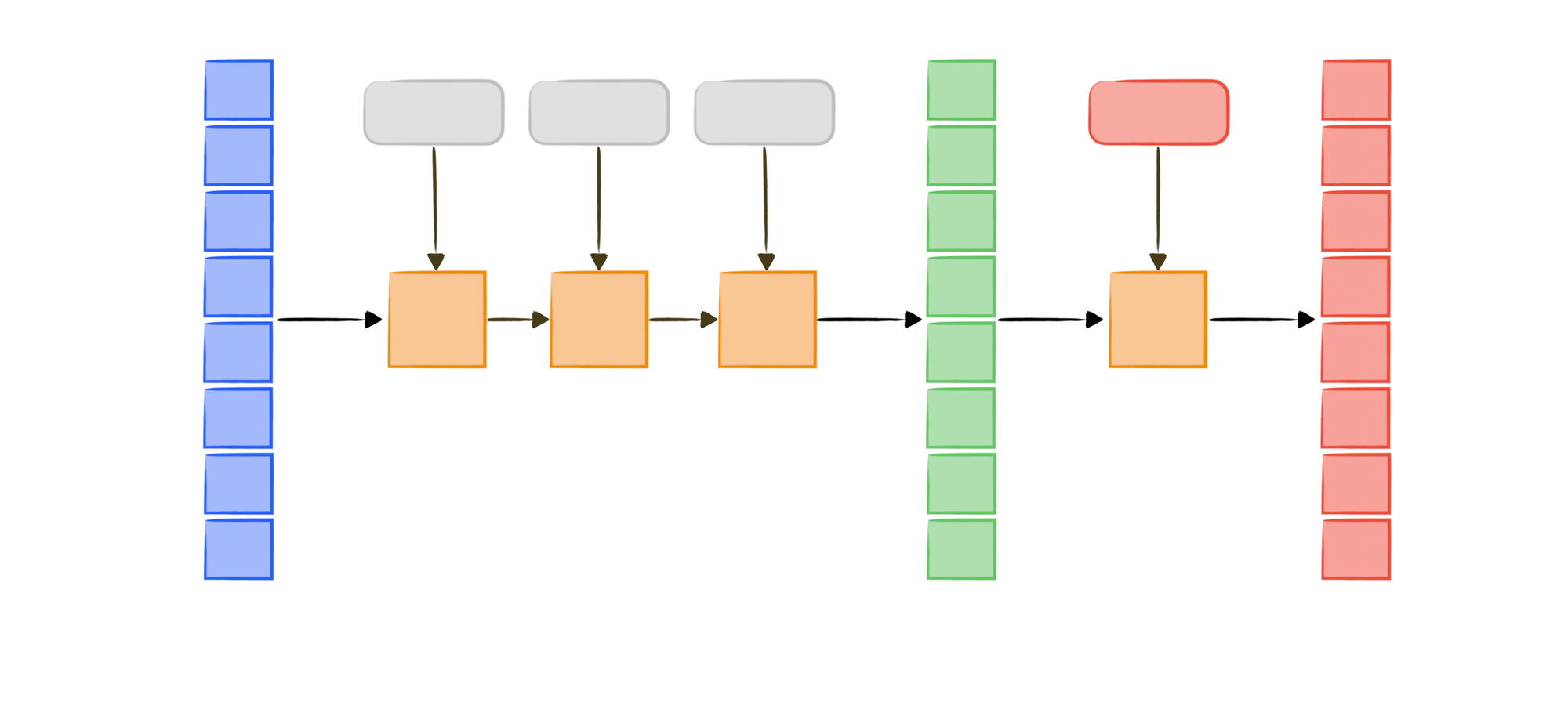
Length Extension Attack In Hash . A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. It takes advantage of the predictable nature of. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that.
from www.aspires.cc
An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. It takes advantage of the predictable nature of. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's.
An Introduction to SHA256 Hash Extension Attack
Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. It takes advantage of the predictable nature of. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The length extension attack is a sophisticated cryptographic exploit that targets hash functions.
From www.studocu.com
Crypto Hash Length Ext Hash Length Extension Attack Lab Copyright Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine. Length Extension Attack In Hash.
From d0nut.medium.com
Week 17 Hash Length Extensions. This week I spent a little bit of time Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. It takes advantage of the predictable nature of. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. The length extension attack is a sophisticated cryptographic exploit that. Length Extension Attack In Hash.
From slides.com
Hash Length Extension Attacks Length Extension Attack In Hash The length extension attack is a sophisticated cryptographic exploit that targets hash functions. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The key to understanding hash extension attacks is. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. It takes advantage of the predictable nature of. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that.. Length Extension Attack In Hash.
