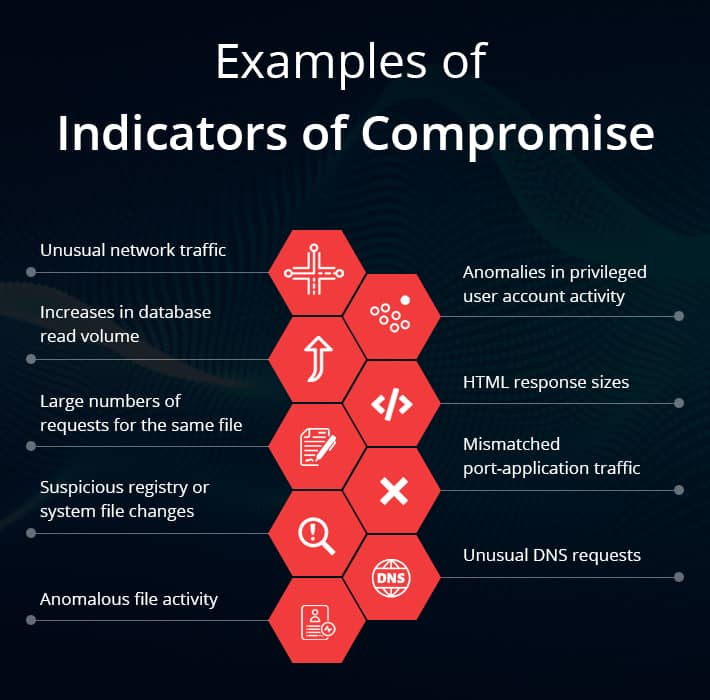
Security Indicators Of Compromise . Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. For example, iocs can be unusual network traffic. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their.
from www.lepide.com
An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. For example, iocs can be unusual network traffic. This guide explores the types of iocs, their. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. They are types of forensic evidence that point to the presence of malware or. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked.
What are Indicators of Compromise?
Security Indicators Of Compromise They are types of forensic evidence that point to the presence of malware or. Their presence indicates a vulnerability within. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. For example, iocs can be unusual network traffic. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types of iocs, their. They are types of forensic evidence that point to the presence of malware or. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Security Indicators Of Compromise For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. An indicator of compromise (ioc). Security Indicators Of Compromise.
From www.linkedin.com
Indicators of Compromise (IOCs) Explained Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. They are types of forensic evidence that point to the presence of malware or. Their presence indicates a vulnerability within. For example, iocs can be. Security Indicators Of Compromise.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Security Indicators Of Compromise For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint. Security Indicators Of Compromise.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.15] Elastic Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. Indicators of compromise (iocs) are. Security Indicators Of Compromise.
From virtualarmour.com
Identifying a Breach Finding Indicators of Compromise (IOC) Security Indicators Of Compromise Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be unusual network traffic. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. They are types of forensic evidence that point to the presence of malware. Security Indicators Of Compromise.
From www.linkedin.com
What are IT Security Indicators of Compromise? Security Indicators Of Compromise Their presence indicates a vulnerability within. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber. Security Indicators Of Compromise.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Security Indicators Of Compromise Their presence indicates a vulnerability within. They are types of forensic evidence that point to the presence of malware or. For example, iocs can be unusual network traffic. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack.. Security Indicators Of Compromise.
From www.redpacketsecurity.com
Indicators of compromise (IOCs) how we collect and use them Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise are behaviors or data which show that. Security Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Security Indicators Of Compromise Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. They are types of forensic evidence that point to the presence of malware or. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s. Security Indicators Of Compromise.
From www.trendmicro.com.ph
Indicators of compromise Definition Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are. Security Indicators Of Compromise.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.10] Elastic Security Indicators Of Compromise Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) refer to data that indicates a system may. Security Indicators Of Compromise.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. For example, iocs can. Security Indicators Of Compromise.
From www.crowdstrike.com
IOC Security Indicators of Attack vs. Indicators of Compromise Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise. Security Indicators Of Compromise.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Security Indicators Of Compromise Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. They are types of forensic evidence that point to the presence of malware or. Their presence indicates a vulnerability. Security Indicators Of Compromise.
