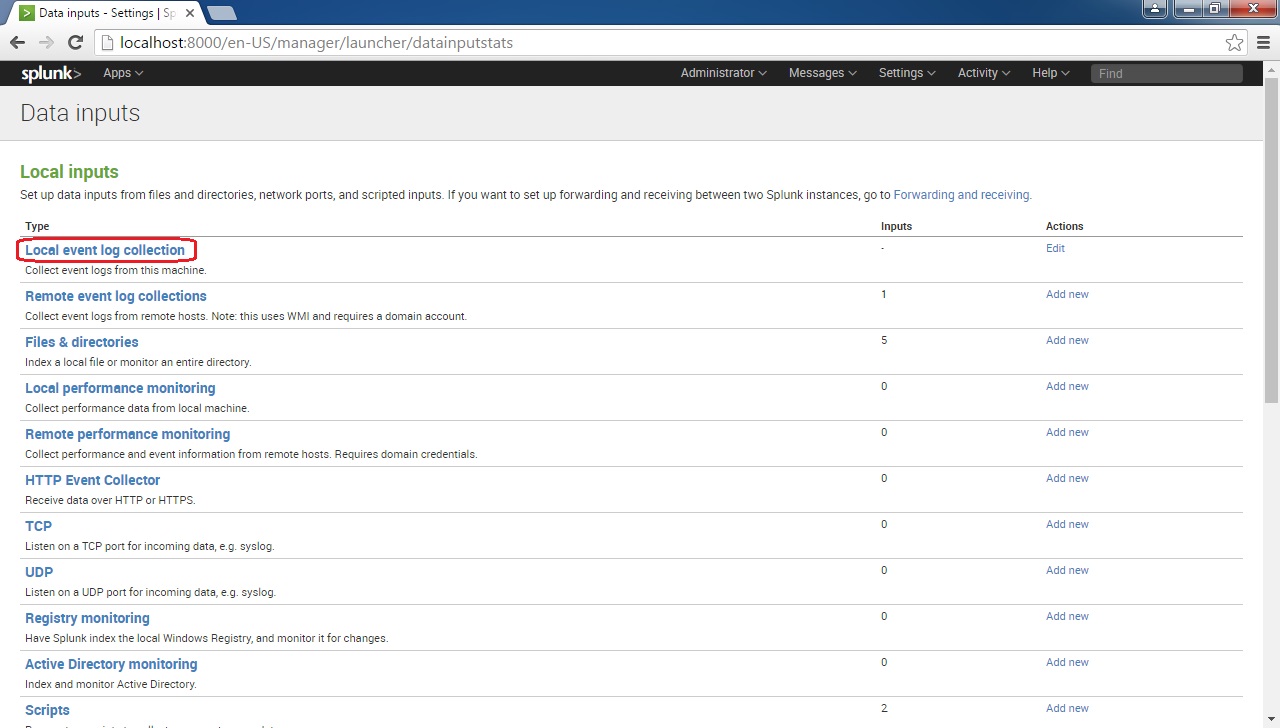
Windows Event Log In Splunk . Click local event log collection. In splunk 6, everything is done in inputs.conf. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click new to add an input. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click remote event log collections. Here is a new inputs.conf stanza for you: Adding event ids to splunk. Click the add data link in splunk home. Under data, click data inputs. Make sure that your splunk. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you.
from geek-university.com
Make sure that your splunk. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: In splunk 6, everything is done in inputs.conf. Adding event ids to splunk. Click local event log collection. Click remote event log collections. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Click the add data link in splunk home. Click new to add an input.
Collect event logs from a local Windows machine Splunk
Windows Event Log In Splunk Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Click local event log collection. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click new to add an input. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Under data, click data inputs. In splunk 6, everything is done in inputs.conf. Adding event ids to splunk. Click the add data link in splunk home. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Here is a new inputs.conf stanza for you: Click remote event log collections. Make sure that your splunk.
From appuals.com
The 5 Best Event and Log Analysis Tools and Software Windows Event Log In Splunk Adding event ids to splunk. Click the add data link in splunk home. Make sure that your splunk. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Click new to add an input. In splunk 6, everything is done in inputs.conf. Under data, click data inputs. Search indexes where windows event. Windows Event Log In Splunk.
From mindmajix.com
Splunk logging best practices Splunk logback Mindmajix Windows Event Log In Splunk Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Make sure that your splunk. In splunk 6, everything is done in inputs.conf. Click remote event log collections. Adding event ids to splunk. Click new to add an input. Click local event log collection. Here is a. Windows Event Log In Splunk.
From apps.splunk.com
Windows Event Logs Analysis Splunkbase Windows Event Log In Splunk Click new to add an input. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click remote event log collections. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Make sure that your splunk. Ingesting events from. Windows Event Log In Splunk.