From danq.me
Length Extension Attack Demonstration Dan Q Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. Imagine a server which is signing some. Length Extension Attack In Hash.
From www.youtube.com
Mastering Length Extension Attacks Exploiting Hash Functions YouTube Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the. Length Extension Attack In Hash.
From www.slideserve.com
PPT Cryptography Crash Course PowerPoint Presentation, free download Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the. Length Extension Attack In Hash.
From www.studocu.com
Hash Length Extension Attack Lab Lab 10 Hash length extension Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the. Length Extension Attack In Hash.
From slowmist.medium.com
The Hidden Risks of Hash Functions Length Extension Attacks and Server Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. It takes advantage of the predictable nature of. The key to understanding hash extension attacks is to understand that the hash. Length Extension Attack In Hash.
From aftermath.digital
MerkleDamgård Length Extensions and Keccak256 Aftermath.digital Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server which is signing some data by appending a secret to some known clear text data. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Imagine a server. Length Extension Attack In Hash.
From ciphersaw.me
Hash Length Extension Attack(哈希长度扩展攻击) Secrypt Agency Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. Imagine a server which is signing some data by appending a secret to some known clear text data and then. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. It takes advantage of the predictable nature of. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their.. Length Extension Attack In Hash.
From www.aspires.cc
An Introduction to SHA256 Hash Extension Attack Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.
From hyggevv.github.io
hash length extension attacks(hash长度拓展攻击) hey's blog Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. It takes advantage of the predictable nature of. An application is susceptible to a hash length extension attack. Length Extension Attack In Hash.
From www.slideshare.net
Hash length extension attacks PPT Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. A length extension attack is a sophisticated. Length Extension Attack In Hash.
From slideplayer.com
OneWay Hash Functions ppt download Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a. Length Extension Attack In Hash.
From studylib.net
Hash Length Extension Attacks Explained Length Extension Attack In Hash An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. The key to understanding hash extension attacks. Length Extension Attack In Hash.
From github.com
GitHub sTorro/HashPumpWIN32 A tool to exploit the hash length Length Extension Attack In Hash It takes advantage of the predictable nature of. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with. Length Extension Attack In Hash.
From slideplayer.com
OneWay Hash Functions ppt download Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. It takes advantage of the predictable nature of. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. The length extension attack is a sophisticated cryptographic exploit that. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. An application is susceptible to. Length Extension Attack In Hash.
From ciphersaw.me
Hash Length Extension Attack(哈希长度扩展攻击) Secrypt Agency Length Extension Attack In Hash The length extension attack is a sophisticated cryptographic exploit that targets hash functions. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that.. Length Extension Attack In Hash.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free Length Extension Attack In Hash The length extension attack is a sophisticated cryptographic exploit that targets hash functions. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. It takes advantage of the predictable nature of. An application is susceptible to a hash length extension attack if it prepends a secret value to. Length Extension Attack In Hash.
From slides.com
Hash Length Extension Attacks Length Extension Attack In Hash The length extension attack is a sophisticated cryptographic exploit that targets hash functions. The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that.. Length Extension Attack In Hash.
From blog.csdn.net
哈希长度拓展攻击 (hash length extension attacks) 示例与原理CSDN博客 Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. The length extension. Length Extension Attack In Hash.
From medium.com
The Partial Preimage Technique. How to Use Length Extension Attacks For Length Extension Attack In Hash It takes advantage of the predictable nature of. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.
From www.youtube.com
Length Extension Attack YouTube Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.
From muens.io
Hash Function Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it. Length Extension Attack In Hash.
From dzone.com
an SHA1 MAC Using a LengthExtension Attack in Python DZone Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.
From github.com
GitHub ibamba/HashLengthExtensionAttack Implementation of the Length Extension Attack In Hash A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. The length extension attack is a sophisticated cryptographic exploit that targets hash functions. Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. The key to understanding hash extension attacks is. Length Extension Attack In Hash.
From www.studypool.com
SOLUTION Hash length extension attack questions Studypool Length Extension Attack In Hash Imagine a server which is signing some data by appending a secret to some known clear text data and then hashing that. It takes advantage of the predictable nature of. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. The length extension attack is a sophisticated cryptographic exploit that targets hash functions.. Length Extension Attack In Hash.
From ciphersaw.me
Hash Length Extension Attack(哈希长度扩展攻击) Secrypt Agency Length Extension Attack In Hash The key to understanding hash extension attacks is to understand that the hash output isn't just the output of the machine generating the hash, it's. An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the. Length Extension Attack In Hash.