Profiling Threat Actors . Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. In this article, which is a starting point in our cybersecurity journey, we will focus on. The actors can range from. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're.
from blackcell.io
The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. The actors can range from. In this article, which is a starting point in our cybersecurity journey, we will focus on. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face.
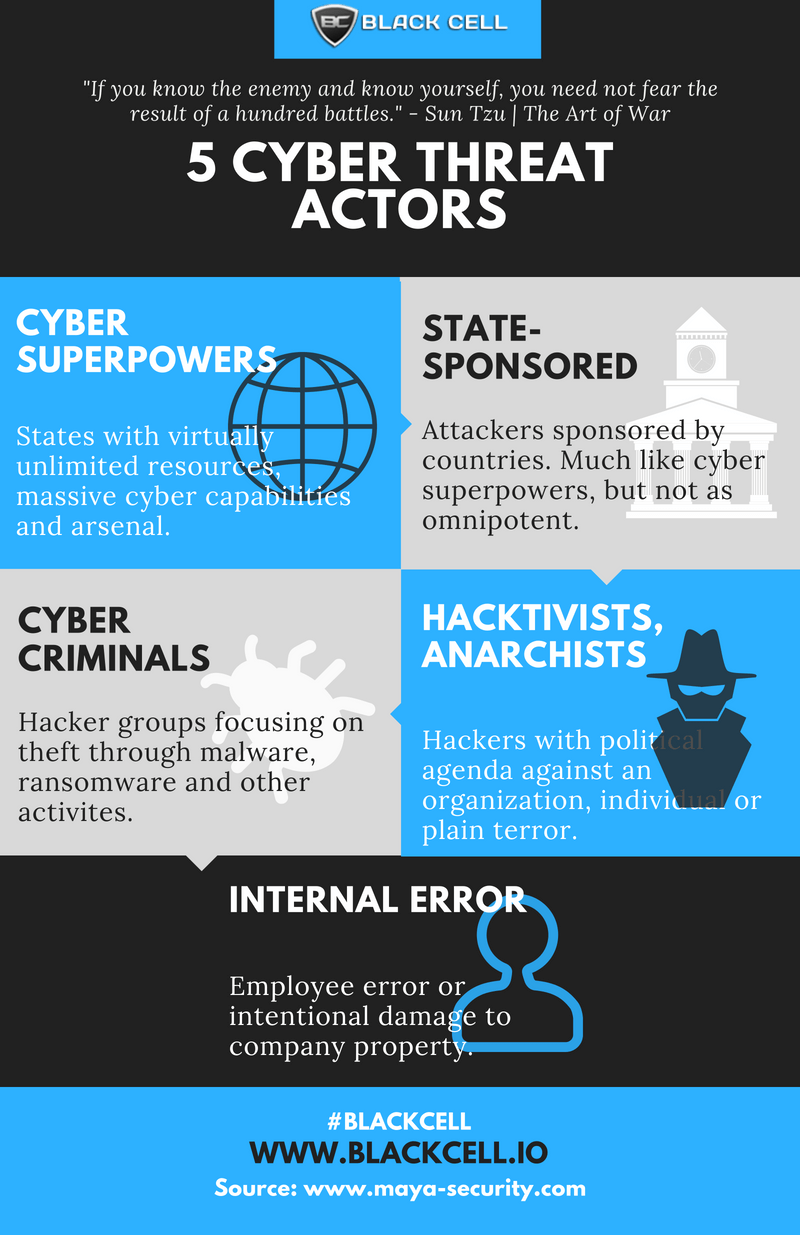
5 Cyber Threat Actors Infographic Black Cell
Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. The actors can range from. In this article, which is a starting point in our cybersecurity journey, we will focus on. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack.
From cybersecurity-why-for-me.blogspot.com
Cyber Security (Why For Me?) Threat Actors Profiling Threat Actors The actors can range from. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. In this article, which is a starting point in our cybersecurity journey, we will focus. Profiling Threat Actors.
From kravensecurity.com
Threat Profiling How to Understand Hackers and Their TTPs Kraven Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the. Profiling Threat Actors.
From cyble.com
What is a Cyber Threat Actor? Types of Threat Actors Cyble Profiling Threat Actors The actors can range from. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Threat. Profiling Threat Actors.
From www.linkedin.com
How to Profile Threat Actors in Cybersecurity Profiling Threat Actors Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics. Profiling Threat Actors.
From www.slideserve.com
PPT Prevention of Data Breach PowerPoint Presentation, free download Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the. Profiling Threat Actors.
From it.sentinelone.com
Threat Actor Basics Understanding The 5 Main Threat Types SentinelOne Profiling Threat Actors In this article, which is a starting point in our cybersecurity journey, we will focus on. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat actor profiling is the process of identifying and analyzing the characteristics,. Profiling Threat Actors.
From securityboulevard.com
Cybersecurity AI Threat Actor Profiling Provides Instant Insights Profiling Threat Actors Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing. Profiling Threat Actors.
From www.mandiant.fr
Cyber Threat Profile Cyber Threat Actors and Tactics Insights Profiling Threat Actors The actors can range from. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. In this. Profiling Threat Actors.
From webz.io
How to Use Dark Data for Threat Actor Profiling? z.io Profiling Threat Actors Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. In this article, which is a starting point in our cybersecurity journey, we will focus on. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and. Profiling Threat Actors.
