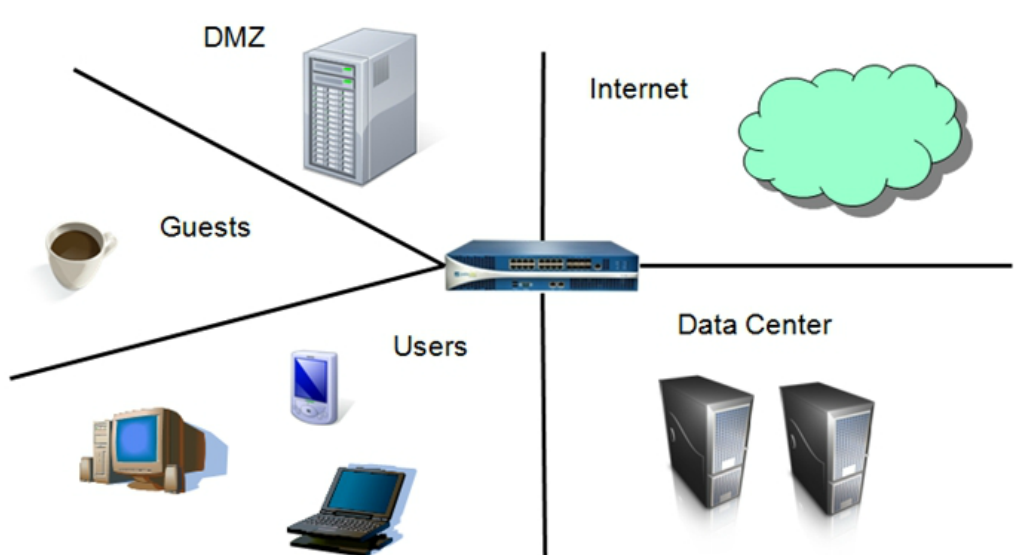
Security System Zones . By default, developed information systems should consist of at least three components (security zones): Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Here are some questions that can help guide your boundary protection analysis. A security zone is a portion of a network that has specific security requirements set. Learn about network security architectures, including dmz, trusted, and untrusted zones. Each zone consists of a single interface or a group of interfaces, to which a security policy is. Understand how these security zones. Each zone inside the network has different security requirement depending on the systems hosted within. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Consists of the grouping of cyber assets that share the same cybersecurity requirements. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. As per the sans, below listed are common security zones which should be implemented.
from palo-alto-firewall.blogspot.com
A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. By default, developed information systems should consist of at least three components (security zones): A security zone is a portion of a network that has specific security requirements set. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Each zone consists of a single interface or a group of interfaces, to which a security policy is. Each zone inside the network has different security requirement depending on the systems hosted within. Learn about network security architectures, including dmz, trusted, and untrusted zones. Here are some questions that can help guide your boundary protection analysis. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Consists of the grouping of cyber assets dedicated exclusively to communications, and which.
Palo Alto Interfaces and security zones
Security System Zones As per the sans, below listed are common security zones which should be implemented. Consists of the grouping of cyber assets that share the same cybersecurity requirements. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Here are some questions that can help guide your boundary protection analysis. By default, developed information systems should consist of at least three components (security zones): Understand how these security zones. Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Each zone consists of a single interface or a group of interfaces, to which a security policy is. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Learn about network security architectures, including dmz, trusted, and untrusted zones. As per the sans, below listed are common security zones which should be implemented. A security zone is a portion of a network that has specific security requirements set. Each zone inside the network has different security requirement depending on the systems hosted within.
From www.securityri.com
Security Strategy for Facility and Assets A Holistic Approach Security System Zones Understand how these security zones. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. By default, developed information systems should consist of at least three components (security zones): Each zone inside the network has different security requirement depending on the systems hosted within. Consists of. Security System Zones.
From www.slideshare.net
Chapter 06 Security System Zones Understand how these security zones. As per the sans, below listed are common security zones which should be implemented. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Learn about network security architectures, including dmz, trusted, and untrusted zones. A security zone is. Security System Zones.
From alanstreet.net
Reading List Using the IBM Security Framework and IBM Security Security System Zones As per the sans, below listed are common security zones which should be implemented. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Understand how these security zones. A security zone is a. Security System Zones.
From www.alamy.com
Isometric alarm system home. Home security. Security alarm keypad with Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. A security zone is a portion of a network that has specific security requirements set. By default, developed information systems should consist of at least three components (security zones): A security zone is a grouping of systems and components based on their. Security System Zones.
