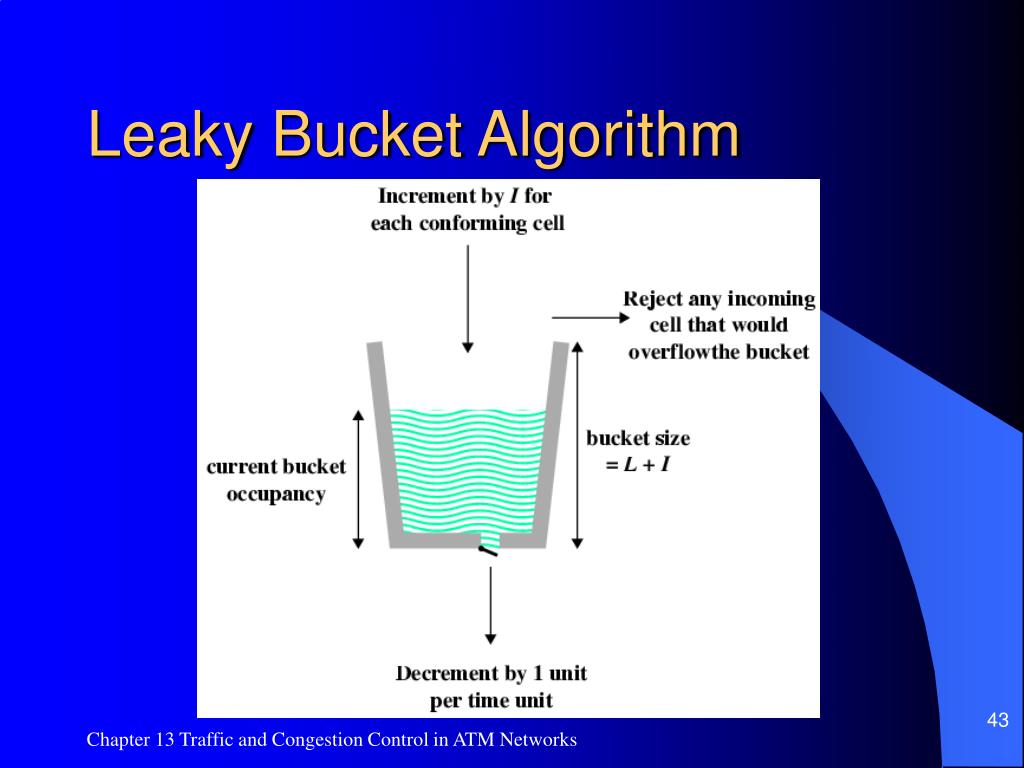
Leaky Bucket Algorithm Flowchart . The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. Leaky bucket algorithm for congestion control. Compare leaky bucket with token bucket and see examples, code and difference. This is one of the algorithm used for congestion control in network layer. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. See examples, diagrams, and java. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Picture a bucket with a.
from www.slideserve.com
The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Leaky bucket algorithm for congestion control. Compare leaky bucket with token bucket and see examples, code and difference. See examples, diagrams, and java. This is one of the algorithm used for congestion control in network layer. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Picture a bucket with a. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a.
PPT Chapter 13 PowerPoint Presentation, free download ID4138688
Leaky Bucket Algorithm Flowchart Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Leaky bucket algorithm for congestion control. Picture a bucket with a. Compare leaky bucket with token bucket and see examples, code and difference. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. See examples, diagrams, and java.
From www.fatalerrors.org
Using pooling technology, token bucket algorithm and leaky bucket Leaky Bucket Algorithm Flowchart Compare leaky bucket with token bucket and see examples, code and difference. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Picture a bucket with a. Learn how to. Leaky Bucket Algorithm Flowchart.
From mozillazg.com
rate limiting 之 leaky bucket mozillazg's Blog Leaky Bucket Algorithm Flowchart The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Leaky bucket algorithm for congestion control. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. This is one of the algorithm used for congestion control in network layer. The leaky bucket is a traffic shaping. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Flowchart Picture a bucket with a. This is one of the algorithm used for congestion control in network layer. See examples, diagrams, and java. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Leaky bucket algorithm for congestion control. The leaky bucket is a traffic shaping algorithm used to control. Leaky Bucket Algorithm Flowchart.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm Flowchart See examples, diagrams, and java. Leaky bucket algorithm for congestion control. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. Learn how leaky bucket algorithm can smooth out bursty traffic and control. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Flowchart Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how to implement the leaky. Leaky Bucket Algorithm Flowchart.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm Flowchart See examples, diagrams, and java. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Compare leaky bucket with token bucket and see examples, code and difference. This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Flowchart The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Compare leaky bucket with token bucket and see examples, code and difference. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Learn how. Leaky Bucket Algorithm Flowchart.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Flowchart See examples, diagrams, and java. Picture a bucket with a. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how to control congestion in computer networks using the leaky bucket algorithm,. Leaky Bucket Algorithm Flowchart.
From blog.bytebytego.com
Rate Limiting Fundamentals by Alex Xu Leaky Bucket Algorithm Flowchart This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Compare leaky bucket with token bucket and see examples, code and difference. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Flowchart Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Leaky bucket algorithm for congestion control. Compare leaky bucket with token bucket and see examples, code and difference. See examples, diagrams, and java. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket. Leaky Bucket Algorithm Flowchart.
