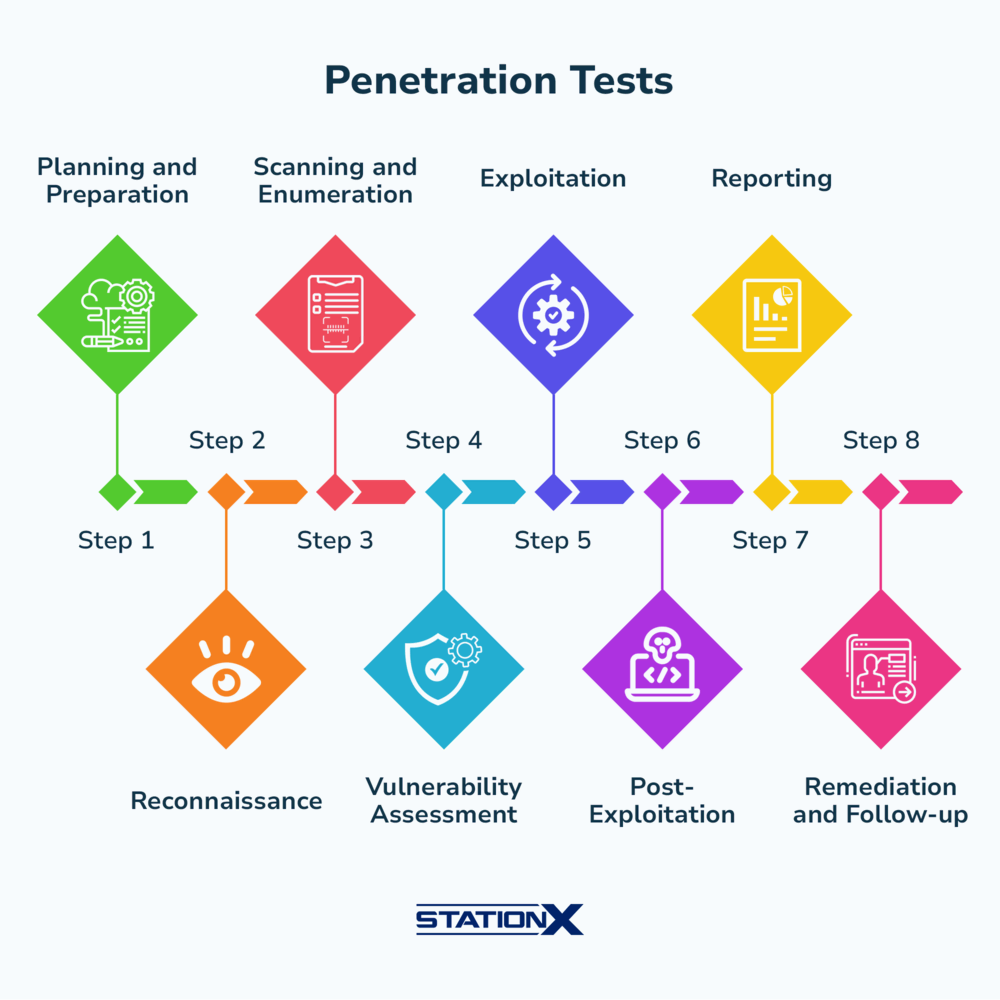
Pen Testing Scanning And Enumeration . They involve probing systems to gather info on open ports ,. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Let’s take a closer look at the 5 penetration testing phases. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. There are five penetration testing phases: Scanning and enumeration are crucial steps in network security assessment. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Testers perform the target system scan using various tools and techniques. It is a key component of ethical hacking. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. The enumeration phase specifically focuses on gathering information about the target system or network. The first penetration testing phase is reconnaissance.
from www.stationx.net
Testers perform the target system scan using various tools and techniques. The enumeration phase specifically focuses on gathering information about the target system or network. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. It is a key component of ethical hacking. They involve probing systems to gather info on open ports ,. Scanning and enumeration are crucial steps in network security assessment. The first penetration testing phase is reconnaissance. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. There are five penetration testing phases: Enumeration in information security is the process of extracting user names, machine names, network resources, and other services.