From www.caplin.com
Caplin Systems Caplin Platform 8 Deployment Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Learn about network security architectures, including dmz, trusted, and untrusted zones. Each zone consists of a single interface or a group of interfaces, to which a security policy is. Each zone inside the network. Security System Zones.
From www.connectsavannah.com
Large 'Enhanced Security Zone' set for Pence visit; includes multiple Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. As per the sans, below listed are common security zones which should be implemented. Each zone inside the network has different security requirement depending on the systems hosted within. Consists of the grouping of cyber assets dedicated exclusively to communications, and which.. Security System Zones.
From www.alamy.com
Access control system Alarm zones security system concept website Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. A security zone is a portion of a network that has specific security requirements set. Each zone consists of a single interface or a group of interfaces, to which a security policy is. Each zone inside the network has different security requirement depending on the systems hosted. Security System Zones.
From www.youtube.com
Configuring Security Zones with J YouTube Security System Zones A security zone is a portion of a network that has specific security requirements set. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Learn about network security architectures, including dmz, trusted, and untrusted zones. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within. Security System Zones.
From systemscoach.blogspot.com
Systems Coach Map of G20 Security Zones Security System Zones In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Understand how these security zones. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Each zone consists of a single interface or a group of interfaces, to which a security policy is.. Security System Zones.
From aws.amazon.com
VPC Zoning Patterns for SAP on AWS, Part 2 Network Zoning AWS Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. Learn about network security architectures, including dmz, trusted, and untrusted zones. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. As per the sans, below listed are. Security System Zones.
From www.alamy.com
Access control system Alarm zones security system concept website Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. A security zone is a portion of a network that has specific security requirements set. Each zone consists of a single interface or a group of interfaces, to which a security policy is. A security zone is a grouping of systems and components based on their functional,. Security System Zones.
From www.alamy.com
Access control system Alarm zones security system concept website Security System Zones A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Understand how these security zones. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Consists of the grouping of cyber assets that. Security System Zones.
From www.titanhq.com
Best Firewall Security Zone Segmentation Free Guide Security System Zones Consists of the grouping of cyber assets that share the same cybersecurity requirements. Here are some questions that can help guide your boundary protection analysis. A security zone is a portion of a network that has specific security requirements set. As per the sans, below listed are common security zones which should be implemented. Each zone inside the network has. Security System Zones.
From www.chemanager-online.com
Cyber Security for Industrial Control Systems CHEManager Security System Zones By default, developed information systems should consist of at least three components (security zones): Each zone inside the network has different security requirement depending on the systems hosted within. As per the sans, below listed are common security zones which should be implemented. A security zone is a portion of a network that has specific security requirements set. Consists of. Security System Zones.
From medium.com
Security Zoning in Network Architecture by Aman Bansal Jun, 2020 Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. By default, developed information systems should consist of at least three components (security zones): As per the sans, below listed are common security zones which should be implemented. Consists of the grouping of cyber assets that share the same cybersecurity requirements. Each. Security System Zones.
From jervis.ws
Implementing Security Zones with Home Routers for the IoT early years Security System Zones Understand how these security zones. Here are some questions that can help guide your boundary protection analysis. A security zone is a portion of a network that has specific security requirements set. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Consists of the grouping of. Security System Zones.
From www.dreamstime.com
Access Control System Alarm Zones Security System Concept site Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Understand how these security zones. A security zone is a portion of a network that has specific security requirements set. Here are some questions that can help guide your boundary protection analysis. As per the sans, below listed are common security zones which should be implemented. Each. Security System Zones.
From www.mdpi.com
JCP Free FullText Security and Independence of Process Safety and Security System Zones By default, developed information systems should consist of at least three components (security zones): Each zone consists of a single interface or a group of interfaces, to which a security policy is. Understand how these security zones. Each zone inside the network has different security requirement depending on the systems hosted within. Here are some questions that can help guide. Security System Zones.
From www.alamy.com
Access control system Alarm zones security system concept website Security System Zones Understand how these security zones. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Consists of the grouping of cyber assets that share the same cybersecurity requirements. By default, developed information systems. Security System Zones.
From www.slideserve.com
PPT Security+ AllInOne Edition Chapter 7 Physical Security Security System Zones Each zone inside the network has different security requirement depending on the systems hosted within. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Here are some questions that can help guide your boundary protection analysis. Understand how these security zones. As per the sans, below. Security System Zones.
