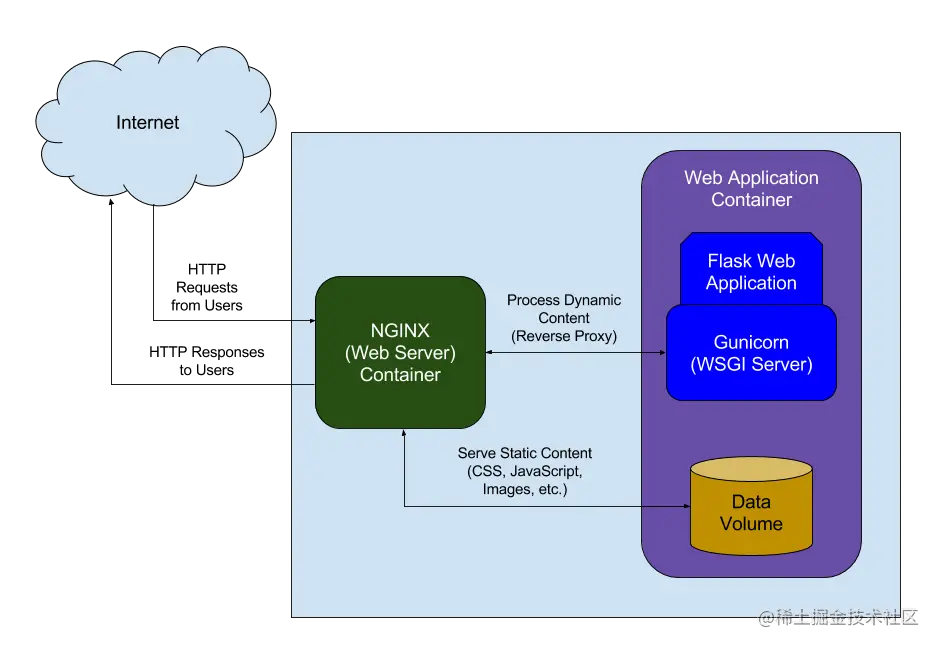
Nginx Flask Exploit . Registration is based on invites. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If success, we may be able to exploit with os command injection.
from blog.csdn.net
If we can access to /console page,. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If success, we may be able to exploit with os command injection.
如何为 Flask 应用配置 Nginx_flask nginxCSDN博客
Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. If success, we may be able to exploit with os command injection. If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file.
From linuxtut.com
Using Flask with Nginx + gunicorn configuration [Local environment] Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If we can access to /console page,. If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Registration is based on invites.. Nginx Flask Exploit.
From stackoverflow.com
nginx How do I successfully deploy the flask app on ec2? Stack Overflow Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. If success, we may be able to exploit with os command injection. If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s. Nginx Flask Exploit.
From www.e-tinkers.com
How to properly host Flask application with Nginx and Guincorn ETinkers Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to. Nginx Flask Exploit.
From www.youtube.com
Dockerfile for NGINX Flask application with EC2 instance using Docker Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If success, we may be able to exploit with os command injection. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one. Nginx Flask Exploit.
From www.youtube.com
Python Tutorial Connecting Flask and Nginx with Docker YouTube Nginx Flask Exploit If success, we may be able to exploit with os command injection. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one. Nginx Flask Exploit.
From 9to5answer.com
[Solved] Python uWSGI configuration for NGINX+FLASK 9to5Answer Nginx Flask Exploit If success, we may be able to exploit with os command injection. If we can access to /console page,. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s. Nginx Flask Exploit.
From blog.csdn.net
如何为 Flask 应用配置 Nginx_flask nginxCSDN博客 Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at.. Nginx Flask Exploit.
From guneycansanli.github.io
Nginx Load Balancer Example With Flask App Guneycan Sanli Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by. Nginx Flask Exploit.
From flask.ivan-shamaev.ru
Python Flask 6. Обзор архитектуры приложения Flask + Nginx + Gunicorn Nginx Flask Exploit If success, we may be able to exploit with os command injection. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,.. Nginx Flask Exploit.
From www.youtube.com
How to setup Python Flask applications with Gunicorn and Nginx on Nginx Flask Exploit If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. Today, let’s discuss one. Nginx Flask Exploit.
From medium.com
Deploy a Flask app with NGINX on AWS ECS Medium Nginx Flask Exploit If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If success, we may be able to exploit with os command injection. A simple get request, like. Nginx Flask Exploit.
From exocifzmg.blob.core.windows.net
How To Use Flask With Nginx at Krystal Hairston blog Nginx Flask Exploit If success, we may be able to exploit with os command injection. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one. Nginx Flask Exploit.
From j2logo.com
Desplegar una aplicación Flask en producción con nginx + gunicorn Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If we can access to /console page,. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. If success, we may be able to exploit with os command injection. The. Nginx Flask Exploit.
