Fence_Scsi Example . Using scsi persistent reservations as a fence device. Configure the fence device itself to be able to fence your nodes and accept fencing requests. The actual fence agent you will use and the command that calls. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. These examples use the fence_ipmilan fence agent script for an ilo device. This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. This configuration protects storage resources from being written to by two.
from bcblog.sios.jp
This configuration protects storage resources from being written to by two. This includes any necessary configuration on. Using scsi persistent reservations as a fence device. The actual fence agent you will use and the command that calls. Configure the fence device itself to be able to fence your nodes and accept fencing requests. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. These examples use the fence_ipmilan fence agent script for an ilo device.
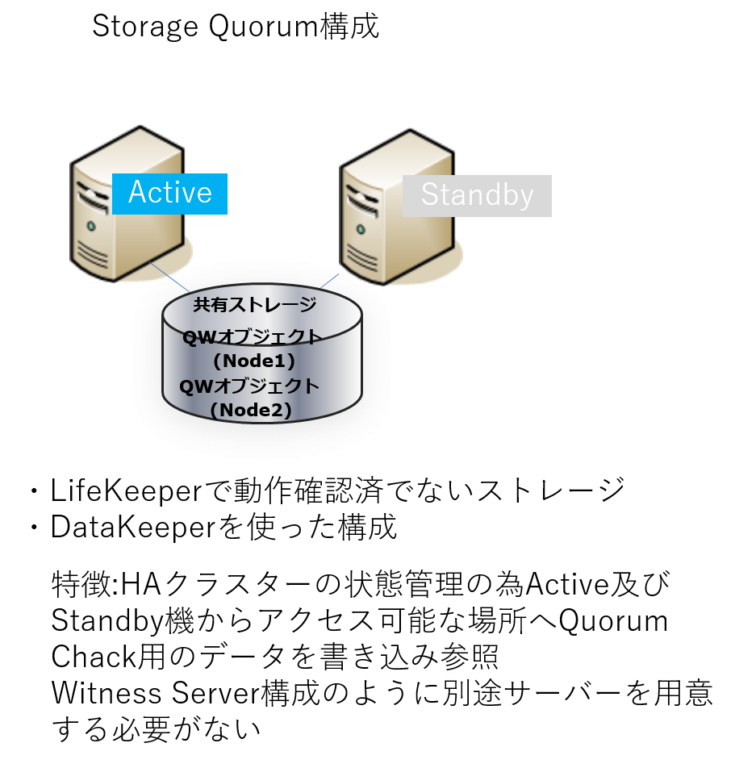
SCSI Reservationだけではない!LifeKeeperのIO Fencing機能 ビジネス継続とITについて考える
Fence_Scsi Example Using scsi persistent reservations as a fence device. This includes any necessary configuration on. Configure the fence device itself to be able to fence your nodes and accept fencing requests. The actual fence agent you will use and the command that calls. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Using scsi persistent reservations as a fence device. This configuration protects storage resources from being written to by two. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent.
From bcblog.sios.jp
SCSI Reservationだけではない!LifeKeeperのIO Fencing機能 ビジネス継続とITについて考える Fence_Scsi Example After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. This configuration protects storage resources from being written to by two. Using scsi persistent reservations as a fence device. The actual fence agent you will use and the command that calls. Configure the fence device itself to be able to fence. Fence_Scsi Example.
From ardupilot.org
Inclusion and Exclusion Fences — Rover documentation Fence_Scsi Example This includes any necessary configuration on. The actual fence agent you will use and the command that calls. These examples use the fence_ipmilan fence agent script for an ilo device. Using scsi persistent reservations as a fence device. This configuration protects storage resources from being written to by two. Red hat cluster suite employs scsi persistent reservations as a fencing. Fence_Scsi Example.
From www.unifloorwpc.com
Teak Composite Fence Panels UNIFLOOR Fence_Scsi Example Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. This includes any necessary configuration on. This configuration protects storage resources from being written to by two. Configure the fence device itself to be able to fence your nodes and accept fencing requests. After configuring a scsi fence device for clusternode1.example.com,. Fence_Scsi Example.
From www.steelfence.org
Ornamental Steel Fence Panels with Endless Designs Fence_Scsi Example This includes any necessary configuration on. Using scsi persistent reservations as a fence device. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Configure the fence device itself to be able to fence your nodes and accept fencing requests. This configuration protects storage resources from being written to by two.. Fence_Scsi Example.
From allanblock.com
Concrete Block Fence Fence Design Calculations Fence_Scsi Example This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. The actual fence agent you will use and the command that calls. This configuration protects storage. Fence_Scsi Example.
