Server Access Control . This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. There are two main types of access lists: An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acls are the oldest type of access control lists. Standard acl and extended acl. They are used to filter network traffic by examining the source ip address in a packet. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. Management of access control involves maintaining and updating the access control system. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This includes defining and updating access policies, managing user credentials, onboarding and.
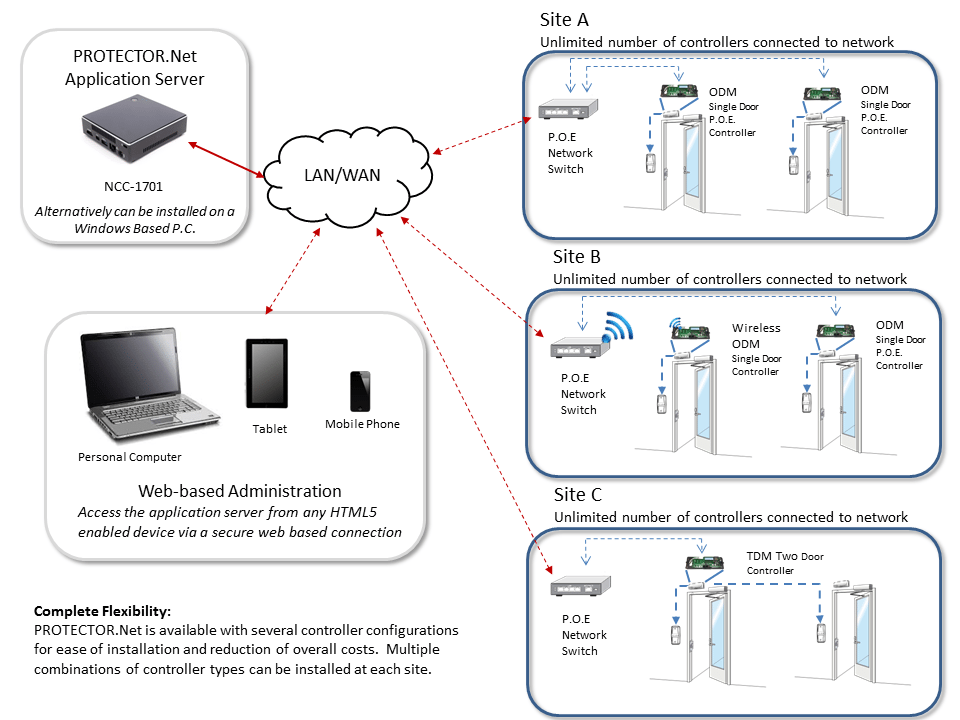
from protectorsecurity.net
Management of access control involves maintaining and updating the access control system. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acl and extended acl. They are used to filter network traffic by examining the source ip address in a packet. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. There are two main types of access lists: This includes defining and updating access policies, managing user credentials, onboarding and. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Standard acls are the oldest type of access control lists.
Access Control Topology Home Security Systems KW Area
Server Access Control Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. They are used to filter network traffic by examining the source ip address in a packet. Standard acls are the oldest type of access control lists. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. Standard acl and extended acl. Management of access control involves maintaining and updating the access control system. There are two main types of access lists: This includes defining and updating access policies, managing user credentials, onboarding and. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms.
From ip-integra.com
IPINTEGRA Access Control solution Server Access Control This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Standard acl and extended acl. Management of access control involves maintaining and updating the access control system. This includes defining and updating access policies, managing user credentials, onboarding and. There are two main types of access lists: This article describes access. Server Access Control.
From cyberhoot.com
Access Control Mechanism CyberHoot Server Access Control There are two main types of access lists: This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. They are used to filter network traffic by examining the source ip. Server Access Control.
From www.itechguides.com
Routing and Remote Access Windows Server 2016 Install Remote Access Server Access Control Management of access control involves maintaining and updating the access control system. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This overview topic for the it professional describes dynamic access control. Server Access Control.
From www.conceptdraw.com
Network Security Server Access Control This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control system. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This article describes access control in windows, which is the process of authorizing users, groups, and computers. Server Access Control.
From maynardpestcontrolhickoryncbusurei.blogspot.com
Maynard Pest Control Hickory Nc Server Rack Access Control Server Access Control They are used to filter network traffic by examining the source ip address in a packet. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This includes defining and updating access policies, managing. Server Access Control.
From dirteam.com
New features in Active Directory Domain Services in Windows Server 2012 Server Access Control They are used to filter network traffic by examining the source ip address in a packet. Standard acl and extended acl. There are two main types of access lists: This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control system. Access control mechanisms contribute to the physical. Server Access Control.
From www.cisco.com
Cisco Secure Access Control System Products & Services Cisco Server Access Control They are used to filter network traffic by examining the source ip address in a packet. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acl and extended acl. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This includes. Server Access Control.
From getsafeandsound.com
Access Control Systems The Complete Guide for 2023 Server Access Control This includes defining and updating access policies, managing user credentials, onboarding and. Standard acl and extended acl. Standard acls are the oldest type of access control lists. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. There are two main types of access lists: This overview. Server Access Control.
From www.ionos.com
File Server What is a file server and how does it work? IONOS Server Access Control There are two main types of access lists: Management of access control involves maintaining and updating the access control system. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,.. Server Access Control.
From www.alibaba.com
Factory 2 Door Server Access Control Board Buy Access Control Server Access Control An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acls are the oldest type of access control lists. There are two main types of access lists: This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. Access control. Server Access Control.
From www.techtarget.com
Secure data in the cloud with encryption and access controls TechTarget Server Access Control This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control system. There are two main types of access lists: This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This article describes access control in windows, which is. Server Access Control.
