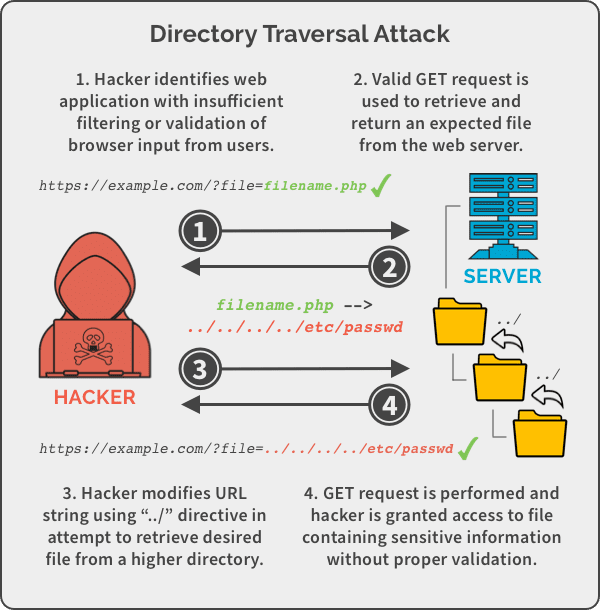
Directory Traversal Examples . Path traversal is also known as directory traversal. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. You will first use a directory traversal attack to hack a vulnerable web server. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. The exploit allows an attacker. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. For instance, an attacker might.
from spanning.com
The exploit allows an attacker. Path traversal is also known as directory traversal. You will first use a directory traversal attack to hack a vulnerable web server. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. For instance, an attacker might.
directorytraversalexample Spanning
Directory Traversal Examples Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. Path traversal is also known as directory traversal. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. The exploit allows an attacker. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. You will first use a directory traversal attack to hack a vulnerable web server. For instance, an attacker might. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files.
From www.ivanglinkin.com
Path (directory) traversal Ivan Glinkin Directory Traversal Examples For instance, an attacker might. The exploit allows an attacker. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. In this lesson, you will. Directory Traversal Examples.
From www.ubikasec.com
How to prevent exploitation of Path Traversal vulnerabilities Directory Traversal Examples For instance, an attacker might. Path traversal is also known as directory traversal. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. The exploit allows an attacker. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. You will first use a. Directory Traversal Examples.
From byte-mind.net
Directory Traversal Qué es y como funciona Byte Mind Directory Traversal Examples The exploit allows an attacker. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. For instance, an attacker might. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. You will first use. Directory Traversal Examples.
From www.comparitech.com
What is a Directory Traversal Attack and How to Prevent it in 2024? Directory Traversal Examples The exploit allows an attacker. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. Examples of. Directory Traversal Examples.
From www.insecure.in
Directory Traversal Attacks, Examples and Prevention Directory Traversal Examples In this lesson, you will learn how directory traversal works and how to mitigate it in your application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. A path traversal attack (also known as directory traversal) aims to access. Directory Traversal Examples.
From www.fity.club
Directory Traversal Directory Traversal Examples An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. The exploit allows an attacker. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method. Directory Traversal Examples.
From null-byte.wonderhowto.com
How to Leverage a Directory Traversal Vulnerability into Code Execution Directory Traversal Examples You will first use a directory traversal attack to hack a vulnerable web server. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. The exploit allows an attacker. In this lesson, you will learn how directory traversal works and. Directory Traversal Examples.
From www.incredigeek.com
Directory Traversal Burp Suite Incredigeek Directory Traversal Examples A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. Path traversal is also known as directory traversal. In a directory traversal attack, also known as path traversal, an. Directory Traversal Examples.
From www.csoonline.com
Directory traversal explained Definition, examples and prevention Directory Traversal Examples The exploit allows an attacker. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. For instance, an attacker might. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. In this lesson, you will. Directory Traversal Examples.
From www.macrometa.com
Traversal Examples Macrometa Directory Traversal Examples An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. In this lesson, you will learn how. Directory Traversal Examples.
From www.fity.club
Directory Traversal Directory Traversal Examples For instance, an attacker might. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. A path traversal attack (also known as directory traversal). Directory Traversal Examples.
From brightsec.com
Directory Traversal Examples, Testing, and Prevention Directory Traversal Examples Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. You will first use a directory traversal attack to hack a vulnerable web server. Path traversal is also known as directory traversal. For instance, an attacker might. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. A path. Directory Traversal Examples.
From cheatography.com
Command Inj, LFI/RFI, and Directory Traversal Cheat Sheet by binca Directory Traversal Examples The exploit allows an attacker. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Examples of directory traversal attacks often involve manipulating url parameters. Directory Traversal Examples.
From brightsec.com
Directory Traversal Attack Reallife Attacks and Code Examples Directory Traversal Examples For instance, an attacker might. You will first use a directory traversal attack to hack a vulnerable web server. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. The exploit allows an attacker. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside. Directory Traversal Examples.
From www.fity.club
Directory Traversal Directory Traversal Examples You will first use a directory traversal attack to hack a vulnerable web server. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. Path traversal is also known as directory traversal. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. The exploit allows an attacker. These. Directory Traversal Examples.
