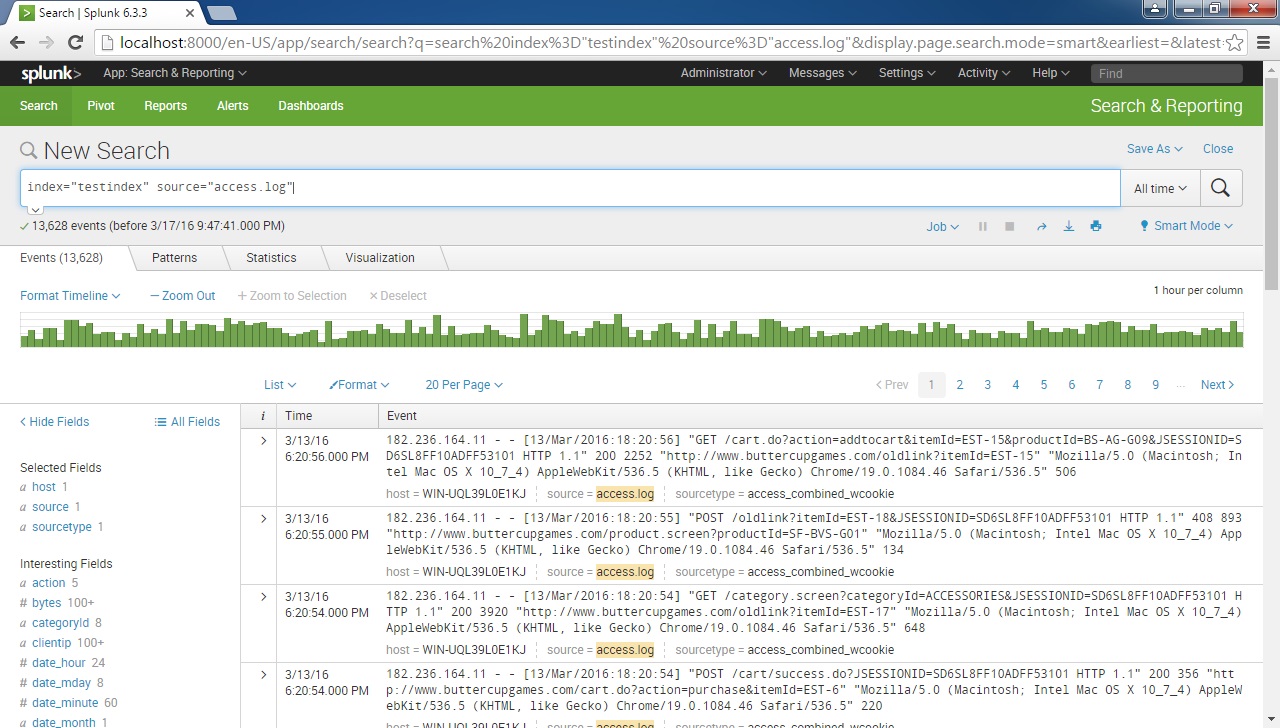
Splunk Eventcount Example . Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. This is the current search logic that i am using. | eventcount summarize=false index=* report_size=true. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. The objective of this search is to count the number of events in a search result. I have the following search: | rename content.orderid as order id. Calculate the average duration grouped by a specific field. Returns the number of events in the specified indexes. This example is the same as the previous example except that an. I would like to return the number of events in which new state = state one.
from geek-university.com
I have the following search: This is the current search logic that i am using. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. I would like to return the number of events in which new state = state one. | eventcount summarize=false index=* report_size=true. This example is the same as the previous example except that an. Returns the number of events in the specified indexes. Calculate the average duration grouped by a specific field. The objective of this search is to count the number of events in a search result.
top command Splunk
Splunk Eventcount Example Returns the number of events in the specified indexes. Calculate the average duration grouped by a specific field. This is the current search logic that i am using. Returns the number of events in the specified indexes. I have the following search: This example is the same as the previous example except that an. I would like to return the number of events in which new state = state one. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. The objective of this search is to count the number of events in a search result. | eventcount summarize=false index=* report_size=true. | rename content.orderid as order id. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats.
From examples.javacodegeeks.com
Splunk Stats Command Example Java Code Geeks Splunk Eventcount Example | rename content.orderid as order id. Returns the number of events in the specified indexes. The objective of this search is to count the number of events in a search result. This example is the same as the previous example except that an. I have the following search: I would like to return the number of events in which new. Splunk Eventcount Example.
From examples.javacodegeeks.com
Splunk Stats Command Example Java Code Geeks Splunk Eventcount Example Returns the number of events in the specified indexes. This example is the same as the previous example except that an. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. Calculate the average duration grouped by a specific field. The objective of this search is to count the number. Splunk Eventcount Example.
From avleonov.com
How to correlate different events in Splunk and make dashboards Splunk Eventcount Example Returns the number of events in the specified indexes. This example is the same as the previous example except that an. Calculate the average duration grouped by a specific field. This is the current search logic that i am using. I have the following search: If you use federated search for splunk, you can find the count of events in. Splunk Eventcount Example.
