Security Control List . This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. Scope, define, and maintain regulatory demands online in minutes. They are based on the most common.
from smallbizepp.com
They are based on the most common. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks.
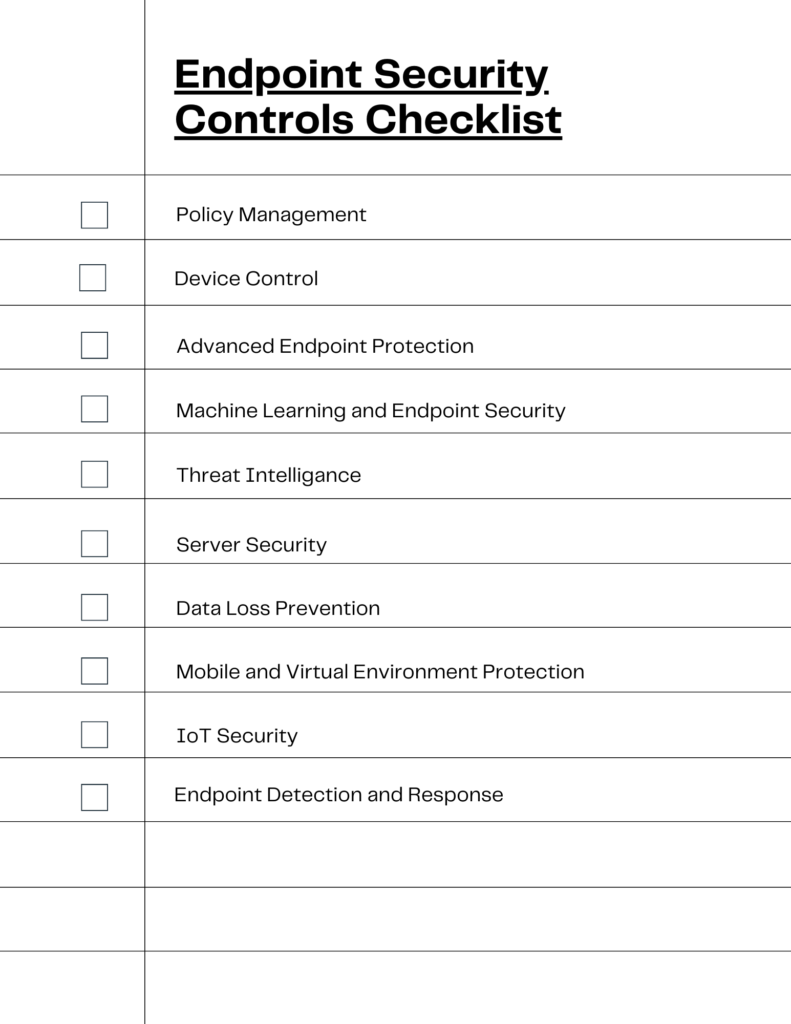
Endpoint Security Controls Plan your Defense!
Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. They are based on the most common. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information.
From www.sampletemplates.com
FREE 12+ Sample Security Risk Assessment Templates in PDF MS Word Excel Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. Scope, define, and maintain regulatory demands online in minutes. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This catalog of security controls allows federal government agencies the recommended security and privacy controls. Security Control List.
From grcready.com
Digital Security Controls Checklist GRCReady Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. The cis critical security controls (cis. Security Control List.
From helpdesk.kaseya.com
Build Custom Templates using the Secure Controls Framework Kaseya Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. They are based on the most common. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. Scope, define, and maintain regulatory demands online in minutes. This publication provides a catalog of security. Security Control List.
From blueteamresources.in
2023 Cyber Security Audit Checklist Strengthen Your Defense Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks.. Security Control List.
From www.exemplifygroup.com
The Ultimate Security Checklist eXemplify More Than A Technology Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. They are based on the most common. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This publication. Security Control List.
From www.pinterest.com
Browse Our Example of It Security Audit Checklist Template for Free Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security controls allows federal government agencies the recommended security and. Security Control List.
From www.scribd.com
Cybersecurity Checklist Security Computer Security Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This catalog. Security Control List.
From www.verizon.com
CIS Critical Security Controls Verizon Enterprise Solutions Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices. Security Control List.
