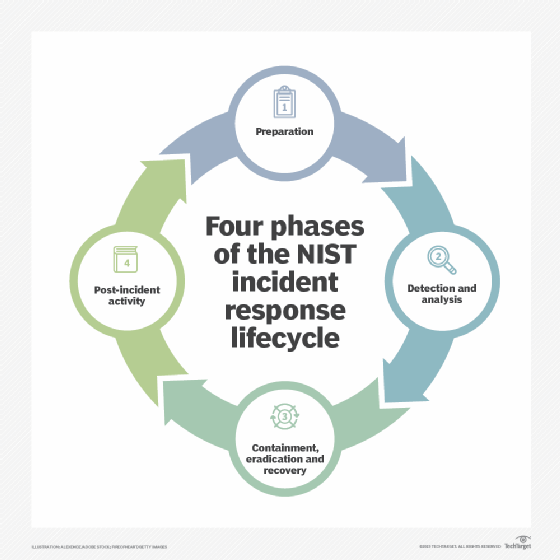
What Is The Best First Step In Responding To A Compromised System . This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. What actions you’ve taken to remedy the situation; Discovering a compromised host can be stressful but first and foremost, remember not to panic: Begin by evaluating the scope and nature of the data breach. When you discover that your company is under attack, there are seven essential steps you should take. What steps you are taking. It is important to follow. These eight steps are the foundation. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. [describe how you are responding to the data breach, including: The office of information security. Follow these steps to effectively respond to a data breach: To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. The goals are to both stop the attack and mitigate its effects.
from searchsecurity.techtarget.com
Discovering a compromised host can be stressful but first and foremost, remember not to panic: These eight steps are the foundation. [describe how you are responding to the data breach, including: When you discover that your company is under attack, there are seven essential steps you should take. Follow these steps to effectively respond to a data breach: To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. What actions you’ve taken to remedy the situation; The goals are to both stop the attack and mitigate its effects. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. What steps you are taking.
Building an incident response framework for your enterprise
What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. What steps you are taking. What actions you’ve taken to remedy the situation; When you discover that your company is under attack, there are seven essential steps you should take. Discovering a compromised host can be stressful but first and foremost, remember not to panic: These eight steps are the foundation. [describe how you are responding to the data breach, including: Begin by evaluating the scope and nature of the data breach. It is important to follow. The office of information security. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. Follow these steps to effectively respond to a data breach: When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. The goals are to both stop the attack and mitigate its effects.
From securityboulevard.com
Your Security Guide to Insider Threats Detection, Best Practices What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. Follow these steps to effectively respond to a data breach: What actions you’ve taken to remedy the situation; The office of information security. It is important to follow. Discovering a compromised host can be stressful but first and foremost, remember not to panic: When breaches happen, organizational leaders. What Is The Best First Step In Responding To A Compromised System.
From blogs.windows.com
Trusted Cyber Physical Systems looks to protect your critical What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. It is important to follow. When you discover that your company is under attack, there are seven essential steps you should take. What steps you are taking. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. These eight steps are. What Is The Best First Step In Responding To A Compromised System.
From www.nyu.edu
IT Security Information Breach Notification Policy What Is The Best First Step In Responding To A Compromised System Begin by evaluating the scope and nature of the data breach. The goals are to both stop the attack and mitigate its effects. Discovering a compromised host can be stressful but first and foremost, remember not to panic: The office of information security. [describe how you are responding to the data breach, including: What actions you’ve taken to remedy the. What Is The Best First Step In Responding To A Compromised System.
From www.centerconsulting.org
Leadership Skills How to Respond (Not React) to Conflict — The Center What Is The Best First Step In Responding To A Compromised System This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. [describe how you are responding to the data breach, including: What actions you’ve taken to remedy the situation; These eight steps are the foundation. Discovering. What Is The Best First Step In Responding To A Compromised System.