How to Perform Subdomain Enumeration Top 10 Tools
Pen Testing Scanning And Enumeration They involve probing systems to gather info on open ports ,. They involve probing systems to gather info on open ports ,. The first penetration testing phase is reconnaissance. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. There are five penetration testing phases: Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. It is a key component of ethical hacking. Scanning and enumeration are crucial steps in network security assessment. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. Testers perform the target system scan using various tools and techniques. Let’s take a closer look at the 5 penetration testing phases. The enumeration phase specifically focuses on gathering information about the target system or network.
From www.bitlyft.com
Comparing Vulnerability Scanning and Testing Pen Testing Scanning And Enumeration Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. The enumeration phase specifically focuses on gathering information about the target system or network. There are five penetration testing phases: Let’s take a closer look at the 5 penetration testing phases. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. It is a key. Pen Testing Scanning And Enumeration.
From pentesttools.net
Kenzer Automated Assets Enumeration And Scanning PentestTools Pen Testing Scanning And Enumeration Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Scanning and enumeration are crucial steps in network security assessment. It is a key component of ethical hacking. Let’s take a closer look at the 5 penetration testing phases. Testers perform the target system scan using various tools and techniques. The first. Pen Testing Scanning And Enumeration.
From pentest-tools.com
6 techniques for account enumeration in a test [demo Pen Testing Scanning And Enumeration The first penetration testing phase is reconnaissance. There are five penetration testing phases: They involve probing systems to gather info on open ports ,. Let’s take a closer look at the 5 penetration testing phases. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. It is a key component of ethical hacking. Scanning. Pen Testing Scanning And Enumeration.
From www.youtube.com
Pen Test Pro Easy Scanning & Enumeration Techniques Revealed! Scanning Pen Testing Scanning And Enumeration The enumeration phase specifically focuses on gathering information about the target system or network. The first penetration testing phase is reconnaissance. Scanning and enumeration are crucial steps in network security assessment. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. Testers perform the target system scan using various tools and techniques. Reconnaissance, scanning,. Pen Testing Scanning And Enumeration.
From www.appsealing.com
What is Testing? A Comprehensive guide for PenTesting Pen Testing Scanning And Enumeration Scanning and enumeration are crucial steps in network security assessment. It is a key component of ethical hacking. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. The first penetration testing phase is reconnaissance. Testers perform the target system scan using various tools and techniques. The enumeration phase specifically focuses on. Pen Testing Scanning And Enumeration.
From www.scribd.com
Module 2 Introduction & Pen Test Methodologies Scanning and Service Pen Testing Scanning And Enumeration This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. There are five penetration testing phases: Scanning and enumeration are crucial steps in network security assessment. Testers perform the target system scan using various tools and techniques. Enumeration is extracting a system’s valid usernames, machine names, share. Pen Testing Scanning And Enumeration.
From jerait.co.uk
Pen Test Life Cycle How To Triumph Jera IT Pen Testing Scanning And Enumeration Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. The first penetration testing phase is reconnaissance. The enumeration phase specifically focuses on gathering information about the target system. Pen Testing Scanning And Enumeration.
From techodrom.com
How to Conduct a Successful Test Techodrom Pen Testing Scanning And Enumeration Testers perform the target system scan using various tools and techniques. They involve probing systems to gather info on open ports ,. It is a key component of ethical hacking. There are five penetration testing phases: Let’s take a closer look at the 5 penetration testing phases. The first penetration testing phase is reconnaissance. Enumeration is extracting a system’s valid. Pen Testing Scanning And Enumeration.
From segalgcse.com
Pen Testing Segal GCSE LLP Pen Testing Scanning And Enumeration This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. The enumeration phase specifically focuses on gathering information about the target system or network. It is a key component of ethical hacking. There are five penetration testing phases: Enumeration in information security is the process of extracting. Pen Testing Scanning And Enumeration.
From mechsoftme.com
What Is Testing and How Pen Testing Works? Pen Testing Scanning And Enumeration It is a key component of ethical hacking. The enumeration phase specifically focuses on gathering information about the target system or network. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. They involve probing systems to gather info on open ports ,. Enumeration is extracting a system’s valid usernames, machine names,. Pen Testing Scanning And Enumeration.