From securityzone.vn
Splunk Splunk 7.x Fundamentals 2 Module 10 Working with Tags and Splunk Eventcount Example I have the following search: I would like to return the number of events in which new state = state one. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. The objective of this search is to count the number of events in a search result. | eventcount. Splunk Eventcount Example.
From www.function1.com
Event Sampling Splunk 6.4 Feature Function1 Splunk Eventcount Example If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This is the current search logic that i am using. I have the following search: Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. I would like to. Splunk Eventcount Example.
From bceweb.org
Splunk Chart Span A Visual Reference of Charts Chart Master Splunk Eventcount Example Returns the number of events in the specified indexes. I have the following search: This example is the same as the previous example except that an. This is the current search logic that i am using. | eventcount summarize=false index=* report_size=true. The objective of this search is to count the number of events in a search result. Want to count. Splunk Eventcount Example.
From community.splunk.com
Solved Splunk stats count group by multiple fields Splunk Community Splunk Eventcount Example If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This example is the same as the previous example except that an. Returns the number of events in the specified indexes. | rename content.orderid as order id. Calculate the average duration grouped by a specific field. I have the. Splunk Eventcount Example.
From queirozf.com
Splunk Examples Timecharts Splunk Eventcount Example If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. The objective of this search is to count the number of events in a search result. This example is the same as the previous example except that an. | eventcount summarize=false index=* report_size=true. Returns the number of events in. Splunk Eventcount Example.
From splunkbase.com
Network Behavior Analytics for Splunk Splunkbase Splunk Eventcount Example I would like to return the number of events in which new state = state one. The objective of this search is to count the number of events in a search result. Calculate the average duration grouped by a specific field. This is the current search logic that i am using. This example is the same as the previous example. Splunk Eventcount Example.
From www.splunk.com
Using Splunk for SEO Log File Analysis Splunk Splunk Eventcount Example This example is the same as the previous example except that an. Returns the number of events in the specified indexes. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. Calculate the average duration grouped by a specific field. This is the current search logic that i am using.. Splunk Eventcount Example.
From examples.javacodegeeks.com
Splunk Basic Search Example Java Code Geeks Splunk Eventcount Example Calculate the average duration grouped by a specific field. I have the following search: The objective of this search is to count the number of events in a search result. This example is the same as the previous example except that an. This is the current search logic that i am using. Want to count all events from specific indexes. Splunk Eventcount Example.
From examples.javacodegeeks.com
Splunk Calculated Fields Example Java Code Geeks Splunk Eventcount Example Returns the number of events in the specified indexes. The objective of this search is to count the number of events in a search result. | eventcount summarize=false index=* report_size=true. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. If you use federated search for splunk, you can find. Splunk Eventcount Example.
From community.splunk.com
Is there a way to display more than 20 charts at a... Splunk Community Splunk Eventcount Example If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. | eventcount summarize=false index=* report_size=true. This is the current search logic that i am using. Calculate the average duration grouped by a specific field. The objective of this search is to count the number of events in a search. Splunk Eventcount Example.
From hodgkins.io
Splunk Spotlight The Lookup Command Splunk Eventcount Example I have the following search: I would like to return the number of events in which new state = state one. Returns the number of events in the specified indexes. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. | eventcount summarize=false index=* report_size=true. Calculate the average duration. Splunk Eventcount Example.
From kinneygroup.com
Splunk Collect Command Using It For Summary Indexing Kinney Group Splunk Eventcount Example I have the following search: This example is the same as the previous example except that an. Returns the number of events in the specified indexes. | eventcount summarize=false index=* report_size=true. The objective of this search is to count the number of events in a search result. Want to count all events from specific indexes say abc, pqr and xyz. Splunk Eventcount Example.
From www.itprotoday.com
Splunk .conf23 Boosts Observability, Security, AIPowered Products Splunk Eventcount Example This is the current search logic that i am using. The objective of this search is to count the number of events in a search result. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. | eventcount summarize=false index=* report_size=true. I would like to return the number of. Splunk Eventcount Example.
From queirozf.com
Splunk Examples Manipulating Text and Strings Splunk Eventcount Example The objective of this search is to count the number of events in a search result. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. | rename content.orderid as order id. I would like to return the number of events in which new state = state one. Calculate the. Splunk Eventcount Example.
From www.socinvestigation.com
Splunk Features Quick Guide on Key Elements Security Investigation Splunk Eventcount Example Returns the number of events in the specified indexes. This example is the same as the previous example except that an. I have the following search: If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. | eventcount summarize=false index=* report_size=true. The objective of this search is to count. Splunk Eventcount Example.
From www.youtube.com
What is Splunk ITSI?—Splunk's Solution for ITOps Explained Splunk Eventcount Example Calculate the average duration grouped by a specific field. | rename content.orderid as order id. This example is the same as the previous example except that an. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. I have the following search: I would like to return the number of. Splunk Eventcount Example.
