X Server Detection Exploit . A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. Checks if you're allowed to connect to the x server. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. The remote host is running an x11 server. If the x server is listening on tcp port 6000+n (where n is. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows.
from www.trendmicro.com
If the x server is listening on tcp port 6000+n (where n is. The remote host is running an x11 server. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to connect to the x server. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows.
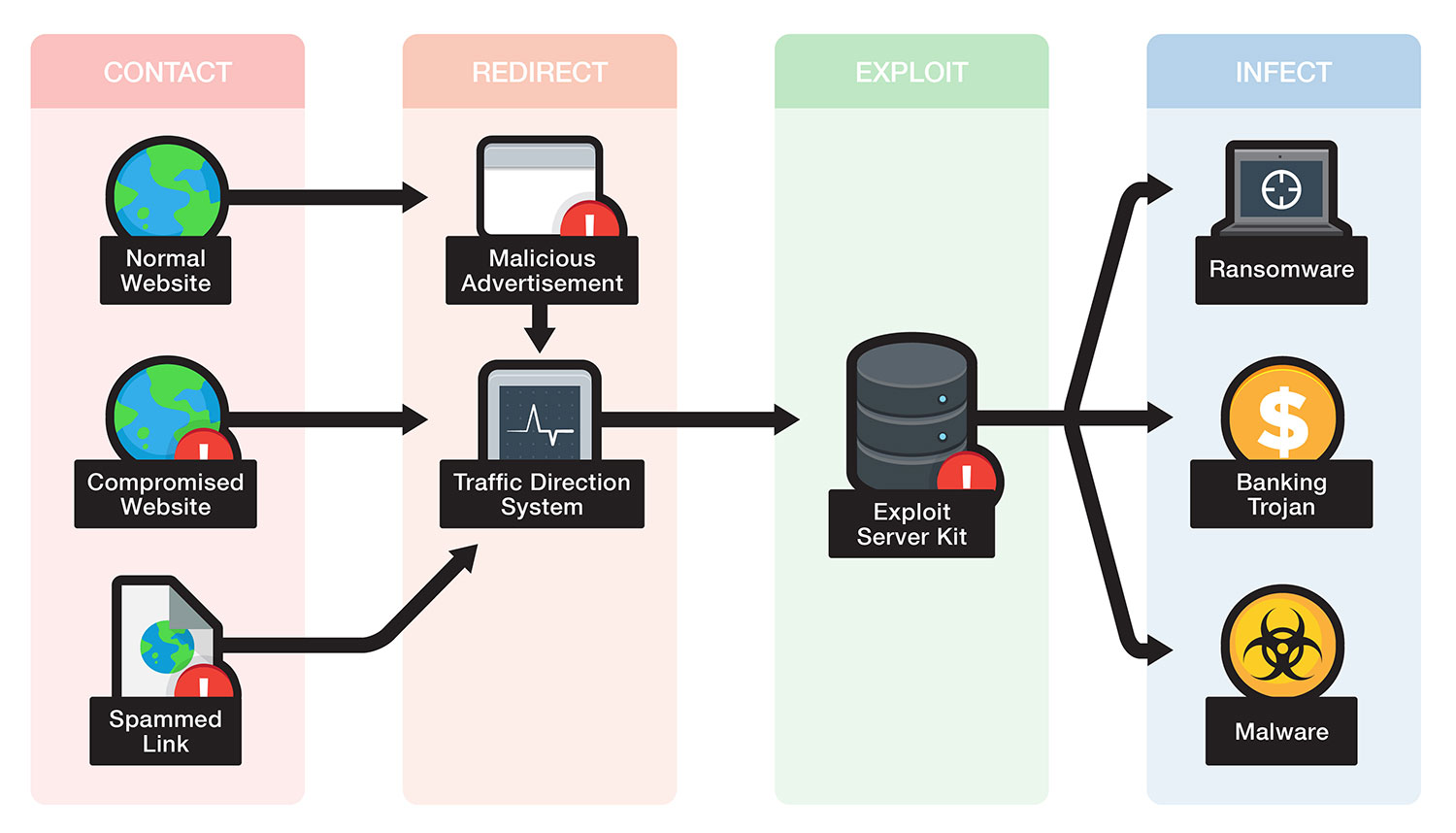
Exploit Kit Definition Trend Micro (US)
X Server Detection Exploit Checks if you're allowed to connect to the x server. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. The remote host is running an x11 server. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. Checks if you're allowed to connect to the x server. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. If the x server is listening on tcp port 6000+n (where n is. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect.