From fortressbp.com
3 Qualities that Strengthen School Fences Fortress Fencing Fence_Scsi Example These examples use the fence_ipmilan fence agent script for an ilo device. This includes any necessary configuration on. The actual fence agent you will use and the command that calls. This configuration protects storage resources from being written to by two. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for.. Fence_Scsi Example.
From farmstylegroup.co.za
Electric Fencing Farmstyle Construction Group Fence_Scsi Example This configuration protects storage resources from being written to by two. This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. The actual fence agent you will use and the command that calls. These examples use the fence_ipmilan fence agent script for an ilo device.. Fence_Scsi Example.
From www.bearsfencing.com.au
Fencing and landscaping example. Bears Fencing Fence_Scsi Example After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. These examples use the fence_ipmilan fence agent script for an ilo device. The actual fence agent you will use and the command that calls. Configure the fence device itself to be able to fence your nodes and accept fencing requests. Using. Fence_Scsi Example.
From www.quotientapp.com
Fencing Estimate Template Quotient Fence_Scsi Example Using scsi persistent reservations as a fence device. Configure the fence device itself to be able to fence your nodes and accept fencing requests. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. This includes any necessary configuration on. After configuring a scsi fence device for clusternode1.example.com, use the following. Fence_Scsi Example.
From www.homedit.com
15 Types of Fences for Your Yard Privacy, Safety, and Style Fence_Scsi Example After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Using scsi persistent reservations as a fence device. This includes any necessary configuration on. This configuration protects storage resources from being written. Fence_Scsi Example.
From www.quotientapp.com
Fencing Estimate Template Quotient Fence_Scsi Example This includes any necessary configuration on. Configure the fence device itself to be able to fence your nodes and accept fencing requests. This configuration protects storage resources from being written to by two. Using scsi persistent reservations as a fence device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for.. Fence_Scsi Example.
From e3d.ie
Safety / Security Fencing E3D Steel Design Ltd. Fence_Scsi Example The actual fence agent you will use and the command that calls. This includes any necessary configuration on. Using scsi persistent reservations as a fence device. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. This configuration protects. Fence_Scsi Example.
From fortressbp.com
Steel Fencing Steel Fence Options Fortress Framing Fence_Scsi Example This includes any necessary configuration on. The actual fence agent you will use and the command that calls. Configure the fence device itself to be able to fence your nodes and accept fencing requests. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent. Fence_Scsi Example.
From www.obriendriveways.ie
Wooden Fence Installers O'Brien Driveways Fence_Scsi Example This includes any necessary configuration on. Using scsi persistent reservations as a fence device. This configuration protects storage resources from being written to by two. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Configure the fence device itself to be able to fence your nodes and accept fencing requests.. Fence_Scsi Example.
From www.fix.com
Guide to Garden Fences Fence_Scsi Example The actual fence agent you will use and the command that calls. Using scsi persistent reservations as a fence device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Configure the fence device itself to be able to fence your nodes and accept fencing requests. Red hat cluster suite employs. Fence_Scsi Example.
From www.inchcalculator.com
Fence Calculator Estimate Wood Fencing Materials and Post Centers Fence_Scsi Example The actual fence agent you will use and the command that calls. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. This configuration protects storage resources from being written to by two. This includes any necessary configuration on.. Fence_Scsi Example.
From arironllc.com
Keep Your Home Secure and Stylish with Custom Iron Fencing Fence_Scsi Example This includes any necessary configuration on. Configure the fence device itself to be able to fence your nodes and accept fencing requests. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a scsi fence device for. Fence_Scsi Example.
From www.quotientapp.com
Fencing Estimate Template Quotient Fence_Scsi Example This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Configure the fence device itself to be able to fence your nodes and accept fencing requests. This configuration protects storage resources from being written to by two. These examples use the fence_ipmilan fence agent script. Fence_Scsi Example.
From oclandscape.com
Fence Detail Turned Earth Fence_Scsi Example After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. This includes any necessary configuration on. Configure the fence device itself to be able to fence your nodes and accept fencing requests.. Fence_Scsi Example.
From www.youtube.com
An Overview of SCSI and SCSI type drives. YouTube Fence_Scsi Example These examples use the fence_ipmilan fence agent script for an ilo device. The actual fence agent you will use and the command that calls. This configuration protects storage resources from being written to by two. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Configure the fence device itself to. Fence_Scsi Example.
From mungfali.com
Fencing Risk Assessment Template Fence_Scsi Example These examples use the fence_ipmilan fence agent script for an ilo device. This configuration protects storage resources from being written to by two. Configure the fence device itself to be able to fence your nodes and accept fencing requests. This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use. Fence_Scsi Example.
