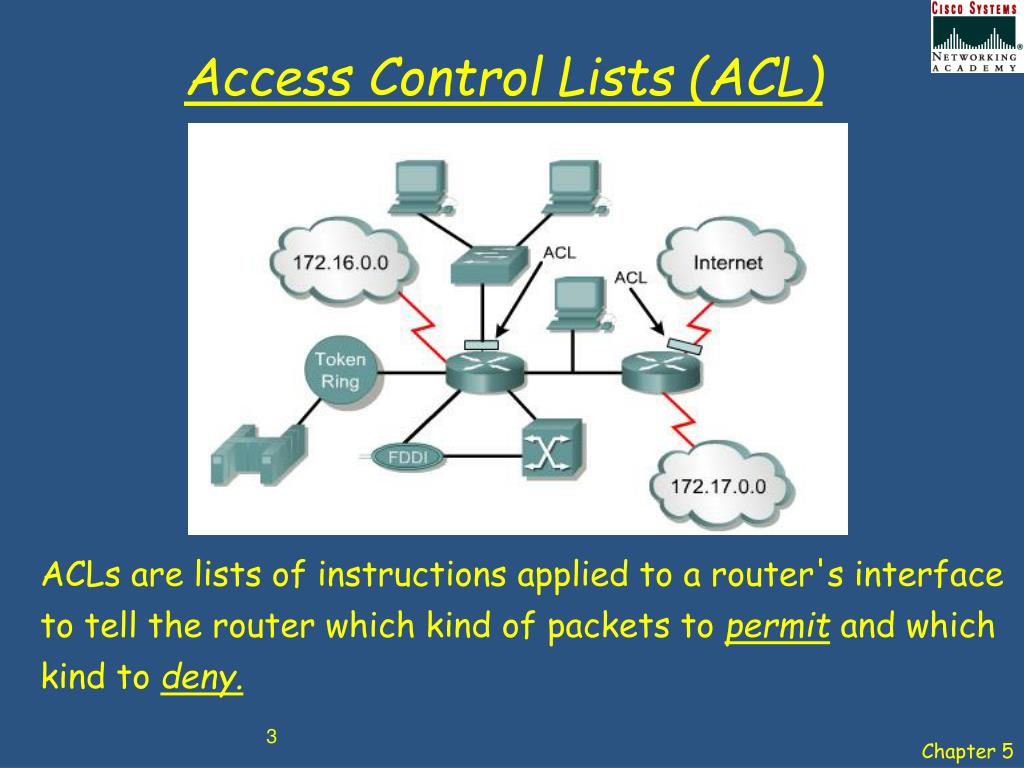
Data Access Control Lists . an access control list (acl) is a fundamental component of computer security. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. Resources in this case may be files, networks, or devices. one of the major mechanisms you use to do that is an access control list (acl). In this article, i will explain. In this article, we'll talk about what access control lists really are, and how you can use them. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. An acl is a set of rules for allowing or denying access to certain resources. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. Acls help to control and manage access permissions to organizational resources. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital.
from www.slideserve.com
An acl is a set of rules for allowing or denying access to certain resources. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. In this article, we'll talk about what access control lists really are, and how you can use them. Resources in this case may be files, networks, or devices. Acls help to control and manage access permissions to organizational resources. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. In this article, i will explain. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets.
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint
Data Access Control Lists the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. one of the major mechanisms you use to do that is an access control list (acl). an access control list (acl) is a fundamental component of computer security. Resources in this case may be files, networks, or devices. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. In this article, we'll talk about what access control lists really are, and how you can use them. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. Acls help to control and manage access permissions to organizational resources. In this article, i will explain. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. An acl is a set of rules for allowing or denying access to certain resources. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a.
From docs.fastly.com
Working with ACLs using the web interface Access control lists Data Access Control Lists an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. one of the major mechanisms you use to do that is an access control list (acl). the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within. Data Access Control Lists.
