Palo Alto Hip Features . Learn more about hip profiles used in rules and how hip checks for the host os version and much more. Configure hip exceptions for patch management. Today we will discuss host information profile or hip for short. Hello everyone and welcome to another episode of pancast. For more information on the hip. Hip objects are used to define objects for a host information profile (hip). The hip profiles used in rules assessment checks to see if. This feature is all about. To enable the use of host information in policy enforcement, you must complete the following steps. Hip objects provide the matching criteria for filtering the raw data reported by an. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to.
from help.zscaler.com
Learn more about hip profiles used in rules and how hip checks for the host os version and much more. Hello everyone and welcome to another episode of pancast. This feature is all about. Today we will discuss host information profile or hip for short. The hip profiles used in rules assessment checks to see if. To enable the use of host information in policy enforcement, you must complete the following steps. For more information on the hip. Hip objects provide the matching criteria for filtering the raw data reported by an. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to.
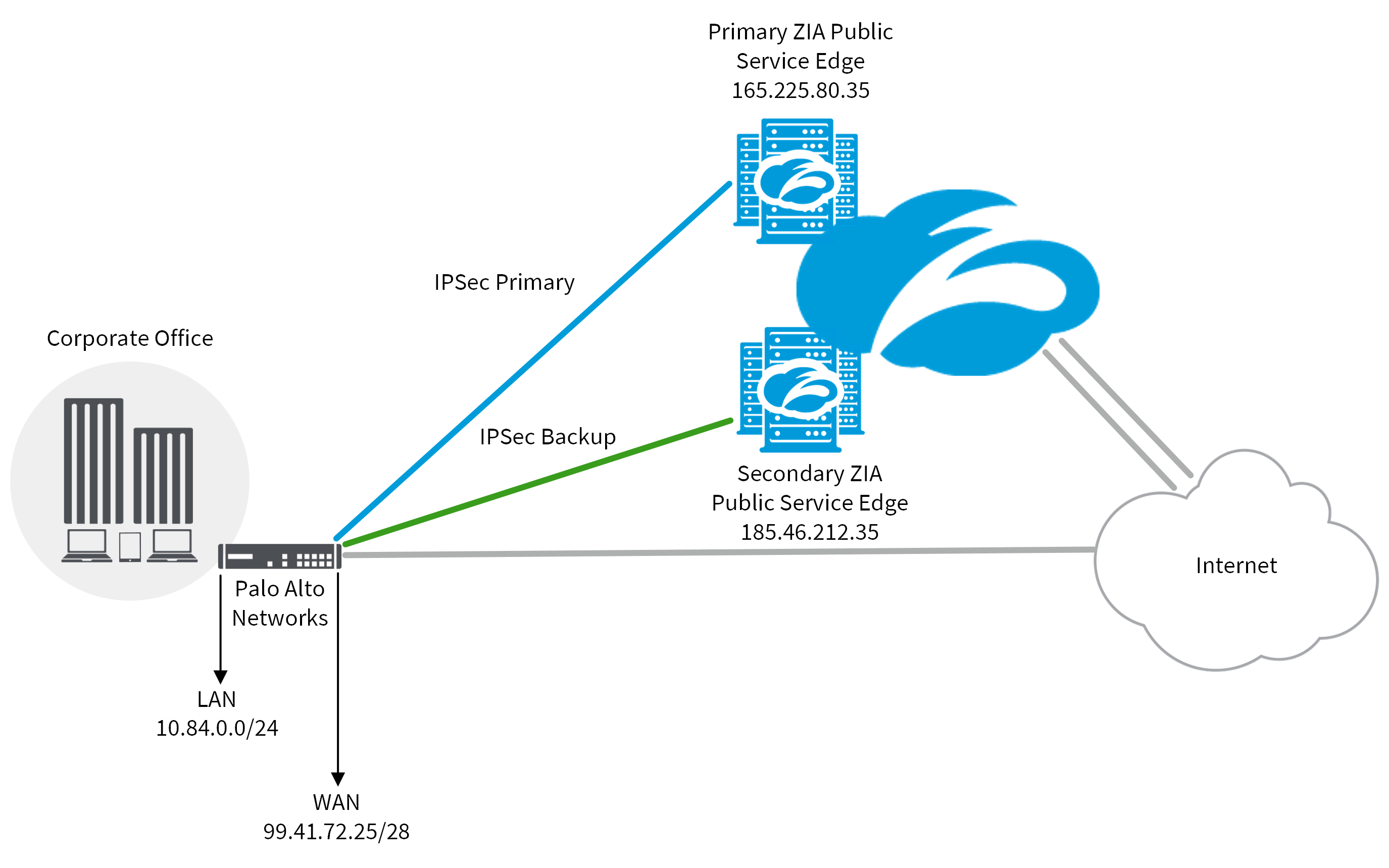
IPSec VPN Configuration Guide for Palo Alto Networks Firewall Zscaler
Palo Alto Hip Features Hip objects are used to define objects for a host information profile (hip). How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Learn more about hip profiles used in rules and how hip checks for the host os version and much more. Today we will discuss host information profile or hip for short. The hip profiles used in rules assessment checks to see if. This feature is all about. Hip objects provide the matching criteria for filtering the raw data reported by an. Hello everyone and welcome to another episode of pancast. For more information on the hip. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. To enable the use of host information in policy enforcement, you must complete the following steps. Hip objects are used to define objects for a host information profile (hip). Configure hip exceptions for patch management.
From usermanual.wiki
How to guide palo alto networks platform Palo Alto Hip Features Configure hip exceptions for patch management. Hip objects provide the matching criteria for filtering the raw data reported by an. To enable the use of host information in policy enforcement, you must complete the following steps. Learn more about hip profiles used in rules and how hip checks for the host os version and much more. This feature is all. Palo Alto Hip Features.
From www.enbitcon.com
Palo Alto PA5220 Professional Bundle Professional Bundle 5 Years Palo Alto Hip Features Learn more about hip profiles used in rules and how hip checks for the host os version and much more. For more information on the hip. To enable the use of host information in policy enforcement, you must complete the following steps. Hip objects provide the matching criteria for filtering the raw data reported by an. Today we will discuss. Palo Alto Hip Features.
