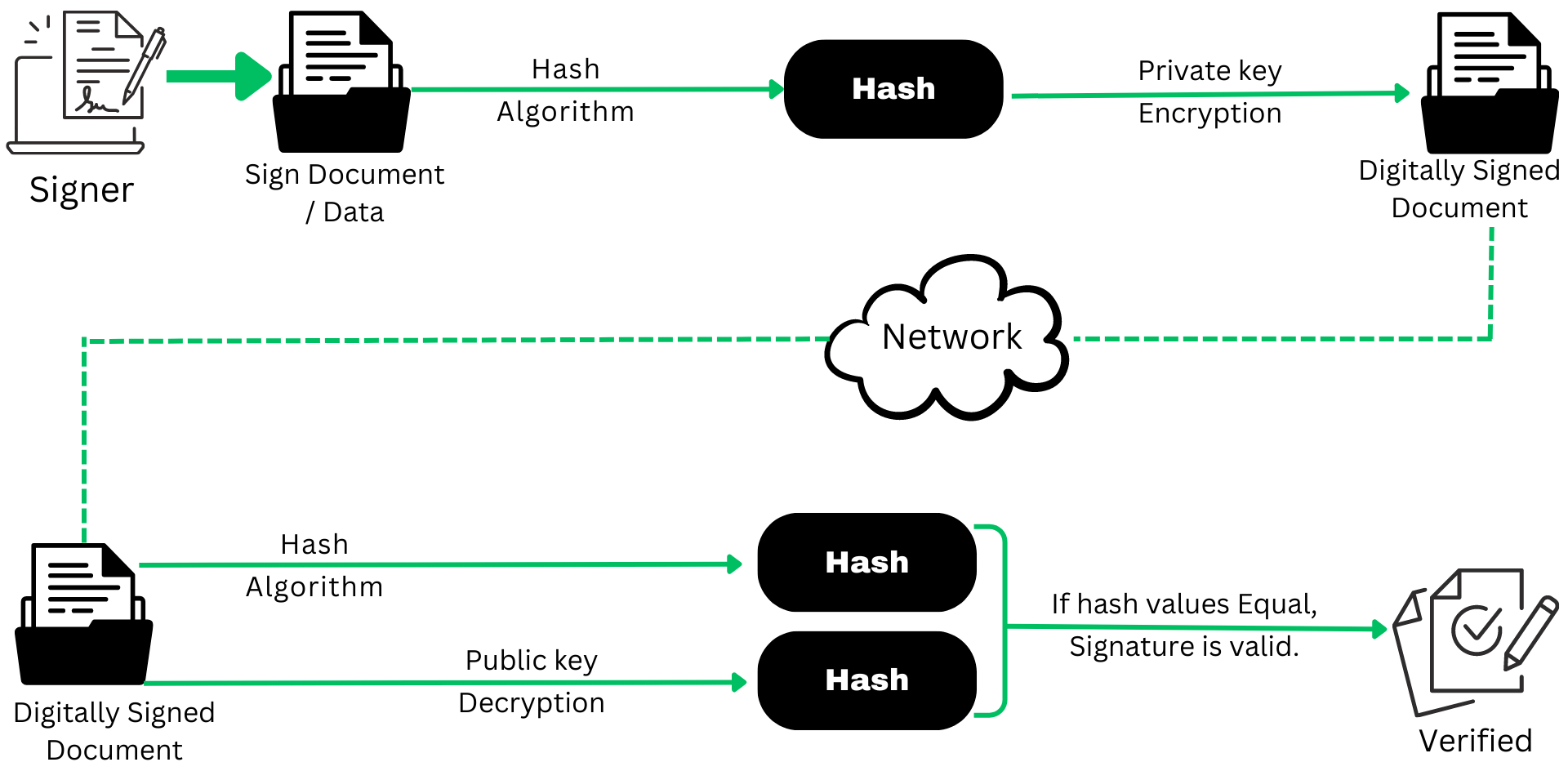
Use Public Key To Verify Signature . This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. Compares the 2 hash values. To use the public key, you first want to make sure that it contains the correct information; Decrypts the digital signature using the sender's public key, and. To do that, you verify the signature on the certificate, using. It can also use encryption and public and private keys to decrypt and verify the data. If they match, the signature is considered valid. The public key is shared with others and can be used to verify the digital signature.
