Transfer For Public Use Example . In this section, we will explore the most important concepts and position our study. How do i give the business partner working with me on a project access to sensitive server data? This guide is organised in six different steps to be followed to carry out a tia: There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. In the surplus case, taxes and. Document the transfer tool used. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. Several terms exist to denote. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Is it considered technology transfer when.
from merchantcostconsulting.com
Is it considered technology transfer when. In this section, we will explore the most important concepts and position our study. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. How do i give the business partner working with me on a project access to sensitive server data? The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. Document the transfer tool used. This guide is organised in six different steps to be followed to carry out a tia: Several terms exist to denote. In the surplus case, taxes and.
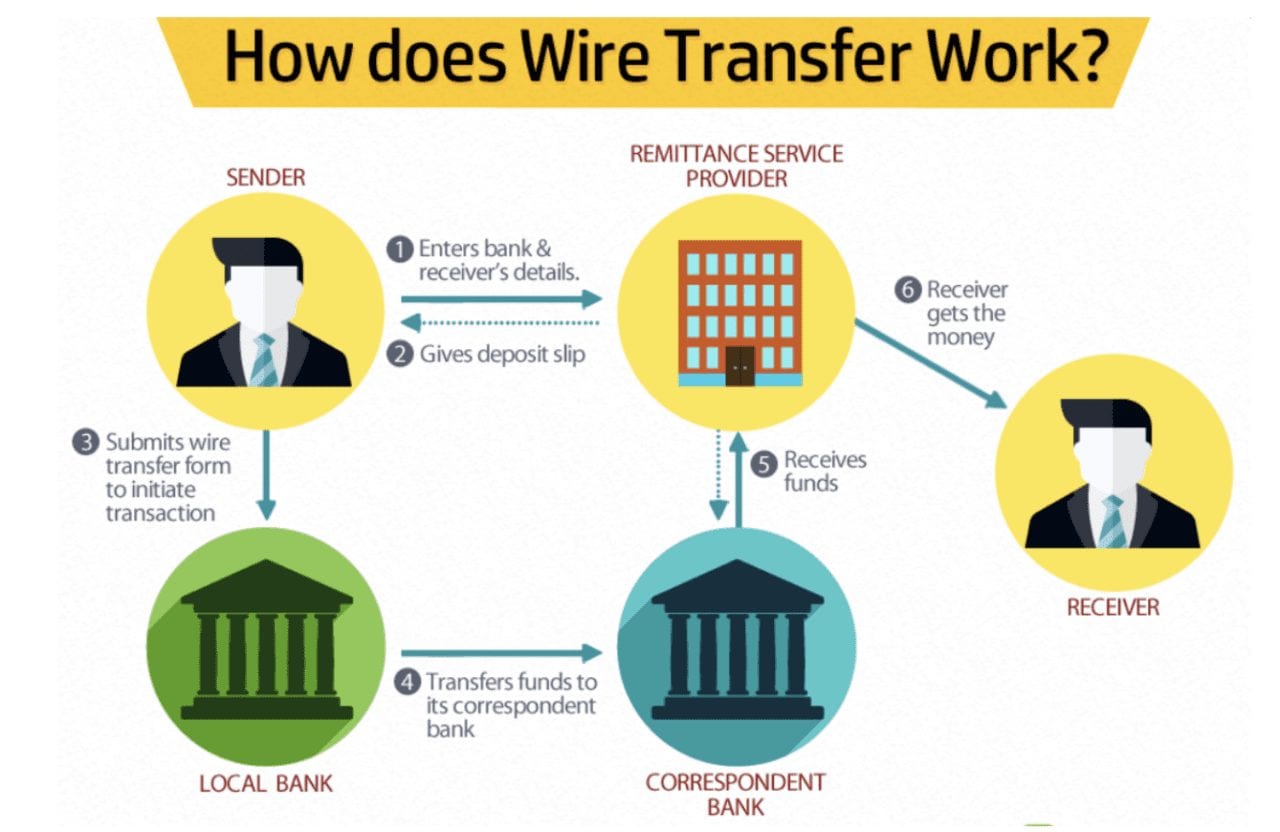
ACH vs. Wire Transfer What’s the Difference? Merchant Cost Consulting
Transfer For Public Use Example Is it considered technology transfer when. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Several terms exist to denote. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. Document the transfer tool used. In the surplus case, taxes and. How do i give the business partner working with me on a project access to sensitive server data? In this section, we will explore the most important concepts and position our study. This guide is organised in six different steps to be followed to carry out a tia: Is it considered technology transfer when.
From smbcart.com
Transfer Policy Employee Transfer Staff Transfer SMB CART Transfer For Public Use Example There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. In this section, we will explore the most important concepts and position our study. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register.. Transfer For Public Use Example.
From ubsapp.com
Inter Department Transfer Letter Meaning, Format, Examples, and More Transfer For Public Use Example Several terms exist to denote. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. How do i give the business partner working with me on a project access to sensitive server data? Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a. Transfer For Public Use Example.
