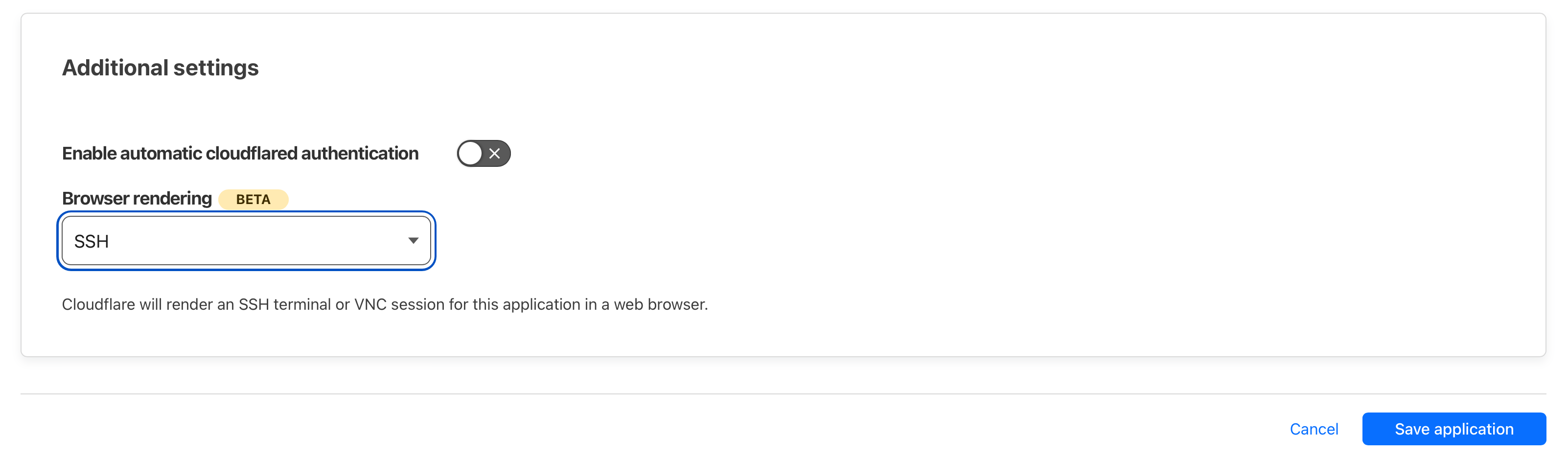
Tunnel X Through Ssh . For example to access target one can: Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. First, connect to machine b and forward [localport] to c:22 through b. You can use a ssh connection to get a remote port mapped in a local port. Next, connect to c from a through this newly. Map the port 22 on target to a. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Simply type the following command: Ssh is frequently used to tunnel insecure traffic over the internet in a secure way.
from cola16.app
Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. For example to access target one can: Next, connect to c from a through this newly. You can use a ssh connection to get a remote port mapped in a local port. Simply type the following command: This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. Map the port 22 on target to a. First, connect to machine b and forward [localport] to c:22 through b.
Tunnel로 연결된 서버에 웹 브라우저로 ssh, vnc를 연결해보자. cola16k
Tunnel X Through Ssh This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Map the port 22 on target to a. You can use a ssh connection to get a remote port mapped in a local port. For example to access target one can: Next, connect to c from a through this newly. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. First, connect to machine b and forward [localport] to c:22 through b. Simply type the following command:
From responsedop.weebly.com
Unix ssh tunnel responsedop Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. Next, connect to c from a through this newly. For example to access target one can: Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Simply type the following command: Map. Tunnel X Through Ssh.
From www.isabekov.pro
Reverse SSH Tunnel Explained Altynbek Isabekov Tunnel X Through Ssh Simply type the following command: First, connect to machine b and forward [localport] to c:22 through b. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a. Tunnel X Through Ssh.
From ryan.himmelwright.net
Simple Reverse SSH Tunnels λ ryan. himmelwright. net Tunnel X Through Ssh Next, connect to c from a through this newly. First, connect to machine b and forward [localport] to c:22 through b. For example to access target one can: This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. You can use a ssh connection to get a remote. Tunnel X Through Ssh.
From www.mybluelinux.com
A Visual Guide to SSH Tunnels Local and Remote Port Forwarding Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. First, connect to machine b and forward [localport] to c:22 through b. For example to access target one can: This page explains how to run an x window graphical application over an ssh session. Tunnel X Through Ssh.
