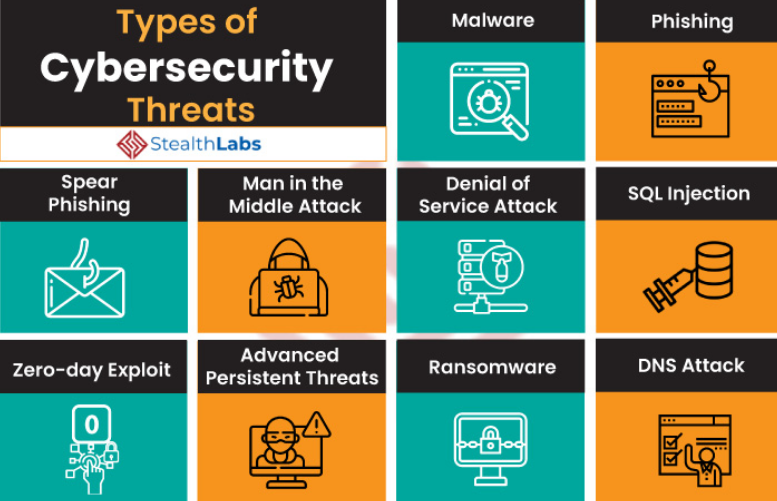
Hardware Threats Examples . Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here are some common hardware security flaws to look. But they can capture headlines. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware attacks do not usually make the news. This list, though not comprehensive, presents the most significant. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. The top 10 hardware vulnerabilities msps should know about. Gaining physical access to hardware is difficult. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that.
from support.aiesec.org
Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. The top 10 hardware vulnerabilities msps should know about. Gaining physical access to hardware is difficult. This list, though not comprehensive, presents the most significant. Here are some common hardware security flaws to look. But they can capture headlines. Hardware attacks do not usually make the news. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors.
Cyber Security Threats and Attacks AIESEC Help Center
Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. The top 10 hardware vulnerabilities msps should know about. This list, though not comprehensive, presents the most significant. Hardware attacks do not usually make the news. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. But they can capture headlines. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Gaining physical access to hardware is difficult. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Here are some common hardware security flaws to look. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors.
From identitymanagementinstitute.org
System Access and Compliance Threats Identity Management Institute® Hardware Threats Examples Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. But they can capture headlines. Here are some common hardware security flaws to look. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at. Hardware Threats Examples.
From www.trendmicro.com.tr
The IoT Attack Surface Threats and Security Solutions Security News Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. But they can capture headlines. Hardware attacks do not usually make the news. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware security has evolved into a pressing it issue as enterprises install autonomous. Hardware Threats Examples.
From www.slideserve.com
PPT IT Computer Security PowerPoint Presentation, free download ID Hardware Threats Examples Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware attacks do not usually make the news. Gaining physical access to hardware is difficult. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. To cast some light onto this alarming trend, let’s review the top 5. Hardware Threats Examples.
From www.revealrisk.com
Understanding and Managing Insider Threats in Cybersecurity Reveal Hardware Threats Examples Hardware attacks do not usually make the news. Here are some common hardware security flaws to look. Gaining physical access to hardware is difficult. This list, though not comprehensive, presents the most significant. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. But they can capture headlines. Hardware security has evolved into. Hardware Threats Examples.
From shawnetuma.com
OCR Issues Cyberattack Response Checklist and Infographic Business Hardware Threats Examples Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware attacks do not usually make the news. Here are some common hardware security flaws to look. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. The top 10 hardware vulnerabilities msps should know about.. Hardware Threats Examples.
From trailhead.salesforce.com
Cybersecurity Threat Identification Guide Salesforce Trailhead Hardware Threats Examples Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Here are some common hardware security flaws to look. The top 10 hardware vulnerabilities msps should know about. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Gaining physical access to hardware is difficult. This. Hardware Threats Examples.
From www.easeus.de
Virus vs. Ransomware vs. Malware Finden Sie die Unterschiede in 1 Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. This list, though not comprehensive, presents the most significant. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Gaining physical. Hardware Threats Examples.
From www.dailyinfographic.com
6 Types of Malware You Need To Know Daily Infographic Hardware Threats Examples Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Here are some common hardware security flaws to look.. Hardware Threats Examples.
From www.enisa.europa.eu
Hardware Threat Landscape and Good Practice Guide — ENISA Hardware Threats Examples Hardware attacks do not usually make the news. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. This list, though not comprehensive, presents the most significant. Gaining physical access to hardware is difficult. But they can capture headlines. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing. Hardware Threats Examples.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Hardware Threats Examples Here are some common hardware security flaws to look. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. This list, though not comprehensive, presents the most significant. But they can capture headlines. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Gaining physical access. Hardware Threats Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Hardware Threats Examples Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware attacks do not usually make the news. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. This list, though not comprehensive, presents the most significant. Hardware security has evolved into a pressing it issue. Hardware Threats Examples.
From www.slideserve.com
PPT Chapter 14 Computer Security Threats PowerPoint Presentation Hardware Threats Examples Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware attacks do not usually make the news. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Meltdown. Hardware Threats Examples.
From owasp.org
Threat Modeling Process OWASP Foundation Hardware Threats Examples Gaining physical access to hardware is difficult. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. This list, though not comprehensive, presents the most significant. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. To cast some light onto this alarming trend, let’s review. Hardware Threats Examples.
From www.researchgate.net
Hardwareinduced reliability threats in an example DHA and their Hardware Threats Examples This list, though not comprehensive, presents the most significant. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. The top. Hardware Threats Examples.
