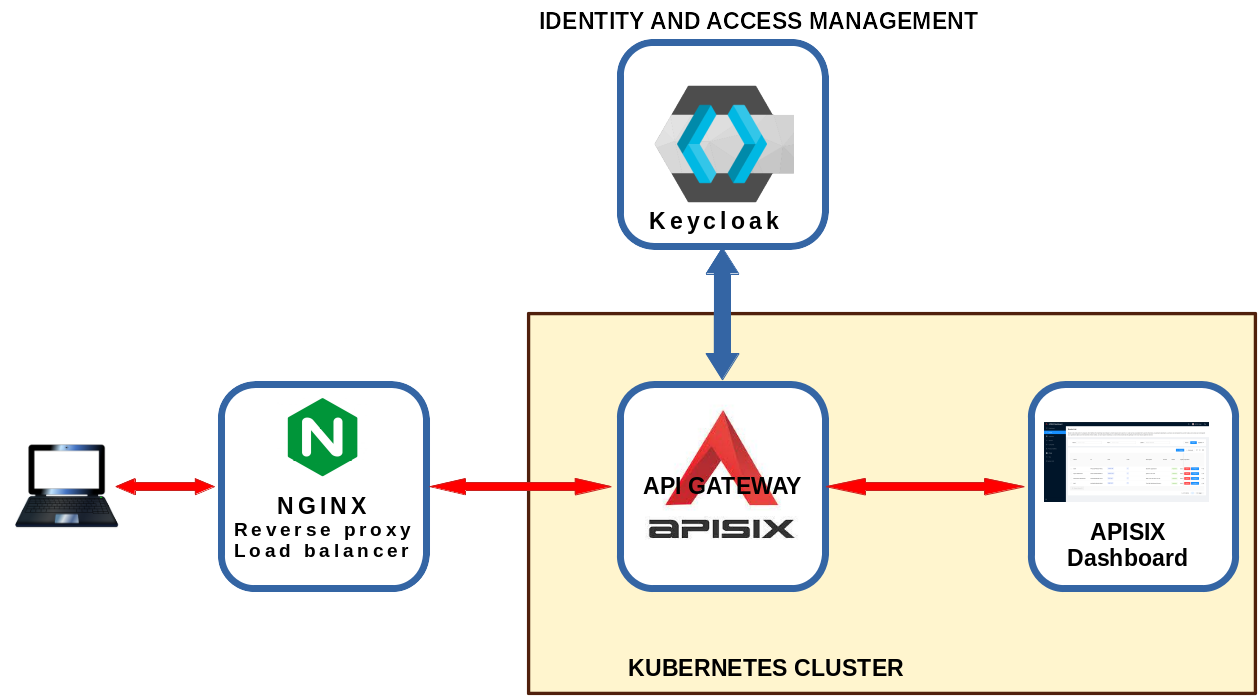
Keycloak Authentication Diagram . This article will explore setting up robust. keycloak and use these tokens to authenticate users. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation.
from apisix.apache.org
keycloak and use these tokens to authenticate users. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. This article will explore setting up robust.
Accessing APISIXDashboard from Everywhere with Keycloak Authentication
Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. This chapter will focus on the different authorization strategies.
From keycloak.discourse.group
Defining custom OIDC provider with delegating authentication to another Keycloak Authentication Diagram In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From www.amazonaws.cn
Keycloak on AWS AWS Solutions Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. This article will explore setting up robust. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From www.vrogue.co
Step By Step Guide Setting Up Keycloak Oauth2 In Angu vrogue.co Keycloak Authentication Diagram This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From www.mdpi.com
Sensors Free FullText Applying Spring Security Framework with Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From keycloak.discourse.group
Conditional Authenticator Getting advice Keycloak Keycloak Authentication Diagram In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. This article will explore setting up robust. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Diagram This article will explore setting up robust. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From login-master.com
Keycloak als Identity Broker Login Master Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From www.keycloak.org
Authorization Services Guide Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. Keycloak Authentication Diagram.
From clouddocs.f5.com
Step 7 Set up authentication and authorization Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From documentation.censhare.com
Configure Keycloak with LDAP Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From developers.redhat.com
How to implement single signout in Keycloak with Spring Boot Red Hat Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From admin.dominodatalab.com
keycloak upstream idp trust Keycloak Authentication Diagram This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From walkingtree.tech
Introduction to Keycloak and the Need for Containerization Keycloak Authentication Diagram In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. keycloak and use these tokens to authenticate users. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From developers.redhat.com
Keycloak Core concepts of open source identity and access management Keycloak Authentication Diagram This article will explore setting up robust. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. Keycloak Authentication Diagram.
From younite.us
Configuring SSO and OAuth with Keycloak Keycloak Authentication Diagram In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. keycloak and use these tokens to authenticate users. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From sciencegateways.org
sciencegateways Tech Blog Using Keycloak to Provide Authentication Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From www.agile-solutions.ch
Keycloak agilesolution Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Diagram This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. Keycloak Authentication Diagram.
From www.vrogue.co
Authentication With Keycloak Openid Connec vrogue.co Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From medium.com
Facebook as Identity Provider in Keycloak by Didelotkev Medium Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Authentication Diagram This article will explore setting up robust. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From www.cncf.io
Securing Cloud Native Microservices with RoleBased Access Control Keycloak Authentication Diagram This article will explore setting up robust. This chapter will focus on the different authorization strategies. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From developers.redhat.com
Keycloak Core concepts of open source identity and access management Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. This article will explore setting up robust. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From developers.redhat.com
Docker Authentication with Keycloak Red Hat Developer Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Keycloak Authentication Diagram.
From github.com
GitHub shinyay/springkeycloakauthzserver Embedded Keycloak Server Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. This article will explore setting up robust. Keycloak Authentication Diagram.
From jpassing.com
Using a Google Cloud service account to authenticate to KeyCloak Keycloak Authentication Diagram This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From dxojsauju.blob.core.windows.net
Keycloak Google Authentication at Connie Emmett blog Keycloak Authentication Diagram In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. keycloak and use these tokens to authenticate users. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From stackoverflow.com
authentication Keycloak Authorization between services and the Keycloak Authentication Diagram keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. This chapter will focus on the different authorization strategies. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.
From www.vrogue.co
Authentication Flows Explained Beyond Identity vrogue.co Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. This article will explore setting up robust. Keycloak Authentication Diagram.
From www.redpill-linpro.com
Get started with OpenID Connect and Keycloak /techblog Keycloak Authentication Diagram This chapter will focus on the different authorization strategies. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. being based on keycloak authentication server, you can obtain attributes from identities and runtime. This article will explore setting up robust. Keycloak Authentication Diagram.
From awesomeopensource.com
Keycloak On Aws Keycloak Authentication Diagram being based on keycloak authentication server, you can obtain attributes from identities and runtime. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This chapter will focus on the different authorization strategies. This article will explore setting up robust. keycloak and use these tokens to authenticate users. Keycloak Authentication Diagram.
From www.tremolosecurity.com
Authentication Comparing Solutions Keycloak Authentication Diagram This article will explore setting up robust. This chapter will focus on the different authorization strategies. keycloak and use these tokens to authenticate users. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. being based on keycloak authentication server, you can obtain attributes from identities and runtime. Keycloak Authentication Diagram.