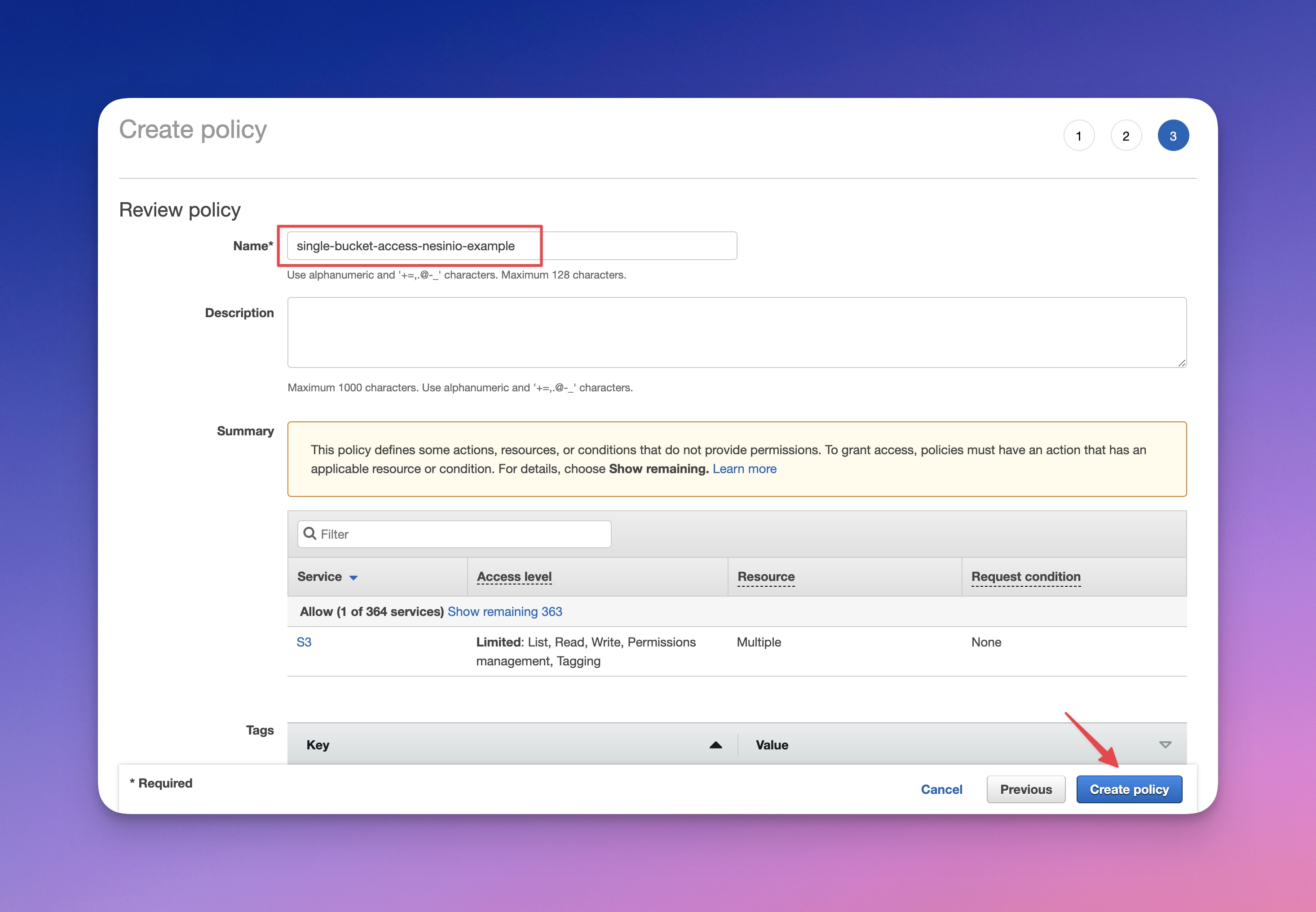
S3 Bucket Policy Limit . A group policy that is like the one below will allow. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. Bucket ownership is not transferable to another account. An amazon s3 bucket is owned by the aws account that created it. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. You can use bucket policies to add or deny. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation.
from nesin.io
A group policy that is like the one below will allow. You can use bucket policies to add or deny. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. Bucket ownership is not transferable to another account. An amazon s3 bucket is owned by the aws account that created it. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users.
How to Limit AWS IAM User Access to a Single S3 Bucket
S3 Bucket Policy Limit This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. A group policy that is like the one below will allow. Bucket ownership is not transferable to another account. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. You can use bucket policies to add or deny. An amazon s3 bucket is owned by the aws account that created it.