From www.slideserve.com
PPT Chapter 18 Frame Relay PowerPoint Presentation, free download Leaky Bucket Algorithm Flowchart Compare leaky bucket with token bucket and see examples, code and difference. Picture a bucket with a. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Leaky bucket algorithm. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Illustration of the GCRA (i,l) Algorithm as Leaky Bucket Download Leaky Bucket Algorithm Flowchart Picture a bucket with a. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. The leaky bucket algorithm provides an elegant solution to the problem of. Leaky Bucket Algorithm Flowchart.
From www.slideserve.com
PPT Lecture 10 PowerPoint Presentation, free download ID4737649 Leaky Bucket Algorithm Flowchart The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Compare leaky bucket with token bucket and see examples, code and difference. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Learn how leaky bucket algorithm can smooth out. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Flowchart Leaky bucket algorithm for congestion control. See examples, diagrams, and java. This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Picture a bucket with a. The leaky bucket algorithm provides an elegant solution to the problem. Leaky Bucket Algorithm Flowchart.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Algorithm Flowchart Picture a bucket with a. This is one of the algorithm used for congestion control in network layer. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Leaky bucket algorithm for congestion control. See examples, diagrams, and java. Learn how leaky bucket algorithm. Leaky Bucket Algorithm Flowchart.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Flowchart Compare leaky bucket with token bucket and see examples, code and difference. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. See examples,. Leaky Bucket Algorithm Flowchart.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Flowchart Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Picture a bucket with. Leaky Bucket Algorithm Flowchart.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Flowchart Leaky bucket algorithm for congestion control. Picture a bucket with a. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. This is one of the algorithm. Leaky Bucket Algorithm Flowchart.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Flowchart Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. This is one of the algorithm used for congestion control in network layer. Picture a bucket with a. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Leaky bucket. Leaky Bucket Algorithm Flowchart.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Flowchart Leaky bucket algorithm for congestion control. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. See examples, diagrams, and java. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Picture a bucket. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
2. Optimal control tokenbucket algorithm flowchart (part 1 Leaky Bucket Algorithm Flowchart This is one of the algorithm used for congestion control in network layer. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. See examples, diagrams, and java. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to implement the leaky bucket rate. Leaky Bucket Algorithm Flowchart.
From www.semanticscholar.org
Figure 3 from A secondorder leaky bucket algorithm to guarantee QoS in Leaky Bucket Algorithm Flowchart Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate. Leaky Bucket Algorithm Flowchart.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Flowchart The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer.. Leaky Bucket Algorithm Flowchart.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Flowchart Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Compare leaky bucket with token bucket. Leaky Bucket Algorithm Flowchart.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Leaky Bucket Algorithm Flowchart Picture a bucket with a. Leaky bucket algorithm for congestion control. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Compare leaky bucket with token bucket and see examples,. Leaky Bucket Algorithm Flowchart.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Flowchart This is one of the algorithm used for congestion control in network layer. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Picture a bucket with a. Leaky bucket algorithm for congestion control. See examples, diagrams, and java. Compare leaky bucket with token. Leaky Bucket Algorithm Flowchart.
From www.pinterest.com
This sample shows the Leaky Bucket Algorithm that is widely used in Leaky Bucket Algorithm Flowchart Picture a bucket with a. See examples, diagrams, and java. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. This is one of the algorithm used for congestion control in network layer. Leaky bucket algorithm for congestion control. Learn how to implement the leaky bucket rate limiting algorithm, which. Leaky Bucket Algorithm Flowchart.
From www.tech-maze.info
System Design Leaky Bucket Algorithm And Its UsesSystem Design Rohit Modi Leaky Bucket Algorithm Flowchart Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. Compare leaky bucket with token bucket and see examples, code and difference. Leaky bucket algorithm for congestion control. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. This is one of the. Leaky Bucket Algorithm Flowchart.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Flowchart Learn how leaky bucket algorithm can smooth out bursty traffic and control the rate of data transmission in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that. Leaky Bucket Algorithm Flowchart.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Flowchart This is one of the algorithm used for congestion control in network layer. Compare leaky bucket with token bucket and see examples, code and difference. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a. Learn how leaky bucket algorithm can smooth out bursty. Leaky Bucket Algorithm Flowchart.
From www.slideserve.com
PPT CS 456 Computer Networks Congestion Control/QoS PowerPoint Leaky Bucket Algorithm Flowchart Picture a bucket with a. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Compare leaky bucket with token bucket and see examples, code and difference. Learn how to implement the leaky bucket rate limiting. Leaky Bucket Algorithm Flowchart.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Flowchart Picture a bucket with a. Leaky bucket algorithm for congestion control. This is one of the algorithm used for congestion control in network layer. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Flowchart Compare leaky bucket with token bucket and see examples, code and difference. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at. Leaky Bucket Algorithm Flowchart.
From www.researchgate.net
Algorithm of optimal leaks management. Download Scientific Diagram Leaky Bucket Algorithm Flowchart The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Picture a bucket with a. Leaky bucket algorithm for congestion control. Learn how to control congestion in computer networks using the leaky bucket algorithm, which limits the rate and amount of. Compare leaky bucket with token bucket and see examples, code and difference. Learn how leaky. Leaky Bucket Algorithm Flowchart.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Leaky Bucket Algorithm Flowchart Compare leaky bucket with token bucket and see examples, code and difference. Learn how to implement the leaky bucket rate limiting algorithm, which uses a fifo queue with a fixed capacity to manage request rates. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Learn how leaky bucket algorithm can smooth out bursty traffic and. Leaky Bucket Algorithm Flowchart.