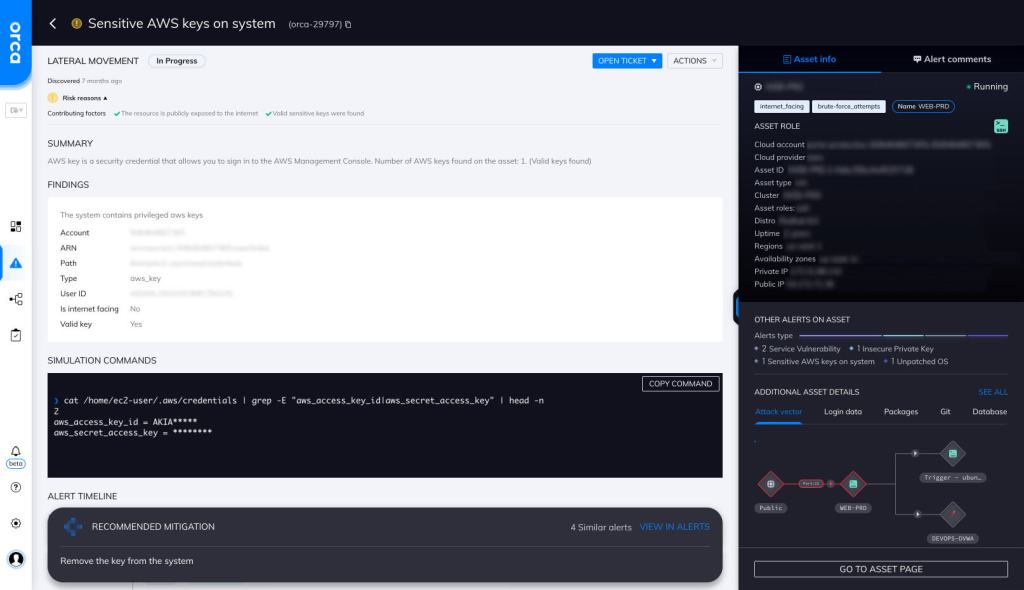
Aws Access Key Security . the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. Together, they authenticate requests to aws apis, allowing users. an aws access key consists of an access key id and a secret access key; an access key id and secret access key are required to sign requests that you make using the aws command. You can use access keys to sign. this applies to both root secret access keys and aws identity and access management (iam) user secret.
from orca.security
changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. Together, they authenticate requests to aws apis, allowing users. an aws access key consists of an access key id and a secret access key; this applies to both root secret access keys and aws identity and access management (iam) user secret. an access key id and secret access key are required to sign requests that you make using the aws command. You can use access keys to sign.
AWS Access Keys Cloud Risk Encyclopedia Orca Security
Aws Access Key Security the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an aws access key consists of an access key id and a secret access key; this applies to both root secret access keys and aws identity and access management (iam) user secret. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access key are required to sign requests that you make using the aws command. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. You can use access keys to sign. Together, they authenticate requests to aws apis, allowing users.
From www.youtube.com
How to get AWS access key and secret key AWS Tutorials 2022 Amazon Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. You can use access keys to sign. an aws access key consists of an access key id and a secret access key; changing access keys (which consist of an access key id and a secret access key). Aws Access Key Security.
From www.msp360.com
How to Get AWS Access Key ID and Secret Access Key Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. this applies to both root secret access keys and aws. Aws Access Key Security.
From support.freeappanalytics.com
AWS Access Key and Secret Access Key Creation and Management Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. an aws access key consists of an access key id and a secret access key; an access key id and secret access key are required to sign requests that you make using the aws command. the access key id. Aws Access Key Security.
From www.cloudysave.com
AWS S3 Set Access Key CloudySave Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. Together, they authenticate requests to aws apis, allowing users. You can use access keys to sign. an aws access key consists of an access key id and a secret access key; this applies to both root secret. Aws Access Key Security.