From www.youtube.com
access control lists cisco ccna 200 125 100 105 16 Building a Extended Data Access Control Lists an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. an access control list (acl) is a fundamental component of computer security. An acl is a set of rules for allowing or denying access to certain resources. In this article, we'll talk about what access. Data Access Control Lists.
From studylib.net
Extended Access Control Lists Data Access Control Lists an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. Acls help to control and manage access permissions to organizational resources. In this article, we'll talk about what access control lists really are, and how you can use them. an access control list (acl) is. Data Access Control Lists.
From www.slideserve.com
PPT ACL(Access Control Lists) PowerPoint Presentation, free download Data Access Control Lists An acl is a set of rules for allowing or denying access to certain resources. one of the major mechanisms you use to do that is an access control list (acl). In this article, i will explain. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. Resources in this. Data Access Control Lists.
From www.freecodecamp.org
What is An ACL? Access Control Lists Explained Data Access Control Lists the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. In this article, we'll talk about what access control lists really are, and how you can use them. An access control. Data Access Control Lists.
From www.slideserve.com
PPT Chapter IX File Systems PowerPoint Presentation, free download Data Access Control Lists an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. one of the major mechanisms you use to do that is an access control list (acl). an access control list (acl) is a fundamental component of computer security. An acl. Data Access Control Lists.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Data Access Control Lists an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. An acl is a set of rules for allowing or denying access to certain resources. In this article, i will explain. the access control list (acl) contains access control entries (ace), telling a system how. Data Access Control Lists.
From benisnous.com
What is Access control lists (ACLs)? Data Access Control Lists an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. In this article, i will explain. In this article, we'll talk about. Data Access Control Lists.
From supertechman.com.au
What is an Access Control List (ACL) and How to Configure Them! Data Access Control Lists Resources in this case may be files, networks, or devices. an access control list (acl) is a fundamental component of computer security. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. An acl is a set of rules for allowing or denying access to certain resources. Acls help to. Data Access Control Lists.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Data Access Control Lists an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. Acls help to control and manage access permissions to organizational resources. . Data Access Control Lists.
From www.slideshare.net
Access Control Principles and Practice Data Access Control Lists Acls help to control and manage access permissions to organizational resources. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. an access control list (acl) is a fundamental component of computer security. An access control list, abbreviated as acl, is. Data Access Control Lists.
From people.cs.rutgers.edu
Access Control Data Access Control Lists In this article, we'll talk about what access control lists really are, and how you can use them. an access control list (acl) is a fundamental component of computer security. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. . Data Access Control Lists.
From heimdalsecurity.com
What Is an Access Control List (ACL)? Definition, Types and Benefits Data Access Control Lists the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. an access control list (acl) is a fundamental component of computer security. An acl is a set of rules for allowing or denying access to certain resources. an access control list (acl) is a list of rules that. Data Access Control Lists.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Data Access Control Lists one of the major mechanisms you use to do that is an access control list (acl). Resources in this case may be files, networks, or devices. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. an access control. Data Access Control Lists.
From www.scribd.com
Access Control Lists Router Computer Network Data Access Control Lists Acls help to control and manage access permissions to organizational resources. An acl is a set of rules for allowing or denying access to certain resources. In this article, we'll talk about what access control lists really are, and how you can use them. an access control list (acl) is a list of rules that specifies which users or. Data Access Control Lists.
From cyral.com
What is Data Access Control? Definition and Related FAQs Cyral Data Access Control Lists Resources in this case may be files, networks, or devices. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. an access control list (acl) is a fundamental component of computer security. an access control list (acl) is a set of rules that determine whether a user or. Data Access Control Lists.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Data Access Control Lists an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. Acls help to control and manage access permissions to organizational resources. the. Data Access Control Lists.
From help.sap.com
SAP Help Portal Data Access Control Lists An acl is a set of rules for allowing or denying access to certain resources. one of the major mechanisms you use to do that is an access control list (acl). an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital.. Data Access Control Lists.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Data Access Control Lists The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. Acls help to control and manage access permissions to organizational resources. Resources in this case may be files, networks, or devices.. Data Access Control Lists.