From www.researchgate.net
The proposed Network Security Zones and Levels Download Scientific Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Learn about network security architectures, including dmz, trusted, and untrusted zones. A security zone is a portion of a. Security System Zones.
From storables.com
Which Home Security System Allows Arming Specific Zones Storables Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. Consists of the grouping of cyber assets that share the same cybersecurity requirements. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Understand how these security zones. By. Security System Zones.
From evbn.org
Top 21 security zones in network security in 2022 EUVietnam Business Security System Zones Consists of the grouping of cyber assets that share the same cybersecurity requirements. As per the sans, below listed are common security zones which should be implemented. Each zone inside the network has different security requirement depending on the systems hosted within. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of. Security System Zones.
From build5nines.com
IoT Security Architecture Trust Zones And Boundaries Build5Nines Security System Zones By default, developed information systems should consist of at least three components (security zones): Each zone inside the network has different security requirement depending on the systems hosted within. A security zone is a portion of a network that has specific security requirements set. Here are some questions that can help guide your boundary protection analysis. In cybersecurity, the concepts. Security System Zones.
From www.cisco.com
Industrial Security Design Guide Industrial Security Design Guide Security System Zones A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Here are some questions that can help guide your boundary protection analysis. Consists of the grouping of cyber assets that share the same cybersecurity requirements. As per the sans, below listed are common security zones which should. Security System Zones.
From palo-alto-firewall.blogspot.com
Palo Alto Interfaces and security zones Security System Zones Each zone consists of a single interface or a group of interfaces, to which a security policy is. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. By default, developed information systems should consist of at least three components (security zones): Consists of the grouping. Security System Zones.
From techacad.net
Juniper SRX Firewall Security Zones Configuration StepbyStep Guide Security System Zones Consists of the grouping of cyber assets that share the same cybersecurity requirements. Consists of the grouping of cyber assets dedicated exclusively to communications, and which. By default, developed information systems should consist of at least three components (security zones): Each zone inside the network has different security requirement depending on the systems hosted within. Understand how these security zones.. Security System Zones.
From www.slideserve.com
PPT NERC CIP Compliance PowerPoint Presentation, free download ID Security System Zones Here are some questions that can help guide your boundary protection analysis. A security zone is a portion of a network that has specific security requirements set. Consists of the grouping of cyber assets that share the same cybersecurity requirements. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share. Security System Zones.
From blog.isa.org
How to Design and Configure Secure Industrial Networks Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. Each zone inside the network has different security requirement depending on the systems hosted within. Consists of the grouping of cyber assets that share the same cybersecurity requirements. As per the sans, below listed are common security zones which should be implemented. By default, developed information systems. Security System Zones.
From www.regencyfireandsecurity.co.uk
A Fire Alarm Zone Plan Will Make Your Business A Safer Place Regency Security System Zones A security zone is a portion of a network that has specific security requirements set. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Each zone consists of a single interface or a group of interfaces, to which a security policy is. Understand how these security. Security System Zones.
From www.dreamstime.com
Access Control System Alarm Zones Security System Concept site Security System Zones Consists of the grouping of cyber assets that share the same cybersecurity requirements. Consists of the grouping of cyber assets dedicated exclusively to communications, and which. A security zone is a portion of a network that has specific security requirements set. Each zone inside the network has different security requirement depending on the systems hosted within. By default, developed information. Security System Zones.
From petrorisk.com
PetroRisk Technical Safety & Risk Management Services Cyber Security Security System Zones Consists of the grouping of cyber assets dedicated exclusively to communications, and which. As per the sans, below listed are common security zones which should be implemented. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Learn about network security architectures, including dmz, trusted, and untrusted. Security System Zones.
From www.dreamstime.com
Access Control System Alarm Zones Security System Concept site Security System Zones Consists of the grouping of cyber assets that share the same cybersecurity requirements. Here are some questions that can help guide your boundary protection analysis. A security zone is a grouping of systems and components based on their functional, logical, and physical relationship that share common security requirements. Understand how these security zones. A security zone is a portion of. Security System Zones.
From build5nines.com
IoT Security Architecture Trust Zones And Boundaries Build5Nines Security System Zones Understand how these security zones. Here are some questions that can help guide your boundary protection analysis. A security zone is a portion of a network that has specific security requirements set. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Learn about network security. Security System Zones.
From www.protectivesecurity.govt.nz
Security zones Protective Security Requirements Security System Zones By default, developed information systems should consist of at least three components (security zones): Each zone consists of a single interface or a group of interfaces, to which a security policy is. In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Learn about network security. Security System Zones.