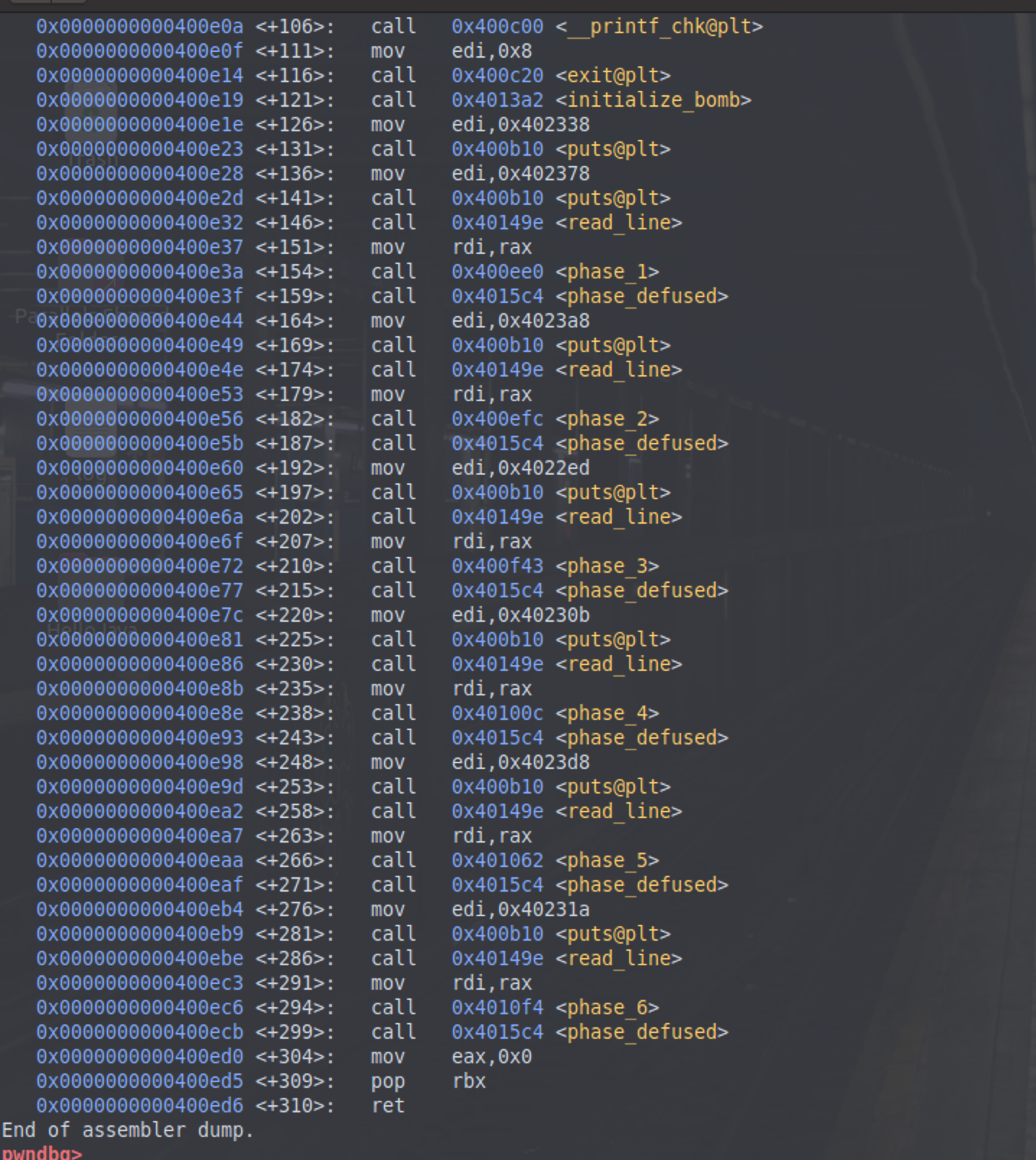
Bomb Lab Phase 1 . Solve a total of 6 phases to defuse the bomb. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Enter a random string and then. Become familiar with linux vm and linux. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Each phase has a password/key that is solved through the hints found within the assembly code. We enter gdb, set a breakpoint at the phase 1. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Get started on the path to defeating dr. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret.