From www.meusec.com
Vulnerability Scanning and Enumeration for Pen Testing MeuSec Pen Testing Scanning And Enumeration Scanning and enumeration are crucial steps in network security assessment. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Let’s take a closer look at the 5 penetration testing phases. They involve probing systems to gather info on open ports ,. It is a key component. Pen Testing Scanning And Enumeration.
From cyberguard.ae
Complete Guide To Testing Methodology Pen Testing Scanning And Enumeration Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Scanning and enumeration are crucial steps in network security assessment. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Testers perform the target system scan using various tools and techniques. There are five penetration testing phases: The enumeration phase. Pen Testing Scanning And Enumeration.
From cyvatar.ai
Vulnerability Scanning VS Testing Know the main Pen Testing Scanning And Enumeration It is a key component of ethical hacking. The enumeration phase specifically focuses on gathering information about the target system or network. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. Scanning and enumeration are crucial steps in network security assessment. There are five penetration testing. Pen Testing Scanning And Enumeration.
From www.cybermaxx.com
What is Testing? The Role of Pen Testing in Cybersecurity Pen Testing Scanning And Enumeration They involve probing systems to gather info on open ports ,. Scanning and enumeration are crucial steps in network security assessment. The enumeration phase specifically focuses on gathering information about the target system or network. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. There are five penetration testing phases: Testers. Pen Testing Scanning And Enumeration.
From slideplayer.com
Testing Karen Miller. ppt download Pen Testing Scanning And Enumeration Let’s take a closer look at the 5 penetration testing phases. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. The first penetration testing phase is reconnaissance. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in. Pen Testing Scanning And Enumeration.
From blog.securelayer7.net
What Testing Tool Combines Known Scanning Techniques and Pen Testing Scanning And Enumeration Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. The enumeration phase specifically focuses on gathering information about the target system or network. Scanning and enumeration are crucial steps in network security assessment. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. They involve. Pen Testing Scanning And Enumeration.
From medium.com
Black Box Test Day 1 port scanning and Enumeration Pen Testing Scanning And Enumeration The first penetration testing phase is reconnaissance. Let’s take a closer look at the 5 penetration testing phases. It is a key component of ethical hacking. The enumeration phase specifically focuses on gathering information about the target system or network. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the. Pen Testing Scanning And Enumeration.
From www.slideserve.com
PPT Testing PowerPoint Presentation, free download ID Pen Testing Scanning And Enumeration Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Let’s take a closer look at the 5 penetration testing phases. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. Testers perform the target system scan using various. Pen Testing Scanning And Enumeration.
From www.youtube.com
Scanning and Enumeration Testing Boot camp YouTube Pen Testing Scanning And Enumeration Let’s take a closer look at the 5 penetration testing phases. Scanning and enumeration are crucial steps in network security assessment. The first penetration testing phase is reconnaissance. The enumeration phase specifically focuses on gathering information about the target system or network. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services.. Pen Testing Scanning And Enumeration.
From theqalead.com
The Key Difference Between Vulnerability Scanning And Testing Pen Testing Scanning And Enumeration It is a key component of ethical hacking. Let’s take a closer look at the 5 penetration testing phases. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process.. Pen Testing Scanning And Enumeration.
From itglobal.com
Что такое тестирование на проникновение (pentest), для чего нужен Pen Testing Scanning And Enumeration The enumeration phase specifically focuses on gathering information about the target system or network. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Enumeration is extracting a system’s. Pen Testing Scanning And Enumeration.
From www.cr-t.com
Testing vs Vulnerability Scanning IT Services CRT Utah Pen Testing Scanning And Enumeration This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Scanning and enumeration are crucial steps in network security assessment. Let’s take a closer look at the 5 penetration. Pen Testing Scanning And Enumeration.
From desklib.com
Networking Testing ( Scanning and Enumeration) Pen Testing Scanning And Enumeration The enumeration phase specifically focuses on gathering information about the target system or network. Scanning and enumeration are crucial steps in network security assessment. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. There are five penetration testing phases: Enumeration is extracting a system’s valid usernames,. Pen Testing Scanning And Enumeration.