From awesomeopensource.com
Ssh Tunnel Port Forwarding Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. You can use a ssh connection to get a remote port mapped in a local port. Simply type the following command: First, connect to machine b and forward [localport] to c:22 through b. Ssh. Tunnel X Through Ssh.
From codsplaice.blogspot.com
Cods Plaice Putting VNC traffic through an SSH tunnel Tunnel X Through Ssh Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. For example to access target one can: This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. You can use a ssh connection to get a remote port mapped in a local port.. Tunnel X Through Ssh.
From learn.ictadmins.com
راه اندازی SSH Tunnel در میکروتیک مجید برکاتی 1402 Tunnel X Through Ssh Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one. Tunnel X Through Ssh.
From statidentity.weebly.com
statidentity Blog Tunnel X Through Ssh For example to access target one can: Next, connect to c from a through this newly. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a secure. Tunnel X Through Ssh.
From tonyteaches.tech
How to Reverse SSH Tunnel Tony Teaches Tech Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. Map the port 22 on target to a. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. For example to access target one can: Forwarding an x session over ssh brings a remote gui application. Tunnel X Through Ssh.
From www.bram.us
A visual guide to SSH tunnels Bram.us Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Next, connect to c from a through this newly. Simply type the following command: For example to access target one can: Ssh. Tunnel X Through Ssh.
From www.youtube.com
How to Make an SSH Proxy Tunnel YouTube Tunnel X Through Ssh This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. You can use a ssh connection to get a remote port mapped in a local port. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in. Tunnel X Through Ssh.
From cola16.app
Tunnel로 연결된 서버에 웹 브라우저로 ssh, vnc를 연결해보자. cola16k Tunnel X Through Ssh Next, connect to c from a through this newly. You can use a ssh connection to get a remote port mapped in a local port. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. Map the port 22 on target to a. This page explains how to run an x window graphical application over. Tunnel X Through Ssh.
From thecurioustechnoid.com
SSH Tunneling (Port Forwarding) a use case The Curious Technoid Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. First, connect to machine b and forward [localport] to c:22 through b. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. You can use a ssh connection to. Tunnel X Through Ssh.
From networktutorialss.blogspot.com
SSH Tunneling or SSH Port forwarding Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. You can use a ssh connection to get a remote port mapped in a local port. Simply type the. Tunnel X Through Ssh.
From www.thyssenkrupp.com
Underground giants our six most impressive tunnel systems Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. Next, connect to c from a through this newly. You can use a ssh connection to get a remote port mapped in a local port. Map the port 22 on target to a.. Tunnel X Through Ssh.
From linuxlearn.org
نحوه ایجاد SSH Tunnel یا Port Forward در لینوکس آموزش لینوکس 🐧 آموزش Tunnel X Through Ssh Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. First, connect to machine b and forward [localport] to c:22 through b. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and. Tunnel X Through Ssh.
From www.starkandwayne.com
Jumping through tunnels (A guide to SSHProxyJump) Stark & Wayne Tunnel X Through Ssh Map the port 22 on target to a. First, connect to machine b and forward [localport] to c:22 through b. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Simply type the following command: You can use a ssh connection to get a remote port mapped in. Tunnel X Through Ssh.
From koochieplay.com
Tunnel X Playground Equipment Manufacturers Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Simply type the following command: Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a. Tunnel X Through Ssh.
From esc.sh
Using SSH tunnel to reach a database server via JumpHost Tunnel X Through Ssh This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. You can use a ssh connection to get a remote port mapped in a local port. First, connect to machine b and forward [localport] to c:22 through b. Next, connect to c from a through this newly. For. Tunnel X Through Ssh.
From www.crushftp.com
Crush10wiki SSH Tunnel Tunnel X Through Ssh You can use a ssh connection to get a remote port mapped in a local port. Map the port 22 on target to a. Next, connect to c from a through this newly. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. For example to access target one can: First, connect to machine b. Tunnel X Through Ssh.
From wiki.networksecuritytoolkit.org
Tunnelling UDP Traffic Through An SSH Connection MediaWiki Tunnel X Through Ssh Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. For example to access target one can: Next, connect to c from a through this newly. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Forwarding an x session over ssh brings. Tunnel X Through Ssh.