From www.packetswitch.co.uk
Palo Alto Ansible Example Interfaces and Zones Palo Alto Hip Features How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. The hip profiles used in rules assessment checks to see if. Hip objects provide the matching criteria for filtering the raw data reported by an. To enable the use of host information in policy enforcement, you must complete. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. For more information on the hip. The hip profiles used in rules assessment checks to see if. Configure hip exceptions for patch management. Hip objects are used to define objects for a host information profile (hip).. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Today we will discuss host information profile or hip for short. Hip objects are used to define objects for a host information profile (hip). For more information on the hip. This feature is all about. This document provides. Palo Alto Hip Features.
From www.youtube.com
Components and Operation of SP3 Palo Alto NGFW YouTube Palo Alto Hip Features Today we will discuss host information profile or hip for short. Hello everyone and welcome to another episode of pancast. Hip objects provide the matching criteria for filtering the raw data reported by an. Configure hip exceptions for patch management. Learn more about hip profiles used in rules and how hip checks for the host os version and much more.. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features For more information on the hip. To enable the use of host information in policy enforcement, you must complete the following steps. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Hip objects provide the matching criteria for filtering the raw data reported by an.. Palo Alto Hip Features.
From help.zscaler.com
IPSec VPN Configuration Guide for Palo Alto Networks Firewall Zscaler Palo Alto Hip Features Learn more about hip profiles used in rules and how hip checks for the host os version and much more. For more information on the hip. Today we will discuss host information profile or hip for short. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Configure. Palo Alto Hip Features.
From www.sfgate.com
Historic Palo Alto hotel reopens with new name, rooftop bar Palo Alto Hip Features For more information on the hip. Learn more about hip profiles used in rules and how hip checks for the host os version and much more. Today we will discuss host information profile or hip for short. Hip objects provide the matching criteria for filtering the raw data reported by an. This document provides an overview of the various settings. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features To enable the use of host information in policy enforcement, you must complete the following steps. The hip profiles used in rules assessment checks to see if. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Learn more about hip profiles used in rules and how hip. Palo Alto Hip Features.