From cabledan.co.uk
Server Room Access ControlCabledan 01923 624120 Server Access Control They are used to filter network traffic by examining the source ip address in a packet. This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control system. There are two main types of access lists: Standard acl and extended acl. This overview topic for the it professional. Server Access Control.
From progeny.co.uk
Control access with Progeny Online Access Control Systems Server Access Control They are used to filter network traffic by examining the source ip address in a packet. There are two main types of access lists: This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Management of access control involves maintaining and updating the access control system. Standard acl and extended acl.. Server Access Control.
From www.locksmithjournal.co.uk
Videx Launches New Server Access Control System Locksmith Journal Server Access Control Standard acl and extended acl. This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control system. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. There are two main types of access lists:. Server Access Control.
From www.emkablog.co.uk
Server rack access control systems from EMKA Server Access Control Standard acl and extended acl. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Standard acls are the oldest type of access control lists. There are two main types of access lists: An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. This. Server Access Control.
From sssengineeringbd.com
Access Control System with all type of Hardware and Software Solution Server Access Control An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acls are the oldest type of access control lists. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. They are used to filter network traffic by examining the source ip address. Server Access Control.
From medium.com
Access Control Server in a Connected World by FriendlyTechnologies Server Access Control There are two main types of access lists: This includes defining and updating access policies, managing user credentials, onboarding and. Standard acls are the oldest type of access control lists. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Access control mechanisms contribute to the physical security of cloud infrastructure. Server Access Control.
From systemsurveyor.com
A Guide to Commercial Access Control Systems with PDK Server Access Control Standard acl and extended acl. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. They are used to filter network traffic by examining the source ip address in a packet. There are two main types of access lists: This overview topic for the it professional describes. Server Access Control.
From www.juniper.net
Control Network Access Using Device Identity Authentication Juniper Server Access Control This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Management of access control involves maintaining and updating the access control system. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acl and extended acl. Access control mechanisms contribute to the physical. Server Access Control.
From docs.oracle.com
How Access Control Works (Oracle Server 7.0.9 Administrator Server Access Control An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acl and extended acl. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. There are two main types of access lists: They are used to filter network traffic by examining the. Server Access Control.
From getsafeandsound.com
Difference Between Cloud & Server Access Control Full Guide Server Access Control This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. They are used to filter network traffic by examining the source ip address in a packet. There are two main types of access lists: Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers. Server Access Control.
From learn.microsoft.com
Security principals Microsoft Learn Server Access Control This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. This includes defining and updating access policies, managing user credentials, onboarding and. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Standard acl and extended acl. Standard. Server Access Control.
From www.portnox.com
Cyber Security Essential 2 802.1x Network Access Control Portnox Server Access Control This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating. Server Access Control.
From newabel.en.alibaba.com
WaterproofData Server Access Control Lock, View access control Server Access Control Standard acl and extended acl. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Management of access control involves maintaining and updating the access control system. Standard acls are the oldest type. Server Access Control.
From dicsan.com
Access control server Dicsan Technology Server Access Control This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. They are used to filter network traffic by examining the source ip address in a packet. This includes defining and updating access policies, managing user credentials, onboarding and. This overview topic for the it professional describes dynamic. Server Access Control.
From www.ltsecurityinc.com
serverbasedaccesscontrolsolution Server Access Control Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Standard acls are the oldest type of access control lists. This article describes access control in windows, which is the process. Server Access Control.
From www.eztcp.com
Applications Security Server Access Control Management of access control involves maintaining and updating the access control system. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. This article describes access control in windows, which is. Server Access Control.
From protectorsecurity.net
Access Control Topology Home Security Systems KW Area Server Access Control An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This includes defining and updating access policies, managing user credentials, onboarding and. Management of access control involves maintaining and updating the access control. Server Access Control.
From www.dnsstuff.com
How to Install, Access, and Connect to Remote Server Administration Server Access Control They are used to filter network traffic by examining the source ip address in a packet. There are two main types of access lists: Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. Management of access control involves maintaining and updating the access control system. Standard acl and extended. Server Access Control.
From vectorified.com
Access Control Icon at Collection of Access Control Server Access Control Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. This overview topic for the it professional describes dynamic access control and its associated elements, which were. Server Access Control.
From support.supremainc.com
Technical Support Suprema Server Access Control There are two main types of access lists: Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. Management of access control involves maintaining and updating the access control system. This includes defining and updating access policies, managing user credentials, onboarding and. This overview topic for the it professional describes. Server Access Control.
From ar.inspiredpencil.com
Data Center Rack Server Access Control They are used to filter network traffic by examining the source ip address in a packet. An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. Standard acl and extended acl. This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the. Server Access Control.
From platinumsystems.co.uk
Remote Access Platinum Systems Server Access Control This article describes access control in windows, which is the process of authorizing users, groups, and computers to access objects on the network. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and. Server Access Control.
From www.youtube.com
Implementación de Dynamic Access Control con Windows Server 2012 R2 Server Access Control Management of access control involves maintaining and updating the access control system. Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. This overview topic for the it professional describes dynamic access control and its associated elements, which were introduced in. An organization's choice often hinges on factors like its. Server Access Control.
From www.craiyon.com
Server access control on Craiyon Server Access Control Access control mechanisms contribute to the physical security of cloud infrastructure by limiting access to data centers and server rooms. There are two main types of access lists: An organization's choice often hinges on factors like its size, it resources at its disposal (both expertise,. They are used to filter network traffic by examining the source ip address in a. Server Access Control.