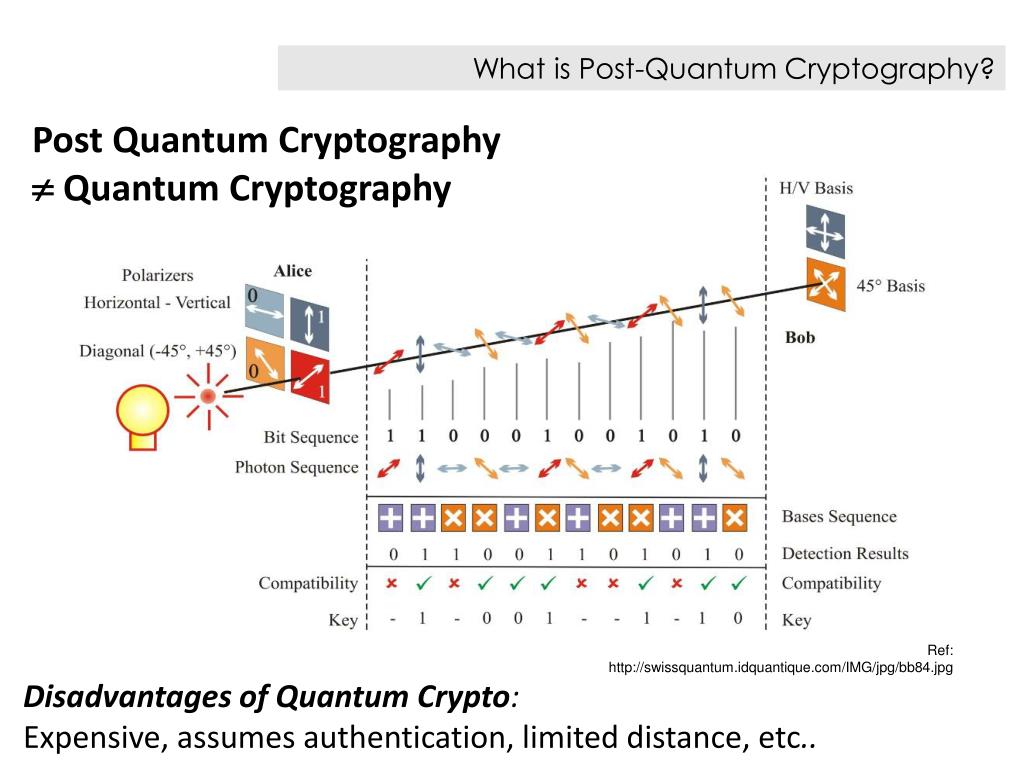
Post Quantum Cryptography Algorithms . Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer.
from www.slideserve.com
Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer.
PPT Cryptography in a Post Quantum Computing World PowerPoint
Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Conduct an inventory to identify and understand cryptographic systems and assets.
From www.researchgate.net
The third round algorithms of the NIST post quantum cryptography Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this. Post Quantum Cryptography Algorithms.
From semiwiki.com
Postquantum cryptography steps on the field SemiWiki Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released. Post Quantum Cryptography Algorithms.
From www.secure-ic.com
Post quantum cryptography advanced Solutions SecureIC Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this. Post Quantum Cryptography Algorithms.
From www.cbinsights.com
PostQuantum Cryptography A Look At How To Withstand Quantum Computer Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this. Post Quantum Cryptography Algorithms.
From www.technologyreview.com
Explainer What is postquantum cryptography? MIT Technology Review Post Quantum Cryptography Algorithms Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the. Post Quantum Cryptography Algorithms.
From www.mdpi.com
Sensors Free FullText Resilience Optimization of PostQuantum Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From www.mpg.de
NIST identifies four algorithms for postquantum cryptography Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the. Post Quantum Cryptography Algorithms.
From www.infineon.com
Ready for tomorrow Infineon demonstrates first postquantum Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has chosen four encryption algorithms that are designed to withstand the. Post Quantum Cryptography Algorithms.
