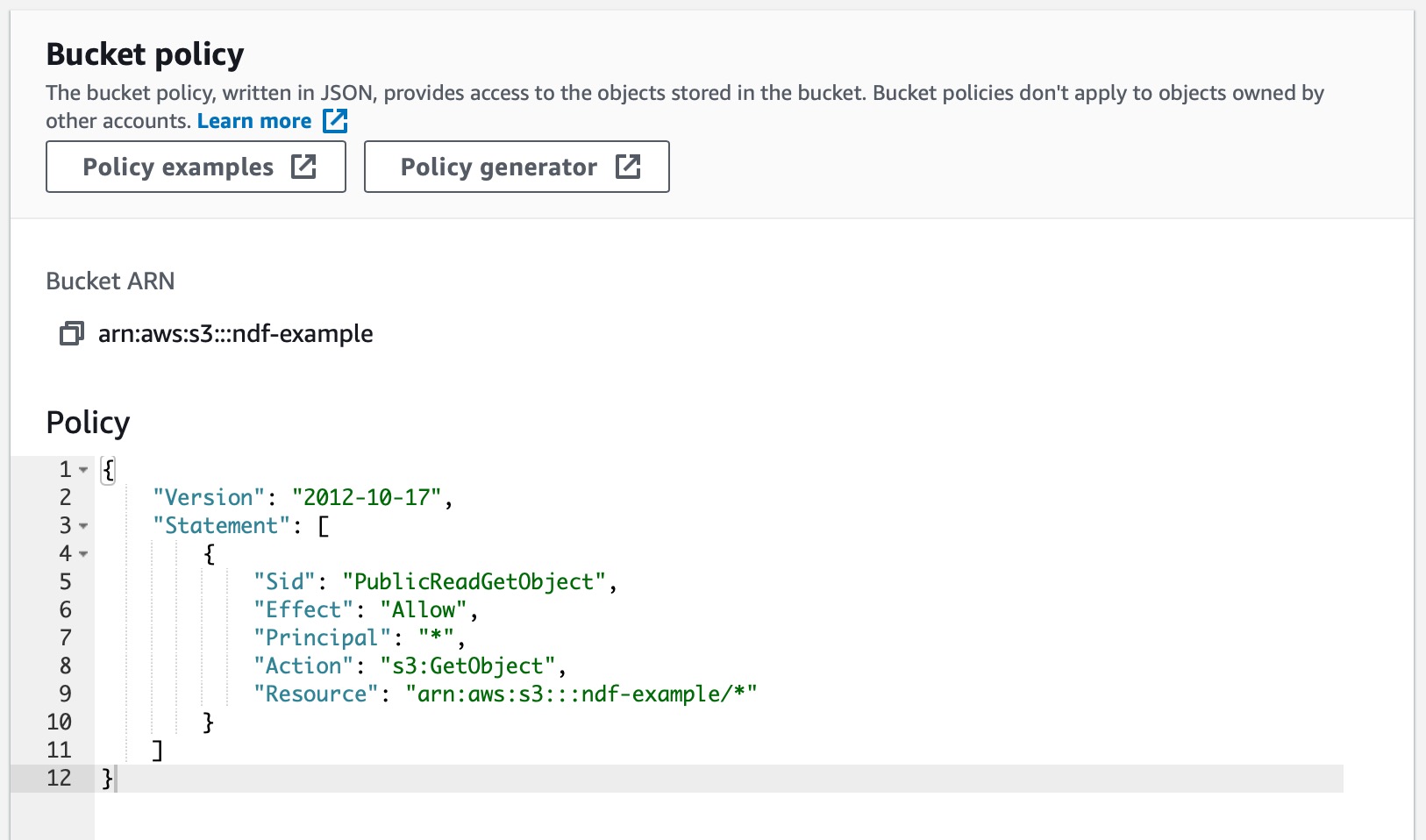
S3 Bucket Policy Wildcard Principal . To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. You can use wildcards as part of the resource arn. This policy allows akua, a user in account. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This is the format of a bucket policy generated with a cloudfront using origin access:. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. The following example bucket policy shows the effect, principal, action, and resource elements. Principals must always name a specific. Syntax of a s3 bucket policy to wildcard sourcearn condition.
from nodeployfriday.com
You can use wildcards as part of the resource arn. The following example bucket policy shows the effect, principal, action, and resource elements. Principals must always name a specific. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. Syntax of a s3 bucket policy to wildcard sourcearn condition. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. This policy allows akua, a user in account. This is the format of a bucket policy generated with a cloudfront using origin access:. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values.
Better Static site Hosting on S3 AWS Solutions Architect’s Guide
S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. This is the format of a bucket policy generated with a cloudfront using origin access:. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. The following example bucket policy shows the effect, principal, action, and resource elements. You can use wildcards as part of the resource arn. Principals must always name a specific. This policy allows akua, a user in account. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Syntax of a s3 bucket policy to wildcard sourcearn condition. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values.
