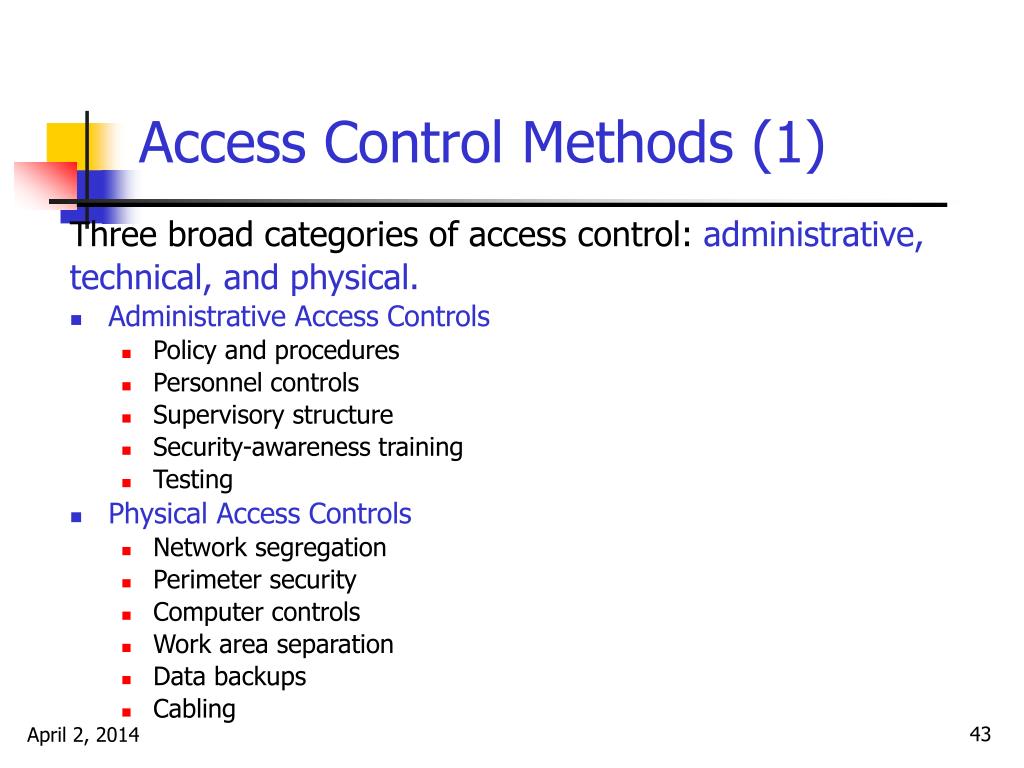
Access Control Methods . Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. Discretionary access control (dac) allows resource owners to control access. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. access control is the combination of policies and technologies that decide which authenticated users may access which resources. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. there are four main types of access control: access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). organizations have two general ways to determine someone’s access rights once past initial authentication: Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
from www.slideserve.com
access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Discretionary access control (dac) allows resource owners to control access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control is the combination of policies and technologies that decide which authenticated users may access which resources. organizations have two general ways to determine someone’s access rights once past initial authentication: Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. there are four main types of access control: access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or.
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free
Access Control Methods access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Robust access controls secure sensitive data by making it hard for hackers to gain access. there are four main types of access control: Discretionary access control (dac) allows resource owners to control access. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). organizations have two general ways to determine someone’s access rights once past initial authentication: access control is the combination of policies and technologies that decide which authenticated users may access which resources. Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: Robust access controls secure sensitive data by making it hard for hackers to gain access. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. access control methods include various techniques for enforcing access control policies,. Access Control Methods.
From slimjim.me
A Guide To The Basics Of Access Control Systems Access Control Methods Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. there are. Access Control Methods.
From www.securityguards.org.uk
Effective Access Control Methods Which One Is Right For You Access Control Methods access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control is the combination of policies and technologies that decide which authenticated. Access Control Methods.
From cyberhoot.com
Access Control Mechanism CyberHoot Access Control Methods Discretionary access control (dac) allows resource owners to control access. there are four main types of access control: access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). organizations have two general ways to determine someone’s access rights once past initial authentication: Robust access controls secure sensitive data by. Access Control Methods.
From trivestgroup.com
What is Physical Access Control and Which Types Do You Need? Access Control Methods access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. there are four main types of. Access Control Methods.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control Methods By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). there are four main types of access control: access control governs decisions and processes. Access Control Methods.
From www.youtube.com
Access Control Models An Overview of the Four Main Types YouTube Access Control Methods there are four main types of access control: access control is the combination of policies and technologies that decide which authenticated users may access which resources. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Robust access controls secure sensitive data by making it hard for hackers to gain. Access Control Methods.
From www.youtube.com
Access Control Methods and Models YouTube Access Control Methods access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). Discretionary access control (dac) allows resource owners to control access. access control is the combination of policies and technologies that decide which authenticated users may access which resources. access control is a proactive security measure that helps deter, detect,. Access Control Methods.
From www.securitycamerahub.com
Access Control Systems Security Camera Hub Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: there are four main types of access control: access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). Discretionary access control (dac) allows resource owners to control access. access control is crucial to identity. Access Control Methods.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Access Control Methods Robust access controls secure sensitive data by making it hard for hackers to gain access. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. Discretionary access control (dac) allows resource owners to control access. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges.. Access Control Methods.