from la13x.github.io
Then we take a look at the assembly code above, we see one register eax and an address 0x402400. We enter gdb, set a breakpoint at the phase 1. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Solve a total of 6 phases to defuse the bomb. Get started on the path to defeating dr. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Each phase has a password/key that is solved through the hints found within the assembly code. Enter a random string and then. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string.
Bomb Lab Alex's blog
Bomb Lab Phase 1 Solve a total of 6 phases to defuse the bomb. We enter gdb, set a breakpoint at the phase 1. Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Solve a total of 6 phases to defuse the bomb. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Get started on the path to defeating dr. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Each phase has a password/key that is solved through the hints found within the assembly code. Become familiar with linux vm and linux. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Enter a random string and then. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call.
From www.slideserve.com
PPT Assembly and Bomb Lab PowerPoint Presentation, free download ID6178632 Bomb Lab Phase 1 Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Become familiar with linux vm and linux. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we. Bomb Lab Phase 1.
From www.ppmy.cn
讲解pwngdb的用法,以csapp的bomb lab phase_1为例 Bomb Lab Phase 1 Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Solve a total. Bomb Lab Phase 1.
From la13x.github.io
Bomb Lab Alex's blog Bomb Lab Phase 1 So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. We enter gdb, set a breakpoint at the phase 1. Solve a total of 6 phases to defuse the bomb. Each phase has a password/key that is solved through the hints found within the assembly code. Become familiar. Bomb Lab Phase 1.
From www.chegg.com
Solved this is the binary bomb lab phase 1 assembly code. . Bomb Lab Phase 1 Solve a total of 6 phases to defuse the bomb. We enter gdb, set a breakpoint at the phase 1. Enter a random string and then. Each phase has a password/key that is solved through the hints found within the assembly code. Then we take a look at the assembly code above, we see one register eax and an address. Bomb Lab Phase 1.
From omarshehata11.github.io
Binary Bomb Lab phase 1 0xEFE4 Bomb Lab Phase 1 Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Solve a total of 6 phases to defuse the bomb. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Learn how to use gdb to solve the first three phases. Bomb Lab Phase 1.
From www.chegg.com
Solved Please help me solve binanary bomb lab phase 1 the Bomb Lab Phase 1 Each phase has a password/key that is solved through the hints found within the assembly code. Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. We enter gdb, set a breakpoint at the. Bomb Lab Phase 1.
From www.youtube.com
CSCI2467 Lecture 15. Bomb Lab Intro + Phase 1 YouTube Bomb Lab Phase 1 Solve a total of 6 phases to defuse the bomb. Each phase has a password/key that is solved through the hints found within the assembly code. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Then we. Bomb Lab Phase 1.
From arthals.ink
更适合北大宝宝体质的 Bomb Lab 踩坑记 Arthals' ink Bomb Lab Phase 1 Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Enter a random string and then. Get started on the path to defeating dr. Each phase has a password/key that is solved through the hints found. Bomb Lab Phase 1.
From www.slideserve.com
PPT Assembly and Bomb Lab PowerPoint Presentation, free download ID1890494 Bomb Lab Phase 1 Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Enter a random. Bomb Lab Phase 1.
From www.slideserve.com
PPT System Level Programming Software College of SCU PowerPoint Presentation ID9647471 Bomb Lab Phase 1 We enter gdb, set a breakpoint at the phase 1. Get started on the path to defeating dr. Each phase has a password/key that is solved through the hints found within the assembly code. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Learn how to. Bomb Lab Phase 1.