From mfrcorp.com
Fence System, Architectural Fence and Security Fence Solutions Fence_Scsi Example Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Configure the fence device itself to be able to fence your nodes and accept fencing requests. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to. Fence_Scsi Example.
From pentagonfencing.com.au
Colorbond Fencing Everything You Need to Know Pentagon Fence_Scsi Example This includes any necessary configuration on. The actual fence agent you will use and the command that calls. Using scsi persistent reservations as a fence device. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. These examples use the fence_ipmilan fence agent script for an ilo device. After configuring a. Fence_Scsi Example.
From bcblog.sios.jp
SCSI Reservationだけではない!LifeKeeperのIO Fencing機能 ビジネス継続とITについて考える Fence_Scsi Example Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. These examples use the fence_ipmilan fence agent script for an ilo device. This configuration protects storage resources from being written to by two. Using scsi persistent reservations as a fence device. This includes any necessary configuration on. After configuring a scsi. Fence_Scsi Example.
From csfencing.com
Property Management Fencing Markets C&S Fencing Fence_Scsi Example Configure the fence device itself to be able to fence your nodes and accept fencing requests. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Using scsi persistent reservations as a fence device. This configuration protects storage resources from being written to by two. These examples use the fence_ipmilan fence. Fence_Scsi Example.
From trexfencingfds.com
Fence Layout Example Trex Fencing FDS Fence_Scsi Example These examples use the fence_ipmilan fence agent script for an ilo device. This configuration protects storage resources from being written to by two. The actual fence agent you will use and the command that calls. This includes any necessary configuration on. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent.. Fence_Scsi Example.
From www.inchcalculator.com
15 Popular Fence Styles for Privacy and Picket Fences Inch Calculator Fence_Scsi Example This includes any necessary configuration on. These examples use the fence_ipmilan fence agent script for an ilo device. Using scsi persistent reservations as a fence device. Configure the fence device itself to be able to fence your nodes and accept fencing requests. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi. Fence_Scsi Example.
From www.perthtradecentre.com.au
colorbondfencingandgates Perth Trade Centre Fence_Scsi Example After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Configure the fence device itself to be able to fence your nodes and accept fencing requests. These examples use the fence_ipmilan fence agent script for an ilo device. Using scsi persistent reservations as a fence device. This includes any necessary configuration. Fence_Scsi Example.
From www.flickr.com
Fencing Technique David Gallagher Flickr Fence_Scsi Example Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Configure the fence device itself to be able to fence your nodes and accept fencing requests. This configuration protects storage resources from. Fence_Scsi Example.
From www.scribd.com
Example of Structural Details for a Fence Building Technology Fence_Scsi Example Configure the fence device itself to be able to fence your nodes and accept fencing requests. Using scsi persistent reservations as a fence device. This includes any necessary configuration on. This configuration protects storage resources from being written to by two. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent.. Fence_Scsi Example.
From www.homeimprovementpages.com.au
Examples of Fencing Galleries Ezy Budget Fencing Fence_Scsi Example Configure the fence device itself to be able to fence your nodes and accept fencing requests. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. These examples use the fence_ipmilan fence agent script for an ilo device. This includes any necessary configuration on. Using scsi persistent reservations as a fence. Fence_Scsi Example.
From www.flickr.com
img_3628_fence examples_ Fencing done properly Flickr Fence_Scsi Example This includes any necessary configuration on. These examples use the fence_ipmilan fence agent script for an ilo device. This configuration protects storage resources from being written to by two. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent reservations as a fencing methods. Fence_Scsi Example.
From fenceall.com
A quick rundown of fencing language Fence All Fence_Scsi Example This includes any necessary configuration on. Configure the fence device itself to be able to fence your nodes and accept fencing requests. These examples use the fence_ipmilan fence agent script for an ilo device. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. This configuration protects storage resources from being. Fence_Scsi Example.
From www.familyhandyman.com
10 Modern Fence Ideas for Your Backyard — The Family Handyman Fence_Scsi Example Configure the fence device itself to be able to fence your nodes and accept fencing requests. This includes any necessary configuration on. Using scsi persistent reservations as a fence device. The actual fence agent you will use and the command that calls. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device. Fence_Scsi Example.
From staytuff.com
Fence Post Spacing A stepbystep guide Fence_Scsi Example The actual fence agent you will use and the command that calls. After configuring a scsi fence device for clusternode1.example.com, use the following procedure to configure a scsi fence device for. Red hat cluster suite employs scsi persistent reservations as a fencing methods through the use of the fence_scsi agent. Using scsi persistent reservations as a fence device. Configure the. Fence_Scsi Example.