From www.salvagedata.com
Cyber Security Awareness What Are Indicators of Compromise (IoC Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. This guide explores the types of iocs, their. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. Indicators of compromise (ioc) in cybersecurity refers. Security Indicators Of Compromise.
From www.scribd.com
What Are Indicators of Compromise (IoCs) PDF Security Computer Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Their presence indicates a vulnerability within. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. They are types of forensic evidence that point to the presence of malware or. Indicators of compromise (ioc) in cybersecurity refers. Security Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Security Indicators Of Compromise They are types of forensic evidence that point to the presence of malware or. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Their presence indicates a vulnerability within. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest. Security Indicators Of Compromise.
From www.semanticscholar.org
Table 1 from Understanding Indicators of Compromise against Cyber Security Indicators Of Compromise Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Their presence indicates a vulnerability within. This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion.. Security Indicators Of Compromise.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat.. Security Indicators Of Compromise.
From www.youtube.com
Understanding Indicators of Compromise for Incident Response YouTube Security Indicators Of Compromise They are types of forensic evidence that point to the presence of malware or. This guide explores the types of iocs, their. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs). Security Indicators Of Compromise.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Security Indicators Of Compromise Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types of iocs, their. They are types of forensic evidence that point to the presence of malware or. An indicator of compromise (ioc) is. Security Indicators Of Compromise.
From www.cyberwiki.in
Indicators of Compromise (IoCs) CyberWiki Encyclopedia of Cybersecurity Security Indicators Of Compromise For example, iocs can be unusual network traffic. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. This guide explores the types of iocs, their. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached.. Security Indicators Of Compromise.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.15] Elastic Security Indicators Of Compromise An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate. Security Indicators Of Compromise.
From widyasecurity.com
Apa itu Indicator of Compromise? • Widya Security Security Indicators Of Compromise An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. This guide explores the types of iocs, their. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise. Security Indicators Of Compromise.
From www.youtube.com
What are the Indicators of compromise YouTube Security Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate. Security Indicators Of Compromise.
From cyberwarzone.com
Indicators of Compromise (IoCs) in Cybersecurity Cyberwarzone Security Indicators Of Compromise Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. Indicators of compromise are behaviors or data which show that. Security Indicators Of Compromise.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Security Indicators Of Compromise Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that. Security Indicators Of Compromise.
From github.com
GitHub Log4j Security Indicators Of Compromise Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. For example, iocs can be unusual network traffic.. Security Indicators Of Compromise.
From securityboulevard.com
Indicators of Compromise (IOCs) and External Risk Monitoring Security Security Indicators Of Compromise Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may. Security Indicators Of Compromise.
From www.slideshare.net
Security Analytics to Identify the 12 Indicators of Compromise Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. For example, iocs can be unusual network traffic. An indicator of compromise (ioc) is evidence that someone may have. Security Indicators Of Compromise.
From cybersecurityresource.com
What Are Indicators Of Compromise? Cyber Security Resource Security Indicators Of Compromise Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Their presence indicates a vulnerability within. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. For example, iocs can be unusual network traffic. They are types of forensic evidence that point to the presence of malware or. An indicator. Security Indicators Of Compromise.
From www.trendmicro.com.my
Empowering the Analyst Indicators of Compromise Security News Security Indicators Of Compromise For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types. Security Indicators Of Compromise.
From practonet.com
Indicators of compromise (IOCs) Cyber Security, Networking Security Indicators Of Compromise Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. They are types of forensic evidence that point to the presence of malware or. This guide explores the types of iocs, their. Their presence indicates a vulnerability within. Indicators of compromise (iocs) are artifacts that indicate a potential. Security Indicators Of Compromise.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Security Indicators Of Compromise Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion.. Security Indicators Of Compromise.
From www.securebrain.co.jp
The Impact of Indicators of Compromise (IoCs) in Cybersecurity Security Indicators Of Compromise For example, iocs can be unusual network traffic. Their presence indicates a vulnerability within. They are types of forensic evidence that point to the presence of malware or. This guide explores the types of iocs, their. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. An indicator. Security Indicators Of Compromise.