From www.stylesrant.org
Responding to a Compromised site Steps to Recover from a Cyber What Is The Best First Step In Responding To A Compromised System This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. It is important to follow. These eight steps are the foundation. Discovering a compromised host can be stressful but first and foremost, remember not to panic: The goals are to both stop the attack and mitigate its effects. Follow these steps to effectively. What Is The Best First Step In Responding To A Compromised System.
From tipsmake.com
Determine whether the system is compromised What Is The Best First Step In Responding To A Compromised System When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. Begin by evaluating the scope and nature of the data breach. The goals are to both stop the. What Is The Best First Step In Responding To A Compromised System.
From www.clouddefense.ai
What Is Spyware? Definition, Types, And Protection What Is The Best First Step In Responding To A Compromised System Follow these steps to effectively respond to a data breach: What actions you’ve taken to remedy the situation; The office of information security. [describe how you are responding to the data breach, including: When you discover that your company is under attack, there are seven essential steps you should take. This incident response cheat sheet is for performing live analysis. What Is The Best First Step In Responding To A Compromised System.
From rezonate.io
Best Practices to Detect and Respond to a Compromised Identity Rezonate What Is The Best First Step In Responding To A Compromised System Begin by evaluating the scope and nature of the data breach. The office of information security. When you discover that your company is under attack, there are seven essential steps you should take. What steps you are taking. [describe how you are responding to the data breach, including: This incident response cheat sheet is for performing live analysis on a. What Is The Best First Step In Responding To A Compromised System.
From www.jdsupra.com
OCR Publishes Checklist and Infographic for Cyber Attack Response What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. What actions you’ve taken to remedy the situation; What steps you are taking. Discovering a compromised host can be stressful but first and foremost, remember not to panic: These eight steps. What Is The Best First Step In Responding To A Compromised System.
From www.slideserve.com
PPT 2013 PCI Data Security Awareness Training PowerPoint Presentation What Is The Best First Step In Responding To A Compromised System It is important to follow. To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. [describe how you are responding to the data breach, including: When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. Begin by evaluating. What Is The Best First Step In Responding To A Compromised System.
From www.vrogue.co
Understanding Cyber Incident Response Phases A Guide vrogue.co What Is The Best First Step In Responding To A Compromised System When you discover that your company is under attack, there are seven essential steps you should take. [describe how you are responding to the data breach, including: When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. Follow these steps to effectively respond to a data breach: The goals are to both. What Is The Best First Step In Responding To A Compromised System.
From www.dreamstime.com
Cybersecurity Vulnerability, Data Breach, Illegal Connection What Is The Best First Step In Responding To A Compromised System These eight steps are the foundation. Begin by evaluating the scope and nature of the data breach. The office of information security. [describe how you are responding to the data breach, including: Follow these steps to effectively respond to a data breach: When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation.. What Is The Best First Step In Responding To A Compromised System.
From searchsecurity.techtarget.com
Building an incident response framework for your enterprise What Is The Best First Step In Responding To A Compromised System It is important to follow. Follow these steps to effectively respond to a data breach: The goals are to both stop the attack and mitigate its effects. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. What actions you’ve taken to remedy the situation; These eight steps are the foundation. When. What Is The Best First Step In Responding To A Compromised System.
From www.codewithc.com
Automating Incident Response With Python A Proactive Approach To What Is The Best First Step In Responding To A Compromised System It is important to follow. When you discover that your company is under attack, there are seven essential steps you should take. What actions you’ve taken to remedy the situation; When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. These eight steps are the foundation. Begin by evaluating the scope and. What Is The Best First Step In Responding To A Compromised System.
From www.onlinesalesguidetip.com
How to Create a Great RFP Response Process Online Sales Guide Tips What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. These eight steps are the foundation. Discovering a compromised host can be stressful but first and foremost, remember not to panic: It is important to follow. What steps you are taking. [describe how you are responding to the data breach, including: When you discover that your company is. What Is The Best First Step In Responding To A Compromised System.