From www.slideserve.com
PPT Assembly and Bomb Lab PowerPoint Presentation, free download ID6178632 Bomb Lab Phase 1 Get started on the path to defeating dr. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step. Bomb Lab Phase 1.
From www.youtube.com
CMU Binary Bomb Lab Phase 1 Example in WinDbg Architecture 1001 x8664 Assembly YouTube Bomb Lab Phase 1 Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Become familiar with linux vm and linux. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Solve a total of 6 phases to defuse the bomb. Learn how to use gdb to solve the first three phases. Bomb Lab Phase 1.
From www.slideserve.com
PPT 15213 Recitation Bomb Lab PowerPoint Presentation, free download ID8928172 Bomb Lab Phase 1 Get started on the path to defeating dr. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Solve a total. Bomb Lab Phase 1.
From omarshehata11.github.io
Binary Bomb Lab phase 1 0xEFE4 Bomb Lab Phase 1 Become familiar with linux vm and linux. Get started on the path to defeating dr. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. We enter gdb, set a. Bomb Lab Phase 1.
From blog.csdn.net
csapp深入理解计算机系统 bomb lab(1)phase_1_深入理解计算机系统csappCSDN博客 Bomb Lab Phase 1 Each phase has a password/key that is solved through the hints found within the assembly code. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Solve a total of 6 phases to defuse the bomb. We enter. Bomb Lab Phase 1.
From omarshehata11.github.io
Binary Bomb Lab phase 1 0xEFE4 Bomb Lab Phase 1 Become familiar with linux vm and linux. We enter gdb, set a breakpoint at the phase 1. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Each phase has a password/key that is solved through the hints found within the assembly code. Get started on the path. Bomb Lab Phase 1.
From 0xf444.medium.com
x86 Binary Bomb Lab Phase 1. Hello World! Today we’re going to solve… by Omar Mokhtar Medium Bomb Lab Phase 1 Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Enter a random string and then. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Become familiar with linux vm and linux. Get started on the path to defeating dr. We enter gdb, set a breakpoint at. Bomb Lab Phase 1.
From blog.csdn.net
CSAPP BOMB LAB part1_call 和 callqCSDN博客 Bomb Lab Phase 1 Become familiar with linux vm and linux. Each phase has a password/key that is solved through the hints found within the assembly code. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. We enter gdb, set a breakpoint at the phase 1. Solve a total of. Bomb Lab Phase 1.
From arthals.ink
更适合北大宝宝体质的 Bomb Lab 踩坑记 Arthals' ink Bomb Lab Phase 1 Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Each phase has a password/key that is solved through the hints found within the assembly code. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Become familiar with linux vm. Bomb Lab Phase 1.
From github.com
BombLab/Phase1 at master · sc2225/BombLab · GitHub Bomb Lab Phase 1 Enter a random string and then. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Each phase has a password/key that is solved through the hints found within the assembly code. Solve a total of 6 phases to defuse the bomb. We enter gdb, set a breakpoint at the phase 1. So by stepping. Bomb Lab Phase 1.
From 7orvs.github.io
Bomb Lab 0x70RVS Bomb Lab Phase 1 Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. We enter gdb, set a breakpoint at the phase 1. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Learn how to work through phase 1 of bryant and o'hallaron's binary. Bomb Lab Phase 1.
From www.youtube.com
X86 Bomb lab phase 1 [Hebrew] YouTube Bomb Lab Phase 1 Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret.. Bomb Lab Phase 1.
From blog.csdn.net
BOMB lab(phase_0 and phase_1)_dr. evil incorporated (the perpetrator) hereby graCSDN博客 Bomb Lab Phase 1 Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Become familiar with linux vm and linux. Get started on the path to defeating dr. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Learn how to use gdb to solve the first three phases. Bomb Lab Phase 1.
From zpalexander.com
Binary Bomb Lab Phase 1 Bomb Lab Phase 1 We enter gdb, set a breakpoint at the phase 1. Become familiar with linux vm and linux. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Then we take a look at the assembly code above, we. Bomb Lab Phase 1.
