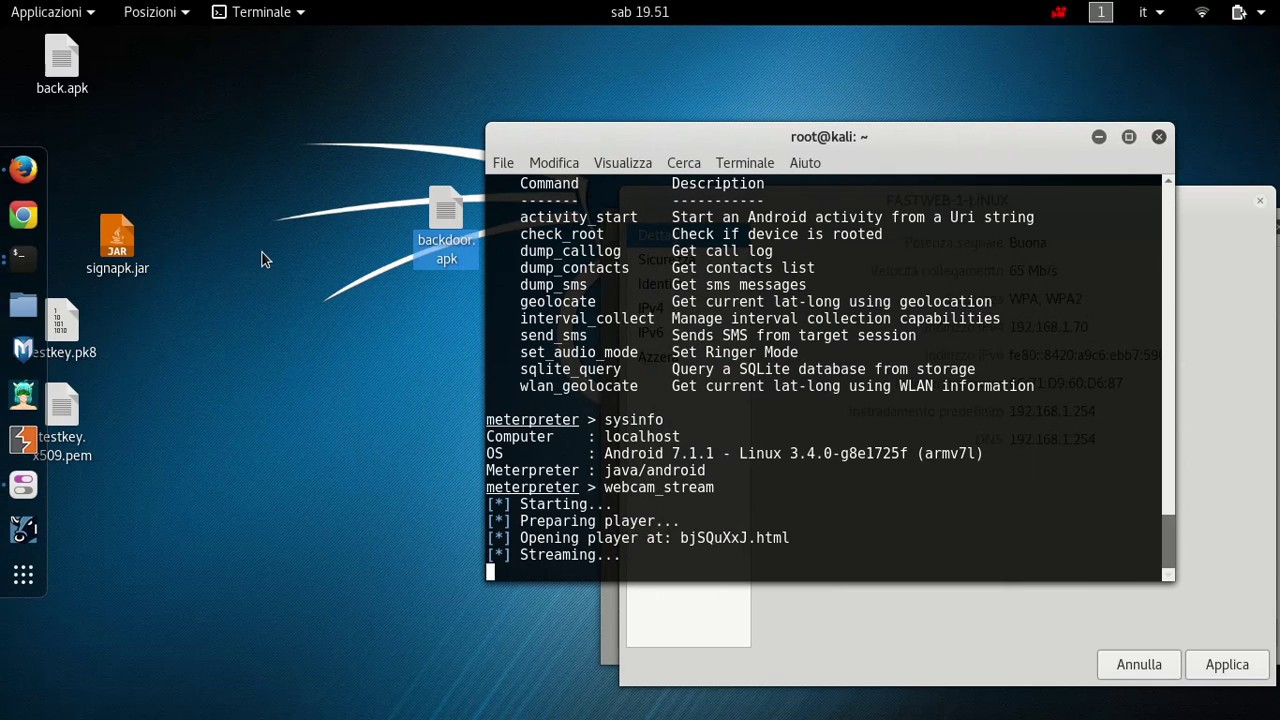
Best Kali Linux Backdoor . Easy tool to generate backdoor. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Thefatrat a massive exploiting tool : A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Here are 1,536 public repositories matching this topic. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Generate a php backdoor (generate) protected with the given password (s3cr3t).
from www.youtube.com
Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). Easy tool to generate backdoor. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Here are 1,536 public repositories matching this topic. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software.
android backdoor kali linux 2017 YouTube
Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Easy tool to generate backdoor. Generate a php backdoor (generate) protected with the given password (s3cr3t). This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Thefatrat a massive exploiting tool : Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Here are 1,536 public repositories matching this topic.
From www.youtube.com
Como instalar en Kali Linux Veilevasion para crear PAYLOAD (BackDoor Best Kali Linux Backdoor Here are 1,536 public repositories matching this topic. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Easy tool to generate backdoor. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. This post will dive into how. Best Kali Linux Backdoor.