From mediasonar.com
Understanding the Threat Actor's Motivation Blog Media Sonar Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. The actors can range from. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Using a. Profiling Threat Actors.
From www.proofpoint.com
Understanding Threat Actors & Their Objectives TA Tracking Profiling Threat Actors The actors can range from. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. In this article, which is. Profiling Threat Actors.
From flare.io
Threat Actors The Definitive 2023 Guide to Cybercriminals Flare Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. In this article, which is a starting point in our cybersecurity journey, we will focus on. Threat actor profiling is the process of identifying and analyzing the characteristics,. Profiling Threat Actors.
From www.securitymadesimple.org
Top 7 Popular Cyber Threat Models for identifying threat actors Profiling Threat Actors Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. In this article, which is a starting point in our cybersecurity journey, we will focus. Profiling Threat Actors.
From www.semanticscholar.org
Creating a Threat Profile for Your Organization Semantic Scholar Profiling Threat Actors In this article, which is a starting point in our cybersecurity journey, we will focus on. The actors can range from. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools. Profiling Threat Actors.
From medium.com
THREAT PROFILING INTELBROKER THREAT ACTOR by John C Jul, 2024 Medium Profiling Threat Actors Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The actors can range from. In this article, which is a starting point in our. Profiling Threat Actors.
From securedebug.com
Threat Actor Profiling Understanding the Key Elements of Cybersecurity Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. The actors can range from. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Using a. Profiling Threat Actors.
From www.criticalstart.com
What is a Threat Actor? Critical Start Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics. Profiling Threat Actors.
From www.securiwiser.com
The different types of threat actors Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. In this article, which is a starting point in our cybersecurity journey, we will focus on. Using a probabilistic model to predict the likely threat. Profiling Threat Actors.
From securedebug.com
Unveiling the Intricacies of Threat Actor Profiling Secure Debug Profiling Threat Actors In this article, which is a starting point in our cybersecurity journey, we will focus on. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. The actors can range. Profiling Threat Actors.
From stixproject.github.io
Identifying a Threat Actor Profile STIX Project Documentation Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. In this article, which is a starting point in our cybersecurity journey, we will focus on. Using a probabilistic model to predict the likely threat. Profiling Threat Actors.
From blackcell.io
5 Cyber Threat Actors Infographic Black Cell Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors. Profiling Threat Actors.
From www.reddit.com
GitHub curatedintel/ThreatActorProfileGuide The Threat Actor Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. In this article, which is a starting point in our cybersecurity journey, we will focus on. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations,. Profiling Threat Actors.
From www.ukcybersecurity.co.uk
THREAT ACTOR AND TYPES UK Cyber Security Group Ltd Profiling Threat Actors Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and. Profiling Threat Actors.
From www.youtube.com
AdversaryThreat Infrastructure Threat Actor Profiles and Tools YouTube Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The actors can range from. Threat actor profiling is the. Profiling Threat Actors.
From kravensecurity.com
Threat Profiling How to Understand Hackers and Their TTPs Kraven Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. In this article, which is a starting point in our cybersecurity journey, we will focus on. The term tactics, techniques and procedures (ttp) describes the behavior of a. Profiling Threat Actors.
From phxtechsol.com
Threat Actor Basics Understanding the 5 Main Threat Types Phoenix Profiling Threat Actors Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. The actors can range from. Using a probabilistic model to predict the likely threat actor behind. Profiling Threat Actors.
From www.linkedin.com
Cyber Threat Profiling Understanding the Different Threat Actors Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics. Profiling Threat Actors.
From www.sentinelone.com
What is a Threat Actor? Types & Examples Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. The actors can range from. Threat. Profiling Threat Actors.
From flare.io
Cybersecurity AI Threat Actor Profiling Provides Instant Insights Flare Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The actors can range from. Threat. Profiling Threat Actors.
From rechargevodafone.co.uk
What Are The 5 Types Of Threat Actors? Protect Your Business From Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The actors can range from. In this article, which is a starting point in our cybersecurity journey, we will focus on. Threat actor profiling is the process of. Profiling Threat Actors.
From www.youtube.com
Understanding Threat Actors Managed Attribution Threat Modeling YouTube Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. The actors can range from. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually. Profiling Threat Actors.
From mediasonar.com
Understanding the Threat Actor's Motivation Blog Media Sonar Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. In this article, which is a starting point in our cybersecurity journey, we will focus on. Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools. Profiling Threat Actors.
From www.proofpoint.com
Understanding Threat Actors & Their Objectives TA Tracking Profiling Threat Actors The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. Creating a threat. Profiling Threat Actors.
From flare.io
Flare Empowers Cybersecurity Analysts with Threat Actor Profiling Profiling Threat Actors Using a probabilistic model to predict the likely threat actor behind an attack removes the need for analysts to manually evaluate and compare techniques and tools with known behaviors with threat groups. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Threat actor profiling is the process. Profiling Threat Actors.
From pcsi.nl
Automated Threat Actor Profiling Events Profiling Threat Actors Creating a threat profile helps organizations identify threat actors, their likely targets and which types of attacks they're. In this article, which is a starting point in our cybersecurity journey, we will focus on. Threat actor profiling is the process of identifying and analyzing the characteristics, motivations, and tactics of individuals or groups that pose a. The term tactics, techniques. Profiling Threat Actors.