Binding Request Stun . This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. The client application sends a binding request to the stun server and the server responds with the public ip address and host of.
from adalkiran.github.io
After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the.
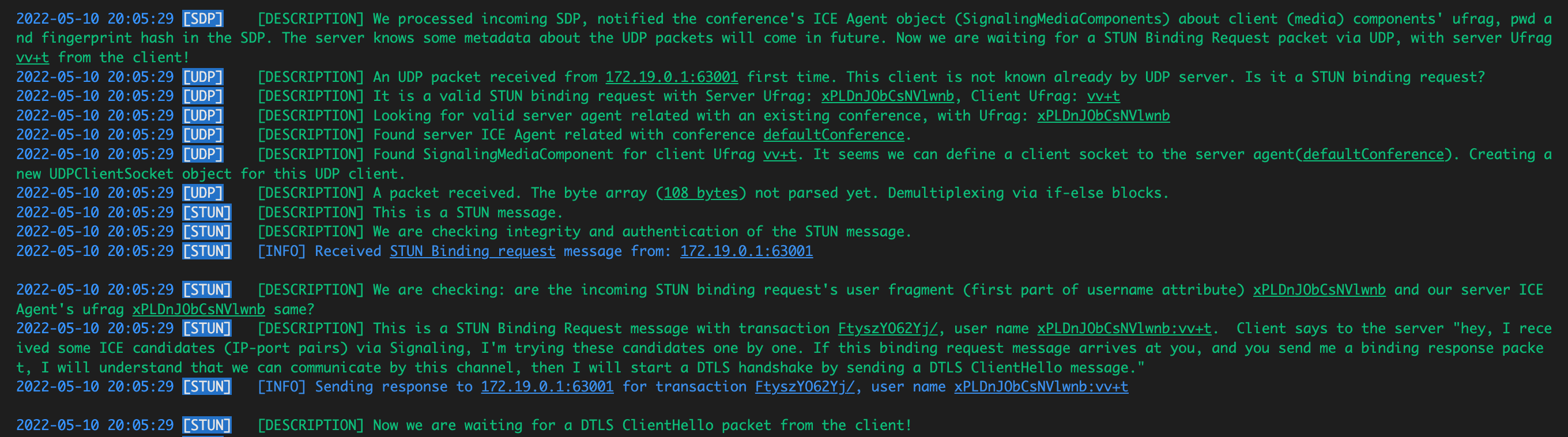
STUN BINDING REQUEST FROM CLIENT RTC Nuts and Bolts
Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client.
From blog.csdn.net
NAT,NAPT,STUN详解_stun和nat区别CSDN博客 Binding Request Stun After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The stun binding request is used to discover the presence of a nat, and. Binding Request Stun.
From www.netmanias.com
NAT Behavior Discovery Using STUN (RFC 5780) NETMANIAS Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. After receiving binding. Binding Request Stun.
From adalkiran.github.io
STUN BINDING REQUEST FROM CLIENT RTC Nuts and Bolts Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. After. Binding Request Stun.
From adalkiran.github.io
STUN BINDING REQUEST FROM CLIENT RTC Nuts and Bolts Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The. Binding Request Stun.
From blog.csdn.net
mediasoup Lite ICE实现说明_mediasoup iceCSDN博客 Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The client application sends a binding request to the stun server and the server. Binding Request Stun.
From www.ppmy.cn
mediasoup Lite ICE实现说明 Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. When used in request/response transactions, the binding method can be used to determine the particular binding a. Binding Request Stun.
From github.com
Stun binding request timeout · Issue 957 · coturn/coturn · GitHub Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The stun binding request is used to discover the presence of a nat, and to discover the public ip. Binding Request Stun.
From www.slideserve.com
PPT STUN Simple Traversal of UDP Through NATs PowerPoint Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The stun binding request is used to discover the presence of a nat, and. Binding Request Stun.
From zhuanlan.zhihu.com
SRS4.0源代码分析之RTC推流端处理 知乎 Binding Request Stun After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. The stun binding request is used to discover the presence of a nat,. Binding Request Stun.
From github.com
Stun binding request timeout · Issue 957 · coturn/coturn · GitHub Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. The client application. Binding Request Stun.
From blog.csdn.net
ICE之STUN协议Binding RequestCSDN博客 Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. When used in request/response transactions, the binding method can be used to determine the particular binding a nat. Binding Request Stun.
From www.unitedworldtelecom.com
What is a STUN Server? United World Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. The client application sends a binding request to the stun server and the server responds with the public ip address. Binding Request Stun.
