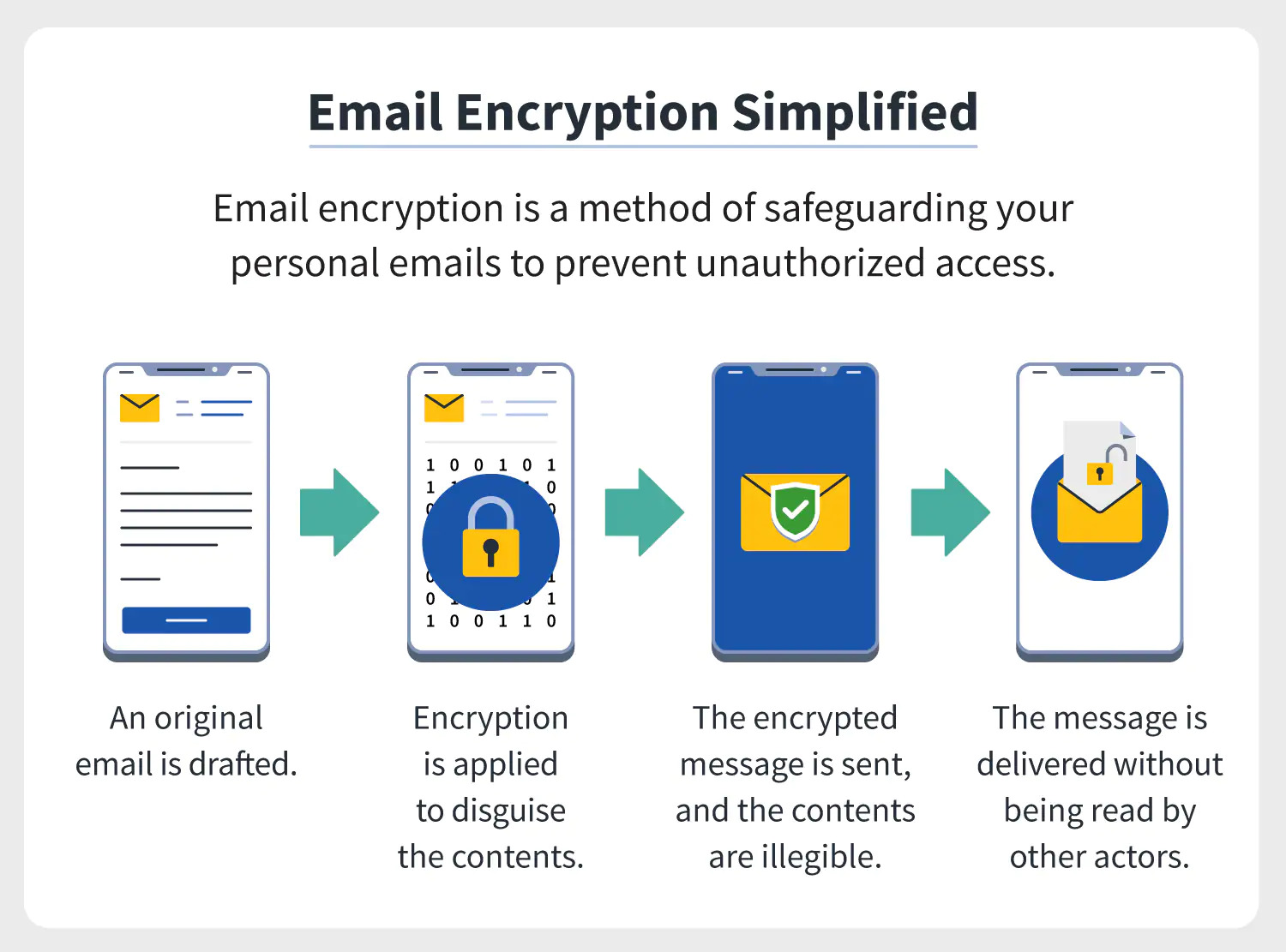
Signing Message Encryption . Is there like a piece of plain text that we sign and pass it through, for. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Do we sign the whole file so it becomes sort of encrypted? In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an.
from www.indrastra.com
Encryption and signing are two methods used widely for data security. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Do we sign the whole file so it becomes sort of encrypted? In signing, a digital signature is used for authenticating the data sender. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Is there like a piece of plain text that we sign and pass it through, for.
How to Encrypt an Email Communication?
Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption and signing are two methods used widely for data security. In signing, a digital signature is used for authenticating the data sender. Do we sign the whole file so it becomes sort of encrypted?
From aws.amazon.com
Combining encryption and signing with AWS KMS asymmetric keys AWS Security Blog Signing Message Encryption Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. In. Signing Message Encryption.
From coderjony.com
CoderJony Difference between Asymmetric Encryption and Signing (Digital Signature) Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. In signing, a digital signature is used for authenticating the data sender. Encryption provides confidentiality where users can encrypt any data. Signing Message Encryption.
From pixelprivacy.com
Encrypted Messaging What Is It, And Why Should You Use It? Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we sign and pass it through,. Signing Message Encryption.
From learn.g2.com
What Does Encryption Mean and Why Is It Important? Signing Message Encryption Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we sign and pass it through, for. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Do we sign the whole file so it becomes sort of. Signing Message Encryption.
From coderscay.blogspot.com
How to Encrypt and Decrypt the files and text using GPG/PGP tool Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. In signing, a digital signature is used for authenticating the data sender. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encryption and signing are two methods used widely for. Signing Message Encryption.
From www.mdpi.com
Applied Sciences Free FullText A Novel Digital Signature Scheme for Advanced Asymmetric Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. In signing, a digital signature is used for authenticating the data sender. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt. Signing Message Encryption.
