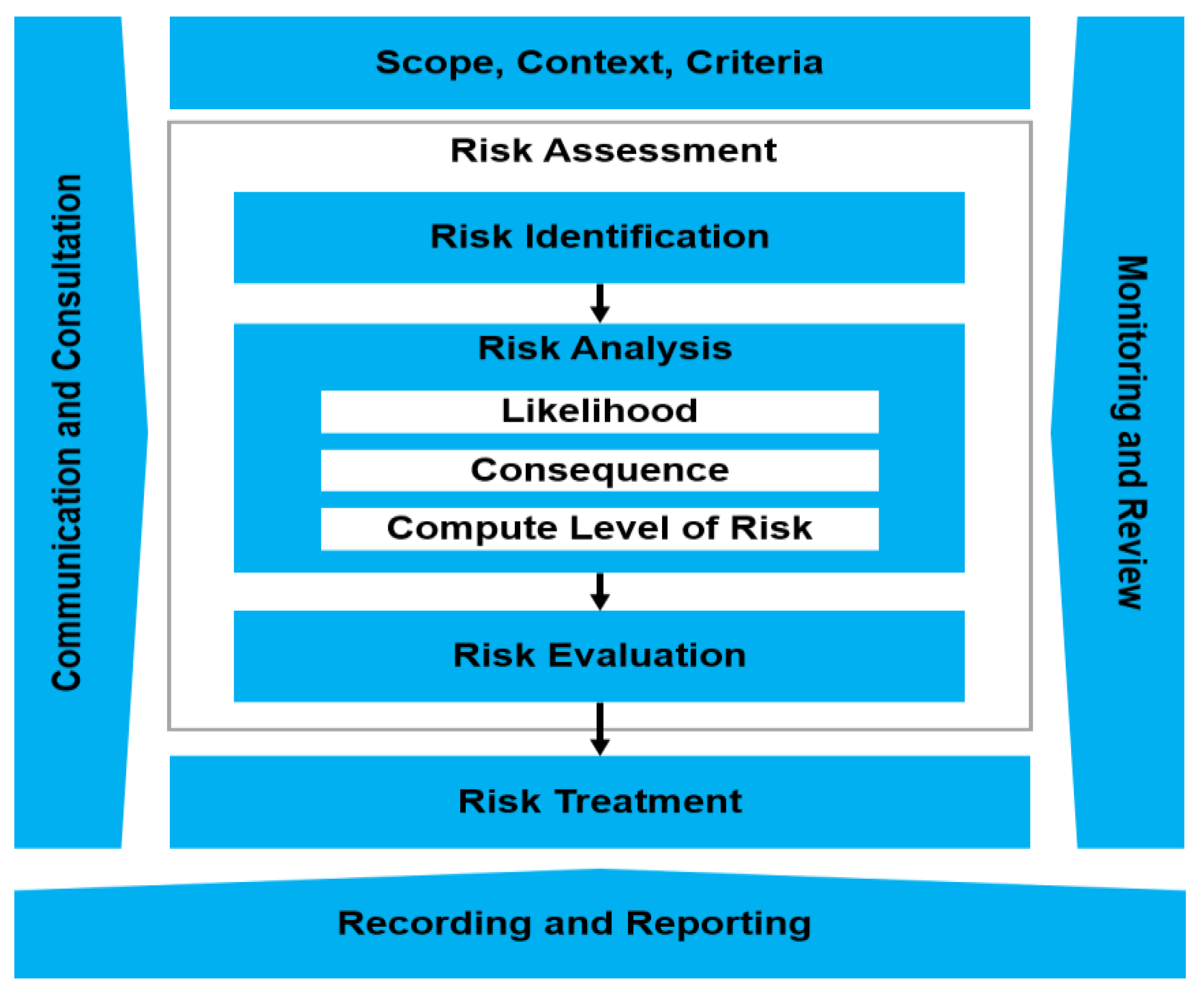
Security & Risk Management . Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Control selection, implementation, and assessment; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Structured, and flexible process for managing security and privacy risk that includes information security categorization;
from www.mdpi.com
Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Structured, and flexible process for managing security and privacy risk that includes information security categorization;
Risks Free FullText ContextBased and Adaptive Cybersecurity Risk
Security & Risk Management Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Structured, and flexible process for managing security and privacy risk that includes information security categorization; The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Control selection, implementation, and assessment;
From safety4sea.com
ISM Code as the key driver in addressing cyber risk SAFETY4SEA Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Control selection, implementation, and assessment;. Security & Risk Management.
From sprinto.com
What is Cybersecurity Risk Management? Sprinto Security & Risk Management Control selection, implementation, and assessment; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible. Security & Risk Management.
From delff.co.uk
Risk management DELFF Security & Risk Management The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Information security risk management identifies. Security & Risk Management.
From www.projectmanager.com
IT Risk Management Strategies and Best Practices ProjectManager Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Control selection, implementation, and assessment; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks. Security & Risk Management.
From digisoter.com
The riskbased approach to cybersecurity moving away from the check Security & Risk Management Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Control selection, implementation,. Security & Risk Management.
From ar.inspiredpencil.com
Risk Management Security & Risk Management Control selection, implementation, and assessment; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible process for managing security and privacy risk that includes information security categorization; The risk. Security & Risk Management.