From www.enterprisedb.com
SSH Tunneling in pgAdmin 4 Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. For example to access target one can: First, connect to machine b and forward [localport] to c:22 through b. This page explains how to run an x window graphical application over an ssh session. Tunnel X Through Ssh.
From www.vrogue.co
Ssh Local And Remote Port Forwarding Ssh Tunneling vrogue.co Tunnel X Through Ssh Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. First, connect to machine b and forward [localport] to c:22 through. Tunnel X Through Ssh.
From tudip.com
Blog What is SSH tunneling and reverse port forwarding? Tudip Tunnel X Through Ssh For example to access target one can: Next, connect to c from a through this newly. Map the port 22 on target to a. First, connect to machine b and forward [localport] to c:22 through b. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. This page explains how to run an x window. Tunnel X Through Ssh.
From b.hatena.ne.jp
[B! ssh] A Visual Guide to SSH Tunnels (with labs) Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. For example to access target one can: Next, connect to c from a through this newly. Simply type the following command: Map the port 22 on target to a. Ssh is frequently used to. Tunnel X Through Ssh.
From www.isabekov.pro
Reverse SSH Tunnel Explained Altynbek Isabekov Tunnel X Through Ssh Map the port 22 on target to a. You can use a ssh connection to get a remote port mapped in a local port. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. First, connect to machine b and forward [localport] to c:22 through b. For example to access target one can: This page. Tunnel X Through Ssh.
From cola16.app
Tunnel로 연결된 서버에 웹 브라우저로 ssh, vnc를 연결해보자. cola16k Tunnel X Through Ssh Map the port 22 on target to a. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. For example to access target one can: Next, connect to c from a through this newly. First, connect to machine b and forward [localport] to c:22. Tunnel X Through Ssh.
From tonyteaches.tech
How to Reverse SSH Tunnel Tony Teaches Tech Tunnel X Through Ssh Next, connect to c from a through this newly. You can use a ssh connection to get a remote port mapped in a local port. This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Forwarding an x session over ssh brings a remote gui application to your. Tunnel X Through Ssh.
From www.computersecuritystudent.com
How Set Up a Reverse SSH Tunnel Reverse SSH Tunnel, ssh R, ssh p Tunnel X Through Ssh You can use a ssh connection to get a remote port mapped in a local port. Simply type the following command: This page explains how to run an x window graphical application over an ssh session using the x11 forwarding in ssh feature. Map the port 22 on target to a. First, connect to machine b and forward [localport] to. Tunnel X Through Ssh.
From zaminhost.com
آموزش ساخت SSH Tunnel و راه اندازی Port Forwarding در لینوکس Tunnel X Through Ssh You can use a ssh connection to get a remote port mapped in a local port. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Simply type the following command: This page explains how to run an x window graphical application over an. Tunnel X Through Ssh.
From www.frank-rahn.de
Ein VPN mit einem SSH Tunnel aufbauen » Frank W. Rahn Tunnel X Through Ssh Simply type the following command: For example to access target one can: Map the port 22 on target to a. You can use a ssh connection to get a remote port mapped in a local port. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place,. Tunnel X Through Ssh.
From blog.famzah.net
Proxy SSH traffic using Cloudflare Tunnels /contrib/famzah Tunnel X Through Ssh Map the port 22 on target to a. For example to access target one can: You can use a ssh connection to get a remote port mapped in a local port. Next, connect to c from a through this newly. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. First, connect to machine b. Tunnel X Through Ssh.
From plu.one
sshtunnel原理及其使用 先飞的博客 Tunnel X Through Ssh First, connect to machine b and forward [localport] to c:22 through b. Map the port 22 on target to a. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. For example to access target one can: Simply type the following command: Next, connect to c from a through this newly. You can use a. Tunnel X Through Ssh.
From www.youtube.com
Tunnels SSH (première partie) YouTube Tunnel X Through Ssh Map the port 22 on target to a. Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way. You can use a ssh connection to get a remote port. Tunnel X Through Ssh.
From www.bogotobogo.com
Linux Secure Shell (SSH) V Reverse SSH Tunnel (remote port forwarding Tunnel X Through Ssh Forwarding an x session over ssh brings a remote gui application to your desktop, so now all of your apps are in one place, and not. For example to access target one can: Next, connect to c from a through this newly. Simply type the following command: First, connect to machine b and forward [localport] to c:22 through b. Ssh. Tunnel X Through Ssh.