From www.youtube.com
How to get AWS access key and secret key id for s3 YouTube Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. an access key id and secret access key are required to sign requests that you make using the aws command. Together, they authenticate requests to aws apis, allowing users. the access key id and secret access key values are the. Aws Access Key Security.
From aws.plainenglish.io
A Guide on Installing AWS CLI on Windows and Configuring Access Keys Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. an access key id and secret access key are required to sign requests that you make using the aws command. You can use access keys to sign. an aws access key consists of an access key. Aws Access Key Security.
From s3browser.com
Access Key Id and Secret Access Key. How to retrieve your AWS Access Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. an aws access key consists of an access key id and a secret access key; Together, they authenticate requests. Aws Access Key Security.
From laptrinhx.com
How to create an Amazon S3 Bucket and AWS Access Key ID and Secret Aws Access Key Security an aws access key consists of an access key id and a secret access key; an access key id and secret access key are required to sign requests that you make using the aws command. this applies to both root secret access keys and aws identity and access management (iam) user secret. Together, they authenticate requests to. Aws Access Key Security.
From www.cloudockit.com
Cloudockit AWS Authentication Using Access Keys Aws Access Key Security an aws access key consists of an access key id and a secret access key; the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. this applies to both root secret access keys and aws identity and access management (iam) user. Aws Access Key Security.
From speakerdeck.com
An attacker’s guide to AWS Access Keys Speaker Deck Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. this applies to both root secret access keys and aws identity and access management (iam) user secret. an aws access key consists of an access key id and a secret access key; an access key. Aws Access Key Security.
From www.startdataengineering.com
Aws Account · Start Data Engineering Aws Access Key Security an aws access key consists of an access key id and a secret access key; an access key id and secret access key are required to sign requests that you make using the aws command. You can use access keys to sign. changing access keys (which consist of an access key id and a secret access key). Aws Access Key Security.
From www.scaler.com
AWS Access Key Scaler Topics Aws Access Key Security You can use access keys to sign. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access key are required to sign requests that you make using the aws command. this applies to both. Aws Access Key Security.
From speakerdeck.com
An attacker’s guide to AWS Access Keys Speaker Deck Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. Together, they authenticate requests to aws apis, allowing users. this applies to both root secret access keys and aws identity and access management (iam) user secret. an aws access key consists of an access key id. Aws Access Key Security.
From www.youtube.com
How to Create AWS Access Key ID and Secret Access Key AWS Access Keys Aws Access Key Security You can use access keys to sign. an access key id and secret access key are required to sign requests that you make using the aws command. an aws access key consists of an access key id and a secret access key; changing access keys (which consist of an access key id and a secret access key). Aws Access Key Security.
From mail.codejava.net
How to Generate AWS Access Key ID and Secret Access Key Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. Together, they authenticate requests to aws apis, allowing users. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are. Aws Access Key Security.
From nerdyelectronics.com
Create AWS Access key ID and secret access key NerdyElectronics Aws Access Key Security an aws access key consists of an access key id and a secret access key; Together, they authenticate requests to aws apis, allowing users. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. You can use access keys to sign. . Aws Access Key Security.
From www.youtube.com
How to get AWS access key and secret key id YouTube Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. this applies to both root secret access keys and aws identity and access management (iam) user secret. You can use access keys to sign. the access key id and secret access key values are the security credentials. Aws Access Key Security.
From tntdrive.com
AWS Access Keys Access Key Id and Secret Access Key. Where to obtain Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. an access key id and secret access key are required to sign requests that you make using the aws command. the access key id and secret access key values are the security credentials aws uses to. Aws Access Key Security.
From velog.io
AWS account security 관리 IAM Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. this applies to both root secret access keys and aws identity and access management (iam) user secret. an aws access key consists of an access key id and a secret access key; the access key. Aws Access Key Security.
From tntdrive.com
AWS Access Keys Access Key Id and Secret Access Key. Where to obtain Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. an aws access key consists of an access key id and a secret access key; You can use access keys to sign. the access key id and secret access key values are the security credentials aws uses. Aws Access Key Security.