From 4sysops.com
Splunk Analyze system logs 4sysops Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Under data, click data inputs. In splunk 6, everything is done in inputs.conf. Click new to add an input. Make sure that your splunk. Click remote event log collections. Click local event log collection. Click the add data link in splunk. Windows Event Log In Splunk.
From docs.splunk.com
Events viewer Splunk Documentation Windows Event Log In Splunk Adding event ids to splunk. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Here is a new inputs.conf stanza for you: In splunk 6, everything is done in inputs.conf. Under data, click data inputs. When you experience issues getting event logs from remote windows servers, try. Windows Event Log In Splunk.
From www.mintsecurity.fi
Mint Security SIEM, Splunk & Log Management Windows Event Log In Splunk Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Click the add data link in splunk home. Under data, click data inputs. In splunk 6, everything is done in inputs.conf. Click new to add an input. Even if those aren't relevant in your deployment, most splunk apps. Windows Event Log In Splunk.
From docs.splunk.com
Upload the tutorial data Splunk Documentation Windows Event Log In Splunk In splunk 6, everything is done in inputs.conf. Here is a new inputs.conf stanza for you: Click remote event log collections. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how. Windows Event Log In Splunk.
From docs.splunk.com
Events viewer Splunk Documentation Windows Event Log In Splunk Click local event log collection. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Adding event ids to splunk. Click remote event log collections. In splunk 6, everything is done in inputs.conf. Under data, click data inputs. Ingesting events from the windows event log is not a complicated process, but. Windows Event Log In Splunk.
From www.detectionlab.network
Windows Event Forwarding DetectionLab Windows Event Log In Splunk Click the add data link in splunk home. In splunk 6, everything is done in inputs.conf. Under data, click data inputs. Adding event ids to splunk. Click remote event log collections. Make sure that your splunk. Click new to add an input. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make. Windows Event Log In Splunk.
From support.vectra.ai
Windows Event Log Ingestion Splunk (Syslog / Legacy) Configuration Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking. Windows Event Log In Splunk.
From geek-university.com
Monitor remote Windows event logs Splunk Windows Event Log In Splunk Here is a new inputs.conf stanza for you: Click the add data link in splunk home. Under data, click data inputs. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. When you experience issues getting event logs from remote windows servers, try these solutions to fix. Windows Event Log In Splunk.
From apps.splunk.com
Windows Event Logs Analysis Splunkbase Windows Event Log In Splunk Here is a new inputs.conf stanza for you: In splunk 6, everything is done in inputs.conf. Make sure that your splunk. Adding event ids to splunk. Click local event log collection. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Under data, click data inputs. Click. Windows Event Log In Splunk.
From www.tactig.com
How to Configure and Analyze Event Logs in Windows 10? Tactig Windows Event Log In Splunk Click local event log collection. Click new to add an input. Here is a new inputs.conf stanza for you: Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make. Windows Event Log In Splunk.
From infohub.delltechnologies.com
Configure a Splunk dashboard for the events Advanced Anomaly Windows Event Log In Splunk Click the add data link in splunk home. Make sure that your splunk. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Under data, click data inputs. Here is a new inputs.conf stanza for you: In splunk 6, everything is done in inputs.conf. Click new to add an input. Adding event. Windows Event Log In Splunk.
From www.atatus.com
15 Best Log Monitoring Tools and Event Logging Software in 2024 Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click the add data link in splunk home. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click new to add an input. Under data, click data. Windows Event Log In Splunk.
From www.splunk.com
Peeping Through Windows (Logs) Splunk Splunk Windows Event Log In Splunk Click local event log collection. Click new to add an input. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click remote event log collections. Under data,. Windows Event Log In Splunk.
From mindmajix.com
Splunk Windows Event Log Monitoring Data Mindmajix Windows Event Log In Splunk Click new to add an input. Click remote event log collections. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Under data, click data inputs. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in. Windows Event Log In Splunk.
From dokumen.tips
(PDF) Splunk and Windows Event Log Best Practices, Reduction Windows Event Log In Splunk Click the add data link in splunk home. Adding event ids to splunk. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Make sure that your splunk. Click new to add an. Windows Event Log In Splunk.
From support.vectra.ai
Windows Event Log Ingestion Splunk (Syslog / Legacy) Configuration Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Adding event ids to splunk. Make sure that your splunk. Click local event log collection. Click new to add an input. In splunk 6, everything is done in inputs.conf. Even if those aren't relevant in your deployment, most splunk apps that. Windows Event Log In Splunk.
From vedcraft.com
How Did We Increase Incident Analysis Efficiency By Over 40 using Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click local event log collection. Under data, click data inputs. Here is a new inputs.conf stanza for you: Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Even. Windows Event Log In Splunk.