From tech.asimio.net
Using an AWS S3 Bucket as your Maven Repository S3 Bucket Policy Wildcard Principal This policy allows akua, a user in account. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. When you specify users in a. S3 Bucket Policy Wildcard Principal.
From www.whizlabs.com
How to create a Lifecycle Policy for an S3 Bucket?Blog S3 Bucket Policy Wildcard Principal This policy allows akua, a user in account. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. Principals must always name a specific. You can use wildcards as part of the resource arn. Syntax of a s3 bucket policy to wildcard sourcearn condition. To prevent. S3 Bucket Policy Wildcard Principal.
From openvpn.net
Tutorial Configure AWS S3 bucket for CloudConnexa Log Streaming S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. The following example bucket policy shows the effect, principal, action, and resource elements. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. Principals must always name a. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
How do I use wildcards with a Principal element and explicit deny in an Amazon S3 bucket policy S3 Bucket Policy Wildcard Principal Syntax of a s3 bucket policy to wildcard sourcearn condition. The following example bucket policy shows the effect, principal, action, and resource elements. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. To grant or deny permissions to a set of objects, you can use wildcard characters. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
Understand S3 Bucket Policy (AWS beginners) YouTube S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. Principals must always name a specific. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This policy allows akua, a user in account. To prevent access to your amazon s3 buckets made by aws identity. S3 Bucket Policy Wildcard Principal.
From www.techlear.com
How to create a lifecycle policy for an S3 Bucket on AWS Techlear S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. You can use wildcard. S3 Bucket Policy Wildcard Principal.
From blog.jineshkumar.com
S3 Bucket Object Ownership Explained S3 Bucket Policy Wildcard Principal Syntax of a s3 bucket policy to wildcard sourcearn condition. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. You can use wildcard characters (* and ?). S3 Bucket Policy Wildcard Principal.
From www.youtube.com
How to apply Bucket Policy? What is Principal in S3? (English) YouTube S3 Bucket Policy Wildcard Principal This policy allows akua, a user in account. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities,. S3 Bucket Policy Wildcard Principal.
From www.ibm.com
Attaching an AWS S3 Bucket S3 Bucket Policy Wildcard Principal The following example bucket policy shows the effect, principal, action, and resource elements. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Syntax of a s3 bucket policy to wildcard sourcearn condition. Principals must always name a specific. To grant or deny permissions to a set of. S3 Bucket Policy Wildcard Principal.
From fyowfpqqd.blob.core.windows.net
Best Practices For S3 Bucket Policy at Clifford Guyton blog S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Syntax of a s3 bucket policy to wildcard sourcearn condition. This policy allows akua, a user in account. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names. S3 Bucket Policy Wildcard Principal.
From www.howtoforge.com
How to create a lifecycle policy for an S3 Bucket on AWS S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. This policy allows akua, a user in account. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. To grant or deny permissions to a set of objects, you can. S3 Bucket Policy Wildcard Principal.
From serverless-stack.com
Create an S3 Bucket S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This is the format of a bucket policy generated with a cloudfront using origin access:. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. Principals must always name. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
AWS S3 Bucket policies indepth intuition YouTube S3 Bucket Policy Wildcard Principal This is the format of a bucket policy generated with a cloudfront using origin access:. This policy allows akua, a user in account. The following example bucket policy shows the effect, principal, action, and resource elements. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Principals must. S3 Bucket Policy Wildcard Principal.
From stackoverflow.com
node.js Configuring AWS S3 bucket policies Stack Overflow S3 Bucket Policy Wildcard Principal Syntax of a s3 bucket policy to wildcard sourcearn condition. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To grant or deny permissions to a set of objects,. S3 Bucket Policy Wildcard Principal.
From www.scaler.com
S3 Bucket Policy Scaler Topics S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. Syntax of a s3 bucket policy to wildcard sourcearn condition. This policy allows akua, a user in account. When you specify users in a principal element, you cannot use a wildcard (*) to. S3 Bucket Policy Wildcard Principal.
From exodkftil.blob.core.windows.net
Aws S3 Bucket Policies Examples at Guy Deaton blog S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Principals must always name a specific. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. The following example bucket policy shows the effect, principal, action, and resource elements. This. S3 Bucket Policy Wildcard Principal.
From devsday.ru
AWS Cross Account S3 Access Through Lambda Functions DevsDay.ru S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. Syntax of a s3 bucket policy to wildcard sourcearn condition. The following example bucket policy shows the effect, principal, action, and resource elements. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This is the. S3 Bucket Policy Wildcard Principal.
From laptrinhx.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure Your Amazon S3 Data LaptrinhX S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. The following example bucket policy shows the effect, principal, action, and resource elements. You can use wildcards as part of the resource arn. Principals must always name a specific. This policy allows akua, a user in account. To prevent access to your. S3 Bucket Policy Wildcard Principal.
From www.geeksforgeeks.org
Create Bucket Policy in AWS S3 Bucket with Python S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. This is the format of a bucket policy generated with a cloudfront using origin access:. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other. S3 Bucket Policy Wildcard Principal.