From www.youtube.com
What Are Access Lists? Access Control Lists (ACLs) Part 1 of 8 Data Access Control Lists In this article, we'll talk about what access control lists really are, and how you can use them. one of the major mechanisms you use to do that is an access control list (acl). the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. The rules describe the packet. Data Access Control Lists.
From website-redesign-project-enterprise--budibase.netlify.app
RoleBased Access Control Ultimate Guide Data Access Control Lists In this article, i will explain. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. one of the major mechanisms you use to do that. Data Access Control Lists.
From studylib.net
Access Control Lists Lecture 1 Data Access Control Lists An acl is a set of rules for allowing or denying access to certain resources. Resources in this case may be files, networks, or devices. In this article, we'll talk about what access control lists really are, and how you can use them. an access control list (acl) is a fundamental component of computer security. one of the. Data Access Control Lists.
From www.wallarm.com
What is ACL? Examples and Types of Access Control List Data Access Control Lists In this article, i will explain. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. an access control list (acl) is a fundamental component of computer security. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access. Data Access Control Lists.
From www.strongdm.com
What is Access Control Lists (ACL)? Definition StrongDM Data Access Control Lists an access control list (acl) is a fundamental component of computer security. In this article, i will explain. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. Resources in this case may be files, networks, or devices. the. Data Access Control Lists.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Data Access Control Lists Resources in this case may be files, networks, or devices. one of the major mechanisms you use to do that is an access control list (acl). In this article, we'll talk about what access control lists really are, and how you can use them. An acl is a set of rules for allowing or denying access to certain resources.. Data Access Control Lists.
From infocenter.sybase.com
Data Federation Permissions and Access Control Lists Data Access Control Lists An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. Acls help to control and manage access permissions to organizational resources. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. . Data Access Control Lists.
From www.ccnaacademy.com
Access Control Lists (ACLs) What They Are and How to Configure Them Data Access Control Lists an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. one of the major mechanisms you use. Data Access Control Lists.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Data Access Control Lists In this article, we'll talk about what access control lists really are, and how you can use them. one of the major mechanisms you use to do that is an access control list (acl). Acls help to control and manage access permissions to organizational resources. The rules describe the packet matching conditions, such as the source address, destination address,. Data Access Control Lists.
From www.slideserve.com
PPT Computer Security Network + Link Layer Security + Network Data Access Control Lists Acls help to control and manage access permissions to organizational resources. an access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. Resources in this case may. Data Access Control Lists.
From www.serverlesssql.com
Using Access Control Lists To Manage FineGrain Data Lake Permissions Data Access Control Lists an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. Acls help to control and manage access permissions to organizational resources. Resources in this case may be files, networks, or devices. The rules describe the packet matching conditions, such as the source. Data Access Control Lists.
From www.youtube.com
Types of access control lists explained Standard, Extended, Numbered Data Access Control Lists An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. In this article, we'll talk about what access control lists really are,. Data Access Control Lists.
From www.alamy.com
Data access control infographic chart design template. Abstract Data Access Control Lists In this article, i will explain. one of the major mechanisms you use to do that is an access control list (acl). The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets. an access control list (acl) is a list of rules that specifies which users or systems are. Data Access Control Lists.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Data Access Control Lists An acl is a set of rules for allowing or denying access to certain resources. one of the major mechanisms you use to do that is an access control list (acl). In this article, i will explain. Resources in this case may be files, networks, or devices. the access control list (acl) contains access control entries (ace), telling. Data Access Control Lists.
From pediaa.com
What is the Difference Between Access Control List and Access Control Data Access Control Lists one of the major mechanisms you use to do that is an access control list (acl). an access control list (acl) is a fundamental component of computer security. An access control list, abbreviated as acl, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. . Data Access Control Lists.
From identitymanagementinstitute.org
Access Control Matrix and Capability List Identity Management Institute® Data Access Control Lists the access control list (acl) contains access control entries (ace), telling a system how to filter traffic within a. an access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital. an access control list (acl) is a list of rules that. Data Access Control Lists.