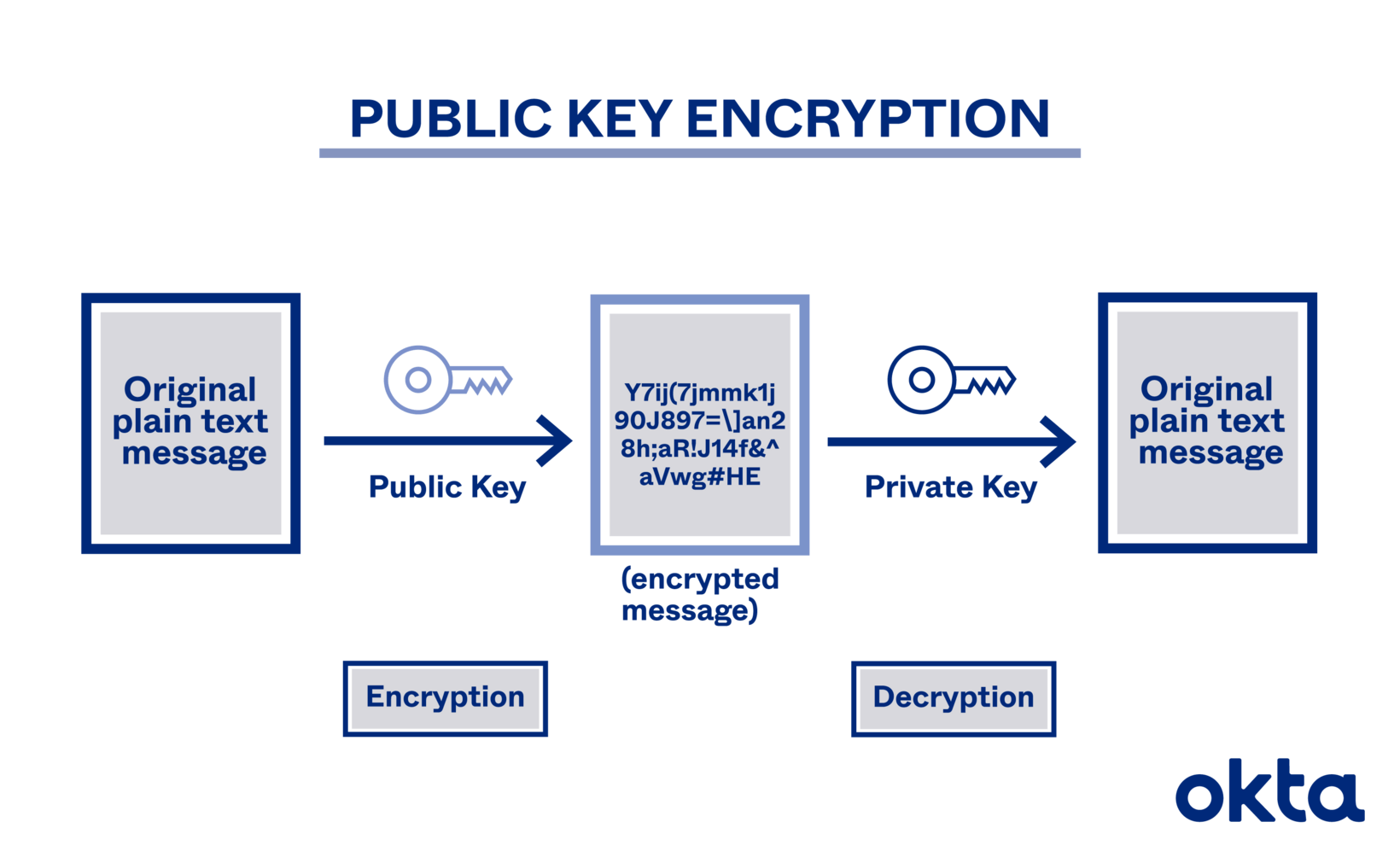
Sign Message Using Public Key . public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. public keys aren't used to encrypt, they're used to sign. to use the public key, you first want to make sure that it contains the correct information; signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it. the public key that the receiver has can be used to verify that the signature is actually being sent by the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. To do that, you verify the signature on the. We will be using secp256k1 from the.
from www.okta.com
to use the public key, you first want to make sure that it contains the correct information; the public key that the receiver has can be used to verify that the signature is actually being sent by the. The terminology is important because if something is encrypted, it. To do that, you verify the signature on the. We will be using secp256k1 from the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. public keys aren't used to encrypt, they're used to sign. signing the hash now that we've converted the message to a hash message, we can sign it with our key. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the.
Public Key Encryption What Is Public Cryptography? Okta
Sign Message Using Public Key To do that, you verify the signature on the. We will be using secp256k1 from the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. public keys aren't used to encrypt, they're used to sign. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. To do that, you verify the signature on the. to use the public key, you first want to make sure that it contains the correct information; signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities.
