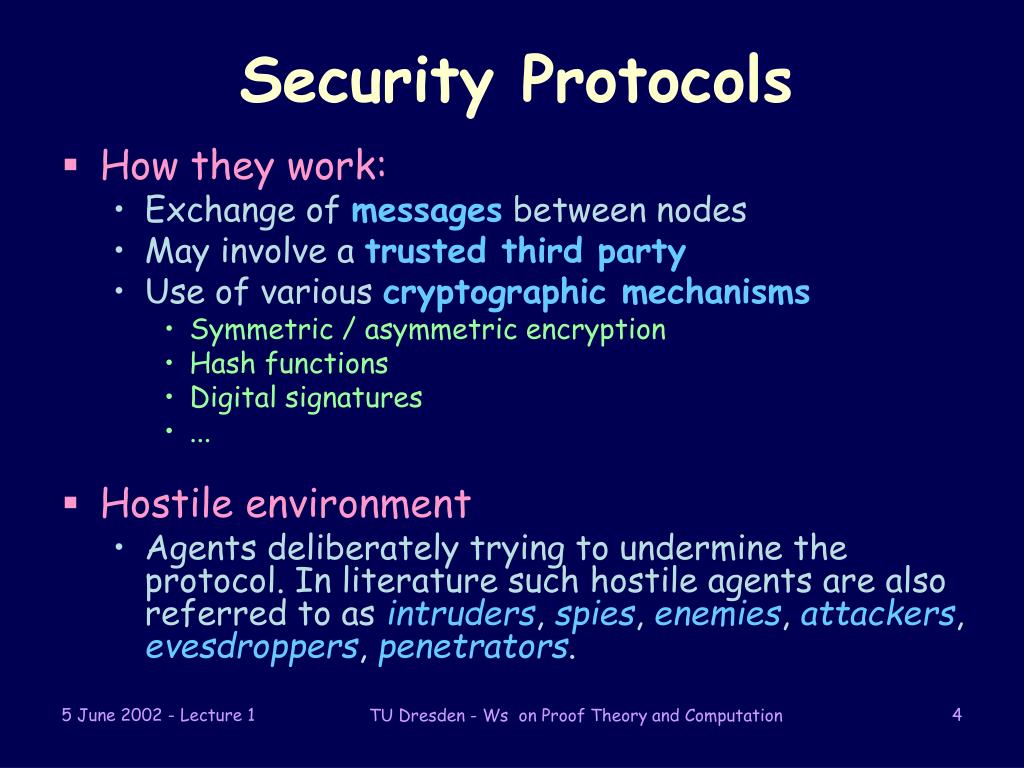
Examples Of Security Protocols . Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security.
from www.slideserve.com
There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security.
PPT Formal Methods for Security Protocols PowerPoint Presentation
Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the.
From www.bitdefender.com
Types of Security Protocols Bitdefender Cyberpedia Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Security protocols designed to protect. Examples Of Security Protocols.
From fity.club
Understanding Cluster Application Network Security Protocols Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such. Examples Of Security Protocols.
From purplesec.us
How To Develop & Implement A Network Security Plan Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. There are many examples of network security protocols creating safe, reliable interactions between. Examples Of Security Protocols.
From www.slideserve.com
PPT Formal Verification of Security Protocols an Introduction Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer. Examples Of Security Protocols.
From fity.club
Understanding Cluster Application Network Security Protocols Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From www.bitdefender.com
What is Data Encryption? Bitdefender Cyberpedia Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect. Examples Of Security Protocols.
From blog.usecure.io
7 Key steps to implement security awareness training Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From www.accuenergy.com
TLS 1.2 Transport Layer Security Protocol Accuenergy Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Employing a layered security approach is necessary to. Examples Of Security Protocols.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data,. Examples Of Security Protocols.
From fity.club
Understanding Cluster Application Network Security Protocols Examples Of Security Protocols Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between users and systems,. Examples Of Security Protocols.
From www.slideserve.com
PPT Chp . 8 ISP Responsibility PowerPoint Presentation, free Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. To fully secure their data, organizations must employ a combination of. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between. Examples Of Security Protocols.