From www.docusign.com
How Digital Signatures Work DocuSign Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Do we sign the whole file so it becomes sort of encrypted? Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting. Signing Message Encryption.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. Do we sign the whole file so it becomes sort of encrypted? Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Is there like a piece of plain text that we sign and pass it through, for.. Signing Message Encryption.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email. Signing Message Encryption.
From www.indrastra.com
How to Encrypt an Email Communication? Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. In signing, a digital signature is used. Signing Message Encryption.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we. Signing Message Encryption.
From www.poweradmin.com
A Quick Guide to Encrypted Messaging Network Wrangler Tech Blog Signing Message Encryption Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Encryption and signing are two methods used widely for data security. Do we sign the whole file so it becomes sort of encrypted? Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable.. Signing Message Encryption.
From www.simplilearn.com
RSA Algorithm Secure Your Data with PublicKey Encryption Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Do we sign the whole file so it becomes sort of encrypted? Encryption and signing are two methods. Signing Message Encryption.
From slideplayer.com
Cryptography. ppt download Signing Message Encryption Encryption and signing are two methods used widely for data security. In signing, a digital signature is used for authenticating the data sender. Do we sign the whole file so it becomes sort of encrypted? Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Is there like a piece. Signing Message Encryption.
From www.dreamstime.com
Hand Writing Sign Email Encryption. Business Concept Systematic Tactic in Maximizing Email Signing Message Encryption Encryption and signing are two methods used widely for data security. In signing, a digital signature is used for authenticating the data sender. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Do. Signing Message Encryption.
From www.usenix.org
Sample Encrypted Message Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Is there like a piece of plain text that we sign and pass it through, for. Do we sign the whole file so it becomes sort of encrypted?. Signing Message Encryption.
From turingpoint.de
Email Encryption with PGP turingpoint Signing Message Encryption Encryption and signing are two methods used widely for data security. Do we sign the whole file so it becomes sort of encrypted? Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key.. Signing Message Encryption.
From www.thesslstore.com
Symmetric Encryption Algorithms Live Long & Encrypt Hashed Out by The SSL Store™ Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key.. Signing Message Encryption.
From securityboulevard.com
7 Ways to Increase Email Security with Automated Encryption (Infographic) Security Boulevard Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it. Signing Message Encryption.
From blog.mdaemon.com
Encrypting vs. Signing with OpenPGP. What’s the Difference? Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Do we sign the whole file so it becomes sort of encrypted? Is there like a piece of plain text that we sign and pass it through, for. Encrypting, or obscuring, emails is a process designed to keep. Signing Message Encryption.
From www.pandasecurity.com
PGP Encryption The Email Security Standard Panda Security Signing Message Encryption Encryption and signing are two methods used widely for data security. Do we sign the whole file so it becomes sort of encrypted? Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable.. Signing Message Encryption.
From blog.4d.com
CryptoKey Encrypt, Decrypt, Sign, and Verify! 4D Blog Signing Message Encryption Do we sign the whole file so it becomes sort of encrypted? Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encrypting, or obscuring, emails is a. Signing Message Encryption.
From www.thesslstore.com
What Is a Message Authentication Code (MAC)? Hashed Out by The SSL Store™ Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Encryption and signing are two methods used widely for data security. In signing, a digital signature is used for authenticating the data sender. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption provides confidentiality where. Signing Message Encryption.
From www.zoho.com
S/MIME Encryption and other security extensions for email Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Do we. Signing Message Encryption.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Do we sign the whole file. Signing Message Encryption.
From office.losrios.edu
Sending Encrypted Email Exchange and Office Online Signing Message Encryption Do we sign the whole file so it becomes sort of encrypted? Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we sign and pass it through, for. Encrypting,. Signing Message Encryption.
From www.preveil.com
Public and private encryption keys PreVeil Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Do we sign the whole file so it becomes sort of encrypted? In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. A digital signature attached to an email message offers. Signing Message Encryption.
From preyproject.com
Encryption choices rsa vs. aes explained Prey Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Do we sign the whole file so. Signing Message Encryption.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. A digital signature attached to an email. Signing Message Encryption.
From www.okta.com
Hashing vs. Encryption Definitions & Differences Okta Signing Message Encryption In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. Is there like a piece of plain text that we sign and pass it through, for. Do we sign the whole file so it becomes sort of encrypted? A digital signature attached to an email message offers. Signing Message Encryption.
From www.lumificyber.com
What is Email Encryption? Methods, Keys, Asymmetric RSA Security Lumifi Cybersecurity Signing Message Encryption Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. In signing, a digital signature is used for authenticating the data sender. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Is there like a piece of plain text that we sign. Signing Message Encryption.
From signx.wondershare.com
Digital Signature Example and Digital Signature Processing Signing Message Encryption Is there like a piece of plain text that we sign and pass it through, for. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Encryption and signing are two methods used. Signing Message Encryption.
From xmtp.org
Invitation and message encryption with XMTP Signing Message Encryption Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key. Is there like a piece of plain text that we sign and pass it through, for. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. Do we sign the whole file so. Signing Message Encryption.
From blog.mailfence.com
Digital signatures. How do digitally signed emails work? Signing Message Encryption A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. In signing, a digital signature is used for authenticating the data sender. Encryption and signing are two methods used widely for data security. Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold. Signing Message Encryption.
From learn.microsoft.com
Legacy information for Office 365 Message Encryption Microsoft Purview Signing Message Encryption Encrypting, or obscuring, emails is a process designed to keep cybercriminals—especially identity thieves—from getting hold of valuable. A digital signature attached to an email message offers another layer of security by providing assurance to the recipient that you—not an. In signing, a digital signature is used for authenticating the data sender. Do we sign the whole file so it becomes. Signing Message Encryption.