From www.kitploit.com
XSStrike v2.0 An Advanced XSS Detection And Exploitation Suit X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. Checks if you're allowed to connect to the x server. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root. X Server Detection Exploit.
From www.pinterest.com
Intelligent Endpoint Detection and Response technology X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. The remote host is running an x11 server. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. in this blog post we are going to describe some tools we created to find and exploit. X Server Detection Exploit.
From www.youtube.com
IIS Exploit can reboot your Windows Server; install patch KB3042553 X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. If the x server is listening on tcp port 6000+n (where n is. in this blog post we are going to describe some. X Server Detection Exploit.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. If the x server is listening on tcp port 6000+n (where n is. The remote host is running an x11 server. Checks if you're allowed to. X Server Detection Exploit.
From la-technologiesindia.com
Testing X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. If the x server is listening on tcp port 6000+n (where n is. The exploit is otherwise reliable, but depends on a specific version and can't. X Server Detection Exploit.
From www.exploit-db.com
Exploit Database SearchSploit Manual X Server Detection Exploit The remote host is running an x11 server. If the x server is listening on tcp port 6000+n (where n is. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. A. X Server Detection Exploit.
From www.youtube.com
phpmyadmin 0 day exploit server arbitrary file read YouTube X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. If the x server is listening on tcp port 6000+n (where n is. The remote host is running an x11 server. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks. X Server Detection Exploit.
From www.adlice.com
Exploits, Exploit kits and Protection Exploits Adlice Software X Server Detection Exploit The remote host is running an x11 server. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard,. X Server Detection Exploit.
From pentest-tools.com
How to detect and exploit CVE202126084, the Confluence Server RCE X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. If the x server is listening on tcp port 6000+n (where n is. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to connect to the x. X Server Detection Exploit.
From www.youtube.com
Exploiting JBOSS Server YouTube X Server Detection Exploit If the x server is listening on tcp port 6000+n (where n is. Checks if you're allowed to connect to the x server. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The. X Server Detection Exploit.
From www.youtube.com
Unleashed Rogue DHCP Server Detection YouTube X Server Detection Exploit A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. If the x server is listening on tcp port 6000+n (where n is. The exploit is otherwise reliable, but depends on a specific version and can't. X Server Detection Exploit.
From www.exploit-db.com
Rejetto HTTP File Server (HFS) 2.3.x Remote Command Execution (1 X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. The remote host is running an x11 server. A recent metasploit module was released and has simplified this attack by registering a. X Server Detection Exploit.
From pentest-tools.com
How to detect and exploit CVE202126084, the Confluence Server RCE X Server Detection Exploit The remote host is running an x11 server. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. If the x server is listening on tcp port 6000+n (where n is. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. Checks if you're allowed to. X Server Detection Exploit.
From securityxploded.com
XSS in action X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. The remote host is running an x11. X Server Detection Exploit.
From itcompany.com.au
Ransomware used Microsoft Exchange exploit to breach servers X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. Checks if you're allowed to connect to the x server. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The exploit is otherwise reliable, but depends on a specific version and. X Server Detection Exploit.
From www.youtube.com
MAXIMUM SEVERITY Windows Server Exploit Found (And Patched) YouTube X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. The remote host is running an x11 server. If the x server is listening on tcp port 6000+n (where n is. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. . X Server Detection Exploit.
From www.youtube.com
Exploit RDP CVE20190708 on Windows Server 2008 R2 YouTube X Server Detection Exploit If the x server is listening on tcp port 6000+n (where n is. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. Checks if you're allowed to connect to the x server. . X Server Detection Exploit.
