Access Control Entity . Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations.
from www.tpsearchtool.com
Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with.
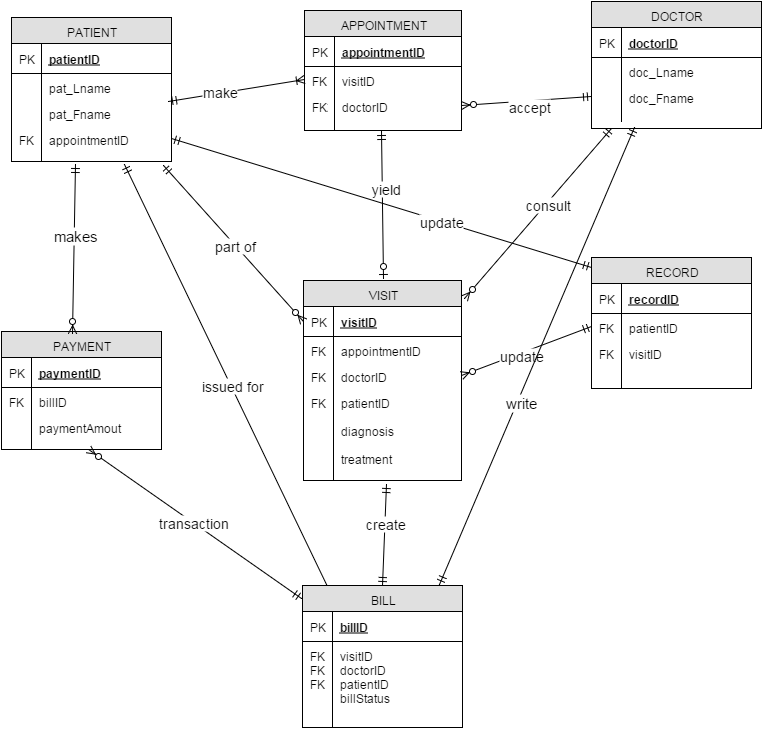
E R Diagram For Role Based Access Control Entity Relationship Diagram
Access Control Entity Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with.
From kintronics.com
Access Control Installation Kintronics Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access control systems. Access Control Entity.
From www.pixazsexy.com
E R Diagram For Role Based Access Control Entity Relationship Diagram Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to. Access Control Entity.
From www.youtube.com
Entity Access Control for Drupal 8, 9, and 10 How to work Entity Access Control Entity Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an. Access Control Entity.
From www.researchgate.net
Entity relationship diagram for MINDS Grid access control framework Access Control Entity Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set. Access Control Entity.
From ermodelexample.com
How To Create An Entity Relationship Diagram In Access Access Control Entity Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access controls identify an. Access Control Entity.
From www.researchgate.net
System architecture for our access control showing the entities Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control is a security term used to refer to a set. Access Control Entity.
From blog.mantratec.com
Why is Access Control Integration in Every Organization a Need for Our Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access controls identify an. Access Control Entity.
From www.tpsearchtool.com
Database Design Rbac Role Based Access Control Er Diagram Stack Images Access Control Entity Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access. Access Control Entity.
From eureka.patsnap.com
Management systems for multiple access control entities Eureka Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person. Access Control Entity.
From content.iospress.com
Distributed management of permission for access control model IOS Press Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access. Access Control Entity.
From www.slideserve.com
PPT Access Control Intro, DAC and MAC PowerPoint Presentation, free Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control systems perform identification, authentication, and authorization of users and entities. Access Control Entity.
From getsafeandsound.com
Access Control System An Overview Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified. Access Control Entity.
From adamtheautomator.com
Manage NTFS Permissions with PowerShell A Tutorial Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Access control systems perform identification, authentication, and authorization of users and entities. Access Control Entity.
From slideplayer.com
Principles and Practice ppt download Access Control Entity Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access controls identify an. Access Control Entity.
From www.youtube.com
Rolebased Access Control for CRUD API with Entity Framework Core & XPO Access Control Entity Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Access control systems perform identification, authentication, and authorization of users and entities. Access Control Entity.
From www.researchgate.net
SMART HOME ACCESS CONTROL ARCHITECTURE & CROSSDOMAIN COMMUNICATION Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control is a security term used to refer to a set. Access Control Entity.
From p8programmer.blogspot.com
P8 Development tutorials Access Control List(ACL) and Access Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to. Access Control Entity.
From www.researchgate.net
Description of accesscontrol model relationship, based on business Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Access control systems perform identification, authentication, and authorization of users and entities. Access Control Entity.
From www.tpsearchtool.com
E R Diagram For Role Based Access Control Entity Relationship Diagram Access Control Entity Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access controls identify. Access Control Entity.
From eventura.com
Access Control Explained Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access control is a security term used to refer to. Access Control Entity.
From ermodelexample.com
Rbac (Role Based Access Control) Er Diagram Stack Overflow Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of. Access Control Entity.
From rasha08.medium.com
Access Control in SaaS applications with EBAC (Entity based access Access Control Entity Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems. Access Control Entity.
From effectivehealthcare.ahrq.gov
Enhanced Functionality for the Distributed Research Network Pilot Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems. Access Control Entity.
From docs.healthcatalyst.com
Controlling Entity Access Access Control Entity Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems. Access Control Entity.
From www.slideserve.com
PPT Access Control Intro, DAC and MAC PowerPoint Presentation, free Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set. Access Control Entity.
From www.researchgate.net
Access Control Conversations between Entities in Distributed Systems Access Control Entity Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access. Access Control Entity.
From www.tpsearchtool.com
E R Diagram For Role Based Access Control Entity Relationship Diagram Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to. Access Control Entity.
From help.sap.com
Access Control Lists (ACL) in the DTR Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and. Access Control Entity.
From maokatur.blogspot.com
Role Based Access Control Configure Role Based Access Control Rbac Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and. Access Control Entity.
From www.researchgate.net
System architecture for our access control showing the entities Access Control Entity Access controls identify an individual or entity, verify the person or application is who or what it claims to be, and authorizes the access level and set of actions associated with. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Iam gives secure access to company resources—like emails, databases, data, and applications—to. Access Control Entity.
From www.researchgate.net
Access Control Conversations between Entities in Distributed Systems Access Control Entity Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a. Access controls identify an individual or entity, verify the person or application is who or what it claims to be,. Access Control Entity.
From www.slideserve.com
PPT Security PowerPoint Presentation, free download ID6985814 Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Iam gives secure access. Access Control Entity.
From www.slideserve.com
PPT Access Control Intro, DAC and MAC PowerPoint Presentation, free Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Access controls identify an. Access Control Entity.
From ermodelexample.com
Er Diagram Access Access Control Entity Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to. Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations. Access control systems perform identification, authentication, and authorization of users and entities by evaluating required login. Iam gives secure access. Access Control Entity.