From speakerdeck.com
An attacker’s guide to AWS Access Keys Speaker Deck Aws Access Key Security an aws access key consists of an access key id and a secret access key; Together, they authenticate requests to aws apis, allowing users. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access. Aws Access Key Security.
From www.cloudockit.com
Cloudockit AWS Authentication Using Access Keys Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are the security credentials aws uses to. Aws Access Key Security.
From orca.security
AWS Access Keys Cloud Risk Encyclopedia Orca Security Aws Access Key Security an aws access key consists of an access key id and a secret access key; the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. this applies to both root secret access keys and aws identity and access management (iam) user. Aws Access Key Security.
From jayendrapatil.com
AWS S3 Encryption Aws Access Key Security an aws access key consists of an access key id and a secret access key; changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant. Aws Access Key Security.
From www.xmodulo.com
How to create a new Amazon AWS access key Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. You can use access keys to sign. changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. Together, they authenticate requests to aws apis, allowing users. the access key. Aws Access Key Security.
From www.msp360.com
How to Get AWS Access Key ID and Secret Access Key Aws Access Key Security Together, they authenticate requests to aws apis, allowing users. this applies to both root secret access keys and aws identity and access management (iam) user secret. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and. Aws Access Key Security.
From k21academy.com
How To Create Access Keys And Secret Keys In AWS Aws Access Key Security the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access key are required to sign requests that you make using the aws command. Together, they authenticate requests to aws apis, allowing users. changing access. Aws Access Key Security.
From www.youtube.com
Authenticating to AWS Services using Access Keys YouTube Aws Access Key Security You can use access keys to sign. an aws access key consists of an access key id and a secret access key; changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. this applies to both root secret access keys and aws identity and access management. Aws Access Key Security.
From myrestraining.com
How To Create Aws Access Key Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. Together, they authenticate requests to aws apis, allowing users. an access key id and secret access key are required to sign requests that you make using the aws command. the access key id and secret access key values are the. Aws Access Key Security.
From nerdyelectronics.com
Create AWS Access key ID and secret access key NerdyElectronics Aws Access Key Security Together, they authenticate requests to aws apis, allowing users. an access key id and secret access key are required to sign requests that you make using the aws command. this applies to both root secret access keys and aws identity and access management (iam) user secret. an aws access key consists of an access key id and. Aws Access Key Security.
From www.decodingdevops.com
How To Create AWS Access Key and Secret Key DecodingDevops Aws Access Key Security an aws access key consists of an access key id and a secret access key; You can use access keys to sign. this applies to both root secret access keys and aws identity and access management (iam) user secret. the access key id and secret access key values are the security credentials aws uses to verify your. Aws Access Key Security.
From support.kochava.com
AWS Access and Secret Keys Aws Access Key Security Together, they authenticate requests to aws apis, allowing users. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access key are required to sign requests that you make using the aws command. this applies. Aws Access Key Security.
From www.decodingdevops.com
How To Create AWS Access Key and Secret Key DecodingDevops Aws Access Key Security this applies to both root secret access keys and aws identity and access management (iam) user secret. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. an access key id and secret access key are required to sign requests that. Aws Access Key Security.
From speakerdeck.com
An attacker’s guide to AWS Access Keys Speaker Deck Aws Access Key Security an access key id and secret access key are required to sign requests that you make using the aws command. Together, they authenticate requests to aws apis, allowing users. this applies to both root secret access keys and aws identity and access management (iam) user secret. the access key id and secret access key values are the. Aws Access Key Security.
From speakerdeck.com
An attacker’s guide to AWS Access Keys Speaker Deck Aws Access Key Security changing access keys (which consist of an access key id and a secret access key) on a regular schedule is a. the access key id and secret access key values are the security credentials aws uses to verify your identity and grant or deny you access to. You can use access keys to sign. an aws access. Aws Access Key Security.