from logicmojo.com
It can also use encryption and public and private keys to decrypt and verify the data. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. To use the public key, you first want to make sure that it contains the correct information; Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. Compares the 2 hash values. To do that, you verify the signature on the certificate, using. The public key is shared with others and can be used to verify the digital signature. Decrypts the digital signature using the sender's public key, and. If they match, the signature is considered valid. This key is mathematically linked to the private.
Digital Signature Enhancing Security and Efficiency Logicmojo
Use Public Key To Verify Signature If they match, the signature is considered valid. The public key is shared with others and can be used to verify the digital signature. To do that, you verify the signature on the certificate, using. Decrypts the digital signature using the sender's public key, and. It can also use encryption and public and private keys to decrypt and verify the data. This key is mathematically linked to the private. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. To use the public key, you first want to make sure that it contains the correct information; Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. If they match, the signature is considered valid. Compares the 2 hash values.
From kay-is.github.io
3 From Zero Lesson 6 Use Public Key To Verify Signature Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. The public key is shared with others and can be used to verify the digital signature. If they match, the signature is considered valid. Compares the 2 hash values. Decrypts the digital signature using the sender's public key, and. It can also use encryption. Use Public Key To Verify Signature.
From aws.amazon.com
How to verify AWS KMS signatures in decoupled architectures at scale Use Public Key To Verify Signature Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. It can also use encryption and public and private keys to decrypt and verify the data. The public key is shared with others and can be used to verify the digital signature. Compares the 2 hash values. This key is mathematically linked to the. Use Public Key To Verify Signature.
From global.alipay.com
Sign a request and verify the signature Product APIs Alipay Docs Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. To use the public key, you first want to make sure that it contains the correct information; This key is mathematically linked to the private. Compares the 2 hash values. Decrypts the digital signature using the sender's public key,. Use Public Key To Verify Signature.
From securityboulevard.com
Public Private Key Pairs & How they work Security Boulevard Use Public Key To Verify Signature Decrypts the digital signature using the sender's public key, and. It can also use encryption and public and private keys to decrypt and verify the data. To use the public key, you first want to make sure that it contains the correct information; If they match, the signature is considered valid. This key is mathematically linked to the private. Compares. Use Public Key To Verify Signature.
From sslcertificate.support
Public Key Signature What It Is & Why It's Everywhere Hashed Out by Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. If they match, the signature is considered valid. To do that, you verify the signature on the certificate, using. This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different. Use Public Key To Verify Signature.
From www.sectigo.com
What Is PKI? The Guide To Public Key Infrastructure Sectigo® Official Use Public Key To Verify Signature To use the public key, you first want to make sure that it contains the correct information; This key is mathematically linked to the private. Decrypts the digital signature using the sender's public key, and. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. Compares the 2 hash values. To verify a signature,. Use Public Key To Verify Signature.
From www.awesomefintech.com
Public Key AwesomeFinTech Blog Use Public Key To Verify Signature The public key is shared with others and can be used to verify the digital signature. This key is mathematically linked to the private. If they match, the signature is considered valid. Decrypts the digital signature using the sender's public key, and. To do that, you verify the signature on the certificate, using. To use the public key, you first. Use Public Key To Verify Signature.
From signx.wondershare.com
Digital Signature Verification How to Verify a Digital Signature Use Public Key To Verify Signature This key is mathematically linked to the private. If they match, the signature is considered valid. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. Decrypts the digital signature using the sender's. Use Public Key To Verify Signature.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Use Public Key To Verify Signature Decrypts the digital signature using the sender's public key, and. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To do that, you verify the signature on the certificate, using. To use the public key, you first want to make sure that it contains the correct information; To verify a signature, the recipient. Use Public Key To Verify Signature.
