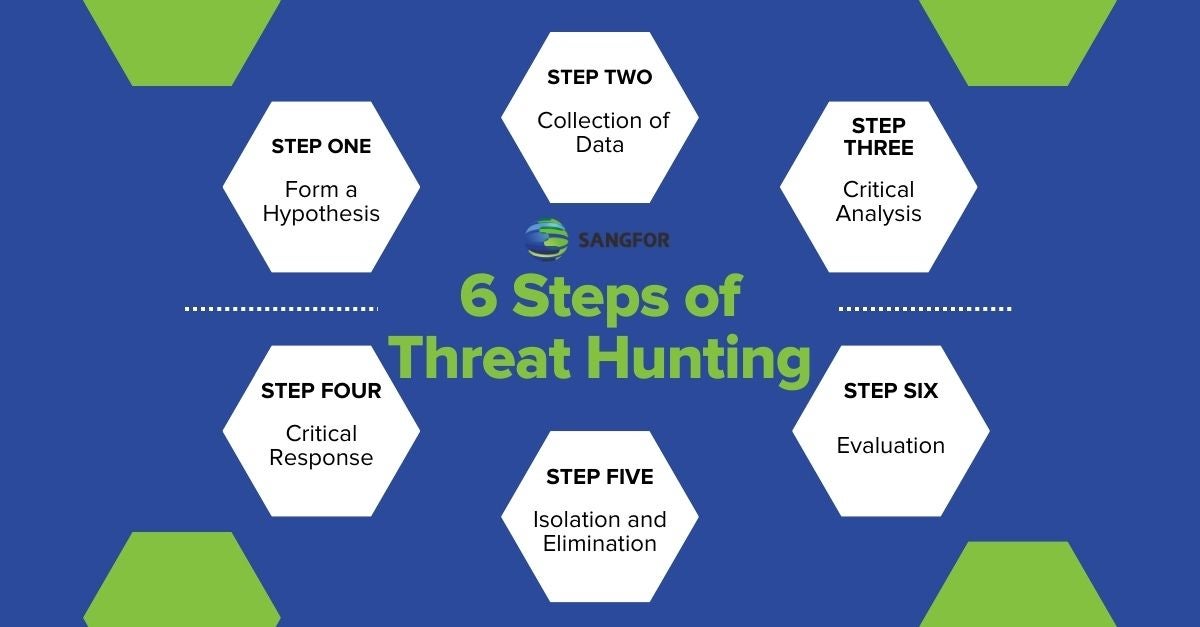
Threat Hunting Sites . This repository is a library for hunting and detecting cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Find out if your data has been exposed on the deep web. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or.
from www.sangfor.com
This library contains a list of: Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Find out if your data has been exposed on the deep web. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This repository is a library for hunting and detecting cyber threats.
Cyber Threat Hunting Definition, Techniques, and Solutions
Threat Hunting Sites Find out if your data has been exposed on the deep web. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This library contains a list of: Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Find out if your data has been exposed on the deep web. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This repository is a library for hunting and detecting cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top.
From www.sangfor.com
Cyber Threat Hunting Definition, Techniques, and Solutions Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. Find out if your data has been exposed on the deep web. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This repository. Threat Hunting Sites.
From www.bitlyft.com
Cyber Threat Hunting What You Need to Know Threat Hunting Sites This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a. Threat Hunting Sites.
From www.cloud4c.com
Threat Hunting Services Cloud4C Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. This repository is a library for hunting and detecting cyber threats. Find out if your data has been exposed on the deep web. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Threat hunting tools proactively search for and detect. Threat Hunting Sites.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Find out if your data has been exposed on the deep web. Hunter is. Threat Hunting Sites.
From www.uptycs.com
Threat Hunting Solutions Uptycs Threat Hunting Sites This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This library contains a list of: Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats.. Threat Hunting Sites.
From cyberwarzone.com
URLscan Threat Hunting For Beginners Cyberwarzone Threat Hunting Sites This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Find out if your data has been exposed on the deep web. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems,. Threat Hunting Sites.
From searchsecurity.techtarget.com
Threat hunting techniques move beyond the SOC Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This library contains a list of: In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This repository is a library for hunting and. Threat Hunting Sites.
From proinf.com
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Find out if your data has been exposed on the deep web. Hunter is a powerful threat hunting. Threat Hunting Sites.
From www.sangfor.com
Cyber Threat Hunting Definition, Techniques, and Solutions Threat Hunting Sites This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Threat hunting tools proactively search for and. Threat Hunting Sites.
From www.microfocus.com
What is Cyber Threat Hunting? How it Works OpenText Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Threat hunting tools proactively search for and. Threat Hunting Sites.
From naturenex.net
Threat Hunting Practices And Tools To Secure Your Network Naturenex Threat Hunting Sites In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: This repository is a library for hunting. Threat Hunting Sites.
From www.logpoint.com
What is Cyber Threat Hunting? A simple guide to Threat Hunting Threat Hunting Sites This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This repository is a library for hunting and detecting cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s. Threat Hunting Sites.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Sites Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This repository is a library for hunting and detecting cyber threats. This library contains a list of: Find out if your data has been exposed on the deep web. Threat hunting tools proactively search for and detect potential security threats within an. Threat Hunting Sites.