From www.halkynconsulting.co.uk
Security Risk Response Options Halkyn Security Blog Security & Risk Management The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Information security risk management. Security & Risk Management.
From securityboulevard.com
Realizing an information security risk management framework Security Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Structured, and flexible. Security & Risk Management.
From www.alpinesecurity.com
How to Perform a Cybersecurity Risk Assessment A StepbyStep Guide Security & Risk Management Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Structured,. Security & Risk Management.
From www.theirmindia.org
Relationship between Governance, Risk Compliance (GRC), and Enterprise Security & Risk Management Control selection, implementation, and assessment; The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Learn how to identify and minimize potential risks or threats to. Security & Risk Management.
From www.cybersecurity360.it
Risk Management un framework dedicato alla cyber security Cyber Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and. Security & Risk Management.
From www.threatanalysis.com
SECURITY RISK MANAGEMENT Threat Analysis Group Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Control selection, implementation, and assessment;. Security & Risk Management.
From seguro.ltd
Risk management in information security Seguro Cyber Security Security & Risk Management The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the. Security & Risk Management.
From www.intellisoft.com.sg
Managing Cyber Security Risks (WSQ) Course in Singapore at Intellisoft Security & Risk Management The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Control selection, implementation, and assessment; Information security. Security & Risk Management.
From www.smatica.com
ISO 27005 Information Security Risk Management SMATICA LLC Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. The risk management framework (rmf) provides a process that integrates security, privacy,. Security & Risk Management.
From securityboulevard.com
Risk Register Examples for Cybersecurity Leaders Security Boulevard Security & Risk Management Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called. Security & Risk Management.
From blog.radware.com
Risk Management from the CISO Perspective Radware Blog Security & Risk Management Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber. Security & Risk Management.
From www.csoonline.com
PwC UK partners with ReversingLabs to bring software supply chain Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Control selection, implementation, and assessment; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Cybersecurity risk management is the process of. Security & Risk Management.
From oversitesentry.com
Risk management Failed Us! Explaining Security Security & Risk Management Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Structured, and flexible process for managing security and privacy. Security & Risk Management.
From www.protectuk.police.uk
Risk management process ProtectUK Security & Risk Management Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Structured, and flexible process for managing security and privacy risk that includes information security categorization;. Security & Risk Management.
From bizzdesign.com
Risk Security Management Bizzdesign Security & Risk Management Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Control selection, implementation, and assessment; Learn how to identify and minimize. Security & Risk Management.
From australianwomeninsecuritynetwork.blogspot.com
Australian Women in Security Network Cyber Security Risk Management in Security & Risk Management Control selection, implementation, and assessment; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply.. Security & Risk Management.
From www.codubconsulting.com
Security Risk Management Consultant Codub Security & Risk Management Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing,. Security & Risk Management.
From www.researchhq.net
Research HQ Risk Management Framework (RMF) An Overview Research HQ Security & Risk Management Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Control selection, implementation, and assessment; The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Cybersecurity risk management is the process of. Security & Risk Management.
From opsecsolutions.net
Why Security Risk Management is Vital in Event Planning Security & Risk Management Control selection, implementation, and assessment; The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cybersecurity risk management is the. Security & Risk Management.
From www.bankinfosecurity.com
Intro to Security Risk Managementinar. BankInfoSecurity Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Learn how to identify and minimize potential risks or threats to networked. Security & Risk Management.
From www.lepuchin.com
Understanding Core Security Goals and Basic Risk Concepts Puchin Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Control selection, implementation, and assessment; Cyber risk. Security & Risk Management.
From cassie-jolpbloghobbs.blogspot.com
The Risk Management Technique That Is Used to Prevent Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Information security risk management identifies. Security & Risk Management.
From uniserveit.com
Conducting An Effective IT Security Risk Assessment Security & Risk Management Control selection, implementation, and assessment; Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Cybersecurity risk management is the process of. Security & Risk Management.
From www.intercloud.ro
Security & Risk Assessment Security & Risk Management The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Control selection, implementation, and assessment;. Security & Risk Management.
From www.mdpi.com
Risks Free FullText ContextBased and Adaptive Cybersecurity Risk Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Structured, and flexible process for managing. Security & Risk Management.
From www.securitymagazine.com
Workforce risk reaches five year high reveals International SOS Risk Security & Risk Management Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Control selection, implementation, and assessment; The risk. Security & Risk Management.
From aperionglobalinstitute.com
How to Develop Effective Risk Management Techniques in Entertainment Security & Risk Management Structured, and flexible process for managing security and privacy risk that includes information security categorization; The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Information security risk management identifies and prioritizes potential threats, assesses their likelihood and impact,. Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures,. Security & Risk Management.
From matrix247.com
Cyber Security to Manage Risk Matrix247 Security & Risk Management Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Cyber risk management, also called cybersecurity risk management, is the process of identifying, prioritizing, managing and monitoring risks to. Control selection, implementation, and assessment; Learn how to identify. Security & Risk Management.
From blog.lnsresearch.com
Operational Risk Management Gets Smart with AI Security & Risk Management Control selection, implementation, and assessment; Cybersecurity risk management is the process of identifying an organization's digital assets, reviewing existing security measures, and. Structured, and flexible process for managing security and privacy risk that includes information security categorization; Learn how to identify and minimize potential risks or threats to networked systems, data, and users with cisco's risk management solutions. The risk. Security & Risk Management.