From unit42.paloaltonetworks.com
Exploits in the Wild for Citrix ADC and Citrix Gateway Directory Directory Traversal Examples In this lesson, you will learn how directory traversal works and how to mitigate it in your application. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. The exploit allows an attacker. An attacker can leverage a directory traversal vulnerability in the system to step out. Directory Traversal Examples.
From achievetampabay.org
How To Fix Path Traversal Vulnerability In C? New Directory Traversal Examples A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. You will first use a directory traversal attack to hack a vulnerable web server. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another. Directory Traversal Examples.
From www.invicti.com
Exploiting path traversal vulnerabilities in Java web applications Directory Traversal Examples You will first use a directory traversal attack to hack a vulnerable web server. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. The exploit allows an attacker. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form,. Directory Traversal Examples.
From null-byte.wonderhowto.com
How to Leverage a Directory Traversal Vulnerability into Code Execution Directory Traversal Examples A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. Path traversal is also known as directory traversal. For instance, an attacker might. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input. Directory Traversal Examples.
From spanning.com
directorytraversalexample Spanning Directory Traversal Examples A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. In this lesson, you will learn how. Directory Traversal Examples.
From www.north-networks.com
¿Que es, el ataque Directory Traversal? Directory Traversal Examples For instance, an attacker might. In a directory traversal attack, also known as path traversal, an attacker enters information in a web form, url address line, or another input method that gives them. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file. Directory Traversal Examples.
From blog.secuna.io
Hacking Applications with Directory Traversal Directory Traversal Examples You will first use a directory traversal attack to hack a vulnerable web server. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. The exploit. Directory Traversal Examples.
From www.fastly.com
Back to Basics Directory Traversal Fastly Directory Traversal Examples These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. You will first use a directory traversal attack to hack a vulnerable web server. Path traversal is also known as directory traversal. A path traversal attack (also known as. Directory Traversal Examples.
From www.youtube.com
Directory Traversal examples from web for pentester Directory Traversal Examples These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. For instance, an attacker might. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. In a directory traversal attack, also known as path traversal, an attacker enters information in. Directory Traversal Examples.
From learn.snyk.io
What is directory traversal? Tutorial & examples Snyk Learn Directory Traversal Examples An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. A path traversal attack (also known as directory traversal) aims to access files and directories that. Directory Traversal Examples.
From medium.com
Finding Path Traversal Vulnerability InfoSec Writeups Medium Directory Traversal Examples Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. Path traversal is also known as directory traversal. For instance, an attacker might. You will first use a directory traversal attack to hack a vulnerable web server. A. Directory Traversal Examples.
From computersciencewiki.org
Binary tree Computer Science Wiki Directory Traversal Examples You will first use a directory traversal attack to hack a vulnerable web server. Path traversal is also known as directory traversal. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. For instance, an attacker might. Examples of directory traversal attacks often involve manipulating url parameters. Directory Traversal Examples.
From www.imperva.com
directory traversal payload example 1 Directory Traversal Examples These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. For instance, an attacker might. The exploit allows an attacker. Path traversal is. Directory Traversal Examples.
From www.fity.club
Directory Traversal Directory Traversal Examples In this lesson, you will learn how directory traversal works and how to mitigate it in your application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. The exploit allows an attacker. A path traversal attack (also known as. Directory Traversal Examples.
From prophaze.com
What Is Directory Traversal? Cloud WAF Directory Traversal Examples In this lesson, you will learn how directory traversal works and how to mitigate it in your application. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. The exploit allows an attacker. In a directory traversal attack, also. Directory Traversal Examples.
From tipstrickshack.blogspot.com
How to exploit Directory traversal vulnerability? Hacking & Tricks Directory Traversal Examples For instance, an attacker might. In this lesson, you will learn how directory traversal works and how to mitigate it in your application. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Examples of directory traversal attacks often involve manipulating url parameters to access sensitive files. The exploit allows an attacker. A. Directory Traversal Examples.
From www.hackingloops.com
Hacking websites using Directory Traversal Attacks Hackingloops Directory Traversal Examples The exploit allows an attacker. A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. Path traversal is also known as directory traversal. Examples of directory traversal attacks often involve. Directory Traversal Examples.
From www.stackhawk.com
Node.js Path Traversal Guide Examples and Prevention Directory Traversal Examples An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view. The exploit allows an attacker. You will first use a directory traversal attack to hack a vulnerable web server. A path traversal attack (also known as directory traversal) aims to. Directory Traversal Examples.
From www.hackingloops.com
Hacking sites Using Directory Traversal Attacks Directory Traversal Examples Path traversal is also known as directory traversal. The exploit allows an attacker. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them to access other parts of the file system to view.. Directory Traversal Examples.
From www.akto.io
Mastering Directory Traversal A Comprehensive Guide from Basics to Directory Traversal Examples A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. An attacker can leverage a directory traversal vulnerability in the system to step out of the root directory, allowing them. Directory Traversal Examples.