From www.blusapphire.com
The Complete Guide To Threat Hunting Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Find out if your data has. Threat Hunting Sites.
From www.deepwatch.com
3 Ways Threat Hunting Improves Security Operations Deepwatch Threat Hunting Sites This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of:. Threat Hunting Sites.
From www.sangfor.com
Best ThreatHunting Tools Top 5 OpenSource Tools Threat Hunting Sites Find out if your data has been exposed on the deep web. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. In our quest to help. Threat Hunting Sites.
From www.knowledgehut.com
Cyber Threat Hunting Types, Methodologies, Best Practices Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Find out if your data has been exposed on the deep web. In our quest to help security. Threat Hunting Sites.
From www.sentinelone.com
What is Threat Hunting? A Cybersecurity Guide 101 Threat Hunting Sites This library contains a list of: In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This repository is a library for hunting and detecting cyber threats. Find out if your data has been exposed on the deep web. Hunter is a powerful threat hunting platform designed to help. Threat Hunting Sites.
From antidos.com
Ransomware As a Service What is It and How Can You Protect Your Threat Hunting Sites Find out if your data has been exposed on the deep web. This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This library contains a list of: In our quest to help security operations and incident response teams work more. Threat Hunting Sites.
From threatcop.com
Different Types of Threat Hunting Threatcop Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. This repository is a library for hunting and detecting cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Find out if your data has been exposed on the deep web. This library contains a list of: Hunter is. Threat Hunting Sites.
From socradar.io
Step by Step Threat Hunting SOCRadar® Cyber Intelligence Inc. Threat Hunting Sites Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. This repository is a library for hunting. Threat Hunting Sites.
From infosectrain.wordpress.com
Threat Hunting Tools in Cybersecurity Threat Hunting Sites This library contains a list of: Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a list. Threat Hunting Sites.
From www.strongdm.com
What is Threat Hunting? Defintion StrongDM Threat Hunting Sites In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Find out. Threat Hunting Sites.
From cybersecuritynews.com
20 Best Threat Hunting Tools in 2023 Cyber Security News Threat Hunting Sites In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This repository is a library for hunting and detecting cyber threats. Tools, guides, tutorials, instructions, resources, intelligence, detection and. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Threat hunting. Threat Hunting Sites.
From webapi.bu.edu
🎉 Active security threats. 6 Network Security Threats & What You Can Do Threat Hunting Sites This library contains a list of: Find out if your data has been exposed on the deep web. This repository is a library for hunting and detecting cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and. Threat Hunting Sites.
From kryptera.se
Threat Hunting med Bro, Critical Stack och AlienVault OTX Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Find out if your data has been exposed. Threat Hunting Sites.
From cybersecuritynews.com
20 Best Threat Hunting Tools in 2023 Cyber Security News Threat Hunting Sites This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This library contains a list of: Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. In our quest to help security operations and. Threat Hunting Sites.
From www.cyberproof.com
What is threat hunting? CyberProof Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Find out if your data has been exposed on the deep web. This. Threat Hunting Sites.
From www.dts-solution.com
A Threat Hunt tale Threat Hunting Sites This library contains a list of: This repository is a library for hunting and detecting cyber threats. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. In our quest to help security operations and. Threat Hunting Sites.
From cybeready.com
Top 9 Threat Hunting Tools for 2023 CybeReady Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Find out if your data has been exposed on the deep web. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This. Threat Hunting Sites.
From www.techtarget.com
Threat hunting technology is on the rise, so are threats TechTarget Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Find out if your data has been exposed on the deep web. Hunter is a powerful threat hunting. Threat Hunting Sites.
From www.fortinet.com
What is Threat Hunting? Threat Hunting Types and Techniques Threat Hunting Sites In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. This library contains a list of: This repository is a library for hunting and detecting cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. Tools, guides, tutorials, instructions, resources,. Threat Hunting Sites.
From www.crowdstrike.com
What is Cyber Threat Hunting? [Proactive Guide] CrowdStrike Threat Hunting Sites This library contains a list of: Tools, guides, tutorials, instructions, resources, intelligence, detection and. In our quest to help security operations and incident response teams work more effectively, we’ve created a list of the top. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This repository is a library for hunting. Threat Hunting Sites.
From threatcop.com
Steps of Threat Hunting Threatcop Threat Hunting Sites Tools, guides, tutorials, instructions, resources, intelligence, detection and. Find out if your data has been exposed on the deep web. This repository is a library for hunting and detecting cyber threats. Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. In our quest to help security operations and incident response teams work. Threat Hunting Sites.
From www.care247.tech
What is Threat Hunting? Threat Hunting Sites Threat hunting tools proactively search for and detect potential security threats within an organization’s network, systems, or. This library contains a list of: Find out if your data has been exposed on the deep web. Hunter is a powerful threat hunting platform designed to help organizations proactively detect and respond to cyber threats. This repository is a library for hunting. Threat Hunting Sites.