From docs.splunk.com
Event monitoring Splunk Documentation Windows Event Log In Splunk Click the add data link in splunk home. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Click remote event log collections. In splunk 6, everything is done in inputs.conf. Click new. Windows Event Log In Splunk.
From geek-university.com
Collect event logs from a local Windows machine Splunk Windows Event Log In Splunk Click local event log collection. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Click remote event log collections. Click the add data link in splunk home. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Search indexes. Windows Event Log In Splunk.
From subscription.packtpub.com
Splunk 7.x Quick Start Guide Windows Event Log In Splunk Click remote event log collections. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click new to add an input. In splunk 6, everything is done in inputs.conf. Under data, click data inputs. Ingesting events from the windows event log is not a complicated process, but. Windows Event Log In Splunk.
From www.vrogue.co
Solution Windows Splunk Logging Cheat Sheet V1 1 Stud vrogue.co Windows Event Log In Splunk Click new to add an input. Click local event log collection. Under data, click data inputs. Make sure that your splunk. In splunk 6, everything is done in inputs.conf. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Adding event ids to splunk. Ingesting events from the windows event log is. Windows Event Log In Splunk.
From subscription.packtpub.com
Splunk events Splunk 7.x Quick Start Guide Windows Event Log In Splunk Make sure that your splunk. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click local event log collection. Click the add data link in splunk home. Here. Windows Event Log In Splunk.
From www.dnsstuff.com
SolarWinds vs. Splunk DNSstuff Windows Event Log In Splunk Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click the add data link in splunk home. In splunk 6, everything is done in inputs.conf. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. When you. Windows Event Log In Splunk.
From www.vrogue.co
Splunk Cheat Sheet Windows Logging Cheat Sheet vrogue.co Windows Event Log In Splunk In splunk 6, everything is done in inputs.conf. Under data, click data inputs. Click remote event log collections. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Click local event log collection. Here is a new inputs.conf stanza for you: Adding event ids to splunk. Make sure that your splunk. Click. Windows Event Log In Splunk.
From docs.splunk.com
Basic searches and search results Splunk Documentation Windows Event Log In Splunk Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click local event log collection. Adding event ids to splunk. Make sure that your splunk. Click new to add an input. Ingesting events from the windows event log is not a complicated process, but you'll typically need. Windows Event Log In Splunk.
From geek-university.com
Collect event logs from a local Windows machine Splunk Windows Event Log In Splunk Click new to add an input. Adding event ids to splunk. In splunk 6, everything is done in inputs.conf. Here is a new inputs.conf stanza for you: Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Make sure that your splunk. Click the add data link in splunk home. Click. Windows Event Log In Splunk.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log In Splunk Make sure that your splunk. Adding event ids to splunk. In splunk 6, everything is done in inputs.conf. Click remote event log collections. Click new to add an input. Click the add data link in splunk home. Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the.. Windows Event Log In Splunk.
From apps.splunk.com
Windows Event Logs Analysis Splunkbase Windows Event Log In Splunk Here is a new inputs.conf stanza for you: Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Click the add data link in splunk home. In splunk 6, everything is done in inputs.conf. When you experience issues getting event logs from remote windows servers, try these. Windows Event Log In Splunk.
From geek-university.com
Install a Splunk forwarder on Windows Splunk Windows Event Log In Splunk Even if those aren't relevant in your deployment, most splunk apps that rely on windows event data are looking for it in the. Under data, click data inputs. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Here is a new inputs.conf stanza for you: Make sure. Windows Event Log In Splunk.
From geek-university.com
Collect event logs from a local Windows machine Splunk Windows Event Log In Splunk In splunk 6, everything is done in inputs.conf. When you experience issues getting event logs from remote windows servers, try these solutions to fix the problem: Click the add data link in splunk home. Click new to add an input. Under data, click data inputs. Ingesting events from the windows event log is not a complicated process, but you'll typically. Windows Event Log In Splunk.
From www.splunk.com
Splunk Command> Cluster Splunk Windows Event Log In Splunk Click the add data link in splunk home. Adding event ids to splunk. Here is a new inputs.conf stanza for you: Make sure that your splunk. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Click local event log collection. Under data, click data inputs. When you experience issues getting. Windows Event Log In Splunk.
From downloadsiteparro.weebly.com
Windows Event Logs In Splunk 6 downloadsiteparro Windows Event Log In Splunk Click new to add an input. Click local event log collection. Search indexes where windows event log data is being collected and filter down to the desired hosts to check. Adding event ids to splunk. Ingesting events from the windows event log is not a complicated process, but you'll typically need to make adjustments to how you. Click remote event. Windows Event Log In Splunk.