From www.codingninjas.com
Introduction to PostQuantum Cryptography Coding Ninjas Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From blog.quarkslab.com
Status of postquantum cryptography implementation Quarkslab's blog Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From www.thesslstore.com
NIST Announces 2024 Timeline for First Standardized PostQuantum Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released. Post Quantum Cryptography Algorithms.
From www.mdpi.com
IoT Free FullText PostQuantum Cryptosystems for Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From capalearning.com
What Is Postquantum Cryptography? Capa Learning Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From www.sigarch.org
Post Quantum Cryptography SIGARCH Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack. Post Quantum Cryptography Algorithms.
From seqred.pl
Paving the way for PostQuantum Cryptography SEQRED Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the. Post Quantum Cryptography Algorithms.
From www.eeworldonline.com
What is a postquantum cryptographic method? Post Quantum Cryptography Algorithms Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released. Post Quantum Cryptography Algorithms.
From www.pinterest.co.uk
Approaches to PostQuantum Cryptography Cryptography, Cyber security Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From www.sectigo.com
What Is Quantum Cryptography And How it Works Sectigo® Official Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released a final set of encryption tools designed to withstand the attack. Post Quantum Cryptography Algorithms.
From www.slideshare.net
Post Quantum Cryptography Technical Overview PPT Post Quantum Cryptography Algorithms Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the. Post Quantum Cryptography Algorithms.
From www.researchgate.net
Requirements for the Implementation of Quantum Cryptography Download Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.keyfactor.com
Approaches to Deploying PostQuantum Cryptography Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From certera.com
First Standardized PostQuantum Cryptography Algorithms Timeline 2024 Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.cbinsights.com
PostQuantum Cryptography A Look At How To Withstand Quantum Computer Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.cybersecurity.blog.aisec.fraunhofer.de
A (somewhat) gentle introduction to latticebased postquantum Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released. Post Quantum Cryptography Algorithms.
From www.researchgate.net
(PDF) PostQuantum Cryptosystems for A Survey on Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released. Post Quantum Cryptography Algorithms.
From internationalsecurityjournal.com
What is Post Quantum Cryptography Encryption? Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.nexenio.com
How to adopt PostQuantum Cryptography neXenio Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack. Post Quantum Cryptography Algorithms.
From www.datacenterdynamics.com
NIST picks four candidate algorithms for postquantum cryptography DCD Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this. Post Quantum Cryptography Algorithms.
From www.slideserve.com
PPT Cryptography in a Post Quantum Computing World PowerPoint Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.mdpi.com
IoT Free FullText PostQuantum Cryptosystems for Post Quantum Cryptography Algorithms Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From analyticsdrift.com
NIST announces four postquantum cryptography algorithms Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this vulnerability, the recently announced algorithms are specified in the first completed. Post Quantum Cryptography Algorithms.
From www.cbinsights.com
PostQuantum Cryptography A Look At How To Withstand Quantum Computer Post Quantum Cryptography Algorithms To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Conduct an inventory to identify and understand cryptographic systems and assets. Nist has chosen four encryption algorithms that are designed to withstand the. Post Quantum Cryptography Algorithms.
From www.appviewx.com
6 Steps To Prepare For PostQuantum Cryptography Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. Conduct an inventory to identify and understand cryptographic systems and assets. To defend against this. Post Quantum Cryptography Algorithms.
From www.researchgate.net
(PDF) PostQuantum Cryptography Algorithms Standardization and Post Quantum Cryptography Algorithms Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. To defend against this vulnerability, the recently announced algorithms are specified in the first completed standards from nist’s post. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the. Post Quantum Cryptography Algorithms.
From www.sigarch.org
Post Quantum Cryptography SIGARCH Post Quantum Cryptography Algorithms Conduct an inventory to identify and understand cryptographic systems and assets. Nist has released a final set of encryption tools designed to withstand the attack of a quantum computer. Nist has chosen four encryption algorithms that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect. To defend against this. Post Quantum Cryptography Algorithms.