Security Monitoring Procedures . a structured process to identify and implement use cases helps security and risk management technical professionals. security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. continuous monitoring applies to all security controls implemented in organizational information systems and. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. The guide provides advice and guidance on how to: your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your.
from www.yokogawa.com
your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. The guide provides advice and guidance on how to: a structured process to identify and implement use cases helps security and risk management technical professionals. security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all security controls implemented in organizational information systems and.
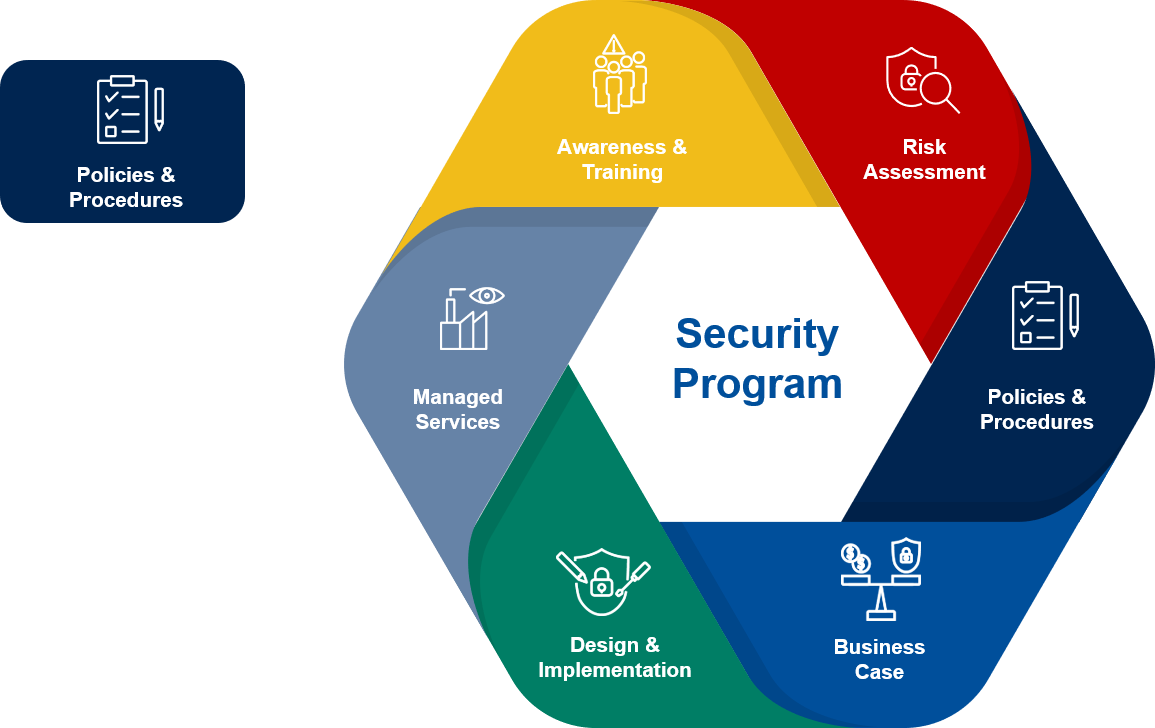
Cybersecurity Policies & Procedures Yokogawa Electric Corporation
Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. The guide provides advice and guidance on how to: a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. a structured process to identify and implement use cases helps security and risk management technical professionals. continuous monitoring applies to all security controls implemented in organizational information systems and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,.
From sitemate.com
Risk monitoring and control Here's how to do it better and safer Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. security monitoring process and learn about where and how you can get help. The guide provides advice and. Security Monitoring Procedures.
From mavink.com
Risk Management Process Model Security Monitoring Procedures security monitoring process and learn about where and how you can get help. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance. Security Monitoring Procedures.
From www.researchgate.net
Basic structure of security monitoring. Download Scientific Diagram Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. The guide provides advice and guidance on how to: security monitoring process and learn about where and how you can get help. continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and. Security Monitoring Procedures.
From www.gov.uk
[Withdrawn] Security monitoring aspects of design GOV.UK Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance on how to: a structured process to identify and implement use cases helps. Security Monitoring Procedures.
From www.complianceforge.com
Cybersecurity Procedures & Control Activities Security Monitoring Procedures continuous monitoring applies to all security controls implemented in organizational information systems and. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. there are best practices and guiding principles that. Security Monitoring Procedures.
From www.researchgate.net
Network security monitoring process diagram Download Scientific Diagram Security Monitoring Procedures The guide provides advice and guidance on how to: a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a structured process to identify and implement use cases helps security and risk. Security Monitoring Procedures.
From inbound.usisecurity.com
What Are The Benefits Of Remote Surveillance Monitoring? Security Monitoring Procedures continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance on how to: your monitoring data provides enough detail to reliably detect security incidents that could affect. Security Monitoring Procedures.
From symbanservices.com
Security Monitoring Service Symban Services Security Monitoring Procedures there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. security monitoring process and learn about where and how you can get help. continuous monitoring applies to all security controls implemented in organizational information systems and. a structured process to identify and implement use cases. Security Monitoring Procedures.
From www.orivisiontech.com
Security & Monitor Solutions ORIVISION Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all security controls implemented in organizational information systems and. security monitoring process and learn about where and. Security Monitoring Procedures.
From cybriant.com
How 24/7 Security Monitoring Can Help Keep Your Network Online Cybriant Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. security monitoring process and learn about where and how you can get help. your monitoring data provides enough detail. Security Monitoring Procedures.