From barokoks.github.io
Security Requirements Check List for Information TECHNOLOGY and Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. They are based on the most common. Scope, define, and maintain regulatory demands online in minutes. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls are a prioritized list. Security Control List.
From sprinto.com
ISO 27001 Audit Checklist [Updated] Sprinto Security Control List They are based on the most common. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This publication. Security Control List.
From purplesec.us
Types Of Security Controls Explained Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls (cis. Security Control List.
From www.selecthub.com
Endpoint Security Requirements & Features Checklist Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. They. Security Control List.
From www.slideserve.com
PPT Risk Management Framework (RMF) For Cleared Industry Partners Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. They are based on the most common. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices. Security Control List.
From bawn.com
Critical security controls for businesses Bawn Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. This publication provides. Security Control List.
From ezddies.com
ISO 27001 Controls Explained A Detailed Guide Secureframe (2022) Security Control List Scope, define, and maintain regulatory demands online in minutes. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security. Security Control List.
From wentzwu.com
Digest of NIST SP 80053 R5 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. Scope, define, and maintain regulatory demands online in minutes. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. The cis critical security controls (cis controls) are. Security Control List.
From huntsmansecurity.com
Understanding Australia’s Essential Eight Cyber Security Strategies Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls are a prioritized list of measures that organizations can take to. Security Control List.
From sprinto.com
Guide to ISO 27001 Annex A Controls (Updated) Sprinto Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. This publication provides a catalog of security and privacy controls for information. Security Control List.
From spectralops.io
ISO/IEC 27001 Compliance SelfAssessment The Ultimate ISO 27001 Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This catalog of security controls allows federal government agencies the recommended. Security Control List.
From www.vrogue.co
Nathnac Risk Assessment Risk Management Checklist vrogue.co Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. They are based on the most common. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber. Security Control List.
From drata.com
ISO 27001 Controls A Guide to Annex A Drata Security Control List Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls are a prioritized list of measures that organizations can take to. Security Control List.
From sprinto.com
The Ultimate SOC 2 Controls List Sprinto Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best. Security Control List.
From www.clarusft.com
PaaS and SaaS What you need to know Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information.. Security Control List.
From www.pinterest.co.uk
Building Security Checklist Awesome 28 Of Blank Security Checklist Security Control List The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. Scope, define, and maintain regulatory demands. Security Control List.
From www.studypool.com
SOLUTION Cyber security controls checklist Studypool Security Control List Scope, define, and maintain regulatory demands online in minutes. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. This publication provides. Security Control List.
From www.eits.com
What You Need To Know About CIS Controls Version 8 » EITS Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls (cis. Security Control List.
From www.scribd.com
Security Inspection Checklist PDF Security Clearance Classified Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information.. Security Control List.
From www.securityhq.com
Cyber Security Checklist [Infographic] SecurityHQ Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. This catalog of security controls allows federal government agencies the recommended security and. Security Control List.
From www.pivotpointsecurity.com
ISO 27001 Checklist (Free PDF & XLS Downloads) Pivot Point Security Security Control List They are based on the most common. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls (cis controls) are a. Security Control List.
From its.fsu.edu
IT Network Security Standard Information Technology Services Security Control List The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. Scope, define, and maintain regulatory demands online in minutes. This publication. Security Control List.
From www.securityscientist.net
20 NIST Control Families Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. They are based on the most common. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that. Security Control List.
From hyperproof.io
NIST 80053 Compliance Improve Your Security System [Guide] Security Control List This publication provides a catalog of security and privacy controls for information systems and organizations to protect. They are based on the most common. This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that. Security Control List.
From smallbizepp.com
Endpoint Security Controls Plan your Defense! Security Control List Scope, define, and maintain regulatory demands online in minutes. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This catalog of security controls allows federal government agencies. Security Control List.
From its.fsu.edu
IT Physical Security Standard Information Technology Services Security Control List This catalog of security controls allows federal government agencies the recommended security and privacy controls for federal information. The cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen. They are based on the most common. The cis critical security controls are a prioritized list of measures that. Security Control List.
From minorikk.com
CIS Controls V8 Vs. CIS Top 20 Critical Security Controls (2023) Security Control List Scope, define, and maintain regulatory demands online in minutes. They are based on the most common. The cis critical security controls are a prioritized list of measures that organizations can take to mitigate cyber risks. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. The cis critical security controls (cis controls) are. Security Control List.