From stackoverflow.com
Amazon S3 Change bucket policy with Java SDK Stack Overflow S3 Bucket Policy Wildcard Principal This policy allows akua, a user in account. This is the format of a bucket policy generated with a cloudfront using origin access:. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. The following. S3 Bucket Policy Wildcard Principal.
From www.scaler.com
S3 Bucket Policy Scaler Topics S3 Bucket Policy Wildcard Principal Syntax of a s3 bucket policy to wildcard sourcearn condition. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Principals must always name a specific. This is the format of. S3 Bucket Policy Wildcard Principal.
From nodeployfriday.com
Better Static site Hosting on S3 AWS Solutions Architect’s Guide S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. Syntax of a s3 bucket policy to wildcard sourcearn condition. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. You can use wildcards as part of the resource arn.. S3 Bucket Policy Wildcard Principal.
From techdirectarchive.com
How to grant public access to S3 Bucket using Policy TechDirectArchive S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. This is the format of a bucket policy generated with a cloudfront using origin access:. The following example bucket policy shows the effect, principal, action, and resource elements. Principals must always name. S3 Bucket Policy Wildcard Principal.
From www.techtarget.com
Establish S3 bucket security with proper access control TechTarget S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. This is the format of a bucket policy generated with a cloudfront using origin access:. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. The following example bucket policy shows. S3 Bucket Policy Wildcard Principal.
From docs.logz.io
Logz.io Docs AWS S3 bucket permissions & storage class required for archiving S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. This policy allows akua, a user in account. This is the format of a bucket policy generated with a cloudfront using origin access:. Syntax of a s3 bucket policy to wildcard sourcearn. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
Creating S3 Bucket and S3 Bucket Policy using AWS Cloud Formation YouTube S3 Bucket Policy Wildcard Principal This is the format of a bucket policy generated with a cloudfront using origin access:. Principals must always name a specific. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. You can use wildcard characters (* and ?) within arn segments (the parts separated by. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
Create S3 Bucket Give S3 bucket access only to authorized IAM user Apply Bucket Policy YouTube S3 Bucket Policy Wildcard Principal This policy allows akua, a user in account. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. The following example bucket policy shows the effect, principal, action, and resource elements. When you specify users in a principal element, you cannot use a wildcard (*) to mean all. S3 Bucket Policy Wildcard Principal.
From cloudkatha.com
How to Create S3 Bucket Policy using Terraform CloudKatha S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This is the format of a bucket policy. S3 Bucket Policy Wildcard Principal.
From theitbros.com
Controlling Access to S3 Buckets with AWS S3 Bucket Policy TheITBros S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. You can use wildcards as part of the resource arn. The following example bucket policy shows the effect, principal, action, and resource elements. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific. S3 Bucket Policy Wildcard Principal.
From dxoidreut.blob.core.windows.net
S3 Bucket Policy Allowed Actions at Edna Mendelson blog S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. This is the format of a bucket policy generated with a cloudfront using origin access:. You can use wildcards as part of the resource arn. Syntax of a s3 bucket policy to wildcard sourcearn condition. To. S3 Bucket Policy Wildcard Principal.
From www.k9security.io
Test S3 bucket policy using IAM simulator k9 Security S3 Bucket Policy Wildcard Principal The following example bucket policy shows the effect, principal, action, and resource elements. Principals must always name a specific. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. This policy. S3 Bucket Policy Wildcard Principal.
From fyowfpqqd.blob.core.windows.net
Best Practices For S3 Bucket Policy at Clifford Guyton blog S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. You can use wildcard characters (* and ?) within arn segments (the parts separated by colons) to. The following example bucket policy shows the effect, principal, action, and resource elements. To grant or deny permissions to a set of objects, you can. S3 Bucket Policy Wildcard Principal.
From 2ndsightlab.medium.com
S3 Server Access Log Bucket Policy by Teri Radichel Medium S3 Bucket Policy Wildcard Principal You can use wildcards as part of the resource arn. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions in a. Syntax of a s3 bucket policy to wildcard sourcearn condition.. S3 Bucket Policy Wildcard Principal.
From laptrinhx.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure Your Amazon S3 Data LaptrinhX S3 Bucket Policy Wildcard Principal The following example bucket policy shows the effect, principal, action, and resource elements. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. This is the format of a bucket policy generated with a cloudfront using origin access:. This policy allows akua, a user in account. To grant or deny permissions to. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
AWS S3 Tutorial (Part 3) How to set up Access Control on S3 ? IAM Policies & Bucket Policies S3 Bucket Policy Wildcard Principal The following example bucket policy shows the effect, principal, action, and resource elements. You can use wildcards as part of the resource arn. Syntax of a s3 bucket policy to wildcard sourcearn condition. This is the format of a bucket policy generated with a cloudfront using origin access:. This policy allows akua, a user in account. When you specify users. S3 Bucket Policy Wildcard Principal.