From linuxhint.com
How Do I Verify a PGP Signature? Use Public Key To Verify Signature Decrypts the digital signature using the sender's public key, and. This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. It can also use encryption and public and private keys to decrypt and verify the data. To use the public key, you first want to make. Use Public Key To Verify Signature.
From signx.wondershare.com
Digital Signature Example and Digital Signature Processing Use Public Key To Verify Signature This key is mathematically linked to the private. If they match, the signature is considered valid. The public key is shared with others and can be used to verify the digital signature. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To use the public key, you first want to make sure that. Use Public Key To Verify Signature.
From metamug.com
JWT verify using public key Use Public Key To Verify Signature It can also use encryption and public and private keys to decrypt and verify the data. Decrypts the digital signature using the sender's public key, and. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To verify a signature, the recipient first decrypts the signature using a public key that matches with the. Use Public Key To Verify Signature.
From global.alipay.com
Sign a request and verify the signature Product APIs Alipay Docs Use Public Key To Verify Signature If they match, the signature is considered valid. To do that, you verify the signature on the certificate, using. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. It can also use. Use Public Key To Verify Signature.
From blockchainworm.com
Digital Signature Digital Data Authentication Blockchain Worm Use Public Key To Verify Signature If they match, the signature is considered valid. Decrypts the digital signature using the sender's public key, and. Compares the 2 hash values. The public key is shared with others and can be used to verify the digital signature. It can also use encryption and public and private keys to decrypt and verify the data. To do that, you verify. Use Public Key To Verify Signature.
From blog.mailfence.com
Digital Signatures What Are They and How to Use Them? Mailfence Blog Use Public Key To Verify Signature It can also use encryption and public and private keys to decrypt and verify the data. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To do that, you verify the signature on the certificate, using. If they match, the signature is considered valid. To use the public key, you first want to. Use Public Key To Verify Signature.
From www.youtube.com
How To Verify Or Validate Digital Signature In Any Document. [Using Use Public Key To Verify Signature If they match, the signature is considered valid. It can also use encryption and public and private keys to decrypt and verify the data. This key is mathematically linked to the private. To use the public key, you first want to make sure that it contains the correct information; To do that, you verify the signature on the certificate, using.. Use Public Key To Verify Signature.
From techterms.com
Digital Signature Definition What is a digital signature? Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. If they match, the signature is considered valid. The public key is shared with others and can be used to verify the digital signature. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and. Use Public Key To Verify Signature.
From www.infosec.gov.hk
InfoSec Public Key Infrastructure Use Public Key To Verify Signature Decrypts the digital signature using the sender's public key, and. If they match, the signature is considered valid. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. This key is mathematically linked to the private. To use the public key, you first want to make sure that it contains the correct information; Compares. Use Public Key To Verify Signature.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta AU & NZ Use Public Key To Verify Signature This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. It can also use encryption and public and private keys to decrypt and verify the data. Compares the 2 hash values. To verify a signature, the recipient first decrypts the signature using a public key that. Use Public Key To Verify Signature.
From infosec.gov.hk
InfoSec Public Key Infrastructure Use Public Key To Verify Signature To use the public key, you first want to make sure that it contains the correct information; Decrypts the digital signature using the sender's public key, and. It can also use encryption and public and private keys to decrypt and verify the data. The public key is shared with others and can be used to verify the digital signature. If. Use Public Key To Verify Signature.
From cheapsslsecurity.com
Private Key and Public Key with an Example Explained by SSLsecurity Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To use the public key, you first want to make sure that it contains the. Use Public Key To Verify Signature.
From www.youtube.com
Digital signature verify // How to verified digital signature Use Public Key To Verify Signature This key is mathematically linked to the private. Compares the 2 hash values. Decrypts the digital signature using the sender's public key, and. The public key is shared with others and can be used to verify the digital signature. To do that, you verify the signature on the certificate, using. If they match, the signature is considered valid. It can. Use Public Key To Verify Signature.
From github.com
GitHub Akshat12210/DigitalSignatureandVerification Use Public Key To Verify Signature If they match, the signature is considered valid. Decrypts the digital signature using the sender's public key, and. This key is mathematically linked to the private. It can also use encryption and public and private keys to decrypt and verify the data. To verify a signature, the recipient first decrypts the signature using a public key that matches with the. Use Public Key To Verify Signature.