From slideplayer.com
DISTRIBUTED SYSTEMS Principles and Paradigms Second Edition ANDREW S Sign Message Using Public Key The terminology is important because if something is encrypted, it. the public key that the receiver has can be used to verify that the signature is actually being sent by the. signing the hash now that we've converted the message to a hash message, we can sign it with our key. We will be using secp256k1 from the.. Sign Message Using Public Key.
From goteleport.com
Comparing SSH Keys RSA, DSA, ECDSA, or EdDSA? Sign Message Using Public Key The terminology is important because if something is encrypted, it. signing the hash now that we've converted the message to a hash message, we can sign it with our key. We will be using secp256k1 from the. public keys aren't used to encrypt, they're used to sign. public key cryptography is a method of encrypting or signing. Sign Message Using Public Key.
From www.preveil.com
Public and private encryption keys PreVeil Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. We will be using secp256k1 from the. The terminology is important because if something is encrypted, it. To do that, you verify the signature on the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. . Sign Message Using Public Key.
From ssd.eff.org
A Deep Dive on EndtoEnd Encryption How Do Public Key Encryption Sign Message Using Public Key signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it. public keys aren't used to encrypt, they're used to sign. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. . Sign Message Using Public Key.
From docs.nabto.com
Public Key Authentication Nabto Edge Security Nabto Edge Documentation Sign Message Using Public Key We will be using secp256k1 from the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. to use the public key, you first want to make sure that it contains the correct information; learn how to use gpg, a public key cryptography implementation, to securely. Sign Message Using Public Key.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta Sign Message Using Public Key The terminology is important because if something is encrypted, it. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. We will be using secp256k1 from the. to use. Sign Message Using Public Key.
From weteachblockchain.org
Public and Private Keys Sign Message Using Public Key We will be using secp256k1 from the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it.. Sign Message Using Public Key.
From multimedia.report
Multimedia Journalism at UC Berkeley Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. signing the hash now that we've converted the message to a hash message, we can sign it with our key. We will be using secp256k1 from the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. To do that, you. Sign Message Using Public Key.
From www.iconfinder.com
Public, key, security, password icon Download on Iconfinder Sign Message Using Public Key to use the public key, you first want to make sure that it contains the correct information; We will be using secp256k1 from the. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. public keys aren't used to encrypt, they're used to sign. . Sign Message Using Public Key.
From wyzguyscybersecurity.com
Public Key Encryption Explained WyzGuys Cybersecurity Sign Message Using Public Key the public key that the receiver has can be used to verify that the signature is actually being sent by the. The terminology is important because if something is encrypted, it. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. to use the public. Sign Message Using Public Key.
From cryptopitha.com
Public Keys vs Nonpublic Keys What They Are & How They Work Crypto Sign Message Using Public Key The terminology is important because if something is encrypted, it. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. To do that, you verify. Sign Message Using Public Key.
From cheapsslsecurity.com
Private Key and Public Key with an Example Explained by SSLsecurity Sign Message Using Public Key learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. To do that, you verify the signature on the. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. the public key that the receiver has can be used. Sign Message Using Public Key.
From slideplayer.com
Review of Cryptography Symmetric and Asymmetric Crypto Advanced Sign Message Using Public Key public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it. To do that, you verify the. Sign Message Using Public Key.
From slideplayer.com
Cryptography Lecture ppt download Sign Message Using Public Key the public key that the receiver has can be used to verify that the signature is actually being sent by the. signing the hash now that we've converted the message to a hash message, we can sign it with our key. To do that, you verify the signature on the. public keys aren't used to encrypt, they're. Sign Message Using Public Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Sign Message Using Public Key learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. To do that, you verify the signature on the. We will be using secp256k1 from the. The terminology is important because if something is encrypted, it. signing the hash now that we've converted the message to a hash message, we can sign. Sign Message Using Public Key.
From www.pubnub.com
Create Encrypted Chat Messages Tutorial PubNub Sign Message Using Public Key signing the hash now that we've converted the message to a hash message, we can sign it with our key. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. public keys aren't used to encrypt, they're used to sign. the public key that the receiver has can be used. Sign Message Using Public Key.
From www.mdpi.com
Applied Sciences Free FullText A Novel Digital Signature Scheme Sign Message Using Public Key to use the public key, you first want to make sure that it contains the correct information; To do that, you verify the signature on the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. public keys aren't used to encrypt, they're used to sign.. Sign Message Using Public Key.
From sitesnew420.weebly.com
Can A Private Key Generate Many Public Keys sitesnew Sign Message Using Public Key We will be using secp256k1 from the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. public keys aren't used to encrypt, they're used to sign. signing the hash now that we've converted the message to a hash message, we can sign it with our key. the public key. Sign Message Using Public Key.