From www.socinvestigation.com
What Is A Compromise Assessment And When Do You Need One? Security What Is The Best First Step In Responding To A Compromised System The office of information security. Discovering a compromised host can be stressful but first and foremost, remember not to panic: When you discover that your company is under attack, there are seven essential steps you should take. What actions you’ve taken to remedy the situation; Follow these steps to effectively respond to a data breach: This incident response cheat sheet. What Is The Best First Step In Responding To A Compromised System.
From cipherssecurity.com
What Is Information Warfare? Explanation And Types What Is The Best First Step In Responding To A Compromised System What actions you’ve taken to remedy the situation; [describe how you are responding to the data breach, including: When you discover that your company is under attack, there are seven essential steps you should take. These eight steps are the foundation. The goals are to both stop the attack and mitigate its effects. It is important to follow. Discovering a. What Is The Best First Step In Responding To A Compromised System.
From microage.com
Understanding the 6 Elements of the Incident Response (IR) Process What Is The Best First Step In Responding To A Compromised System What steps you are taking. When you discover that your company is under attack, there are seven essential steps you should take. It is important to follow. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. Follow these steps to effectively respond to a data breach: Discovering a compromised host can. What Is The Best First Step In Responding To A Compromised System.
From www.frontiersin.org
Frontiers Handling UserOriented CyberAttacks STRIM, a UserBased What Is The Best First Step In Responding To A Compromised System It is important to follow. These eight steps are the foundation. What steps you are taking. The goals are to both stop the attack and mitigate its effects. When you discover that your company is under attack, there are seven essential steps you should take. Discovering a compromised host can be stressful but first and foremost, remember not to panic:. What Is The Best First Step In Responding To A Compromised System.
From blog.qualys.com
The Convergence of Endpoint Protection with Detection & Response What Is The Best First Step In Responding To A Compromised System To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. These eight steps are the foundation. The office of information security. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. Follow these steps to effectively respond to. What Is The Best First Step In Responding To A Compromised System.
From www.youtube.com
Step Response of a System YouTube What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. Begin by evaluating the scope and nature of the data breach. What actions you’ve taken to remedy the situation; [describe how you are responding to the data breach, including: To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before. What Is The Best First Step In Responding To A Compromised System.
From www.researchgate.net
Data breach response steps. Download Scientific Diagram What Is The Best First Step In Responding To A Compromised System Discovering a compromised host can be stressful but first and foremost, remember not to panic: Follow these steps to effectively respond to a data breach: When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised.. What Is The Best First Step In Responding To A Compromised System.
From www.slideteam.net
Cyber Security Incident Response Process Flow Chart Incident Response What Is The Best First Step In Responding To A Compromised System To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. What actions you’ve taken to remedy the situation; What steps you are taking. The goals are to both stop the attack and mitigate its effects. This incident response cheat sheet is for performing live analysis on. What Is The Best First Step In Responding To A Compromised System.
From www.bipcybersec.com
Digital Footprint know it to avoid cyber risks BIP CyberSec What Is The Best First Step In Responding To A Compromised System [describe how you are responding to the data breach, including: The office of information security. To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. These eight steps are the foundation. Discovering a compromised host can be stressful but first and foremost, remember not to panic:. What Is The Best First Step In Responding To A Compromised System.
From www.grcilaw.com
How to handle data breaches according to the GDPR GRCI Law Blog What Is The Best First Step In Responding To A Compromised System To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before a data breach even occurs. The office of information security. It is important to follow. [describe how you are responding to the data breach, including: These eight steps are the foundation. When breaches happen, organizational leaders are expected to act fast. What Is The Best First Step In Responding To A Compromised System.
From cybersecurity.att.com
Building an Effective Incident Response Framework Infographic LevelBlue What Is The Best First Step In Responding To A Compromised System Discovering a compromised host can be stressful but first and foremost, remember not to panic: These eight steps are the foundation. What steps you are taking. The office of information security. Follow these steps to effectively respond to a data breach: When you discover that your company is under attack, there are seven essential steps you should take. When breaches. What Is The Best First Step In Responding To A Compromised System.