From www.youtube.com
S3 Follow Along Bucket Policies YouTube S3 Bucket Policy Limit You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. An amazon s3 bucket is owned by the aws account that created it. This s3 bucket policy enables. S3 Bucket Policy Limit.
From www.youtube.com
Amazon S3 batch operations S3 Access Points S3 Bucket Policy S3 Bucket Policy Limit This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. You can use bucket policies to add or deny. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users.. S3 Bucket Policy Limit.
From www.youtube.com
AWS S3 Tutorial (Part 3) How to set up Access Control on S3 ? IAM S3 Bucket Policy Limit A group policy that is like the one below will allow. Bucket ownership is not transferable to another account. You can use bucket policies to add or deny. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. This s3 bucket policy enables any iam principal (user or role) in. S3 Bucket Policy Limit.
From exodkftil.blob.core.windows.net
Aws S3 Bucket Policies Examples at Guy Deaton blog S3 Bucket Policy Limit The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. You can use the notprincipal element of an. S3 Bucket Policy Limit.
From www.cloudberrylab.com
Amazon S3 Bucket Policies Configuring Bucket Policy S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. Bucket ownership is not transferable to another account. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. The following example bucket policy. S3 Bucket Policy Limit.
From www.whizlabs.com
How to create a Lifecycle Policy for an S3 Bucket?Blog S3 Bucket Policy Limit The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. A group policy that is like the one below will allow. This. S3 Bucket Policy Limit.
From www.youtube.com
Give Permission to S3 bucket for IAM user using AWS CLI IAM Policy S3 Bucket Policy Limit Bucket ownership is not transferable to another account. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny.. S3 Bucket Policy Limit.
From www.scaler.com
S3 Bucket Policy Scaler Topics S3 Bucket Policy Limit You can use bucket policies to add or deny. An amazon s3 bucket is owned by the aws account that created it. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. You can use the notprincipal element of an iam or s3 bucket policy to limit. S3 Bucket Policy Limit.
From ceyxnyqd.blob.core.windows.net
Which Amazon S3 Bucket Policy Can Limit Access To A Specific Object at S3 Bucket Policy Limit The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny. Bucket ownership is not transferable to another account. This element allows you to block all users who are not defined in its value array, even if they have an allow in. S3 Bucket Policy Limit.
From 9to5answer.com
[Solved] S3 Bucket Policy to Allow access to specific 9to5Answer S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. This s3 bucket policy enables any iam principal (user or role) in account. S3 Bucket Policy Limit.
From ceyxnyqd.blob.core.windows.net
Which Amazon S3 Bucket Policy Can Limit Access To A Specific Object at S3 Bucket Policy Limit Bucket ownership is not transferable to another account. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. A group policy that is like the one below will allow. You can use bucket policies to add or deny. There is a great way to allow users to. S3 Bucket Policy Limit.
From www.techlear.com
How to create a lifecycle policy for an S3 Bucket on AWS Techlear S3 Bucket Policy Limit This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. An amazon s3 bucket is owned by the aws account that created it. You can use bucket policies to add or deny. This s3 bucket policy enables any iam principal (user or. S3 Bucket Policy Limit.
From www.youtube.com
Secure S3 Buckets & Objects with S3 Access Control ACL, Bucket Policy S3 Bucket Policy Limit The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. A group policy that is like the one below will allow. Bucket ownership is not transferable to another account. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set. S3 Bucket Policy Limit.
From nesin.io
How to Limit AWS IAM User Access to a Single S3 Bucket S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. A group policy that is like the one below will allow. You can use bucket policies to add or deny. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket. S3 Bucket Policy Limit.
From www.directdefense.com
Preventing S3 Buckets Exploitation DirectDefense S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. A group policy that is like the one below will allow. Bucket ownership is not transferable to another account. This element allows you to block all users who are not defined in its value array, even if they have an allow. S3 Bucket Policy Limit.
From cytecnet.heroinewarrior.com
Create Bucket Policy in AWS S3 Bucket with Python S3 Bucket Policy Limit An amazon s3 bucket is owned by the aws account that created it. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. A group policy that is like the one below will allow. The following example bucket policy grants amazon s3 permission to write objects (put. S3 Bucket Policy Limit.
From exoaxdnop.blob.core.windows.net
S3 List Bucket Policy Example at Linda Benedetto blog S3 Bucket Policy Limit This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. A group policy that is like the one below will allow. You can use bucket policies to add or deny. There is a great way to allow users to access a specific bucket without comprising knowledge of. S3 Bucket Policy Limit.
From aws.amazon.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure S3 Bucket Policy Limit You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. Bucket ownership is not transferable to another account. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. You can use bucket policies to add or deny. An. S3 Bucket Policy Limit.