From www.forex.academy
Understanding Public Keys & Private Keys and Their Working Forex Academy Sign Message Using Public Key learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. the public key that the receiver has can be used to verify that the signature is actually being sent by the. signing the hash now that we've converted the message to a hash message, we can sign it with our key.. Sign Message Using Public Key.
From www.clickssl.net
What is Public Key Encryption and How Does It Works? Sign Message Using Public Key to use the public key, you first want to make sure that it contains the correct information; The terminology is important because if something is encrypted, it. To do that, you verify the signature on the. We will be using secp256k1 from the. the public key that the receiver has can be used to verify that the signature. Sign Message Using Public Key.
From linuxsimply.com
How to Create User Account in Ubuntu with Public Key Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. To do that, you verify the signature on the. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. signing the hash now that we've converted the message to a hash message, we can sign. Sign Message Using Public Key.
From www.usna.edu
SI110 Asymmetric (Public Key) Cryptography Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. The terminology is important because if something is encrypted, it. the public key that the receiver has can be used to verify that the signature is actually being sent by the. To do that, you verify the signature on the. to use the public key, you first. Sign Message Using Public Key.
From docs.catappult.io
Public Key and Inapp Social Logins Sign Message Using Public Key signing the hash now that we've converted the message to a hash message, we can sign it with our key. The terminology is important because if something is encrypted, it. We will be using secp256k1 from the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. To do that, you verify. Sign Message Using Public Key.
From www.akadia.com
Email Security using Public Key Cryptography Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. To do that, you verify the signature on the. the public key that the receiver has can be used to verify that the signature is. Sign Message Using Public Key.
From www.zoho.com
PGP Encryption Zoho Mail Sign Message Using Public Key signing the hash now that we've converted the message to a hash message, we can sign it with our key. public keys aren't used to encrypt, they're used to sign. We will be using secp256k1 from the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. the public key. Sign Message Using Public Key.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Sign Message Using Public Key to use the public key, you first want to make sure that it contains the correct information; learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. public keys aren't used to encrypt, they're used to sign. The terminology is important because if something is encrypted, it. public key cryptography. Sign Message Using Public Key.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog Sign Message Using Public Key signing the hash now that we've converted the message to a hash message, we can sign it with our key. To do that, you verify the signature on the. to use the public key, you first want to make sure that it contains the correct information; The terminology is important because if something is encrypted, it. public. Sign Message Using Public Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Sign Message Using Public Key To do that, you verify the signature on the. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. the public key that the receiver has can be used to verify that the signature is actually being sent by the. to use the public key, you first want to make sure. Sign Message Using Public Key.
From www.preveil.com
Public and private encryption keys PreVeil Sign Message Using Public Key to use the public key, you first want to make sure that it contains the correct information; learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. signing the hash now that we've converted the message to a hash message, we can sign it with our key. the public key. Sign Message Using Public Key.
From blog.mdaemon.com
Encrypting vs. Signing with OpenPGP. What’s the Difference? Sign Message Using Public Key We will be using secp256k1 from the. To do that, you verify the signature on the. the public key that the receiver has can be used to verify that the signature is actually being sent by the. public keys aren't used to encrypt, they're used to sign. learn how to use gpg, a public key cryptography implementation,. Sign Message Using Public Key.
From security.stackexchange.com
certificates Public key Infrastructure Information Security Stack Sign Message Using Public Key The terminology is important because if something is encrypted, it. signing the hash now that we've converted the message to a hash message, we can sign it with our key. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. To do that, you verify the. Sign Message Using Public Key.
From slideplayer.com
Cryptography Lecture ppt download Sign Message Using Public Key The terminology is important because if something is encrypted, it. signing the hash now that we've converted the message to a hash message, we can sign it with our key. learn how to use gpg, a public key cryptography implementation, to securely communicate and verify identities. to use the public key, you first want to make sure. Sign Message Using Public Key.
From spinningsecurity.com
Public Key Cryptography 2022 Top Benefits, Applications & More Sign Message Using Public Key To do that, you verify the signature on the. to use the public key, you first want to make sure that it contains the correct information; the public key that the receiver has can be used to verify that the signature is actually being sent by the. signing the hash now that we've converted the message to. Sign Message Using Public Key.
From www.infosec.gov.hk
InfoSec Public Key Infrastructure Sign Message Using Public Key public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. signing the hash now that we've converted the message to a hash message, we can sign it with our key. the public key that the receiver has can be used to verify that the signature. Sign Message Using Public Key.
From exowmrhbn.blob.core.windows.net
ServU Public Key Authentication at Lottie Rogers blog Sign Message Using Public Key public keys aren't used to encrypt, they're used to sign. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. to use the public key, you first want to make sure that it contains the correct information; The terminology is important because if something is. Sign Message Using Public Key.