From www.youtube.com
Generate 64bit Backdoor in Kali Linux Msfvenom Windows 10 Exploiting Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). Easy tool to generate backdoor. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Here are 1,536 public repositories. Best Kali Linux Backdoor.
From www.youtube.com
testing Analyzer Kali Linux Como criar um backdoor para Best Kali Linux Backdoor Easy tool to generate backdoor. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Here are 1,536 public repositories matching this topic. A linux. Best Kali Linux Backdoor.
From www.youtube.com
Create windows backdoor using metasploit in kali linux CEHv11 YouTube Best Kali Linux Backdoor Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Easy tool to generate backdoor. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. In. Best Kali Linux Backdoor.
From www.youtube.com
COMO CRIAR BACKDOOR KALI LINUX YouTube Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). In. Best Kali Linux Backdoor.
From www.youtube.com
47 Kali Linux Backdoor Process and Functions YouTube Best Kali Linux Backdoor Easy tool to generate backdoor. Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. In. Best Kali Linux Backdoor.
From www.youtube.com
Backdoor con kali linux 2.0 italiano YouTube Best Kali Linux Backdoor In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Here are 1,536 public repositories matching this topic. Easy tool to generate backdoor. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. This post will dive into how we can take advantage of. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Easy tool to generate backdoor. Thefatrat a massive exploiting tool : Generate a php backdoor (generate) protected with the given password (s3cr3t). In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Using msfvenom,. Best Kali Linux Backdoor.
From www.youtube.com
Lİnux Kali Exploit Linux Kali Backdoor Show YouTube Best Kali Linux Backdoor A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Easy tool to generate backdoor. Here are 1,536 public repositories matching this topic. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Using msfvenom, the combination of msfpayload and msfencode,. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux 2.0 Creating FUD Backdoor Shellter YouTube Best Kali Linux Backdoor Thefatrat a massive exploiting tool : Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. A linux ebpf rootkit with a. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux Backdoor FTP YouTube Best Kali Linux Backdoor Thefatrat a massive exploiting tool : A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Easy tool to generate backdoor. This post will dive into how we can. Best Kali Linux Backdoor.
From www.youtube.com
android backdoor kali linux 2017 YouTube Best Kali Linux Backdoor A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Easy tool to generate backdoor. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). In order to develop a. Best Kali Linux Backdoor.
From www.youtube.com
kali linux php backdoor using msfvenom(metasploit) YouTube Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Here are 1,536 public repositories matching this topic. Generate a php backdoor (generate) protected with the given password (s3cr3t). A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities.. Best Kali Linux Backdoor.
From www.tecnogalaxy.it
Creare una backdoor manualmente con Kali Linux Tecnogalaxy Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Thefatrat a massive exploiting tool : Easy tool to generate backdoor. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux (Metasploit) Creating a Backdoor Undetectable by Antivirus Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Easy tool to generate backdoor. Here are 1,536 public repositories matching this topic. Thefatrat a massive exploiting tool : A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Generate a. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor Thefatrat a massive exploiting tool : A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Here are 1,536 public repositories matching this topic. This post will dive into. Best Kali Linux Backdoor.
From www.youtube.com
VIDEO AULA KALI LINUX como controlar PC via back door. YouTube Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Here are 1,536 public repositories matching this topic. Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux Tutorial Metasploit Android Backdoor erstellen 02 YouTube Best Kali Linux Backdoor Here are 1,536 public repositories matching this topic. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Thefatrat a massive exploiting tool : Using msfvenom, the combination of msfpayload and msfencode, it's possible. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux Tutorial Run Backdoor Exploit Android YouTube YouTube Best Kali Linux Backdoor In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Thefatrat a massive exploiting tool : Generate a php backdoor (generate) protected with the given password (s3cr3t). A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Easy tool to generate backdoor. Here are. Best Kali Linux Backdoor.
From www.youtube.com
Backdoor con kali linux YouTube Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Easy tool to generate backdoor. In order to develop a. Best Kali Linux Backdoor.