From hollywoodholoser.weebly.com
Splunk website monitor remote server hollywoodholoser Splunk Eventcount Example The objective of this search is to count the number of events in a search result. Calculate the average duration grouped by a specific field. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This example is the same as the previous example except that an. | rename. Splunk Eventcount Example.
From www.loggly.com
Splunk Cloud vs. Loggly 2019 Speed Test Loggly Splunk Eventcount Example Calculate the average duration grouped by a specific field. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This example is the same as the previous example except that an. | rename content.orderid as order id. Want to count all events from specific indexes say abc, pqr and. Splunk Eventcount Example.
From www.splunk.com
Using Splunk for SEO Log File Analysis Splunk Splunk Eventcount Example Calculate the average duration grouped by a specific field. I would like to return the number of events in which new state = state one. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This example is the same as the previous example except that an. I have. Splunk Eventcount Example.
From subscription.packtpub.com
Splunk 7.x Quick Start Guide Splunk Eventcount Example | rename content.orderid as order id. Calculate the average duration grouped by a specific field. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This example is the same as the previous example except that an. I have the following search: This is the current search logic that. Splunk Eventcount Example.
From www.youtube.com
Splunk Scripted Input Example Load data to splunk using any scripts Splunk Eventcount Example I have the following search: The objective of this search is to count the number of events in a search result. Returns the number of events in the specified indexes. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. This is the current search logic that i am. Splunk Eventcount Example.
From chase-seibert.github.io
Getting started with Splunk as an Engineer Chase Seibert Blog Splunk Eventcount Example If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. I would like to return the number of events in which new state = state one. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. This is the. Splunk Eventcount Example.
From queirozf.com
Splunk Examples Manipulating Text and Strings Splunk Eventcount Example This example is the same as the previous example except that an. I would like to return the number of events in which new state = state one. Returns the number of events in the specified indexes. The objective of this search is to count the number of events in a search result. I have the following search: If you. Splunk Eventcount Example.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Eventcount Example The objective of this search is to count the number of events in a search result. Calculate the average duration grouped by a specific field. | rename content.orderid as order id. This is the current search logic that i am using. This example is the same as the previous example except that an. I would like to return the number. Splunk Eventcount Example.
From www.youtube.com
What is Splunk Splunk Introduction and Overview in 5 minutes YouTube Splunk Eventcount Example | rename content.orderid as order id. Returns the number of events in the specified indexes. I would like to return the number of events in which new state = state one. | eventcount summarize=false index=* report_size=true. This example is the same as the previous example except that an. I have the following search: The objective of this search is to. Splunk Eventcount Example.
From geek-university.com
top command Splunk Splunk Eventcount Example The objective of this search is to count the number of events in a search result. This is the current search logic that i am using. | eventcount summarize=false index=* report_size=true. | rename content.orderid as order id. This example is the same as the previous example except that an. Want to count all events from specific indexes say abc, pqr. Splunk Eventcount Example.
From subscription.packtpub.com
What is Splunk? Splunk 7.x Quick Start Guide Splunk Eventcount Example Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. I have the following search: Calculate the average duration grouped by a specific field. This is the current search logic that i am using. Returns the number of events in the specified indexes. I would like to return the number. Splunk Eventcount Example.
From www.stationx.net
What Is Splunk Used For? (2024 Guide) Splunk Eventcount Example | eventcount summarize=false index=* report_size=true. If you use federated search for splunk, you can find the count of events in specified indexes on your federated providers. I would like to return the number of events in which new state = state one. | rename content.orderid as order id. This example is the same as the previous example except that an.. Splunk Eventcount Example.
From documentation.n-able.com
Splunk logging Splunk Eventcount Example I would like to return the number of events in which new state = state one. This example is the same as the previous example except that an. I have the following search: Returns the number of events in the specified indexes. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h. Splunk Eventcount Example.
From www.splunk.com
Using Splunk for SEO Log File Analysis Splunk Splunk Eventcount Example Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. | rename content.orderid as order id. I have the following search: Calculate the average duration grouped by a specific field. | eventcount summarize=false index=* report_size=true. This example is the same as the previous example except that an. If you use. Splunk Eventcount Example.
From lantern.splunk.com
Installing and configuring Splunk Stream Splunk Lantern Splunk Eventcount Example I have the following search: | rename content.orderid as order id. | eventcount summarize=false index=* report_size=true. I would like to return the number of events in which new state = state one. Calculate the average duration grouped by a specific field. Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using. Splunk Eventcount Example.
From www.olcya.com
Splunk dans le monde des données Olcya Splunk Eventcount Example Want to count all events from specific indexes say abc, pqr and xyz only for span of 1h using tstats. I would like to return the number of events in which new state = state one. This example is the same as the previous example except that an. Returns the number of events in the specified indexes. The objective of. Splunk Eventcount Example.