From www.torchstoneglobal.com
Exploiting Vulnerabilities in the Attack Cycle TorchStone Global X Server Detection Exploit Checks if you're allowed to connect to the x server. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. If the x server is listening on tcp port 6000+n (where n is. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root. X Server Detection Exploit.
From www.youtube.com
Exploit misconfigured NFS Server YouTube X Server Detection Exploit multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. If the x server is listening on tcp port 6000+n (where n is. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. The exploit is otherwise reliable, but depends. X Server Detection Exploit.
From twitter.com
Cybersecurity and Infrastructure Security Agency on Twitter "ICYMI X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. If the x server is listening on tcp port 6000+n (where n is. Checks if you're allowed to connect to the x server. The exploit is. X Server Detection Exploit.
From www.youtube.com
DLP Detection Server Installation YouTube X Server Detection Exploit A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to connect to the x. X Server Detection Exploit.
From exowrnrox.blob.core.windows.net
Hardware Vulnerability Define at Sandra Earle blog X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. in this blog post we are going to. X Server Detection Exploit.
From www.trendmicro.com
Exploit Kit Definition Trend Micro (US) X Server Detection Exploit The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. If the x server is listening on tcp port 6000+n (where n is. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. A recent metasploit module was released and has simplified this attack. X Server Detection Exploit.
From www.youtube.com
Exploit Windows Server 2003 YouTube X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The remote host. X Server Detection Exploit.
From www.crowdstrike.com
Introducing Falcon Hardware Enhanced Exploit Detection CrowdStrike X Server Detection Exploit multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. The remote host is running an x11 server. in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. If the x server is listening on tcp port 6000+n (where n. X Server Detection Exploit.
From pentest-tools.com
How to detect and exploit CVE202126084, the Confluence Server RCE X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. If the x server is listening on tcp port 6000+n (where n is. Checks if you're allowed to connect to the x server. The remote host is running an x11 server. multiple vulnerabilities allow a local or remote, unprivileged user to execute. X Server Detection Exploit.
From www.youtube.com
How to detect the presence of xData Ransomware and SMBv1 servers on X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to. X Server Detection Exploit.
From www.franksworld.com
Follina MSDT Exploit CVE202230190 Explained with Detection and X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. Checks if you're allowed to connect to the x server. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. A recent metasploit module was released and has simplified this. X Server Detection Exploit.
From exploit.ph
eXploit Authenticated Stored XSS in TangoCMS X Server Detection Exploit A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The remote host is running an x11 server. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. . X Server Detection Exploit.
From seguridadenlainformatica.com
【Exploit que es y como funciona 2023】 ️ X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. Checks if you're allowed to connect to the x server. If the x server is listening on tcp port 6000+n (where n. X Server Detection Exploit.
From aws.amazon.com
Using AWS security services to protect against, detect, and respond to X Server Detection Exploit A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. Checks if you're allowed to connect to. X Server Detection Exploit.
From pentest-tools.com
How to detect and exploit CVE202126084, the Confluence Server RCE X Server Detection Exploit in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to connect to the x server. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably. X Server Detection Exploit.
From www.youtube.com
Find Exploits & Get Root with Linux Exploit Suggester [Tutorial] YouTube X Server Detection Exploit The remote host is running an x11 server. The exploit is otherwise reliable, but depends on a specific version and can't (or doesn't) reliably autodetect. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. Checks if you're allowed to connect to the x server. A recent metasploit module was released. X Server Detection Exploit.
From sustainabilitycasestudy.blogspot.com
Sustainability Chapter 7 Information Security Threats and Policies In X Server Detection Exploit in this blog post we are going to describe some tools we created to find and exploit unauthenticated x windows. A recent metasploit module was released and has simplified this attack by registering a virtual keyboard, then. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. Checks if you're allowed to. X Server Detection Exploit.
From gbhackers.com
How to Detect Obfuscated Malware on Your Server X Server Detection Exploit If the x server is listening on tcp port 6000+n (where n is. in this article, we are going to see how to exploit the x11server unauthenticated access vulnerability. multiple vulnerabilities allow a local or remote, unprivileged user to execute arbitrary code with root privileges on the. Checks if you're allowed to connect to the x server. The. X Server Detection Exploit.