From www.youtube.com
Como Criar Um Backdoor [Kali LInux] [Backdoor] YouTube Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). Thefatrat a massive exploiting tool : Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. This post will dive into how we can take advantage of a vulnerability in a web application to. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Here are 1,536 public repositories matching this topic. This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Thefatrat a massive exploiting. Best Kali Linux Backdoor.
From www.youtube.com
Come creare una backdoor kali linux YouTube Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Easy tool to generate backdoor. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). Here are 1,536 public repositories matching this topic. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. This post will dive into how we can take advantage of a vulnerability in a web. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor Easy tool to generate backdoor. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Generate a php backdoor (generate) protected with the given password (s3cr3t). A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Using msfvenom, the combination of msfpayload and msfencode,. Best Kali Linux Backdoor.
From www.youtube.com
MSF METASPLOIT BACKDOOR KALI LINUX YouTube Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Thefatrat a massive exploiting tool : Easy tool to generate backdoor. Generate a php backdoor (generate) protected with the given password (s3cr3t). This post will dive into how we can take advantage of a vulnerability. Best Kali Linux Backdoor.
From www.youtube.com
Kali Linux Tutorials Backdoor (acoo) 018 YouTube Best Kali Linux Backdoor Thefatrat a massive exploiting tool : Here are 1,536 public repositories matching this topic. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Generate a php backdoor (generate) protected with the given password. Best Kali Linux Backdoor.
From www.officialhacker.com
How To Create Backdoor In Kali Linux Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Thefatrat a massive exploiting tool : Easy tool to generate backdoor. Generate a php backdoor (generate) protected with the given password (s3cr3t). Here are 1,536 public repositories matching this topic. A linux ebpf rootkit with a backdoor,. Best Kali Linux Backdoor.
From www.youtube.com
46 Kali Linux Backdoor Overview YouTube Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Thefatrat a massive exploiting tool : Easy tool to generate backdoor. A. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Here are 1,536 public repositories matching this topic. Easy tool to generate backdoor. In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Thefatrat a massive exploiting. Best Kali Linux Backdoor.
From www.wikihow.com
How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux Best Kali Linux Backdoor A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Generate a php backdoor (generate) protected with the given password (s3cr3t). In order to develop. Best Kali Linux Backdoor.
From www.youtube.com
Apps backdoor kali linux YouTube Best Kali Linux Backdoor Thefatrat a massive exploiting tool : This post will dive into how we can take advantage of a vulnerability in a web application to gain access and upload a. Here are 1,536 public repositories matching this topic. Easy tool to generate backdoor. In order to develop a backdoor, you need to change the signature of your malware to evade any. Best Kali Linux Backdoor.
From www.geeksforgeeks.org
How to Install FatRat Tool in Kali Linux? Best Kali Linux Backdoor Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. A linux ebpf rootkit with a backdoor, c2, library injection, execution hijacking, persistence and stealth capabilities. Thefatrat a massive exploiting tool : Here are 1,536 public repositories matching this topic. In order to develop a. Best Kali Linux Backdoor.
From hack2kalilinux.blogspot.com
Create A Backdoor Using Metsploit and Backtrack 5 or Kali Linux in Best Kali Linux Backdoor In order to develop a backdoor, you need to change the signature of your malware to evade any antivirus software. Thefatrat a massive exploiting tool : Easy tool to generate backdoor. Generate a php backdoor (generate) protected with the given password (s3cr3t). Here are 1,536 public repositories matching this topic. Using msfvenom, the combination of msfpayload and msfencode, it's possible. Best Kali Linux Backdoor.
From www.youtube.com
Como crear un PAYLOAD (Backdoor) en Kali Linux usando Veil Evasion Best Kali Linux Backdoor Generate a php backdoor (generate) protected with the given password (s3cr3t). Using msfvenom, the combination of msfpayload and msfencode, it's possible to create a backdoor that connects back to the attacker by using reverse shell tcp. Easy tool to generate backdoor. This post will dive into how we can take advantage of a vulnerability in a web application to gain. Best Kali Linux Backdoor.