From turbot.com
S3 bucket policies support for custom policies and guardrails S3 Bucket Policy Limit An amazon s3 bucket is owned by the aws account that created it. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets.. S3 Bucket Policy Limit.
From www.youtube.com
AWS S3 Bucket policies indepth intuition YouTube S3 Bucket Policy Limit An amazon s3 bucket is owned by the aws account that created it. A group policy that is like the one below will allow. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. This element allows you to block all users who are not defined in. S3 Bucket Policy Limit.
From www.ibm.com
Attaching an AWS S3 Bucket S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. The following example bucket policy grants amazon s3 permission to write objects (put. S3 Bucket Policy Limit.
From www.howtoforge.com
How to create a lifecycle policy for an S3 Bucket on AWS S3 Bucket Policy Limit An amazon s3 bucket is owned by the aws account that created it. A group policy that is like the one below will allow. You can use bucket policies to add or deny. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. Bucket ownership is not transferable to another account.. S3 Bucket Policy Limit.
From aws.amazon.com
Limit access to Amazon S3 buckets owned by specific AWS accounts AWS S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. An amazon s3 bucket is owned by the aws account that created it. A group policy that is like the one below will allow. This element allows you to block all users who are not defined in its value array, even. S3 Bucket Policy Limit.
From www.k9security.io
Test S3 bucket policy using IAM simulator k9 Security S3 Bucket Policy Limit This element allows you to block all users who are not defined in its value array, even if they have an allow in their own iam user policies. An amazon s3 bucket is owned by the aws account that created it. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a. S3 Bucket Policy Limit.
From exodkftil.blob.core.windows.net
Aws S3 Bucket Policies Examples at Guy Deaton blog S3 Bucket Policy Limit The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. A group policy that is like the one below will allow. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. There is a great way to. S3 Bucket Policy Limit.
From www.scaler.com
S3 Bucket Policy Scaler Topics S3 Bucket Policy Limit A group policy that is like the one below will allow. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. You can use bucket policies to add or deny. This element allows you to block all users who are not defined in its value array, even. S3 Bucket Policy Limit.
From ceyxnyqd.blob.core.windows.net
Which Amazon S3 Bucket Policy Can Limit Access To A Specific Object at S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. A group policy that is like the one below will allow. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny. This. S3 Bucket Policy Limit.
From roadmap.ploi.io
AWS S3 Bucket Options for Backup Ploi Roadmap S3 Bucket Policy Limit You can use bucket policies to add or deny. There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. An amazon s3 bucket is owned by the aws. S3 Bucket Policy Limit.
From theitbros.com
Controlling Access to S3 Buckets with AWS S3 Bucket Policy TheITBros S3 Bucket Policy Limit A group policy that is like the one below will allow. An amazon s3 bucket is owned by the aws account that created it. You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. Bucket ownership is not transferable to another account. This s3 bucket policy enables. S3 Bucket Policy Limit.
From cloudkatha.com
How to Create S3 Bucket Policy using Terraform CloudKatha S3 Bucket Policy Limit An amazon s3 bucket is owned by the aws account that created it. A group policy that is like the one below will allow. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use bucket policies to add or deny. Bucket ownership is not transferable to another. S3 Bucket Policy Limit.
From www.youtube.com
Create S3 Bucket Give S3 bucket access only to authorized IAM user S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. Bucket ownership is not transferable to another account. This element allows you to block all users who are. S3 Bucket Policy Limit.
From nesin.io
How to Limit AWS IAM User Access to a Single S3 Bucket S3 Bucket Policy Limit You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. This element allows you to block all users who are not defined in its. S3 Bucket Policy Limit.
From www.youtube.com
AWS S3 Bucket Permissions Access Control List Bucket Policy S3 Bucket Policy Limit There is a great way to allow users to access a specific bucket without comprising knowledge of other buckets. An amazon s3 bucket is owned by the aws account that created it. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. You can use the notprincipal element of an. S3 Bucket Policy Limit.
From bluexp.netapp.com
S3 Access for Objects With Different Permissions in an S3 Bucket S3 Bucket Policy Limit This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the amazon s3 get bucket (listobjects) operation. You can use bucket policies to add or deny. An amazon s3 bucket is owned by the aws account that created it. There is a great way to allow users to access a specific bucket without comprising. S3 Bucket Policy Limit.
From exohkaxmw.blob.core.windows.net
How To Find Unsecured S3 Buckets at Michael Goodman blog S3 Bucket Policy Limit You can use the notprincipal element of an iam or s3 bucket policy to limit resource access to a specific set of users. The following example bucket policy grants amazon s3 permission to write objects (put requests) from the account for the source. This s3 bucket policy enables any iam principal (user or role) in account 111122223333 to use the. S3 Bucket Policy Limit.