From pentesterworld.com
Scanning and Enumeration in Testing Pen Testing Scanning And Enumeration Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Testers perform the target system scan using various tools and techniques. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. The first penetration testing phase is reconnaissance. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. They. Pen Testing Scanning And Enumeration.
From plextrac.com
Discovery and Enumeration Pentest Phases A Foundation for Success Pen Testing Scanning And Enumeration There are five penetration testing phases: Let’s take a closer look at the 5 penetration testing phases. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. The enumeration phase specifically focuses on gathering information about the target system or network. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. It is a key component of. Pen Testing Scanning And Enumeration.
From wentzwu.com
CISSP PRACTICE QUESTIONS 20210201 by Wentz Wu, ISSAP, ISSEP, ISSMP Pen Testing Scanning And Enumeration It is a key component of ethical hacking. There are five penetration testing phases: Testers perform the target system scan using various tools and techniques. The first penetration testing phase is reconnaissance. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Enumeration is extracting a system’s. Pen Testing Scanning And Enumeration.
From www.youtube.com
FTP Scanning and Enumeration With Ethical Hacking in Pen Testing Scanning And Enumeration The enumeration phase specifically focuses on gathering information about the target system or network. They involve probing systems to gather info on open ports ,. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. It is a key component of ethical hacking. The first penetration testing. Pen Testing Scanning And Enumeration.
From bluegoatcyber.com
Enumeration Phase in Pen Testing Essentials Explained Blue Goat Cyber Pen Testing Scanning And Enumeration It is a key component of ethical hacking. The first penetration testing phase is reconnaissance. The enumeration phase specifically focuses on gathering information about the target system or network. Scanning and enumeration are crucial steps in network security assessment. Let’s take a closer look at the 5 penetration testing phases. They involve probing systems to gather info on open ports. Pen Testing Scanning And Enumeration.
From www.techtarget.com
Pen testing guide Types, steps, methodologies and frameworks TechTarget Pen Testing Scanning And Enumeration Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. It is a key component of ethical hacking. There are five penetration testing phases: The enumeration phase specifically focuses on gathering information about the target system or network. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. They involve. Pen Testing Scanning And Enumeration.
From www.scribd.com
EAGLE GUIBased Testing Tool For Scanning and Enumeration PDF Pen Testing Scanning And Enumeration The first penetration testing phase is reconnaissance. Scanning and enumeration are crucial steps in network security assessment. There are five penetration testing phases: It is a key component of ethical hacking. Testers perform the target system scan using various tools and techniques. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps. Pen Testing Scanning And Enumeration.
From www.meusec.com
Vulnerability Scanning and Enumeration for Pen Testing MeuSec Pen Testing Scanning And Enumeration They involve probing systems to gather info on open ports ,. Testers perform the target system scan using various tools and techniques. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. There are five penetration testing phases: This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Scanning and. Pen Testing Scanning And Enumeration.
From avord.co.uk
Understanding the Testing Process and how to conduct a test Pen Testing Scanning And Enumeration There are five penetration testing phases: Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Let’s take a closer look at the 5 penetration testing phases. It is a key component of ethical hacking. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further. Pen Testing Scanning And Enumeration.
From www.youtube.com
Testing 12 WPScan WordPress Scanning For Pen Testing Scanning And Enumeration Testers perform the target system scan using various tools and techniques. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. They involve probing systems to gather info on. Pen Testing Scanning And Enumeration.
From www.stationx.net
How to Perform Subdomain Enumeration Top 10 Tools Pen Testing Scanning And Enumeration It is a key component of ethical hacking. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. Enumeration is extracting a system’s valid usernames, machine names, share names, directory names, and other information. Reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. The enumeration phase specifically focuses on gathering information about the target. Pen Testing Scanning And Enumeration.
From dokumen.tips
(PDF) Advanced Testing Make The Difference · 20191121 Pen Testing Scanning And Enumeration There are five penetration testing phases: It is a key component of ethical hacking. Enumeration in information security is the process of extracting user names, machine names, network resources, and other services. This information plays a critical role in understanding the target’s architecture, identifying potential vulnerabilities, and planning further steps in the penetration testing process. Testers perform the target system. Pen Testing Scanning And Enumeration.