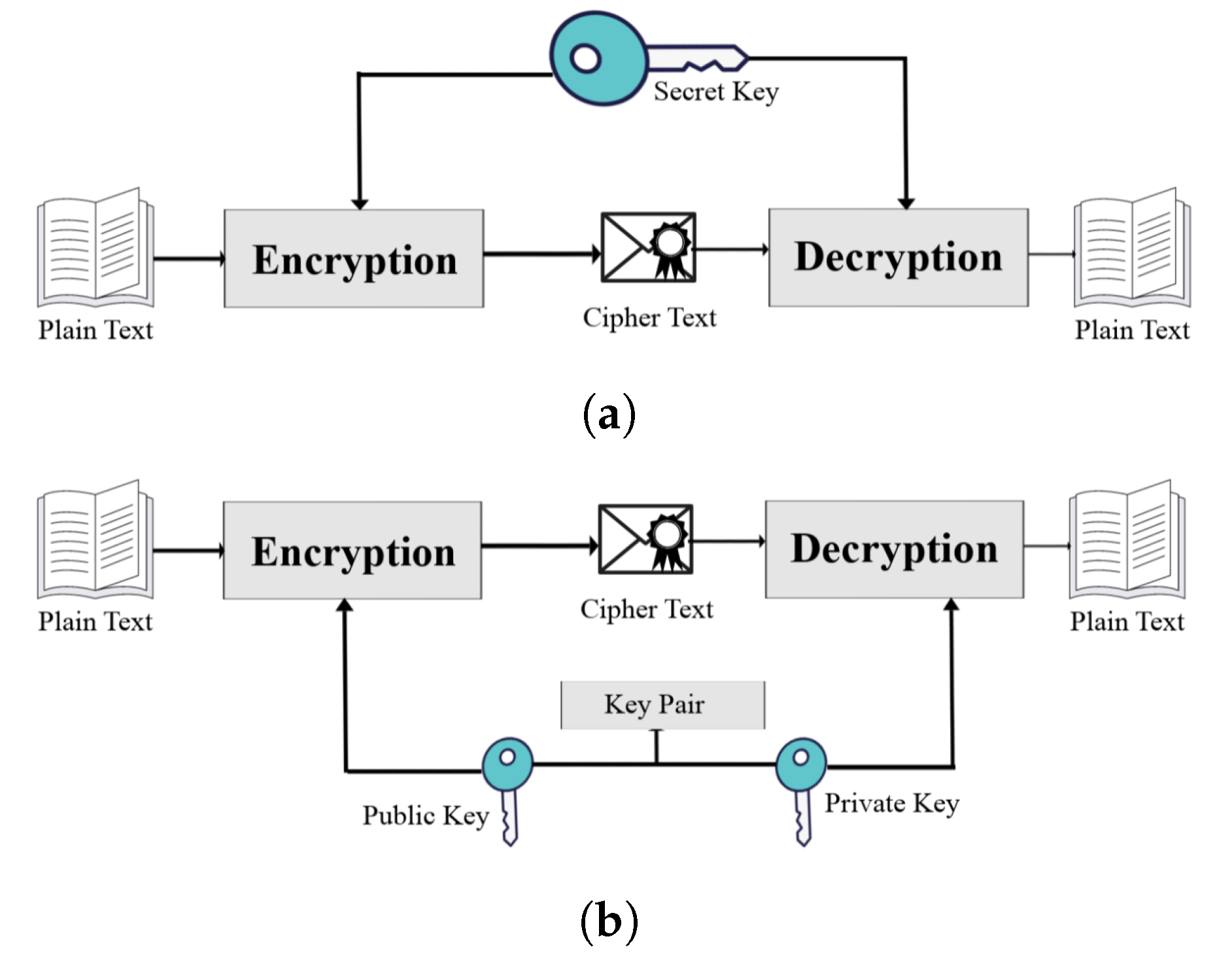
Ratcheting Cryptography . at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet.
from www.mdpi.com
the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric.
Sensors Free FullText Resilience Optimization of PostQuantum
Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric.
From www.researchgate.net
Schematic representation of ratcheting damage. Download Scientific Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using. Ratcheting Cryptography.
From askleo.com
What Is Public Key Cryptography? Ask Leo! Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From www.analyticsvidhya.com
Cloud Cryptography A Reliable Solution to Secure your Cloud Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From crypto.stackexchange.com
encryption Plaintext DH keys in the message header in the Double Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. a ratchet is simply a device that only moves forward, one step at a time, much like fastening. Ratcheting Cryptography.