From help.sumologic.com
Palo Alto Networks 9 Sumo Logic Docs Palo Alto Hip Features Configure hip exceptions for patch management. This feature is all about. Today we will discuss host information profile or hip for short. Hip objects are used to define objects for a host information profile (hip). Learn more about hip profiles used in rules and how hip checks for the host os version and much more. The hip profiles used in. Palo Alto Hip Features.
From thietbimang.com
Bài viết về thiết bị tường lửa firewall Palo Alto Networks PA410 từ chuyên gia mạng Palo Alto Hip Features Configure hip exceptions for patch management. To enable the use of host information in policy enforcement, you must complete the following steps. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Learn more about hip profiles used in rules and how hip checks for the host os. Palo Alto Hip Features.
From epos.myesr.org
EPOS™ Palo Alto Hip Features Today we will discuss host information profile or hip for short. The hip profiles used in rules assessment checks to see if. Hip objects are used to define objects for a host information profile (hip). To enable the use of host information in policy enforcement, you must complete the following steps. How to configure hip object, hip profile for matching,. Palo Alto Hip Features.
From knowledgebase.paloaltonetworks.com
HIP_Profile_NO_match_B. png Palo Alto Hip Features Hello everyone and welcome to another episode of pancast. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. The hip profiles used in rules assessment checks to see if. This feature is all about. Hip objects are used to define objects for a host information profile (hip).. Palo Alto Hip Features.
From www.prnewswire.com
Palo Alto Networks Announces PANOS 11.0 Nova to Keep Organizations One Step Ahead of Zero Day Palo Alto Hip Features Hello everyone and welcome to another episode of pancast. Hip objects provide the matching criteria for filtering the raw data reported by an. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. The hip profiles used in rules assessment checks to see if. This feature is all. Palo Alto Hip Features.
From regenexx.com
Periacetabular Osteotomy Should You Get Hip PAO Surgery? Regenexx Palo Alto Hip Features This feature is all about. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. To enable the use of host information in policy enforcement, you must complete the following steps. Hello everyone and welcome to another episode of pancast. How to configure hip object, hip. Palo Alto Hip Features.
From www.youtube.com
Palo Alto Networks PA820 Firewall Review An Overview of Features, Benefits, & Specs YouTube Palo Alto Hip Features Configure hip exceptions for patch management. For more information on the hip. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. The hip profiles used in rules assessment checks to see if. To enable the use of host information in policy enforcement, you must complete the following. Palo Alto Hip Features.
From www.youtube.com
Palo Alto Training Part11_Content ID and SP3 Architecture YouTube Palo Alto Hip Features Configure hip exceptions for patch management. To enable the use of host information in policy enforcement, you must complete the following steps. For more information on the hip. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Today we will discuss host information profile or. Palo Alto Hip Features.
From www.youtube.com
Core Features Palo Alto Networks FireWall Concepts Training Series YouTube Palo Alto Hip Features For more information on the hip. Learn more about hip profiles used in rules and how hip checks for the host os version and much more. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Today we will discuss host information profile or hip for short. The. Palo Alto Hip Features.
From docs.paloaltonetworks.com
Enhanced HIP Remediation Process Palo Alto Hip Features Configure hip exceptions for patch management. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Hello everyone and welcome to another episode of pancast. For more information on the hip. Hip objects are used to define objects for a host information profile (hip). Today we. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features Hip objects provide the matching criteria for filtering the raw data reported by an. Learn more about hip profiles used in rules and how hip checks for the host os version and much more. For more information on the hip. Hip objects are used to define objects for a host information profile (hip). This document provides an overview of the. Palo Alto Hip Features.
From www.ncnonline.net
Palo Alto Networks Leads the Industry to AIPowered SASE Palo Alto Hip Features How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Hip objects are used to define objects for a host information profile (hip). Hello. Palo Alto Hip Features.
From www.linkedin.com
Palo Alto GlobalProtect and HIP Checks/Policy Palo Alto Hip Features How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Configure hip exceptions for patch management. Hip objects provide the matching criteria for filtering the raw data reported by an. Today we will discuss host information profile or hip for short. Hello everyone and welcome to another episode. Palo Alto Hip Features.