From www.matrixaccesscontrol.com
An Easy Guide to Selecting Access Control Readers for your Organization Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: there are four main types of access control: access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. By controlling who or what has access to a resource, it ensures that only those with the necessary. Access Control Methods.
From www.sovereignfireandsecurity.co.uk
Access Control Methods Explained What Is Access Control? Access Control Methods Access control systems exclude malicious actors and allow legitimate users to use company tools safely. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for. Access Control Methods.
From www.aratek.co
Biometric Access Control System—A Complete Guide Access Control Methods access control is the combination of policies and technologies that decide which authenticated users may access which resources. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control is a proactive security. Access Control Methods.
From www.youtube.com
Access control in System Protection Role Based Access Control(RBAC Access Control Methods By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. there are four main types of access control: Authentication verifies users’ identities, authorization determines access requests and. Access Control Methods.
From www.slideserve.com
PPT IS3340 Windows Security Unit 2 Setting up Windows Systems with Access Control Methods access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control is the combination of policies and. Access Control Methods.
From www.getkisi.com
Access Control Systems Different Types and PDF Guide Kisi Access Control Methods Discretionary access control (dac) allows resource owners to control access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Robust access controls secure sensitive data by making it hard for hackers to gain access. access. Access Control Methods.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control Methods there are four main types of access control: Discretionary access control (dac) allows resource owners to control access. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes.. Access Control Methods.
From www.ipwncase.com
How to Install Access Control Systems ipwncase Access Control Methods there are four main types of access control: access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. organizations have two general ways to determine someone’s access rights once past initial authentication: Discretionary. Access Control Methods.
From www.melinet.am
Access control systems installation Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. Discretionary access control (dac) allows resource owners to control access. access control is crucial to identity and access management. Access Control Methods.
From www.slideteam.net
Access Control Methods Information Security Ppt Powerpoint Presentation Access Control Methods access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. access control is the combination of policies. Access Control Methods.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control Methods access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control is crucial to identity and access management (iam) strategies,. Access Control Methods.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Access Control Methods Discretionary access control (dac) allows resource owners to control access. access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. Robust access controls secure sensitive data by making it hard for hackers to gain access. organizations have two general ways to determine someone’s access rights once past initial authentication: there are. Access Control Methods.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control Methods access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Robust access controls secure sensitive data by making it hard for hackers to gain access. Discretionary access control (dac) allows resource owners to control access. Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks. Access Control Methods.
From thecyphere.com
Access Control Security Types Of Access Control Access Control Methods access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Discretionary access control (dac) allows. Access Control Methods.
From study.com
Access Control Types & Implementation Lesson Access Control Methods Discretionary access control (dac) allows resource owners to control access. organizations have two general ways to determine someone’s access rights once past initial authentication: access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control is the combination of policies and technologies that decide which authenticated users may. Access Control Methods.
From sierraws.com
Time and Attendance Access Control Sierra Access Control Methods access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. . Access Control Methods.
From cie-group.com
How to design an Access Control system Access Control Methods access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Discretionary access control (dac) allows resource owners to control access. access control governs decisions and processes of determining, documenting and managing the. Access Control Methods.
From www.ightysupport.com
What is a Biometric Access Control System? Types and Comparison. IT Access Control Methods Robust access controls secure sensitive data by making it hard for hackers to gain access. there are four main types of access control: By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control is crucial to identity and access management (iam). Access Control Methods.
From www.securityguards.org.uk
Effective Access Control Methods Which One Is Right For You Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: Access control systems exclude malicious actors and allow legitimate users to use company tools safely. By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access the data or service. access control methods include. Access Control Methods.
From www.linkedin.com
Multiple access protocols Access Control Methods Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. access control is the combination of policies and technologies that decide which authenticated users may access which resources. access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. there are. Access Control Methods.
From thecyphere.com
Access Control Security Types Of Access Control Access Control Methods access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). Discretionary access control (dac) allows resource owners to control access. By controlling who or what has access to a resource, it ensures that only. Access Control Methods.
From blog.golittlebird.com
The 4 Main Access Control Models What They Are & How They Work Access Control Methods access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Discretionary access control (dac) allows resource owners to control access.. Access Control Methods.
From www.slideserve.com
PPT Access Control Systems & Methodology PowerPoint Presentation ID Access Control Methods organizations have two general ways to determine someone’s access rights once past initial authentication: Access control systems exclude malicious actors and allow legitimate users to use company tools safely. there are four main types of access control: By controlling who or what has access to a resource, it ensures that only those with the necessary permissions can access. Access Control Methods.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Access Control Methods Access control systems exclude malicious actors and allow legitimate users to use company tools safely. access control methods include various techniques for enforcing access control policies, such as authentication, authorization, and accounting (aaa). Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access events for auditing purposes. Discretionary access control (dac). Access Control Methods.
From www.slideteam.net
Logical Access Control Policy Network Measures PPT Sample Access Control Methods access control governs decisions and processes of determining, documenting and managing the subjects (users, devices or. Discretionary access control (dac) allows resource owners to control access. organizations have two general ways to determine someone’s access rights once past initial authentication: Authentication verifies users’ identities, authorization determines access requests and what resources they can access, and accounting tracks access. Access Control Methods.