From www.paubox.com
The role of cryptographic algorithms in encryption and decryption Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From www.desertcart.in
Buy Cryptography The Key to Digital Security, How It Works, and Why It Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From link.springer.com
Special Issue on Contemporary interactions between codes, cryptographic Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. a ratchet is simply a device that only moves forward, one step at a time, much like fastening. Ratcheting Cryptography.
From github.com
GitHub An implementation of the Double Ratchet Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like. Ratcheting Cryptography.
From www.youtube.com
[Cryptography Meetup] The doubleratchet algorithm its security and Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From www.theqrl.org
History of Cryptography, behind the code Episode 3 Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From www.ituonline.com
Security CompTIA + Cryptography And PKI (7 Of 7 Part Series) ITU Online Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show. Ratcheting Cryptography.
From www.cryptopolitan.com
How to Apply Cryptography Hashing Principles and Algorithms to Your Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using. Ratcheting Cryptography.
From hextechsecurity.com
Quantum Cryptography Revolutionizing Global Security with Unbreakable Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From www.packetlabs.net
Cryptography Attacks 6 Types & Prevention Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness, we are. Ratcheting Cryptography.
From www.youtube.com
Double Ratchet Messaging Encryption Computerphile YouTube Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From www.ccn.com
Cryptography Attacks 6 Types And Prevention Measures Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. a ratchet is simply a device that only moves forward, one step at a time, much like fastening. Ratcheting Cryptography.
From www.techradar.com
What is cryptography? TechRadar Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are. Ratcheting Cryptography.
From lifecodelanka.blogspot.com
Cryptography Part 01 Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much. Ratcheting Cryptography.
From www.baeldung.com
Cryptography What Is a Trapdoor? Baeldung on Computer Science Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using. Ratcheting Cryptography.
From ducarainfo.com
Demystifying Cryptography Understanding PGP, SSL, and IKE Ducara Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From brodiegould.com
BG Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From www.codingninjas.com
What are basic Cryptography tools? Coding Ninjas Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message. Ratcheting Cryptography.
From www.mdpi.com
Sensors Free FullText Resilience Optimization of PostQuantum Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From www.scribd.com
Double Ratchet PDF Key (Cryptography) Cryptography Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From eureka.patsnap.com
Cryptographic apparatus and method Eureka Patsnap develop Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every. Ratcheting Cryptography.
From www.pinterest.com
Specifications >> The Double Ratchet Algorithm Encrypted messages Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are. Ratcheting Cryptography.
From www.trendmicro.com
Diving Deep Into Quantum Computing Modern Cryptography Trend Micro (US) Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show. Ratcheting Cryptography.
From demonstrations.wolfram.com
Kids' Cryptography with a Key from a Propositional Puzzle Wolfram Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every. Ratcheting Cryptography.
From crypto.stackexchange.com
diffie hellman How often do Double ratchet in Signal protocol update Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. a ratchet is simply a device that only moves forward, one step at a time, much like fastening. Ratcheting Cryptography.
From www.zeeve.io
An Exploration of Symmetric Key Cryptography History, Working, and Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much. Ratcheting Cryptography.
From trabic.com
Super Secret Cryptography 7 Ways It Safeguards Cryptocurrencies Trabic Ratcheting Cryptography the double ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using. Ratcheting Cryptography.
From blog.basistheory.com
Encryption vs. Tokenization Similarities and Differences Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. the double ratchet algorithm is used by two parties to exchange. Ratcheting Cryptography.
From atomicdex.io
Symmetric Key Cryptography — What Is It and How Does It Work? Ratcheting Cryptography at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness,. Ratcheting Cryptography.
From publish.obsidian.md
Endtoend Encryption mnml's vault Obsidian Publish Ratcheting Cryptography due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. at its core it uses the concept of \double ratcheting, where every message is encrypted and authenticated using a fresh symmetric. a ratchet is simply a device that only moves forward, one step at a time, much. Ratcheting Cryptography.
From www.codingninjas.com
What are basic Cryptography tools? Coding Ninjas Ratcheting Cryptography a ratchet is simply a device that only moves forward, one step at a time, much like fastening a tie rib (which is a ratchet. due to slight (but meaningful) changes to regard attacks against randomness, we are ultimately able to show that, in order. the double ratchet algorithm is used by two parties to exchange encrypted. Ratcheting Cryptography.