From www.lepide.com
Top 10 Signs That Your System Has Been Compromised What Is The Best First Step In Responding To A Compromised System These eight steps are the foundation. What steps you are taking. [describe how you are responding to the data breach, including: When you discover that your company is under attack, there are seven essential steps you should take. Discovering a compromised host can be stressful but first and foremost, remember not to panic: What actions you’ve taken to remedy the. What Is The Best First Step In Responding To A Compromised System.
From slideplayer.com
Office Centegy Building ppt download What Is The Best First Step In Responding To A Compromised System The goals are to both stop the attack and mitigate its effects. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. Begin by evaluating the scope and nature of the data breach. The office of information security. These eight steps are the foundation. To minimize the damage of a potential breach, your. What Is The Best First Step In Responding To A Compromised System.
From www.freepik.com
Premium AI Image An AI system autonomously responding to a What Is The Best First Step In Responding To A Compromised System What actions you’ve taken to remedy the situation; What steps you are taking. Follow these steps to effectively respond to a data breach: Begin by evaluating the scope and nature of the data breach. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. Discovering a compromised host can be stressful but. What Is The Best First Step In Responding To A Compromised System.
From www.linode.com
Recovering from a System Compromise Linode Docs What Is The Best First Step In Responding To A Compromised System These eight steps are the foundation. When breaches happen, organizational leaders are expected to act fast to preserve evidence and support an efficient investigation. What steps you are taking. What actions you’ve taken to remedy the situation; Begin by evaluating the scope and nature of the data breach. To minimize the damage of a potential breach, your organization needs to. What Is The Best First Step In Responding To A Compromised System.
From asana.com
What is Incident Management? Steps, Tips, and Best Practices • Asana What Is The Best First Step In Responding To A Compromised System These eight steps are the foundation. It is important to follow. Follow these steps to effectively respond to a data breach: Discovering a compromised host can be stressful but first and foremost, remember not to panic: What steps you are taking. To minimize the damage of a potential breach, your organization needs to define steps for response and investigation before. What Is The Best First Step In Responding To A Compromised System.
From www.firehouse.com
The RESPOND System for Emergency Operations Firehouse What Is The Best First Step In Responding To A Compromised System What actions you’ve taken to remedy the situation; The office of information security. [describe how you are responding to the data breach, including: Discovering a compromised host can be stressful but first and foremost, remember not to panic: It is important to follow. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised.. What Is The Best First Step In Responding To A Compromised System.
From www.thesecmaster.com
things to check when a system gets compromised What Is The Best First Step In Responding To A Compromised System What steps you are taking. Begin by evaluating the scope and nature of the data breach. These eight steps are the foundation. It is important to follow. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. The goals are to both stop the attack and mitigate its effects. When breaches happen, organizational. What Is The Best First Step In Responding To A Compromised System.
From brooksitservices.com
How To Tell Your System Has Been Compromised Through A Hack Brooks IT What Is The Best First Step In Responding To A Compromised System Begin by evaluating the scope and nature of the data breach. The goals are to both stop the attack and mitigate its effects. What steps you are taking. It is important to follow. This incident response cheat sheet is for performing live analysis on a system you suspect is compromised. When breaches happen, organizational leaders are expected to act fast. What Is The Best First Step In Responding To A Compromised System.
From lesleyjhandyo.blob.core.windows.net
Threat Hunting Windows Process at lesleyjhandyo blog What Is The Best First Step In Responding To A Compromised System Discovering a compromised host can be stressful but first and foremost, remember not to panic: It is important to follow. The goals are to both stop the attack and mitigate its effects. Follow these steps to effectively respond to a data breach: What steps you are taking. The office of information security. This incident response cheat sheet is for performing. What Is The Best First Step In Responding To A Compromised System.