From helpfulprofessor.com
37 Public Goods Examples (A to Z List) (2024) Transfer For Public Use Example Is it considered technology transfer when. Several terms exist to denote. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages.. Transfer For Public Use Example.
From www.slideserve.com
PPT Propaganda! Animal Farm ! PowerPoint Presentation, free download Transfer For Public Use Example Is it considered technology transfer when. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. This guide is organised in six different steps to be followed to carry out a tia: Several terms exist to denote. How do i give the business partner working with me on a. Transfer For Public Use Example.
From www.slideserve.com
PPT Propaganda Terms PowerPoint Presentation, free download ID2494854 Transfer For Public Use Example Document the transfer tool used. This guide is organised in six different steps to be followed to carry out a tia: In the surplus case, taxes and. In this section, we will explore the most important concepts and position our study. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that. Transfer For Public Use Example.
From www.slideserve.com
PPT PROPAGANDA!!!! PowerPoint Presentation ID3099641 Transfer For Public Use Example Is it considered technology transfer when. Several terms exist to denote. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. How do i. Transfer For Public Use Example.
From merchantcostconsulting.com
ACH vs. Wire Transfer What’s the Difference? Merchant Cost Consulting Transfer For Public Use Example In the surplus case, taxes and. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. Several terms exist to denote. Document the transfer. Transfer For Public Use Example.
From www.pinterest.com
Transfer Letter Format How To Write Transfer Letter? Samples Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. Several terms exist to denote. How do i give the business partner working with me on a project access to sensitive server data? In this section, we will explore the most important concepts and position our. Transfer For Public Use Example.
From www.aplustopper.com
Transfer Letter Format How To Write Transfer Letter? Samples Transfer For Public Use Example Document the transfer tool used. Several terms exist to denote. This guide is organised in six different steps to be followed to carry out a tia: How do i give the business partner working with me on a project access to sensitive server data? In this section, we will explore the most important concepts and position our study. There's lots. Transfer For Public Use Example.
From whoamuu.blogspot.com
Transfer Of Ownership Document Template HQ Printable Documents Transfer For Public Use Example In the surplus case, taxes and. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Document the transfer tool used. Is it considered technology transfer when. In this section, we will explore the most important concepts and position our study. How do i give the business partner working. Transfer For Public Use Example.
From telegra.ph
Sample College Transfer Essay Telegraph Transfer For Public Use Example In the surplus case, taxes and. Is it considered technology transfer when. Several terms exist to denote. How do i give the business partner working with me on a project access to sensitive server data? This guide is organised in six different steps to be followed to carry out a tia: Using a robust assessment framework to diagnose the ‘health’. Transfer For Public Use Example.
From www.slideshare.net
Transfer Essay Transfer For Public Use Example Several terms exist to denote. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. In this section, we will explore the most important concepts and position our study. This guide is organised in six different steps to be followed to carry out a tia: In the surplus case,. Transfer For Public Use Example.
From www.template.net
25+ Transfer Letter Samples Transfer For Public Use Example There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. In the surplus case, taxes and. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. How do i give the. Transfer For Public Use Example.
From www.template.net
44+ FREE Transfer Letter Templates PDF, Google DOC, Excel, Apple Pages Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. In the surplus case, taxes and. Document the transfer tool used. This guide is organised in six different steps to be followed to carry out a tia: Is it considered technology transfer when. In this section,. Transfer For Public Use Example.
From www.template.net
25+ Transfer Letter Samples Transfer For Public Use Example Several terms exist to denote. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. There's lots of ftp sites you can get into with. Transfer For Public Use Example.
From www.formsbank.com
Public Voucher For Purchases And Services Other Than Personal (Sf1034 Transfer For Public Use Example Is it considered technology transfer when. In this section, we will explore the most important concepts and position our study. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. There's lots of ftp sites you can get into with the 'anonymous' account and download, but. Transfer For Public Use Example.
From templatelab.com
40 Wire Transfer Form Templates [PDF, Word, Excel] Transfer For Public Use Example The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Is it considered technology transfer when. Document the transfer tool used. Several terms exist to denote. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor. Transfer For Public Use Example.
From bestlettertemplate.com
Transfer Letter Template for School Format, Sample & Example Transfer For Public Use Example This guide is organised in six different steps to be followed to carry out a tia: Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. Document the transfer tool used. In this section, we will explore the most important concepts and position our study. Is. Transfer For Public Use Example.
From www.examples.com
Transfer Request Letter 13+ Examples, Format, Word, Pages, PDF Transfer For Public Use Example There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. How do i give the business partner working with me on a project access to sensitive server data? Several terms exist to denote. Using a robust assessment framework to diagnose the ‘health’ of the technology. Transfer For Public Use Example.