From www.youtube.com
Global Protect with HIP Configuration in Palo Alto Concept LAB DAY 47 PaloAltoTraining Palo Alto Hip Features Hip objects provide the matching criteria for filtering the raw data reported by an. Configure hip exceptions for patch management. The hip profiles used in rules assessment checks to see if. To enable the use of host information in policy enforcement, you must complete the following steps. Learn more about hip profiles used in rules and how hip checks for. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features For more information on the hip. Hip objects are used to define objects for a host information profile (hip). The hip profiles used in rules assessment checks to see if. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Learn more about hip profiles used. Palo Alto Hip Features.
From www.wwt.com
Palo Alto NGFW Foundations Lab WWT Palo Alto Hip Features Today we will discuss host information profile or hip for short. Hip objects are used to define objects for a host information profile (hip). How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. This document provides an overview of the various settings available for configuring hip checks. Palo Alto Hip Features.
From cybersecurity-excellence-awards.com
Palo Alto Cybersecurity Excellence Awards Palo Alto Hip Features Hip objects are used to define objects for a host information profile (hip). For more information on the hip. Today we will discuss host information profile or hip for short. This feature is all about. Configure hip exceptions for patch management. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them. Palo Alto Hip Features.
From www.cozumpark.com
Palo Alto HIP nedir? Palo Alto HIP Konfigürasyonu Nasıl Yapılır? ÇözümPark Palo Alto Hip Features Hip objects provide the matching criteria for filtering the raw data reported by an. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Hello everyone and welcome to another episode of pancast. How to configure hip object, hip profile for matching, and finally the not. Palo Alto Hip Features.
From emre-ozeel-2245.medium.com
Palo Alto HIP nedir ve Palo Alto HIP Konfigürasyonu by Emre Ozel Medium Palo Alto Hip Features Hello everyone and welcome to another episode of pancast. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. To enable the use of host information in policy enforcement, you must complete the following steps. Configure hip exceptions for patch management. Learn more about hip profiles. Palo Alto Hip Features.
From www.xcitium.com
What Is Palo Alto Cortex XDR? Features Of Palo Alto Cortex XDR Palo Alto Hip Features This feature is all about. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Configure hip exceptions for patch management. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Hello everyone and. Palo Alto Hip Features.
From www.thenetworkdna.com
Revolutionize Your Network Security with NGFW Palo Alto Firewall Vs The Network DNA Palo Alto Hip Features This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Today we will discuss host information profile or hip for short. The hip profiles. Palo Alto Hip Features.
From www.youtube.com
Lecture 1 Palo Alto Interview Questions SP3 Architecture of Palo Alto firewall Training Palo Alto Hip Features To enable the use of host information in policy enforcement, you must complete the following steps. Hip objects are used to define objects for a host information profile (hip). For more information on the hip. Today we will discuss host information profile or hip for short. How to configure hip object, hip profile for matching, and finally the not matching. Palo Alto Hip Features.
From www.thenetworkdna.com
A quick study about Palo Alto Networks Firewalls and models with features and Capabilities The Palo Alto Hip Features Hello everyone and welcome to another episode of pancast. Hip objects are used to define objects for a host information profile (hip). This feature is all about. The hip profiles used in rules assessment checks to see if. Configure hip exceptions for patch management. How to configure hip object, hip profile for matching, and finally the not matching condition and. Palo Alto Hip Features.
From www.youtube.com
Palo Alto Training HIP Host Information Profiles YouTube Palo Alto Hip Features Hello everyone and welcome to another episode of pancast. How to configure hip object, hip profile for matching, and finally the not matching condition and then apply them to security rules. Configure hip exceptions for patch management. The hip profiles used in rules assessment checks to see if. To enable the use of host information in policy enforcement, you must. Palo Alto Hip Features.
From www.paloguard.com
Palo Alto Networks 10 Must haves for Detection and Response Palo Alto Hip Features This feature is all about. This document provides an overview of the various settings available for configuring hip checks for patch management and how these settings work together to. Hip objects provide the matching criteria for filtering the raw data reported by an. The hip profiles used in rules assessment checks to see if. Today we will discuss host information. Palo Alto Hip Features.