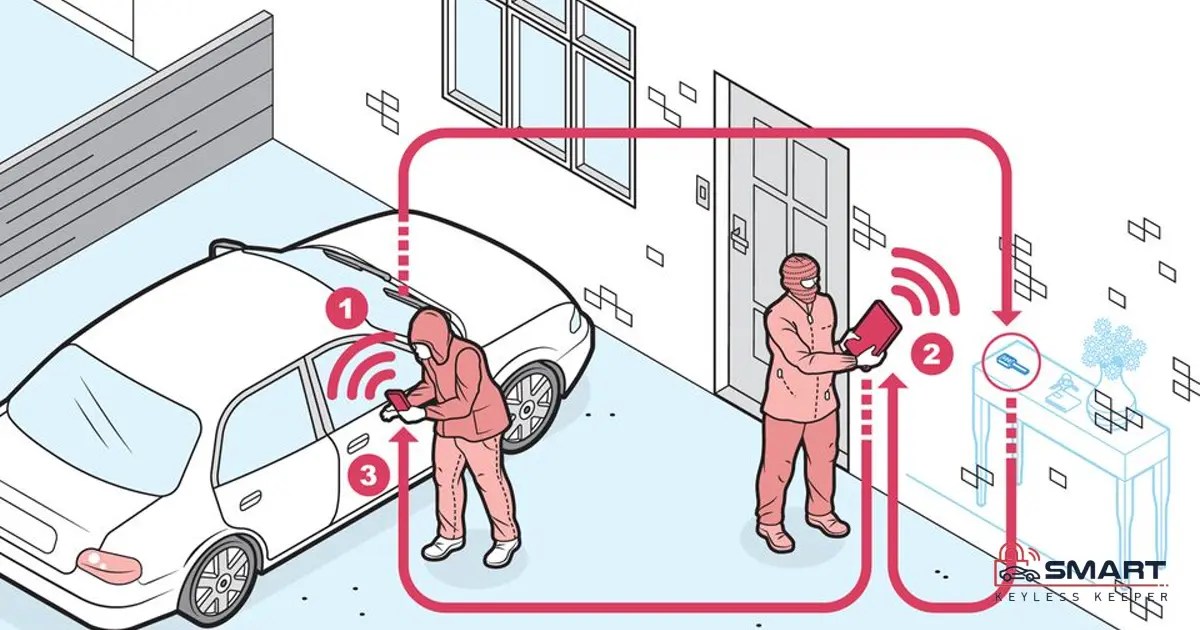
Relay Attack Defense . During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind of attack.
from smartkeylessprotector.com
In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack.
Relay attack All you need to know Smart Keyless Protector
Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind of attack.
From www.slideserve.com
PPT ZeroInteraction Authentication and Relay Attacks PowerPoint Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From smartkeylessprotector.com
Relay attack All you need to know Smart Keyless Protector Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.threatshub.org
New Bluetooth Hack Can Unlock Your Tesla And More ThreatsHub Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.slideserve.com
PPT Relay Attacks on Passive Keyless Entry and Start Systems in Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From nairpaa.github.io
Part 5 SMB Relay Attack Nairpaa Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.fleetaccess.nl
Wat is relay attack? En hoe beveilig ik de auto daartegen? Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.slideserve.com
PPT Keep your enemies close distance bounding against smart card Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.youtube.com
What is a Keyless Relay Attack? How to protect against Car Theft YouTube Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.slideserve.com
PPT A LowCost Method to Thwart Relay Attacks in Wireless Sensor Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From rdctd.pro
Car Relay Attack AntiTheft Guide » RDCTD Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.researchgate.net
(PDF) SideChannel Security on Key Exchange Protocol (KEP) Timing and Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From tcm-sec.com
SMB Relay Attacks and Active Directory TCM Security Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.scirp.org
Vehicle Relay Attack Avoidance Methods Using RF Signal Strength Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.slideserve.com
PPT ZeroInteraction Authentication and Relay Attacks PowerPoint Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.youtube.com
🚀 LLMNR /NBTNS SMB Relay Responder Impacket Hashcat MS AD Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.slideserve.com
PPT A LowCost Method to Thwart Relay Attacks in Wireless Sensor Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.slideserve.com
PPT Keep Your Enemies Close Distance Bounding Against Smartcard Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From stridergearhead.medium.com
SMB Relay An AD Attack. What is SMB Relay? by Aditya Jha Medium Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From slideplayer.com
Relay Threat Model for TGaz ppt download Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.youtube.com
DFSCoerce NTLM Relay Attack Threat SnapShot YouTube Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From identitymanagementinstitute.org
Relay Attack Risks and Prevention Identity Management Institute® Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From slideplayer.com
Relay Threat Model for TGaz ppt download Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.researchgate.net
The relay attack in practice (a) opening the door with the relay. (b Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.hackingloops.com
SMB Relay Attack Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From militaryembedded.com
Satellite relay system intends to augment U.S. space nationalsecurity Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.hackingloops.com
SMB Relay Attack Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.thecybersecuritytimes.com
Critical Microsoft vulnerability threatens NTLM Relay Attack PetitPotam Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.slideserve.com
PPT Relay Attacks on Passive Keyless Entry and Start Systems in Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.semanticscholar.org
Figure 1 from Vehicle Relay Attack Avoidance Methods Using RF Signal Relay Attack Defense In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.secureauth.com
What is old is new again The Relay Attack SecureAuth Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.
From www.reconbee.com
New NTLM Relay Attack Lets Attackers Take Control Over Windows Domain Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From 3dautokeys.co.uk
Protection Against Relay Attacks 3D Autokeys Relay Attack Defense During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. In this post, we will look into the details on how to simulate this kind. Relay Attack Defense.
From www.comparitech.com
What is a Relay Attack (with examples) and How Do They Work? Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. During an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its. Relay Attack Defense.
From www.slideserve.com
PPT ZeroInteraction Authentication and Relay Attacks PowerPoint Relay Attack Defense In this post, we will look into the details on how to simulate this kind of attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or remote control) and its target system,. During an smb relay attack, attackers capture a valid authentication session and then relay it,. Relay Attack Defense.