From www.researchgate.net
Overview of hardware threats and protection scenarios using proposed Hardware Threats Examples Hardware attacks do not usually make the news. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. This list, though not comprehensive, presents the most significant. Meltdown and spectre raised the alarm over vulnerabilities that. Hardware Threats Examples.
From www.slideserve.com
PPT IT Security PowerPoint Presentation, free download ID9613069 Hardware Threats Examples Gaining physical access to hardware is difficult. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. The top 10 hardware vulnerabilities msps should know about. This list, though not comprehensive, presents the most significant. But they can capture headlines. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in. Hardware Threats Examples.
From blog.contecamericas.com
Common Hardware Security Threats and How to Avoid Them Hardware Threats Examples Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware attacks do not usually make the news. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here are some common hardware security flaws to look. Gaining physical access to hardware is difficult. To cast some light. Hardware Threats Examples.
From computersecurityatsusen.blogspot.com
Computer Security Examples Of Computer Security Threats Hardware Threats Examples Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware attacks do not usually make the news. This list, though not comprehensive, presents the most significant. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware security has evolved into a pressing it issue. Hardware Threats Examples.
From slideplayer.com
Network and Security and Privacy ppt download Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware attacks do not usually make the news. The top 10 hardware vulnerabilities msps should know about. Meltdown and spectre raised the alarm over vulnerabilities that. Hardware Threats Examples.
From slideplayer.com
THREATS TO INFORMATION SYSTEMS ppt download Hardware Threats Examples Here are some common hardware security flaws to look. Hardware attacks do not usually make the news. Gaining physical access to hardware is difficult. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. This list,. Hardware Threats Examples.
From securetriad.io
Internal vs External Threats Here’s All You Need to Know Hardware Threats Examples The top 10 hardware vulnerabilities msps should know about. Gaining physical access to hardware is difficult. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Here are some common hardware security flaws to look. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware. Hardware Threats Examples.
From www.kaspersky.com
Deep Dive 5 Threats Affecting Hardware Kaspersky official blog Hardware Threats Examples Hardware attacks do not usually make the news. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. This list, though. Hardware Threats Examples.
From www.csoonline.com
33 hardware and firmware vulnerabilities A guide to the threats CSO Hardware Threats Examples Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware attacks do not usually make the news. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Here are some common hardware security flaws to look. To cast some light onto this alarming trend, let’s. Hardware Threats Examples.
From securetriad.io
Internal vs External Threats Here’s All You Need to Know Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware and firmware vulnerabilities can put your business and your customers’. Hardware Threats Examples.
From www.cybercrimeswatch.com
A Guide to Physical Security Threats and Physical Protection of Data in Hardware Threats Examples Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Here are some common hardware security flaws to look. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. But they. Hardware Threats Examples.
From www.charter-global.com
Common Physical Security Threats and Vulnerabilities (With Examples) Hardware Threats Examples The top 10 hardware vulnerabilities msps should know about. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware attacks do not usually make the news. Gaining physical access to hardware is difficult. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. But they. Hardware Threats Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Hardware Threats Examples Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Gaining physical access to hardware is difficult. Here are. Hardware Threats Examples.
From www.pinterest.com
Common Cyber Threats malwareicon in 2020 Cyber security technology Hardware Threats Examples Hardware attacks do not usually make the news. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here are some common hardware security flaws to look. The top 10 hardware vulnerabilities msps should know about. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. But they. Hardware Threats Examples.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Hardware Threats Examples To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities that. This list, though not comprehensive, presents the most significant. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors.. Hardware Threats Examples.
From www.slideserve.com
PPT 551 Computer and Network Security Slide Set 2 PowerPoint Hardware Threats Examples Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Hardware attacks do not usually make the news. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. But they can. Hardware Threats Examples.
From cyberbylr1.blogspot.com
The ultimate cyber security guide protect your data in the digital age. Hardware Threats Examples But they can capture headlines. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Gaining physical access to hardware is difficult. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. To cast some light onto this alarming trend, let’s review the top 5 dangerous hardware vulnerabilities. Hardware Threats Examples.
From hiotron13.medium.com
Hardware Threats to an IoT Ecosystem by hIOTron Medium Hardware Threats Examples Hardware attacks do not usually make the news. Here are some common hardware security flaws to look. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. But they can capture headlines. Hardware and firmware vulnerabilities can put. Hardware Threats Examples.
From www.founderjar.com
12 Types of Malware Attacks (Including Examples + Prevention Strategies) Hardware Threats Examples Gaining physical access to hardware is difficult. But they can capture headlines. Hardware security has evolved into a pressing it issue as enterprises install autonomous sensors, controllers and monitors. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at. Hardware Threats Examples.
From www.slideserve.com
PPT CSC 2260 Operating Systems and Networks PowerPoint Presentation Hardware Threats Examples Hardware and firmware vulnerabilities can put your business and your customers’ sensitive data at risk, costing you. Here are some common hardware security flaws to look. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. Gaining physical access to hardware is difficult. The top 10 hardware vulnerabilities msps should know about. Meltdown. Hardware Threats Examples.
From www.vrogue.co
The Osi Model Explained And How To Easily Remember It vrogue.co Hardware Threats Examples Gaining physical access to hardware is difficult. Meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Hardware attacks do not usually make the news. The top 10 hardware vulnerabilities msps should know about. Hardware attacks are particularly sneaky because they often require physical access to devices, making them less frequent. This list, though not. Hardware Threats Examples.