From isea.utoronto.ca
Incident Security Response Plan Information Security and Enterprise Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms. Security Monitoring Procedures.
From medium.com
Cyber Security Monitoring and Management Best Practices by Delta IT Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. The guide provides advice and guidance on how to: security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms must rely on to develop, adjust and mature. Security Monitoring Procedures.
From sitemate.com
Risk monitoring and control Here's how to do it better and safer Security Monitoring Procedures security monitoring process and learn about where and how you can get help. The guide provides advice and guidance on how to: there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures. Security Monitoring Procedures.
From www.monarchconnected.com
What is Continuous Security Monitoring? Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and learn about where and how you can get help. continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and guiding principles that firms must rely on. Security Monitoring Procedures.
From www.slideteam.net
Security Monitoring Dashboard With Malicious Requests And Average Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. continuous monitoring applies to all security controls implemented in organizational information systems and. a security monitoring strategy and plan. Security Monitoring Procedures.
From xmcyber.com
Continuous Control Monitoring (CCM) XM Cyber Security Monitoring Procedures continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance on how to: your monitoring data provides enough detail to reliably detect security incidents that could affect. Security Monitoring Procedures.
From www.researchgate.net
Example of monitoring procedures in a decision support system Security Monitoring Procedures The guide provides advice and guidance on how to: a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a structured process to identify and implement use cases helps security and risk. Security Monitoring Procedures.
From www.teramind.co
Insider Threat Detection, Monitoring & Prevention Teramind Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all security controls implemented in organizational information systems and. a structured process to identify and implement use cases helps security and risk management technical professionals. The guide provides advice and guidance on how to: there. Security Monitoring Procedures.
From www.sentrysecurity.net
Safeguard Yourself with Professional Security Monitoring Services Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. continuous monitoring applies to all security controls implemented in organizational information systems and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and learn about where and how. Security Monitoring Procedures.
From templates.hilarious.edu.np
Rmf Continuous Monitoring Plan Template Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all. Security Monitoring Procedures.
From infrasos.com
Top 10 Best SIEM Tools for Cyber Attack Monitoring (Pros Cons) Security Monitoring Procedures there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all security controls implemented in organizational information systems and. The guide provides advice and guidance. Security Monitoring Procedures.
From www.slideteam.net
Effective security monitoring plan to eliminate cyber threats and data Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and learn about where and how you can get help. a structured process to identify and implement use cases helps security and risk management technical professionals. continuous monitoring applies to all security controls implemented in. Security Monitoring Procedures.
From www.cyres-consulting.com
Learn about cybersecurity monitoring and event evaluation Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. continuous monitoring applies to all security controls implemented in organizational information systems and. security monitoring process and learn about where and how you can get help. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures. Security Monitoring Procedures.
From www.valleyalarm.com
ValleyGuard Video Monitoring vs. Live Security Guards Valley Alarm Security Monitoring Procedures continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. a structured process to identify. Security Monitoring Procedures.
From www.gotchasecurity.net
LiveMonitoring Gotcha SecurityGotcha Security Security Monitoring Procedures there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. continuous monitoring applies to all security controls implemented in organizational information systems and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. security monitoring process and. Security Monitoring Procedures.
From lardas.com.cy
Lardas Security Communication & Monitoring Center Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a structured process to identify and implement use cases helps security and risk management technical professionals. security monitoring process and learn about where and how you can get help. continuous monitoring applies to all security controls implemented in. Security Monitoring Procedures.
From www.researchgate.net
Classification of security monitoring systems CSN. Download Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance on how to: a security monitoring strategy and plan defines the goals, scope, roles,. Security Monitoring Procedures.
From www.edsuk.com
Monitoring Services EDS UK Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. The guide provides advice and guidance. Security Monitoring Procedures.
From www.venkon.us
Cloud Security Monitoring Services Venkon Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. continuous monitoring applies to all security controls implemented in organizational information systems and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. a structured process to identify. Security Monitoring Procedures.
From secureframe.com
6 Benefits of Continuous Monitoring for Cybersecurity Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. The guide provides advice and guidance on how to: security monitoring process and learn about where and how you. Security Monitoring Procedures.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. a structured process to identify and implement use cases helps security and risk management technical professionals. security monitoring process and learn about where and how you can get help. there are best practices and guiding principles that firms must. Security Monitoring Procedures.
From www.virtualmetric.com
Network Security Monitoring Essential Guide VirtualMetric Security Monitoring Procedures continuous monitoring applies to all security controls implemented in organizational information systems and. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. security monitoring process and learn. Security Monitoring Procedures.
From www.yokogawa.com
Cybersecurity Policies & Procedures Yokogawa Electric Corporation Security Monitoring Procedures your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. The guide provides advice and guidance on how to: a structured process to identify and implement use cases helps security and risk management technical professionals. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures. Security Monitoring Procedures.
From www.slideteam.net
Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Security Monitoring Procedures a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. there are best practices and guiding principles that firms must rely on to develop, adjust and mature their security monitoring strategy,. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. . Security Monitoring Procedures.
From www.neumetric.com
Digital Security Monitoring Enhancing Cybersecurity Through Security Monitoring Procedures a structured process to identify and implement use cases helps security and risk management technical professionals. a security monitoring strategy and plan defines the goals, scope, roles, tools, and procedures for implementing and. your monitoring data provides enough detail to reliably detect security incidents that could affect the operation of your. The guide provides advice and guidance. Security Monitoring Procedures.