From www.slideserve.com
PPT Propaganda Techniques PowerPoint Presentation, free download ID Transfer For Public Use Example In the surplus case, taxes and. This guide is organised in six different steps to be followed to carry out a tia: Document the transfer tool used. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Several terms exist to denote. Using a robust assessment framework to diagnose. Transfer For Public Use Example.
From www.examples.com
30+ College Essay Examples MS Word, PDF Examples Transfer For Public Use Example The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. This guide is organised in six different steps to be followed to carry out a tia: In this section, we will explore the most important concepts and position our study. How do i give the business partner working with. Transfer For Public Use Example.
From www.slideserve.com
PPT PROPAGANDA TECHNIQUES PowerPoint Presentation, free download ID Transfer For Public Use Example Several terms exist to denote. How do i give the business partner working with me on a project access to sensitive server data? In this section, we will explore the most important concepts and position our study. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor. Transfer For Public Use Example.
From alessa.com
SWIFT Wire Transfers What Compliance Teams Need to Know Alessa Transfer For Public Use Example In this section, we will explore the most important concepts and position our study. Document the transfer tool used. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. Is it considered technology transfer when. How do i give the business partner working with me on a project access. Transfer For Public Use Example.
From www.template.net
14+ Transfer Agreement Templates Free Word, PDF, Apple Pages, Google Transfer For Public Use Example There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. Several terms exist to denote. In this section, we will explore the most important concepts and position our study. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a. Transfer For Public Use Example.
From www.pinterest.com
International Wire Transfer form Template Fresh 7 Wire Transfer forms Transfer For Public Use Example This guide is organised in six different steps to be followed to carry out a tia: The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. In the surplus case, taxes and. Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way. Transfer For Public Use Example.
From propaganda7.weebly.com
Transfer propaganda Transfer For Public Use Example In the surplus case, taxes and. Is it considered technology transfer when. Several terms exist to denote. Document the transfer tool used. How do i give the business partner working with me on a project access to sensitive server data? There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that. Transfer For Public Use Example.
From www.slideserve.com
PPT Effective Transfer Payment Management PowerPoint Presentation Transfer For Public Use Example How do i give the business partner working with me on a project access to sensitive server data? Document the transfer tool used. In this section, we will explore the most important concepts and position our study. In the surplus case, taxes and. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a. Transfer For Public Use Example.
From mavink.com
Examples Of Transfer Propaganda Ads Transfer For Public Use Example This guide is organised in six different steps to be followed to carry out a tia: Document the transfer tool used. Is it considered technology transfer when. Several terms exist to denote. In the surplus case, taxes and. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. There's. Transfer For Public Use Example.
From www.printablesample.com
7 Free Sample Transfer Receipt Templates Printable Samples Transfer For Public Use Example Is it considered technology transfer when. How do i give the business partner working with me on a project access to sensitive server data? This guide is organised in six different steps to be followed to carry out a tia: In this section, we will explore the most important concepts and position our study. Document the transfer tool used. Several. Transfer For Public Use Example.
From www.ejet.com
What is Telegraphic Transfer ? Learn How to Make a Telegraphic Transfer Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. This guide is organised in six different steps to be followed to carry out a tia: Document the transfer tool used. The restricted transfer is from a public register and meets the relevant legal requirements relating. Transfer For Public Use Example.
From www.signnow.com
TRANSFER CERTIFICATE APPLICATION FORM Fill Out and Sign Printable PDF Transfer For Public Use Example How do i give the business partner working with me on a project access to sensitive server data? Several terms exist to denote. Is it considered technology transfer when. There's lots of ftp sites you can get into with the 'anonymous' account and download, but a 'public' site that allows anonymous uploads would be. The restricted transfer is from a. Transfer For Public Use Example.
From www.slideserve.com
PPT Transfer Pricing PowerPoint Presentation, free download ID4457224 Transfer For Public Use Example Document the transfer tool used. The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public register. How do i give the business partner working with me on a project access to sensitive server data? This guide is organised in six different steps to be followed to carry out a tia:. Transfer For Public Use Example.
From www.slideserve.com
PPT Propaganda Techniques PowerPoint Presentation, free download ID Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. This guide is organised in six different steps to be followed to carry out a tia: How do i give the business partner working with me on a project access to sensitive server data? In this. Transfer For Public Use Example.
From www.slideserve.com
PPT Propaganda Techniques PowerPoint Presentation, free download ID Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. Is it considered technology transfer when. This guide is organised in six different steps to be followed to carry out a tia: In the surplus case, taxes and. Several terms exist to denote. In this section,. Transfer For Public Use Example.
From www.sampleforms.com
FREE 23+ Transfer Forms in PDF Ms Word Excel Transfer For Public Use Example Using a robust assessment framework to diagnose the ‘health’ of the technology transfer environment is a way to identify existing barriers or poor linkages. This guide is organised in six different steps to be followed to carry out a tia: The restricted transfer is from a public register and meets the relevant legal requirements relating to access to that public. Transfer For Public Use Example.