From medium.com
Containerizing a Flask App with Celery, Redis, Nginx and uWSGI for Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,. Today, let’s. Nginx Flask Exploit.
From daftsex-hd.com
Python Flask Application On Raspberry Pi With Nginx And Uwsgi Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If success, we may be able to exploit with os command injection. If we can access to /console page,. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The. Nginx Flask Exploit.
From www.youtube.com
OpenSSL with nginx Deploy Flask application on EC2 p.10 YouTube Nginx Flask Exploit If success, we may be able to exploit with os command injection. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If we can access to /console page,. The suggestion is made to exploit. Nginx Flask Exploit.
From avinton.com
Docker Compose(Nginx + Flask + MySQL)演習 Avintonジャパン株式会社 Nginx Flask Exploit If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. Today, let’s discuss one. Nginx Flask Exploit.
From medium.com
Deploy Flask app in Nginx using uWSGI — with architectural explanation Nginx Flask Exploit The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,. If success, we may be able to exploit with os command injection. Registration is based on invites. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to.. Nginx Flask Exploit.
From 9to5tutorial.com
[with image figure] Nginx+gunicorn+Flask Dockerized 9to5Tutorial Nginx Flask Exploit Registration is based on invites. If we can access to /console page,. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If success, we may be able to exploit with. Nginx Flask Exploit.
From www.youtube.com
How to Deploy Flask Application with Nginx using Gunicorn on Linux Nginx Flask Exploit If we can access to /console page,. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. Nginx Flask Exploit.
From www.howtoforge.com
How to Install Flask with Nginx and Gunicorn on Ubuntu 22.04 Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If success, we may be able to exploit with os command injection. If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like. Nginx Flask Exploit.
From github.com
GitHub wgetnz/nginx1.21.5exploit exploit nginx Nginx Flask Exploit The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by. Nginx Flask Exploit.
From www.alexandersimoes.com
Deploying a Flask Site Using NGINX Gunicorn, Supervisor and Virtualenv Nginx Flask Exploit If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. If we can access. Nginx Flask Exploit.
From blog.csdn.net
Flask+Tornado+Nginx实现Windows环境下多并发部署Flask接口应用_flask wsgicontainerCSDN博客 Nginx Flask Exploit Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to.. Nginx Flask Exploit.
From www.youtube.com
Nix on Replit Production Stack with Nginx, Postgress, and Python Nginx Flask Exploit Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If we can access to /console page,. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. If success, we may be able to exploit with os command injection.. Nginx Flask Exploit.
From exo.mk
Build and deploy Flask app with Gunicorn and Nginx EXO Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. If we can access to /console page,. If success, we may be able to exploit with os command injection. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s. Nginx Flask Exploit.
From qiita.com
NGINX + NGINX Unit + Flask で Pythonの アプリを動かす nginx Qiita Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. If success, we may be. Nginx Flask Exploit.
From blog.neilblaze.live
Intersecting Flask with NGINX Nginx Flask Exploit The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Registration is based on invites. If success, we may be able to exploit with os command injection. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If we can access. Nginx Flask Exploit.
From dlabs.ai
How to spin up a simple Flask app using NGINX — in 15 minutes or less Nginx Flask Exploit Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If we can access to /console page,. If success, we may be able to exploit with. Nginx Flask Exploit.
From www.alexandersimoes.com
Deploying a Flask Site Using NGINX Gunicorn, Supervisor and Virtualenv Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. Registration is based on invites. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file.. Nginx Flask Exploit.
From www.raspberrypi-spy.co.uk
Running Flask under NGINX on the Raspberry Pi Raspberry Pi Spy Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If success, we may be able to exploit with os command injection. If we can access to /console page,. Registration is based on invites. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s. Nginx Flask Exploit.
From www.datasciencelearner.com
How to Deploy Flask App using Nginx and Gunicorn ? Docker Nginx Flask Exploit Registration is based on invites. If success, we may be able to exploit with os command injection. If we can access to /console page,. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to.. Nginx Flask Exploit.
From datadevhub.com
Using Nginx for Production ready Flask app with uWSGI Data Developer Hub Nginx Flask Exploit If we can access to /console page,. If success, we may be able to exploit with os command injection. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. Registration is based on invites. A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. The. Nginx Flask Exploit.
From velog.io
[Nginx, uWSGI, Flask] 설치 on AWS EC2 Nginx Flask Exploit Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug initialization file. Registration is based on invites. If we can access to /console page,. If success, we may be able to exploit with os command injection.. Nginx Flask Exploit.
From github.com
GitHub brendancol/nginxgunicornflask Simple example architecture Nginx Flask Exploit A simple get request, like get /nginx.conf, could expose sensitive information by serving the nginx configuration file located at. If success, we may be able to exploit with os command injection. If we can access to /console page,. Today, let’s discuss one of them, a vulnerability found in flask applications that can lead to. The suggestion is made to exploit. Nginx Flask Exploit.