From cway.cisco.com
User guide — Collaboration Solutions Analyzer 1.0 documentation Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. When used. Binding Request Stun.
From educatedguesswork.org
How NATs Work, Part II NAT types and STUN Binding Request Stun The client application sends a binding request to the stun server and the server responds with the public ip address and host of. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the.. Binding Request Stun.
From anyconnect.com
STUN, TURN, and ICE NAT Traversal Protocols AnyConnect Binding Request Stun If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. The stun binding request is used to discover the presence of a nat, and to discover the public. Binding Request Stun.
From cway.cisco.com
User guide — Collaboration Solutions Analyzer 1.0 documentation Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. If a simple traversal of udp through nat (stun) binding request message. Binding Request Stun.
From www.researchgate.net
4 STUN binding message Download Scientific Diagram Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The. Binding Request Stun.
From zhuanlan.zhihu.com
RTC移动端多网卡(安卓智能加速)卡顿问题 知乎 Binding Request Stun The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by. Binding Request Stun.
From blog.csdn.net
ICE之STUN协议Binding RequestCSDN博客 Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has. Binding Request Stun.
From nordvpn.com
Reaching beyond 1Gbps How we achieved NAT traversal with vanilla Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The client application sends a binding request to the stun server and the server responds with the public ip address. Binding Request Stun.
From www.slideshare.net
NAT binding with STUN Binding Request Stun The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and. Binding Request Stun.
From www.h3c.com
Support 24STUN configuration H3C Binding Request Stun If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding. Binding Request Stun.
From www.slideserve.com
PPT STUN, TURN and ICE PowerPoint Presentation, free download ID Binding Request Stun After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are.. Binding Request Stun.
From blog.csdn.net
mediasoup Lite ICE实现说明_mediasoup iceCSDN博客 Binding Request Stun This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates. Binding Request Stun.
From blog.csdn.net
RTCSTUN协议详解_stun webrtc_zyl_『码农修仙』的博客CSDN博客 Binding Request Stun If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The. Binding Request Stun.
From www.slideshare.net
NAT binding with STUN Binding Request Stun The client application sends a binding request to the stun server and the server responds with the public ip address and host of. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. This. Binding Request Stun.
From www.slideshare.net
NAT binding with STUN Binding Request Stun The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends. Binding Request Stun.
From github.com
Stun binding request timeout · Issue 957 · coturn/coturn · GitHub Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends. Binding Request Stun.
From blog.csdn.net
mediasoup Lite ICE实现说明_mediasoup iceCSDN博客 Binding Request Stun The client application sends a binding request to the stun server and the server responds with the public ip address and host of. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The stun binding request is used to discover the presence of a nat, and to. Binding Request Stun.
From zhuanlan.zhihu.com
前端RTC 攻略(五) NAT 穿越与 ICE 知乎 Binding Request Stun The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client.. Binding Request Stun.
From blog.csdn.net
ICE之STUN协议Binding_stun bindingCSDN博客 Binding Request Stun The client application sends a binding request to the stun server and the server responds with the public ip address and host of. After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. If a simple traversal of udp through nat (stun) binding request message is. Binding Request Stun.
From blog.disects.com
Security Unplugged !!! VoIP STUN Request/Response Packet Structure Binding Request Stun After receiving binding requests, the stun server obtains the source ip addresses and port numbers and sends a binding response to each stun client. The client application sends a binding request to the stun server and the server responds with the public ip address and host of. The stun binding request is used to discover the presence of a nat,. Binding Request Stun.
From www.pianshen.com
ICE之STUN协议Binding Request 程序员大本营 Binding Request Stun When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated to a. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. This section specifies the processing of simple traversal of udp through nat (stun) binding request messages by the. The client application. Binding Request Stun.
From wdd.js.org
STUN协议笔记 洞香春 Binding Request Stun The client application sends a binding request to the stun server and the server responds with the public ip address and host of. The validation procedures for simple traversal of udp through nat (stun) binding request messages as specified in. When used in request/response transactions, the binding method can be used to determine the particular binding a nat has allocated. Binding Request Stun.
From blog.csdn.net
ICE之STUN协议Binding RequestCSDN博客 Binding Request Stun The stun binding request is used to discover the presence of a nat, and to discover the public ip address and port mappings generated by the. If a simple traversal of udp through nat (stun) binding request message is received before the remote candidates are. This section specifies the processing of simple traversal of udp through nat (stun) binding request. Binding Request Stun.