From www.helpwire.app
A Complete Guide to IoT Protocols Examples Of Security Protocols Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Employing a layered security approach is necessary to. Examples Of Security Protocols.
From www.slideserve.com
PPT Formal Methods for Security Protocols PowerPoint Presentation Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From www.cloudflare.com
What is Transport Layer Security? TLS protocol Cloudflare Examples Of Security Protocols Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From www.bitdefender.com
Types of Security Protocols Bitdefender Cyberpedia Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to. Examples Of Security Protocols.
From www.myxxgirl.com
Network Protocol Map Osi Model Cybersecurity Infographic Networking Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. To fully secure their data, organizations must employ a combination of. Employing a layered security approach is necessary to. Examples Of Security Protocols.
From www.logsign.com
Cyber Security Protocols That You Should Know Logsign Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Security protocols designed to protect the application layer have many functions, from making sure the data. Examples Of Security Protocols.
From www.lifewire.com
OSI Model Reference Guide (With Examples) Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. Security protocols designed to protect the application layer have many functions, from making sure the data. Examples Of Security Protocols.
From www.slideserve.com
PPT Verification of Security Protocols PowerPoint Presentation, free Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting. Examples Of Security Protocols.
From www.youtube.com
Cyber Security for Absolute Beginners 9 TCP/IP Protocol YouTube Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer. Examples Of Security Protocols.
From www.slideserve.com
PPT Security PowerPoint Presentation ID22681 Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. To fully secure their data, organizations must employ a combination of. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to. Examples Of Security Protocols.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. To fully secure their data, organizations must employ a combination of. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From www.slideserve.com
PPT Part III Protocols PowerPoint Presentation, free download ID Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control,. Examples Of Security Protocols.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting. Examples Of Security Protocols.
From www.slideserve.com
PPT Analysis of Security Protocols (III) PowerPoint Presentation Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting. Examples Of Security Protocols.
From www.bitdefender.com
Types of Security Protocols Bitdefender Cyberpedia Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. To fully secure their data, organizations must employ a combination of.. Examples Of Security Protocols.
From www.slideserve.com
PPT Formal Methods for Security Protocols PowerPoint Presentation Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Network security encompasses protocols such as firewalls, intrusion detection and prevention. Examples Of Security Protocols.
From www.researchgate.net
The Basic Security Protocol Architecture Download Scientific Diagram Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the. Examples Of Security Protocols.
From subscription.packtpub.com
Secure Protocols and Their Use Cases CompTIA Security+ SY0601 Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Network security encompasses protocols such as firewalls, intrusion detection and prevention. Examples Of Security Protocols.
From www.slideteam.net
Network Layer Security Protocols Ppt Powerpoint Presentation Pictures Examples Of Security Protocols There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the. Examples Of Security Protocols.
From tiptopsecurity.com
How Does HTTPS Work? RSA Encryption Explained « TipTopSecurity Examples Of Security Protocols Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. There are many examples of network security protocols creating safe, reliable interactions between users and systems, especially in the. Network security encompasses protocols such as firewalls, intrusion detection and prevention. Examples Of Security Protocols.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Examples Of Security Protocols Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. There are many examples of network security protocols. Examples Of Security Protocols.
From gogetsecure.com
Network Security Protocols [An EasytoRead Guide] Examples Of Security Protocols Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to managing and transferring. Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. To fully secure their data, organizations must employ a combination of. Network security encompasses protocols such. Examples Of Security Protocols.
From www.ir.com
Understanding Network Security Tools & Protection IR Examples Of Security Protocols Employing a layered security approach is necessary to counteract evolving and sophisticated security threats. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting. Examples Of Security Protocols.
From www.slideserve.com
PPT Security Protocols PowerPoint Presentation, free Examples Of Security Protocols To fully secure their data, organizations must employ a combination of. Network security encompasses protocols such as firewalls, intrusion detection and prevention systems, network segmentation, access control, virtual private networks, and cloud security. Security protocols designed to protect the application layer have many functions, from making sure the data delivered to the user is safe, to detecting malicious activity, to. Examples Of Security Protocols.