From logicmojo.com
Digital Signature Enhancing Security and Efficiency Logicmojo Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. The public key is shared with others and can be used to verify the digital signature. It can also use encryption and public and private keys to decrypt and verify the data. Creating and verifying signatures uses the public/private. Use Public Key To Verify Signature.
From blue2digital.com
Create your own digital signature, digitally sign a file, verify a Use Public Key To Verify Signature It can also use encryption and public and private keys to decrypt and verify the data. Compares the 2 hash values. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To do that, you verify the signature on the certificate, using. The public key is shared with others and can be used to. Use Public Key To Verify Signature.
From www.youtube.com
Signing using asymmetric keys Public & Private Keys and Digital Use Public Key To Verify Signature To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. It can also use encryption and public and private keys to decrypt and verify the data. Compares the 2 hash values. This key is mathematically linked to the private. If they match, the signature is considered valid. Creating and. Use Public Key To Verify Signature.
From www.researchgate.net
Steps to verify the validity of the public key. Download Scientific Use Public Key To Verify Signature This key is mathematically linked to the private. If they match, the signature is considered valid. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. To use the public key, you first. Use Public Key To Verify Signature.
From www.maketecheasier.com
How to Verify Authenticity of Windows Software with Digital Signatures Use Public Key To Verify Signature Compares the 2 hash values. The public key is shared with others and can be used to verify the digital signature. Decrypts the digital signature using the sender's public key, and. If they match, the signature is considered valid. This key is mathematically linked to the private. To use the public key, you first want to make sure that it. Use Public Key To Verify Signature.
From securityaffairs.co
What is a digital signature? Fundamental principles Security Use Public Key To Verify Signature Compares the 2 hash values. Decrypts the digital signature using the sender's public key, and. To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. If they match, the signature is considered valid.. Use Public Key To Verify Signature.
From www.youtube.com
How to sign a file or verify a signature of a file using GPG keychain Use Public Key To Verify Signature To do that, you verify the signature on the certificate, using. Decrypts the digital signature using the sender's public key, and. This key is mathematically linked to the private. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. It can also use encryption and public and private keys to decrypt and verify the. Use Public Key To Verify Signature.
From sectigostore.com
Public Key vs Private Key How Do They Work? InfoSec Insights Use Public Key To Verify Signature If they match, the signature is considered valid. Compares the 2 hash values. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. To use the public key, you first want to make sure that it contains the correct information; This key is mathematically linked to the private. The public key is shared with. Use Public Key To Verify Signature.
From www.answersaccess.com
Solved SEED Labs RSA PublicKey Encryption and Signat Use Public Key To Verify Signature If they match, the signature is considered valid. The public key is shared with others and can be used to verify the digital signature. This key is mathematically linked to the private. Decrypts the digital signature using the sender's public key, and. It can also use encryption and public and private keys to decrypt and verify the data. Compares the. Use Public Key To Verify Signature.
From blog.mdaemon.com
Encrypting vs. Signing with OpenPGP. What’s the Difference? Use Public Key To Verify Signature Compares the 2 hash values. To do that, you verify the signature on the certificate, using. Decrypts the digital signature using the sender's public key, and. It can also use encryption and public and private keys to decrypt and verify the data. The public key is shared with others and can be used to verify the digital signature. If they. Use Public Key To Verify Signature.
From surepass.io
How To Create & Verify Digital Signatures Online? SurePass Use Public Key To Verify Signature To use the public key, you first want to make sure that it contains the correct information; To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. Creating and verifying signatures uses the public/private keypair in an operation different from encryption and decryption. If they match, the signature is. Use Public Key To Verify Signature.
From proton.me
What is a digital signature? Proton Use Public Key To Verify Signature This key is mathematically linked to the private. If they match, the signature is considered valid. To use the public key, you first want to make sure that it contains the correct information; To verify a signature, the recipient first decrypts the signature using a public key that matches with the senders private key. It can also use encryption and. Use Public Key To Verify Signature.