From zpalexander.com
Binary Bomb Lab Phase 1 Bomb Lab Phase 1 Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. We enter gdb, set a breakpoint at the phase 1. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Enter a random string and then. Get started on the. Bomb Lab Phase 1.
From www.youtube.com
Bomb Lab Phase 1Hợp ngữ và mã máy YouTube Bomb Lab Phase 1 Enter a random string and then. Get started on the path to defeating dr. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Solve a total of 6 phases to. Bomb Lab Phase 1.
From blog.csdn.net
BOMB lab(phase_0 and phase_1)_dr. evil incorporated (the perpetrator) hereby graCSDN博客 Bomb Lab Phase 1 Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Enter a random string and then. Each phase has a password/key that is solved through the hints found. Bomb Lab Phase 1.
From blog.csdn.net
csapp深入理解计算机系统 bomb lab(1)phase_1_深入理解计算机系统csappCSDN博客 Bomb Lab Phase 1 Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Become familiar with linux vm and linux. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary. Bomb Lab Phase 1.
From www.youtube.com
Bomb Lab Phase 1 YouTube Bomb Lab Phase 1 Solve a total of 6 phases to defuse the bomb. So by stepping over to reach the call of phase_1 function (use ni command in gdb), we noticed that after the call. Enter a random string and then. We enter gdb, set a breakpoint at the phase 1. Learn how to use gdb to solve the first three phases of. Bomb Lab Phase 1.
From blog.csdn.net
csapp bomb lab phase_1_bomb lab phase1CSDN博客 Bomb Lab Phase 1 Then we take a look at the assembly code above, we see one register eax and an address 0x402400. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Become familiar with linux vm and linux. Solve a total of 6 phases to defuse the bomb. We enter gdb, set a breakpoint at. Bomb Lab Phase 1.
From blog.csdn.net
CSAPP Lab2 实验记录 Bomb Lab(Phase 1 Phase 6详细解答 + Secret Phase彩蛋解析)_bomblab所有答案总结CSDN博客 Bomb Lab Phase 1 Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. Solve a total of 6 phases to defuse the bomb. Enter a random string and then. Become familiar with linux vm and linux. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. Learn how to work through. Bomb Lab Phase 1.
From www.freesion.com
深入理解操作系统实验——bomb lab(phase_1) 灰信网(软件开发博客聚合) Bomb Lab Phase 1 We enter gdb, set a breakpoint at the phase 1. Become familiar with linux vm and linux. Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. So by stepping over to reach the call of phase_1 function. Bomb Lab Phase 1.
From blog.csdn.net
csapp深入理解计算机系统 bomb lab(1)phase_4_csapp栈溢出攻击phase4CSDN博客 Bomb Lab Phase 1 Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that involves finding the correct. Get started on the path to defeating dr. Learn how to reverse engineer a binary bomb program that explodes if you enter the wrong string. So by stepping over to reach the call of phase_1 function (use. Bomb Lab Phase 1.
From 7orvs.github.io
Bomb Lab 0x70RVS Bomb Lab Phase 1 Learn how to work through phase 1 of bryant and o'hallaron's binary bomb lab step by step. We enter gdb, set a breakpoint at the phase 1. Enter a random string and then. Each phase has a password/key that is solved through the hints found within the assembly code. Follow the detailed walkthrough of each phase, from 1 to 6,. Bomb Lab Phase 1.
From www.freesion.com
深入理解操作系统实验——bomb lab(phase_1) 灰信网(软件开发博客聚合) Bomb Lab Phase 1 Follow the detailed walkthrough of each phase, from 1 to 6, and find the secret. We enter gdb, set a breakpoint at the phase 1. Solve a total of 6 phases to defuse the bomb. Enter a random string and then. Learn how to use gdb to solve the first three phases of cmu's bomb lab, a binary executable that. Bomb Lab Phase 1.